Lesson 2: Installing Windows 2000 Certificate Services
Lesson 2: Installing Windows 2000 Certificate Services
Windows 2000 creates a public key infrastructure (PKI) through the use of Microsoft Certificate Services, which establishes a CA on a server. In this lesson, you will learn how to install and configure a CA for use in Windows 2000 and for use with third-party PKI products.
After completing this lesson, you will be able to
-
Install Certificate Services for use in a Windows 2000 domain
-
Install Certificate Services for use in third-party PKI systems
-
Install Certificate Services as a root CA
-
Install Certificate Services as a subordinate CA
Estimated lesson time: 20 minutes
Installing Certificate Authorities
To use certificates in your organization, you must either have your own CA or request certificates from an organization that does. Because there is usually a charge associated with each certificate request from a commercial certifier, it is almost always advantageous to generate certificates locally. Furthermore, to use the advanced authentication features like smart card authentication allowed by Windows 2000 enterprise CAs, you must create your own CA.
Creating a CA in Windows 2000 is simple: install Certificate Services and answer a few questions about the type of CA you want to install. Windows 2000 supports two types of CAs:
-
Enterprise CAs are part of an enterprise-wide security infrastructure and require Active Directory.
-
Stand-alone CAs are separate from Active Directory and can issue certificates for extranet or intranet use.
When you install Certificate Services, you must determine which type of CA you intend to install. In addition, you need to determine whether you are installing a root CA, which is the topmost CA in the certification hierarchy, or a subordinate CA, which requires a CA certificate from the root CA. Your final installation decision is about which cryptographic service providers (CSPs) you will use to perform the cryptographic operations for the programming interfaces provided with Certificate Services.
Enterprise CAs
Enterprise CAs are stored in a CA object in Active Directory. Certificates are published in Active Directory, and the CA can be used to generate certificates for specific Windows 2000 purposes such as logging on using smart cards, as well as all purposes for which a stand-alone CA can be used.
Installing an enterprise CA requires the following:
-
The installing user must be a member of the Enterprise Admins group.
-
A fully-functioning, Active Directory integrated DNS infrastructure must be available.
Although enterprise CA objects are stored in the Active Directory database, the CA need not be installed on a domain controller.
Users requesting a certificate from an enterprise CA must have an Active Directory account. Certificate requests can be made through Active Directory services by applications that require them.
Requesting certificates is discussed in Chapter 6, "Managing a Public Key Infrastructure."
Stand-Alone CAs
Installing a stand-alone CA requires administrative privilege on the server. Active Directory is not required, but a stand-alone CA can make use of Active Directory if it is available. Stand-alone CAs are primarily used in situations where Active Directory services are not available, such as for public Web or e-mail services.
Stand-alone CAs can generate certificates for such purposes as exchanging public keys for SSL secure Internet connections and Secure/Multipurpose Internet Mail Extensions (S/MIME) encrypted e-mail. Certificates for stand-alone CAs can be issued and managed through a Web site that is installed during the Certificate Services installation process. This Web site is located at http://localhost/certsrv (Figure 5.5) on all machines with both Certificate Services and IIS installed. IIS must be installed for this functionality to work.
Replace localhost with the DNS name or IP address of the CA if you are not requesting the certificate from a Web browser on the local machine.
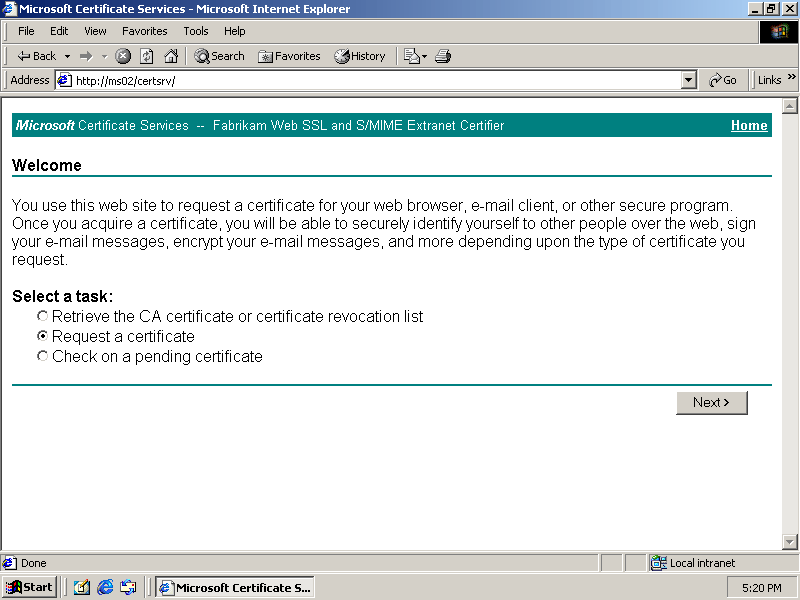
Figure 5-5. The stand-alone CA certificate management Web site
Stand-alone CAs cannot issue certificates that can be used to log on to a Windows 2000 domain.
Root and Subordinate Certificate Authorities
In addition to choosing between the two primary types of CAs, you must also determine whether your CA will be a self-certified root CA or a subordinate CA. Most organizations initially install a root CA and then use that CA to certify all other CAs in the organization. However, you might have multiple root CAs in an organization if you have multiple purposes for which transitive trust is not necessary. For example, you might have an enterprise CA used to create certificates for smart card log on, and a separate root CA for generating S/MIME e-mail encryption certificates for business partners that should not receive the same level of trust as employees.
If you choose to create a subordinate CA, you have to configure the new CA to contact an existing CA to receive its certification. Alternatively, you can finish the installation without certification and later activate the CA by installing a certificate from a parent CA. In Figure 5.6, a certificate is being requested for a subordinate CA during Certificate Services installation.
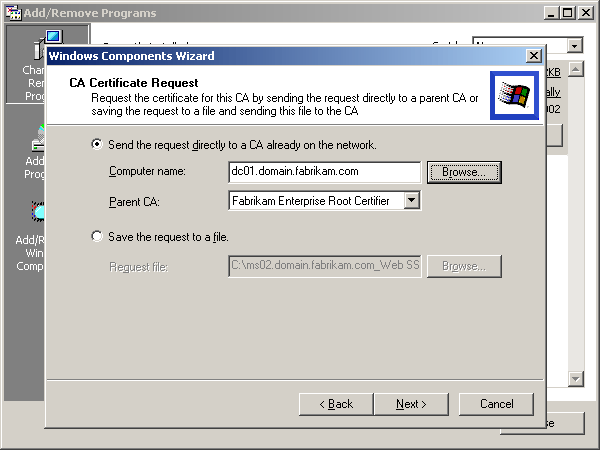
Figure 5-6. Requesting a subordinate CA certificate
Cryptographic Service Providers
The final decision you must make when installing a CA is to determine which CSP you want to use. CSPs determine which algorithms are used to generate keys, encrypt data, and digitally sign documents. The primary difference between them is the strength of their encryption algorithms.
The following list identifies the primary encryption algorithms provided by default CSPs in Windows:
-
RC2 is a secret key algorithm used for block encryption of files stored on disk.
-
RC4 is a secret key algorithm used for stream encryption of Internet connections such as SSL.
-
DES (Data Encryption Standard) is a secret key algorithm used for TCP/IP packet encryption and numerous other uses.
-
SHA-1 is used for public key encryption.
-
MD5 is used for message signing, password encryption, and digital signatures.
The length of the encryption key directly affects how long it will take to factor all possible values. Each bit of additional key length doubles the length of time (or the number of computers) required to factor the key. Currently, 64 bits is the minimum required length to remain secure for the two-year default period of a certificate if the key is being factored by a single powerful machine (defined as an Intel Pentium 4 running at 2 GHz). Currently, 1 million PC-grade computers connected by the Internet could factor an 80-bit key within two years. A 112-bit double-key DES could be factored by 4 billion PCs in the space of 130,000 years. As you can see, increasing the key length by trivial amounts dramatically improves the security of an encrypted key.
Microsoft provides three primary CSPs:
-
Base CSP provides 40-bit RC2, RC4, and 56-bit DES, with 512-bit public keys for signatures and exchanges. Base CSP was originally developed to provide a CSP that could be exported.
-
Strong CSP provides 128-bit RC2, RC4, 112-bit double key DES or 168-bit Triple DES.
-
Enhanced CSP is the same as Strong CSP with improved encryption of keys.
The Base CSP is weak and should not be used unless backward compatibility is more important than security. On standard computers, 40-bit keys can be factored in just a few days. Base CSP is also the default CSP if you do not select Advanced Options when you install Certificate Services.
Strong and Enhanced cannot generate 40-bit keys, but they are backward compatible with the Base CSP and can import 40-bit keys.
Windows 2000 is also distributed with third-party CSPs developed by other software developers for use with their security products. When you install Certificate Services, select Advanced Options in the Certification Authority Type page to see the Public And Private Key Pair page (Figure 5.7), in which you can select the CSPs.
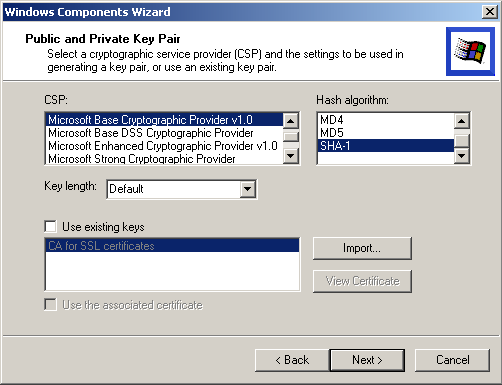
Figure 5-7. Assigning a CSP
Best Practices
Determining how to create your CA hierarchy is not difficult. The first question is whether to install as a root CA or as a subordinate to a third-party trust provider. The simple answer to this question is that, because you can always configure your root CA to trust a third party CA later, there's no reason not to install as a root CA.
The next question is whether your root CA should be a Windows 2000 Active Directory integrated enterprise CA or a stand-alone CA. Because it is easier to create a certificate hierarchy using enterprise CAs that are Active Directory integrated, your root CA should be an enterprise CA. You can always create stand-alone CAs that are subordinate to your enterprise CA, and you can always root your enterprise CA to an external stand-alone CA later if you need to.
Larger enterprises that plan to issue certificates to other business organizations may want to initially begin with a stand-alone root CA and have that CA certify an enterprise root CA. This will allow the organization to create certificates for external parties that are not trusted for enterprise use. By starting with a stand-alone CA, you can easily shut down the CA after it has certified the enterprise CA to ensure that no hacker can forge a request to the root CA to gain wide trust.
For maximum security, create a stand-alone root CA that certifies a subordinate enterprise CA that will actually be used for certificate issuance, and then turn off and store the root CA until it is needed to refresh the certificate issuer's certification or affirm certificate requests from new CAs. This methodology prevents hackers or malicious users from exploiting an administrator's account to certify their own CAs.
Finally, you need to determine how many CAs you need to install. In organizations with more than one CA, your first CA should be used only to certify other CAs. In general, your CA architecture should be somewhat analogous to your Active Directory structure, so it's common practice to install the enterprise root CA on the same machine as was used to create the Active Directory forest. Because this CA certifies only other CAs, Certificate Services does not generate much load.
Once you have an enterprise root CA, you can create CAs as necessary to keep up with the demand for certificates. By creating a first tier of CAs in the first domain level below the top of your Active Directory tree, you can determine whether the CA infrastructure is large enough to keep up easily with demand. If it cannot, you can deploy another tier of CAs at the domain level below, and continue expanding your hierarchy until you have enough CAs to keep up with the demand placed upon them.
You should always use the Microsoft Enhanced CSP unless you have a specific reason for using another CSP, such as instructions from a third-party cryptographic provider. The Enhanced CSP provides the strongest security of the Microsoft standard CSPs and is backward compatible with both the Base CSP and the Strong CSP.

In this practice, you create a CA hierarchy by first creating the enterprise root CA. You then install IIS so that you can create a stand-alone subordinate CA. For larger enterprises or those with strong security requirements, you would first create a stand-alone CA, use that CA to certify the enterprise CA, and then shut down the stand-alone root CA and continue as shown in this practice.
Exercise 1: Installing Certificate Services for an Enterprise Root CA
In this exercise, you establish an enterprise root CA. To complete this exercise, you must log on to the dc01.domain.Fabrikam.com server as a member of the Enterprise Admins group. The default Administrator account for the domain is a member of this group and can be used to complete this exercise.
To install Certificate Services
-
Click Start, point to Settings, and click Control Panel.
-
In Control Panel, double-click Add/Remove Programs.
-
In the Add/Remove Programs dialog box, click Add/Remove Windows Components. This launches the Windows Components Wizard.
-
In the Windows Components Wizard, select the check box for Certificate Services. A Microsoft Certificate Services message box appears.
-
Click Yes to acknowledge the warning that the computer cannot be renamed or have its domain affiliation changed once Certificate Services is installed.
-
Click Next.
If you have Terminal Services installed, the Terminal Services Setup page will appear in the wizard. Click Next to accept the default Terminal Services remote administration mode and continue.
-
The Certificate Authority Type page (Figure 5.8) appears. Select Enterprise Root CA, select Advanced Options, and click Next.
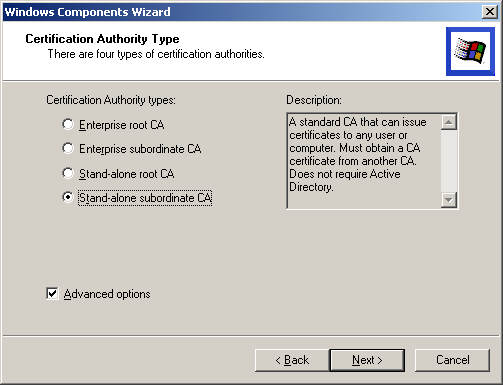
Figure 5-8. Selecting the CA type
-
The Public And Private Key Pair page (Figure 5.7) appears. Select Microsoft Enhanced Cryptographic Provider as the CSP, and click Next.
-
In the CA Identifying Information page (Figure 5.9), Type Fabrikam Enterprise Root Certifier in the CA Name box.
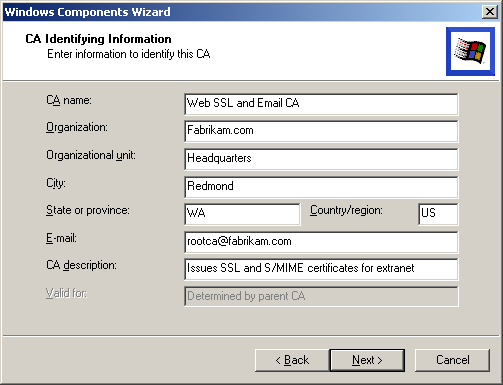
Figure 5-9. The CA Identifying Information page
-
Type Fabrikam, Inc. in the Organization box.
-
Type Redmond in the City box.
-
Type WA in the State box.
-
Type US in the Country/Region box.
-
Type rootca@fabrikam.com in the E-mail box.
-
Type Fabrikam Root Certifier in the CA Description box.
-
Leave the 2 year default duration, and click Next. The Data Storage Location page appears.
-
Ensure that you have placed the Windows 2000 Server installation CD in your CD-ROM drive. To identify where the CA's files will be stored, leave the default setting for the Certificate Database and Certificate Database Log, and click Next.
-
If IIS is running, a message box appears stating that the service must be stopped before proceeding. Click OK to stop IIS and continue.
The service will now generate cryptographic certificates and copy the files necessary for the certificate service from your CD-ROM drive.
Make sure you use a storage location that is backed up on a regular basis.
-
Click Finish. Certificate Services is now installed on your server.
-
Click Close to close the Add/Remove Programs window.
-
Close Control Panel.
You can use this procedure to create a stand-alone root CA by selecting Stand-alone Root CA in this page. All other options are the same.
Exercise 2: Installing Certificate Services for a Stand-alone Subordinate CA
In this exercise, you install a stand-alone CA that is subordinate to the previously installed enterprise CA. For this functionality to work, you must install IIS. You must then install the CA on a member server in the domain.Fabrikam.com domain. The procedure for installing a stand-alone CA is very similar to installing an enterprise CA. If IIS is already installed, you can skip this procedure.
To install a stand-alone subordinate CA
-
Click Start, point to Settings, and then click Control Panel.
-
Double-click Add/Remove Programs.
-
In the Add/Remove Programs window, click Add/Remove Windows Components. This launches the Windows Components Wizard.
-
In the Windows Components Wizard, select Certificate Services. A Microsoft Certificate Services message box appears.
-
Click Yes to acknowledge the warning that the computer cannot be renamed or have its domain affiliation changed once Certificate Services is installed.
-
Click Next.
If you have Terminal Services installed, the Terminal Services Setup page will appear. Click Next to accept the default Terminal Services remote administration mode and continue.
-
In the Certificate Authority Type page (Figure 5.8), select Stand-alone Subordinate CA, select Advanced Options, and click Next.
-
In the Public And Private Key Pair page (Figure 5.7), select Microsoft Enhanced Cryptographic Provider as the CSP, and click Next.
-
In the CA Identifying Information page (Figure 5.10), type Fabrikam Web SSL and S/MIME Extranet Certifier in the CA Name box.
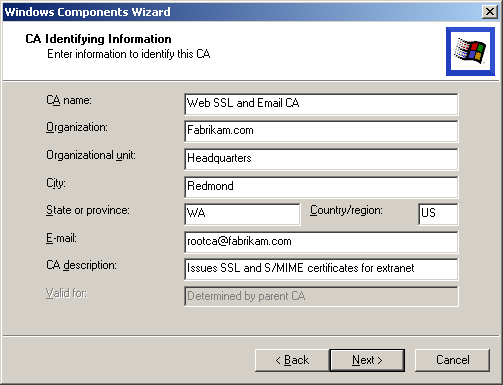
Figure 5-10. Certificate Identity Information is embedded in the certificate
-
Type Fabrikam, Inc. in the Organization box.
-
Type Redmond in the City box.
-
Type WA in the State box.
-
Type US in the Country/Region box.
-
Type rootca@fabrikam.com in the E-mail box.
-
Type Issues SSL and S/MIME certificates for extranet in the CA Description box, and click Next.
-
Leave the default certificate database and log settings as they are. The Data Storage Location page appears.
-
Select Store Configuration Information In A Shared Folder to identify where the CA's files will be stored.
-
Type C:\CAConfig as the name of the shared folder, and click Next.
-
The Root CA selection dialog box appears. Click Browse, select Fabrikam Enterprise Root Certifier, and click OK. The Root CA selection dialog box now appears as shown in Figure 5.11.
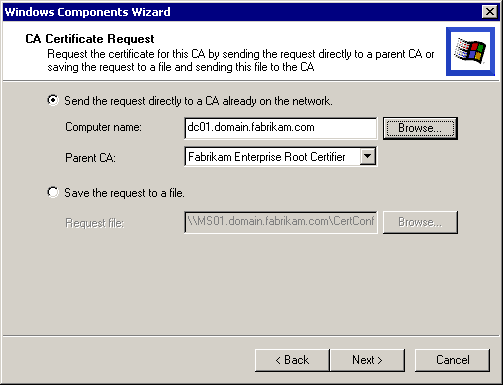
Figure 5-11. The Root CA selection dialog box
-
In the Root CA selection dialog box, click Next. A message box appears asking whether you want to stop IIS. Ensure that you have placed the Windows 2000 Server installation CD in your CD-ROM drive. Click OK to stop IIS.
The service generates cryptographic certificates and copies the files necessary for the Certificate Service from your CD-ROM drive.
-
Click Finish. Certificate Services is now installed on your server.
-
Click Close to close the Add/Remove Programs dialog box.
-
Close Control Panel.

The following questions are intended to reinforce key information in this lesson. If you are unable to answer a question, review the lesson and try the question again. Answers to the questions can be found in the appendix.
-
What is the strongest standard CSP provided by Microsoft?
-
How are certificates normally requested from a stand-alone CA?
-
What is the primary difference between an enterprise CA and a stand-alone CA?
-
How many certificate authorities can a single server host?
Lesson Summary
-
Stand-alone CAs can be used to generate SSL, S/MIME, and other types of Internet standard certificates. Certificates from stand-alone CAs are requested through the certificate services Web site on the server that hosts the CA.
-
Enterprise CAs have all the functionality of stand-alone CAs and can also generate certificates for use within a Windows 2000 domain for purposes such as logging on using a smart card. Active Directory account holders can request certificates through enterprise CAs.
-
CAs can be either self-certifying, stand-alone CAs, or subordinate to another CA. The top CA in any organization's CA hierarchy can be configured as a subordinate to a third-party trust provider. To configure a CA as a subordinate CA, you can select the parent CA from the Active Directory list if the server is a member of the domain, or request and install the CA certificate manually.
-
CAs can use different CSPs to change the algorithms and key lengths used for the various certificate encryption functions. The Microsoft Enhanced CSP provides the best quality of encryption for most purposes and is backward compatible with the Base CSP and the Strong CSP.
EAN: 2147483647
Pages: 82