Network Management Protocols and Tools
| In this section, we first introduce some terminology that is related to network management protocols. This is followed by a discussion of the following protocols and tools:
We conclude with a discussion of some other network management tools that are available. TerminologyFigure 9-1 illustrates some terms that are related to network management; the terms are described as follows:
Figure 9-1. Network Management Terminology SNMP is the simplest network management protocol. The management information standard is the MIB, a detailed definition of the information on a managed device. MIB data is accessible through a network management protocol, such as SNMP. The RMON standard is an extension to the MIB; while the MIB only provides static information about a managed device, an RMON agent creates specific groups of statistics that can be collected for long-term trend analysis. These standards are described in the following sections. SNMPKey Point SNMP is an IP application protocol that runs on top of User Datagram Protocol (UDP) to transport management data. It allows both the configuring and retrieval of management information. The initial SNMP version 1 (SNMPv1) was extended to SNMP version 2 (SNMPv2) and its variants and then further extended to SNMP version 3 (SNMPv3). SNMPv1 defines five message types between the management application and management agents, as follows:
SNMPv2 includes the following two new message types:
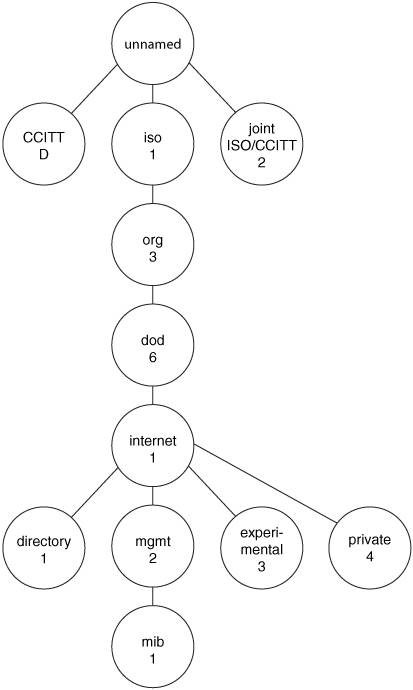
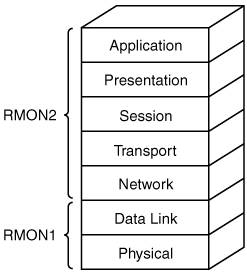
SNMPv3 (implemented on Cisco routers in Internetwork Operating System [IOS] Release 12.0 and later) adds security, including the ability to add authentication and privacy to SNMP communication on a per-user or group-of-users basis. This can be used, for example, to define which objects a user can read or write, and which notifications a user can receive. MIBA MIB is a standard for collecting management information. Key Point A MIB stores the information gathered by a management agent locally on a managed device, for later retrieval by a network management protocol. Note The MIB acronym is usually pronounced as a word (that rhymes with bib), not as individual letters. As shown in Figure 9-2, the MIB structure is logically represented as a tree hierarchy. The root of the tree is not named and splits into three main branches: Consultative Committee for International Telegraph and Telephone (CCITT), ISO, and joint ISO/CCITT. Figure 9-2. Internet MIB Hierarchy[1] The branches in the MIB tree are identified by short text strings and integers, which form object identifiers. For example, the Internet standard MIB is represented by the object identifier 1.3.6.1.2.1; this can also be written as iso.org.dod.internet.mgmt.mib. Each object in a MIB has a unique object identifier. Network management applications specify this identifier when they want to set or retrieve a specific object. Along with the standard MIBs, vendors can reserve their own private branch of the MIB, under which they can create custom objects. For example, Cisco devices have objects in the private section of the MIB tree (1.3.6.1.4.1.9, or iso.org.dod.internet.private.enterprise.cisco) for parameters related to Cisco's proprietary protocols and other variables. As an example, the Cisco 3800 Series integrated services router's object identifier is 1.3.6.1.4.1.9.1.544. Standard MIBs are defined in different Requests For Comments (RFCs). MIB-II, defined by RFC 1213 ("Management Information Base for Network Management of TCP/IP-based Internets: MIB-II"), is an extension of the original MIB (which is now called MIB-I). MIB-II supports some new protocols and provides more detailed and structured information. RMONRMON is defined as part of the MIB-II collection of objects. RMON not only collects and stores data, but RMON agents within managed objects (or on separate RMON probe devices) also perform some analysis of the data. For example, RMON data can include statistical information for conversations between two hosts, from the perspective of the managed object. The RMON MIB is 1.3.6.1.2.1.16 (iso.ord.dod.internet.mgmt.mib.rmon). Because RMON agents must look at every frame on the network, they can cause performance problems on a managed device. Thus, separate RMON probes can be used to offload the processing to another device. RMON1 provides statistics at the data link and physical layers of the Open Systems Interconnection (OSI) model, while RMON2 extends RMON1 through to the application layer, as illustrated in Figure 9-3 and described in the following sections. Figure 9-3. RMON1 Provides Visibility at the Lower Two Layers While RMON2 Extends to the Upper Layers RMON 1RMON1, defined in RFC 2819, "Remote Network Monitoring Management Information Base," provides statistics and analysis for remote LAN segments. Key Point RMON1 works at the data link layer and physical layer. It therefore provides information relating to Media Access Control (MAC) addresses and LAN traffic. RMON1 defines nine groups of statistics (ten, including Token Ring extensions, defined in RFC 1513, "Token Ring Extensions to the Remote Network Monitoring MIB") that can be implemented by RMON1 agents and that can then be requested by the network management system. The RMON1 groups are as follows:
RMON2RMON2 is defined in RFC 2021, "Remote Network Monitoring Management Information Base Version 2 using SMIv2." Key Point RMON2 is not a replacement for RMON1, but an extension to it. RMON2 adds nine more groups that provide the visibility into the upper layers. With RMON2, conversations can be viewed at the network and application layers. For example, statistics can be gathered for traffic generated by a specific application on a specific host, such as a file-transfer program. The RMON2 groups added are as follows:
RMON ExtensionsRFC 3577, "Introduction to the Remote Monitoring (RMON) Family of MIB Modules," describes RMON1 and RMON2; it also has references to various RMON extensions needed to support today's networks, including the following:
Cisco NetFlowCisco NetFlow technology allows the measurement of flows that pass through devices. Key Point A network flow is a unidirectional stream of packets between a given source and destination. A flow is very granularit can be defined by the source and destination IP addresses, source and destination port numbers, protocol type, type of service (ToS), and input interface. NetFlow has two key components:[2] the NetFlow cache, which stores the flow information, and the NetFlow export mechanism, which sends the flow data to a network management collector for data reporting. NetFlow can benefit the network in the following ways:
How does NetFlow compare with RMON? NetFlow provides more detailed information and more types of data on a per-interface basis, and can scale to include more interfaces. NetFlow has less of a performance impact than RMON and does not require external probes. SyslogCisco network devices, such as routers and switches, produce messages with the following format:
The portions of this code are described as follows:
These messages are sent to console sessions by default, but devices can be configured to send the messages to a syslog server. A syslog server is a server that runs a syslog application, a standard for logging system messages. The messages can then be retrieved and analyzed by the network manager. Note Syslog output generated by network devices is clear text, so for security purposes, it could be sent to the syslog server using an encrypted communication channel, such as a virtual private network (VPN) tunnel. This is most important when the syslog data is traversing a publicly accessible network, such as a demilitarized zone. CiscoWorksCisco has a variety of network management products; the full portfolio is listed on the Network Management Products and Services page on the Cisco website (http://www.cisco.com/en/US/products/sw/netmgtsw/index.html). CiscoWorks is the Cisco network management application. CiscoWorks is available either as stand-alone applications or as bundles of tools for specific uses. For example, the CiscoWorks LAN Management Solution (LMS) version 2.5 bundles the following components to allow the configuration, administration, monitoring, and troubleshooting of networks:[3]
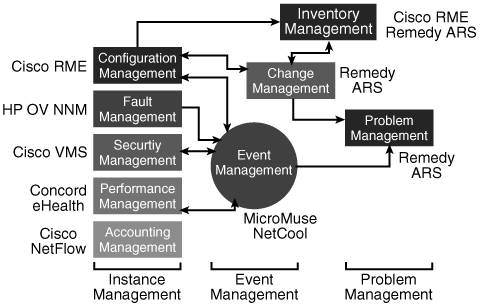
Note The components available, and those included in the various CiscoWorks bundles, change with each version; check the Cisco website for the latest information. Other ToolsIn a recent Networkers presentation, Cisco included a simplified network management framework and some of the suggested tools that would help to manage each aspect within the framework, as illustrated in Figure 9-4. Figure 9-4. Cisco Network Management Framework[4] This framework includes the five elements of the FCAPS model, as described in the "ISO Network Management Standard" section, earlier in this chapter. In addition, the following four new elements are introduced:
The tools mentioned in Figure 9-4 that we have not already introduced include the following:
A variety of other network management tools are available, many of which are also discussed in this same Networkers presentation (see http://www.cisco.com/warp/public/732/Tech/grip/docs/deploymanage.pdf). One network analysis tool available for 802.11a/b/g wireless LANs (WLANs) is Fluke's OptiView Series II Integrated Network Analyzer (http://www.flukenetworks.com/) equipped with the wireless option. Note The tools mentioned in this chapter are examples of available tools and are provided for your information only; their inclusion here does not represent an endorsement or recommendation by the authors. Another tool that can be useful for network management is the Cisco Network-Based Application Recognition (NBAR) classification software feature, running within the IOS on Cisco routers. As mentioned in Chapter 6, "Quality of Service Design," NBAR allows classification (and marking) of a wide variety of applications, including web-based and other difficult-to-classify protocols that use dynamic Transmission Control Protocol (TCP)/UDP port assignments. One more tool, specifically for managing networks of small to medium businesses (SMBs)which Cisco defines as having 250 employees or lessis the Cisco Network Assistant Windows-based management application.[5] Network Assistant can be used to manage Cisco switches, routers, access points, and IP phones, and includes configuration management, inventory reporting, password synchronization, and IOS upgrade capability. This tool also includes the Smartports Advisor, which automatically detects the type of device connected to a switch port (for example, an IP phone, a wireless access point, or a PC) and then applies Cisco's recommended best-practice configuration to the port appropriate for that device. |
EAN: 2147483647
Pages: 156