Authentication and Authorization Flow
| < Day Day Up > |
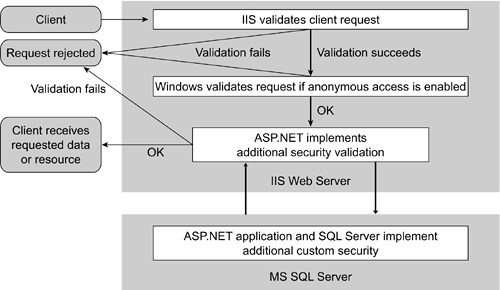
| The security features of IIS, .NET Framework, and SQL Server work together to establish the flow of the authentication and authorization process. A client submits a request for an ASP.NET page. The request is first received by IIS, which works with the Windows operating system to initiate the security process. IIS analyzes the request and, based on selected IIS authentication options, validates it. If IIS authentication fails, the request is rejected and the appropriate error message is displayed in the client's browser. If IIS successfully validates the incoming request, the request is passed to ASP.NET. The Windows operating system then looks at the properties of the file containing the ASP.NET page and decides whether the read request on the file is authorized. If the Windows validation is successful, the request reaches the ASP.NET application, which can implement additional custom steps to authenticate the request and to authorize the resources for the request. The ASP.NET application often works in conjunction with SQL Server to implement custom credentials validation. The sample portal implementation code example at the end of this chapter demonstrates these steps. Figure 6.1 illustrates the authentication and authorization flow. Figure 6.1. IIS, ASP.NET, and SQL Server Authenticate a Request |
| < Day Day Up > |
EAN: 2147483647
Pages: 164