Section 5.9 Man-in-the-Middle Attack
5.9 Man-in-the-Middle Attack
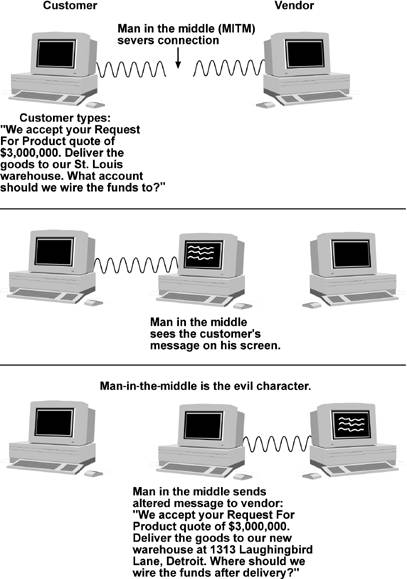
This attack is where your outgoing packets are going not to your intended destination, but rather to someone who has severed the communication path between you and your intended recipient and pretends to be the other person to you and pretends to be you to the intended other person. This "Man in the middle" then may send a different message to your intended recipient. Response packets from that person likewise go to the person in the middle who then sends a different message back to you. In our figure, a vendor and its customer are arranging a business deal for a large purchase of goods. The vendor's salesman and the customer's purchasing agent are specifying the customer's delivery address, the terms of payment, and the vendor's bank account where the funds are to be wired to. To both the vendor and the customer, this seems routine and normal. Please study Figure 5.4 and try to determine a way that the vendor or customer could detect this fraud. Figure 5.4(a). Man-in-the-middle attack.
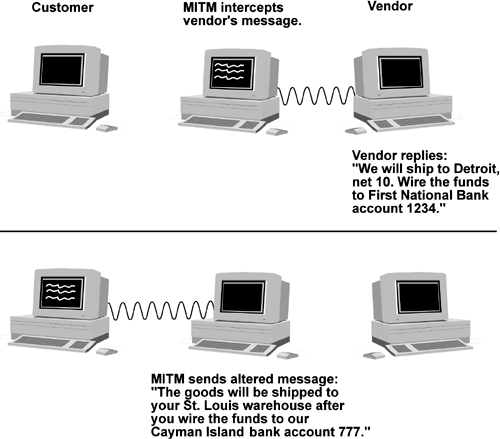
Figure 5.4(b). Man-in-the-middle attack.
As you can see in Figure 5.4, neither the vendor nor the client had any idea that it was not communicating with who it thought that it was. Generally, methods of avoiding this problem require either a secure communications medium (such as Registered Mail or SSH) or some verification information that was securely exchanged between the two parties. This verification information might be a secret algorithm to generate a message digest (see "Using GPG to Encrypt Files the Easy Way" on page 431) or some other cryptographic technique. The risk of a Man-in-the-middle attack really is why the laws regarding tampering with the mail are some of the most severe laws on the books, and why such care is taken with Registered Mail. It is why we have notary publics and corporate seals. It is why the king's seal was so important. In fact one definition of "seal" is that it is a mark or design indicating authenticity. This attack can be very difficult to prevent because you and the intended other person must first exchange some information in a trusted manner to initiate trusted communications. PGP (GPG), SSH, and VPN will prevent a Man-in-the-middle attack only if any initial keys are exchanged without suffering a Man-in-the-middle attack and the two end systems are not compromised. These tools are discussed in "Pretty Good Privacy (PGP)" on page 430, "Using GPG to Encrypt Files the Easy Way" on page 431, "Protecting User Sessions with SSH" on page 409, and "VPN Using FreeS/WAN IPSec" on page 428. Avoiding this compromise of the end systems includes avoiding a compromise between each system and the user's keyboard and screen. Usually this means a secure X configuration, as discussed in "X Marks the Hole" on page 117. It is common to put your PGP public key on your Web site and some will include it in their e-mail. Confirming it via FAX or telephone is sufficient for medium security applications.
|
| Top |
EAN: N/A
Pages: 260