Public Key Cryptography
| |
A secure and simple method of encrypting and decrypting electronic information.
It's been said time and again that Internet commerce won't be viable until tighter security measures are in place and consumers have confidence in them. But on a more basic level, securing computer files and e-mail is of much more concern to users on an everyday basis. After all, if you lose your laptop, your competition can potentially access the sensitive information you were carrying. Also, transferring files back and forth over the Internet or even through proprietary mail systems can present risks if the information is intercepted. To foil the plans of anyone trying to usurp electronic files, many have turned to cryptography, which encrypts and decrypts information such that it's useless to everyone except authorized users.
Traditional cryptosystems are based on the secret key, or symmetric, model (see Figure 1). In this system, each user has his or her own secret key, which is used for both encryptionin which plaintext is converted to ciphertext and decryptionin which the process is reversed .
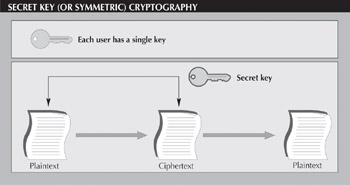
Figure 1: Secret key, or symmetrical cryptosystems, rely on a single key for all encryption and decryption between parties, which means these systems are fast, but can be easily compromised if the key is lost.
An example of a secret key cryptosystem is the data encryption standard (DES), which was originally developed by IBM and endorsed by the U.S. government in 1977. DES uses a 56-bit key and has a 64-bit block size . The encryption process works on one block of data at a timein this case, 64 bitsthen proceeds to process the next block.
Other symmetric cryptosystems include RC2 and RC4, both of which use variable key lengths and operate on 64-bit blocks of data. RC2 and RC4 were developed by RSA Data Security.
The larger the key size, the more complex the algorithm and the more difficult the cryptosystem is to crack. Within the United States, the sky's the limit in terms of key size, with many organizations going with key sizes as large as 1,024 bits. Currently, however, only keys of 40 or fewer bits can be exported, although this is currently under debate and could change in the near future.
Because secret key cryptosystems rely on a single key for both encryption and decryption, making sure all parties involved have the key, without it being intercepted, becomes a problem. Handing out the key on a disk is a relatively reliable way to go, but even that method can be uncertain .
To avoid having to place trust in a third party and to decrease the possibility of secret keys falling into the wrong hands, a new type of system, public key cryptography, was developed.
Public Property
The recognized pioneers in the field of public key cryptography are Whitfield Diffie and Martin Hellman, two researchers whose Diffie-Hellman algorithm was developed in 1976 at Stanford University. Just about a year later, Ron Rivest, Adi Shamir, and Leonard Adleman (the founders of RSA Data Security) invented another public key cryptosystem known as RSA.
Under the public key cryptography model, each user has a pair of keys that are complementary and mathematically related . The keys are generated by a mathematical algorithm that involves very large prime numbers . With a public key system, information encrypted with a particular public key can be decrypted only by using the corresponding private key.
You can hand out your public key to each recipient you communicate with; alternatively, you may choose to post your public key at some central location or on a network directory, so anyone can look it up. To see a working public key directory, visit Pretty Good Privacy's Web site at www.pgp.com. By contrast, you keep your private key, and you should take care to store it in a safe, secure place, whether on a floppy disk or a secured hard drive.
When you want to securely communicate information to another party, you must first generate a key pair, if you don't already have one. Each company's policy on key generation is different, but generally , either each user can generate a key pair using key generation software, or a central authority, such as someone who oversees a company's security policy, creates key pairs for all users.
Once keys have been created, they can be used to send information through e-mail, for example. You first look up the public key of the recipient or have the recipient send the public key directly to you. You then apply the recipient's public key to the plaintext, or unencrypted, message and create a ciphertext, or encrypted, message, which is then sent to the intended recipient. The recipient applies his or her private key to the ciphertext to transform it back to readable plaintext (see Figure 2).
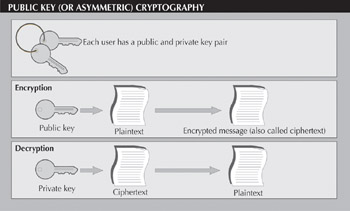
Figure 2: The use of two mathematically related keys, public key, or asymmetrical cryptosystems, makes messages very hard to crack. The public key can be posted at a central location, while the corresponding private key is kept by the individual at all times.
Because Internet mail travels through numerous unknown servers to reach its final destination, it can be intercepted along the way by those with the know-how. However, unless these e-mail hijackers can provide the appropriate private key, all they will see is gobbledygook.
Signed, Sealed, Delivered
Even though RSA is largely based on Diffie-Hellman, there are several differences between these two schemes of public key cryptography. The Diffie-Hellman model was designed to require a dynamic key exchange between sender and receiver, usually for each session. While this process presents more of a challenge for potential attacks, it also requires a lot of communications overhead.
By contrast, RSA enables each user to have an unchanging key pair, no matter whom the communication is with. The two parties need never actually exchange keys; instead they can post their public keys in a public place, such as a server that can be readily accessed by anyone on the network.
Because Diffie-Hellman requires this dynamic key exchange each time, the keys are susceptible to interception and substitution by a third party, preventing senders and receivers from authenticating one another's identities.
RSA allows a sender to attach a digital signature to a message to show whom the message is from and to ensure the message has not been tampered with during transit. To do this, the sender takes a secure hash function and applies it to the message, which results in a message digest that identifies that message. A hash function is the result of an input of any size that becomes mathematically transformed into a string of a fixed size. The message digest, which represents the message and can be used to detect changes in the message, is then encrypted with the sender's private key, which results in a digital signature. The message digest and message itself are then routed to the appropriate recipient.
The recipient uses the sender's public key to decrypt the digital signature and see the message digest. Next, the recipient applies to the message the same hash function the sender used, and the hash function is then compared with the decrypted message digest. The signature is verified if both are the same. If, for some reason, they are not the same, the message either didn't come from the supposed sender or it has been changed in transit. This process is similar to when a store clerk compares your handwritten signature on a credit card sales slip with the signature on the credit card itself.
In addition to RSA's algorithm for creating a digital signature, the U.S. government has its own standard, the Digital Signature Standard (DSS). DSS uses the Secure Hash Algorithm, which converts a message into a 160-bit hash of the message. The hash value, which is, in essence, the contents of the message, is combined with the sender's private key, resulting in a digital signature. DSS employs the Digital Signature Algorithm, which takes the hash value and the private key and generates a 320-bit signature from the two.
In some instances, a digital signature is simply not enough. Although it ensures the message hasn't been altered in transit and it shows the signature of the sender, unless you know the sender, there really is no way to prove that the sender really is the person he or she claims to be. To provide further proof of identity, you can register your public key with a Certificate Authority (CA), an in-house or third-party group that verifies information about the person who holds a particular set of keys and then issues a digital certificate. Consider the certificate as similar to what a notary public issues to vouch for and verify the validity of a paper-based document. When this digital certificate is applied to an encrypted message, the recipient knows for sure the message did indeed come from the sender.
As we've seen, public key cryptography has several advantages over secret key cryptography. First, half of the cryptographic scheme (private keys) is never divulged, thereby increasing security. Also, public key cryptography allows for digital signatures, which enable sender and recipient to feel more confident about communicating with one another. Public key cryptography also has its drawbacks, most notably the fact that it's much slower than the secret key models. Because both types of cryptography have plenty of pros and cons, a combination of the two methods may be the most practical solution for electronic communications. You could encrypt private files, such as those on a hard drive, using the secret key method because technically those files aren't communicated to others. Then, for environments in which many people potentially have access to information, such as e-mail, you could use public key cryptography to secure information.
Whatever you choose, remember that the rapid growth of the Internet also extends invitations to unwanted hackers who will try to intercept messages and break into your network. Some form of cryptography, whether it's secret key or public key, will keep the wolves at bay.
Resources
For an informative 10-part cryptography FAQ listing, visit www.cis.ohio-state.edu/hypertext/faq/usenet/cryptography-faq/top.html.
For a comprehensive look at cryptography, which includes a search engine, see www.rsa.com/rsalabs/newfaq.
This tutorial, number 104, by Anita Karv was originally published in the April 1997 issue of LAN Magazine/Network Magazine.
| |
EAN: 2147483647
Pages: 193