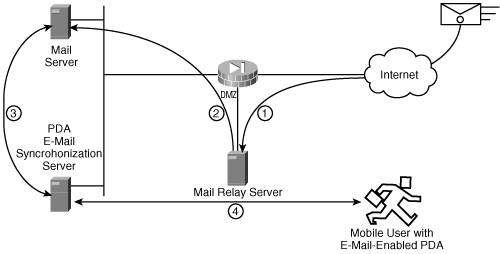
| Basic Internet e-mail security calls for the corporate mail server to not be accessible directly from the Internet. Therefore, as shown in Step 1 of Figure 12-9, incoming e-mail messages transit through the DMZ to a mail relay server. The mail relay server "sanitizes" all messages of viruses, spam, and conspicuous attachments, prior to forwarding them to the corporate mail server located on the inside network, as shown in Step 2 of Figure 12-9. This sanitizing of e-mail will be accomplished for now by software that resides on the mail relay server; a hardware-based solution will be considered in the future if the volume of e-mail warrants it. Figure 12-9. A Mail Relay Server Sanitizes Incoming E-Mail Head-Office E-MailHead office users will access their e-mail directly from the corporate e-mail server. See the "Remote User E-Mail" section for an explanation on how users will access their e-mail from home or while on business trips. In addition to accessing e-mail through their laptops, senior executives and sales staff will be provided with personal digital assistants (PDAs) to extend the benefits of corporate e-mail. As shown in Step 3 of Figure 12-9, the PDA e-mail synchronization server maintains a Messaging Application Programming Interface (MAPI) connection on the user's mailbox, and automatically synchronizes its content to the user's hand-held device, as shown in Step 4 of Figure 12-9. Branch-Office E-MailThe branch office, international offices, and remote users will access their e-mail and files through VPN connectivity back to the head-office servers, as shown earlier in Figure 12-7. Branch office users' mail software will attempt to poll the corporate mail server at its 10.0.0.0 subnet address. The branch-office router, upon seeing the request for the corporate head-office subnet, will initiate a VPN tunnel terminating at the head-office VPN concentrator (if no VPN tunnels are currently live), transiting through the firewall on its way. Remote User E-MailRemote users, whether connecting from home or from a hotel room, will require the activation of their VPN client prior to accessing the corporate e-mail server, which is located on the inside network at the head office. Most organizations do not permit their staff to simultaneously establish a VPN tunnel to the corporate head office and connect directly to the Internet. Allowing both Internet and VPN connections is known as split tunneling (as mentioned earlier) and is rarely permitted because, while the laptop's VPN session is up, that laptop would provide too much exposure to the corporate network. If split tunneling were allowed, a hacker could compromise the laptop, and then after he is inside the user's laptop, the hacker could make his way back to the corporate network through the VPN tunnel. Therefore, as long as the VPN tunnel that terminates at the head-office concentrator is up, the remote user cannot browse the Internet. |
EAN: 2147483647
Pages: 156