Liberty Alliance Architecture
| The initial proposal of Liberty Alliance includes the following stages:
There are three key actors in a Liberty-enabled single sign-on business scenario: User Agent (User, security agent), Service Provider (provider of services to users), and Identity Provider (provider for identifying user identity). The following describe these actors and their relationship.
RelationshipsService providers are affiliated with an identity provider into circles of trust based on Liberty-enabled technology and on operational requirements that define trust relationships among themselves. In addition, users federate their accounts (also known as local identities) with these service providers so that the same user identity can link to multiple accounts under different service providers. Under the mutually trusted environment, if a user authenticates with the identity provider, these service providers will honor the authentication. Such a business relationship is also known as "Circle of Trust." Figure 7-4 summarizes the Liberty concept in the use of cross-domain Single Sign-on and depicts the following interactions:
Figure 7-4. Liberty's logical architecture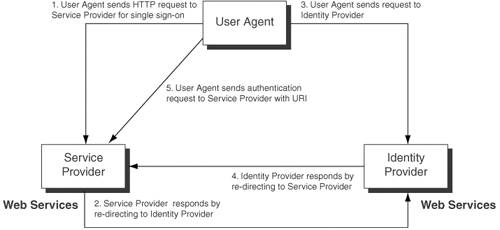 Web RedirectionWeb Redirection refers to actions that enable Liberty-enabled entities to provide services via user agents. It has two variants: HTTP-redirect-based redirection and Form-POST-based redirection. HTTP-redirect-based redirection uses HTTP redirection and the syntax of URIs to provide a communication channel between identity providers and service providers. For instance, the user clicks a link in the Web page displayed in the user agent. The user agent sends an HTTP request of resource access to the service provider using HTTP GET. The service provider responds with an HTTP response with a status code 302 (HTTP redirect) and an alternate URI (identity provider URI such as http://www.myidentityprovider.com/auth) in the Location header field. Then the user agent sends an HTTP request to the identity provider, and the identity provider can then respond with a redirect that specifies the service provider URI in the Location header field. Finally, the user agent sends an HTTP request to the service provider using HTTP GET with the complete URI from the identity provider's Location header field. The flow of events in form-POST-based redirection is similar to the HTTP-redirect-based redirection, except that the service provider responds with an HTML form to the user agent with an action parameter pointing to the identity provider and a method parameter with the value of POST. The user needs to click on the Submit button, which sends the form and the data contents to the identity provider using HTTP POST. Web ServicesWeb services here refer to business services provided by service providers using SOAP protocol profiles that enable Liberty-enabled entities to communicate to each other. Liberty currently supports RPC-style SOAP Web services. Meta-Data and SchemasMeta-data and schemas refer to a common set of classes of information and their formats that are exchanged between service providers and identity providers. They include user account identity information, authentication context (supporting a variety of authentication methods), and provider meta-data (meta-data schemas that need to be exchanged prior to exchanging authentication information, such as X.509v3 certificates and service endpoints). Security MechanismsThe Liberty ID-WSF specification defines security mechanisms that address the use-case scenarios intended for identity-based Web services. It mandates that the Liberty-provider implementation include security mechanisms that address the following requirements in order to secure the exchange of identity information between the applications and participants. The security mechanisms must address the following key requirements:
In the Web redirection scenario, Liberty suggests the use of HTTPS for exchanging identity information and authentication assertions. This provides a secure transport mechanism between service providers and identity providers. In addition to the underlying secure transport, Liberty relies on strong authentication mechanisms used by the identity provider. Using cookies to maintain the local session state is often abused by unauthorized Web sites and hackers. If developers use cookies to persist identity and authentication information, it is possible that once a user exits the Web browser, another user may re-launch the Web browser using the same system, which may result in impersonating the first user. Using Web redirection and URL rewriting, identity providers do not need to send business data to service providers via cookies. For details of the Liberty security mechanisms, please refer to [LibertyIDWSF]. |
EAN: 2147483647
Pages: 204
- Command Reference
- Command Reference
- Command Reference
- Case Study 2: Implementing Multi-VRF CE, VRF Selection Using Source IP Address, VRF Selection Using Policy-Based Routing, NAT and HSRP Support in MPLS VPN, and Multicast VPN Support over Multi-VRF CE
- Case Study 4: Implementing Layer 3 VPNs over Layer 2 VPN Topologies and Providing L2 VPN Redundancy