The Dance of the Seven Layers
| |
The Dance of the Seven Layers
Network protocols are grouped according to their functions, such as sending and receiving messages from the network interface, talking to the hardware, making it possible for applications to do their things in a network environment, and talking to the software.
This group organization involves stacking multiple layers of functionality, where software is associated with each layer. When the software that supports a particular network protocol loads on a computer, it's called a protocol stack. All computers on the network load all or part of the stack. They use the same parts of the stack, called peer protocols , when they communicate with each other as you guessed it peers.
The best-known collection of networking layers was developed as part of an open networking systems effort in the 1980s called the Open Systems Interconnection (OSI) initiative. This model is known as the OSI reference model (also simply called the OSI model) because it defines a common frame of reference for understanding how networks work. Even though the OSI initiative never really achieved widespread adoption, the OSI model remains a standard tool to explain how network communications are structured and how they behave. The OSI model is shown in Figure 3-1.
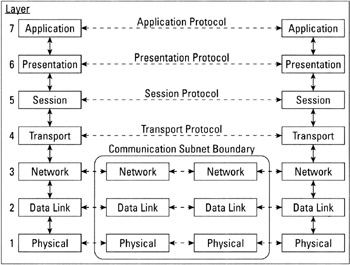
Figure 3-1: The OSI reference model breaks networking protocols into seven layers.
The OSI model consists of seven layers, as follows (working from the bottom up):
-
Physical layer: This is the layer where the network hardware operates. Rules for this layer govern the types of connectors used, what types of signaling techniques carry data across the network, and the types of cable or other networking media that the physical, tangible part of the network uses. In some sense, this is the only part of the OSI model that you can see and touch.
-
Data Link layer: This layer handles communication with the network hardware. For outbound messages, the Data Link layer enables the conversion of the bits that computers use to represent data into equivalent signals needed to move data across the network. For inbound messages, it reverses the process by enabling the conversion of signals into their equivalent bits. The Data Link layer is also where low-level hardware addresses for individual network interface cards (NICs) and other devices are handled.
-
Network layer: This layer routes messages between senders and receivers, which means that it also handles translation between human-readable network addresses and computer-readable network addresses (which are not the same as the hardware addresses that the Data Link layer handles). Each message that passes through this layer includes the sender's and the receiver's addresses to identify the parties involved. The Network layer moves data from sender to receiver when they aren't both attached to the same cable segment.
-
Transport layer: This layer chops up large messages into so-called Protocol Data Units (PDUs), or packets, and sends them across a network. It also puts PDUs back together to reconstitute messages upon receipt. The Transport layer can also include data integrity checks by adding a bit pattern to each message based on a mathematical calculation before sending. This same calculation is repeated by the sender, and the result is compared to the value calculated beforehand. If both values agree, the Transport layer assumes that the transmission was accurate and correct; if they don't agree, the Transport layer requests that the PDU be resent . This integrity function is optional; therefore, some Transport layer protocols include an integrity check and others don't.
-
Session layer: This layer sets up ongoing network conversations (called sessions ) between sender and receiver. This kind of ongoing connection makes it easier for computers to exchange large amounts of data, or to maintain a connection when data moves regularly between both parties to a session. Therefore, the Session layer handles session setup (which is like dialing a phone), session maintenance (which is like having a phone conversation), and session termination , or teardown (which is like ending a phone conversation and then hanging up the phone).
-
Presentation layer: This layer converts data for network delivery. The assumption that drives this activity is that the sender and the receiver may not share a common set of data types, formats, or representations. Therefore, the Presentation layer converts data from formats created by the sender into a generic format for network transit, and then converts that generic form into a format specific to the receiver upon delivery. This conversion process allows programmers on both sides of the network connection to assume generic formats for network data, and to handle the details necessary to deliver that data to a specific client more easily.
-
Application layer: This layer's name is something of a misnomer. It doesn't refer to the application or service that seeks to send or receive data across a network. Rather, it refers to an interface between the protocol stack and applications or system services. The Application layer defines the methods by which applications or system services can request network access and by which they can obtain access to incoming data from the network.
| KEY CONCEPT | Each layer functions more or less independently of the others. But the job of any given layer is to provide services for the layer above it and to deliver data to the layer below. (The lowest level of the OSI model, the Physical layer, simply sends data on to a receiver or to the Data Link layer, depending on whether the communication is coming or going.) |
The encoding that a layer does on the sending side is decoded by the same layer on the receiving side. Therefore, the layered OSI model helps mephasize that protocols on the sending end accept data from applications, convert that data into a generic form, manage conversations, prepare data to be sent across the network, address and route data, and then convert that data into signals for transmission across the network.
On the receiving end, that process is reversed : The protocols convert signals into data, figure out where that data is to be delivered, reconstitute incoming messages into their original containers, manage conversations, prepare the data for the client computer, and deliver that data to an application.
Some wags like to claim that there's an eighth layer to the protocol stack, and that it's the most important layer of all. It's called the Politics and Religion layer, and it jokingly refers to the organizational beliefs and requirements that drive network use. Even though there's no such layer in the OSI model, you'd be well-advised to keep this layer in mind any time you have to sell networking technology to upper management in your organization!
| |
EAN: 2147483647
Pages: 195