Introduction to Front-endBack-end Arrangements
| < Day Day Up > |
Introduction to Front-end/Back-end ArrangementsBy default, Exchange Server 2003 installs OWA and Outlook Mobile Access (OMA) in the Exchange organization. Although OWA and OMA can be used quite effectively internally within an organization to enable non-Windows-based clients to access Exchange mailboxes, their primary purpose is to allow users to access their Exchange mailboxes when away from the network. A typical example of a user using OWA might be a manager who is on vacation, but still needs to monitor his email daily to ensure that any items requiring his attention are taken care of promptly. Given that the primary intended purpose of OWA (and OMA) is to provide Exchange mailbox access to users located outside of your protected internal network, some additional considerations must be given to creating and implementing a secure and highly available solution. Enter the concept of front-end/back-end Exchange servers. If you've ever worked with Network Load Balancing (NLB) or clustering, you are probably familiar with this concept. If not, a short introduction (with an emphasis on the Exchange specifics of the topic) is in order.
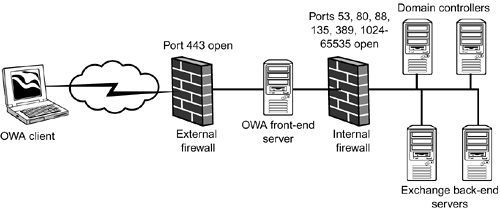
Figure 6.23 depicts a sample front-end/back-end Exchange implementation designed to support only OWA using SSL-secured connections. Figure 6.23. A front-end/back-end Exchange server configuration should be used to provide increased security and reliability.
Notice on the external firewall that only port 443 is open HTTP over SSL. Inbound OWA client requests are passed to the front-end Exchange servers. These servers then communicate with the back-end Exchange servers, performing authentication of the user and making the user's mailbox available to them via OWA. Notice that several ports are open on the internal firewall. These ports are
To further increase network security, you can implement IPSec secured communications between the front-end and back-end Exchange servers. |
| < Day Day Up > |
EAN: 2147483647
Pages: 171