Planning Security Groups
| In Windows NT 4.0, the recommended strategy for assigning permissions to resources is to assign permissions to groups and add specific users to the appropriate groups. Windows 2000 maintains a similar strategy but allows for more flexibility in that different types of security groups can be created. Windows 2000 uses these different security groups to logically organize users and computers for assigning rights and permissions. By placing users into security groups, permissions to access resources can be easily assigned to a large number of users. When planning security groups, consider the following topics, which are covered in this section:
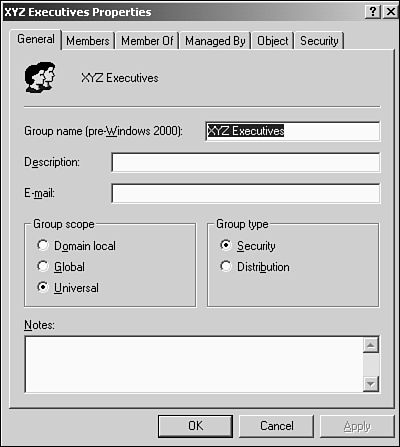
Types of Security GroupsWhen you are planning security groups, you must determine which type of security group to use. You can choose from three security group types:
You select the type of group, as shown in Figure 7.2, when creating a new group using the Active Directory Users and Computers MMC snap-in. You can also change the group type for existing groups using the same interface. Figure 7.2. The various security groups available in Windows 2000. Global GroupThe first type of security group is the global group . Global groups are used to logically organize users in a domain who have common needs to assign them permissions to network resources. When deciding whether to use global groups, keep the following characteristics in mind:
Domain Local GroupDomain local groups are also used to assign permissions to resources on the network, but they do not have the same characteristics as global groups. This type of group is used to organize users throughout the forest and assign them permissions to resources in the local domain. Here are some points to keep in mind concerning domain local groups:
The domain local group created in the Training domain can be used to grant users throughout the forest access to resources only in the Training domain. To grant users throughout the forest permissions to a resource located in the Consulting domain, a domain local group would have to be specifically created in that domain.
Universal GroupsThe third type of security group that can be used is the universal group. This type of group is used to assign a group of users from different domains permission to network resources throughout the forest. Here are some points to keep in mind concerning universal groups:
Now that you've become familiar with the types of security groups available in Windows 2000, let's take a look at group nesting. Nesting Security GroupsNesting is the process of adding groups to groups or creating a hierarchy of groups. Recall the discussion of OUs and how they can be nested in each other; the same thing can be done with security groups. Nesting security groups can greatly simplify the process of assigning permissions and reduce network traffic.
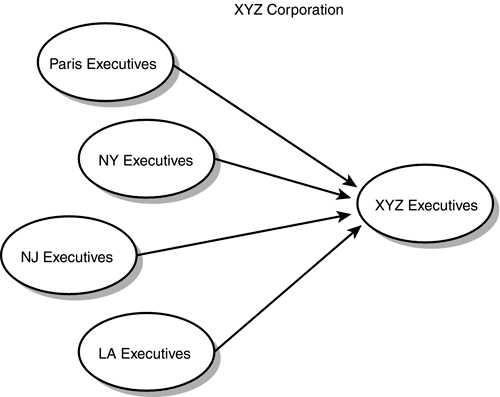
For example, in the XYZ Corporation, specific groups could be created for each group of executives in the different geographical locations. These groups could then be nested into one group that would represent all executives from each location (see Figure 7.3). In cases in which all the executives require access to network resources, permissions need only be assigned once to the XYZ Executives group. Figure 7.3. By nesting the four groups created for the executives into another group (XYZ Executives), permissions need to be set only once to give all executives access to network resources. Here are a couple of guidelines to follow when you are nesting security groups:
If you recall from Windows NT 4.0, the acronym for creating groups and assigning permissions is AGLP (assign user accounts to global groups, assign global groups to local groups, and assign permissions to the local group). Windows 2000 maintains a similar version of this strategy. When creating security groups, use the recommended AGDLP (assign user accounts to global groups, assign global groups to domain local groups, and assign permissions to the local group) model to ensure some form of consistency in a business when creating security groups:
|
EAN: 2147483647
Pages: 148