Exam 70-124: Objective 3.3.1, 3.3.3: Configuring Windows Client Computers for Wireless LAN Security
|
|
Wireless LAN security is provided through myriad solutions. Some of these mechanisms are internal to Windows itself; others are third-party solutions or part of the IEEE 802.11 standard. In this section, we focus primarily on using WEP and 802.1x-based security on Windows 2000 Professional and Windows XP Professional computers. Whatever security mechanism you decide to implement, you must ensure that you are diligent about getting it done right. There is rarely a second chance for security, especially when it comes to securing a wireless LAN.
Windows XP Professional
Windows XP has been hailed as the operating system of choice for wireless LAN users. Whatever your feelings are about this popularity, it is a fact that Windows XP brings to the mainstream excellent support for 802.1lb wireless networks and 802.1x security. The only flaw in Windows XP's solution is that it takes the majority of control away from a user. Sometimes this can be a good thing, though. Configuring WEP and 802.1x security on a Windows XP Professional computer is outlined in Exercise 7.01.
Exercise 7.01: Enabling WEP and 802.1x Security in Windows XP Professional
-
Click Start | Settings | Control Panel | Network Connections.
-
Double-click your wireless LAN connection.
-
Click the Properties button and switch to the Wireless tab, as shown in Figure 7.6.
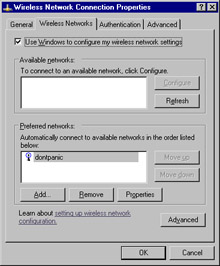
Figure 7.6: The Wireless Tab -
To configure a new connection, click Add. Configure all required information, including the WEP key, as shown in Figure 7.7.
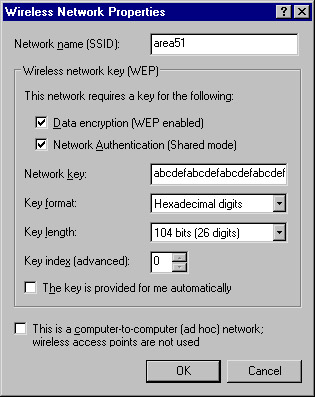
Figure 7.7: Configuring a New Connection -
If your network uses a dynamic keying server, you need only select The key is provided for me automatically instead of specifying the WEP key specifics.
-
Click OK when you have entered all the required information.
-
To configure 802.1x security on the network connection, change to the Authentication tab, as shown in Figure 7.8.
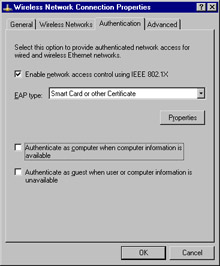
Figure 7.8: Configuring 802.1x Security -
Select Enable network access control using IEEE 802.1x. Select your EAP type from the drop-down list. Most commonly, your EAP type will be Smart Card or other Certificate. By clicking Properties (see Figure 7.9) you can configure the certificate and CA to be used for this authentication.
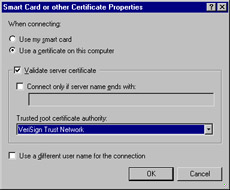
Figure 7.9: Configuring the Certificate Properties -
For increased security, ensure that the Authenticate as computer when computer information is available and Authenticate as guest when user or computer information is unavailable options are not selected. Click OK to accept the settings.
Windows 2000 Professional
Windows 2000 provides none of the built-in niceties for wireless networking that Windows XP provides. It also doesn't take control of your wireless network connection. All configuration and security are the user's job. Exercise 7.02 outlines the process to enable WEP for a wireless network connection in Windows 2000 Professional.
Exercise 7.02: Enabling WEP in Windows 2000 Professional
-
Click Start | Settings | Control Panel | Network Connections.
-
Double-click your wireless LAN connection.
-
Click the Properties button. Notice that the Wireless and Authentication tabs do not show up in Windows 2000, as shown in Figure 7.10.
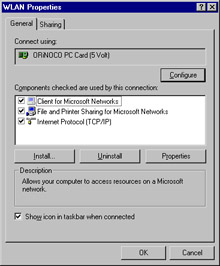
Figure 7.10: Windows 2000 Network Adapter Properties -
Close the network adapter Properties window.
-
Configure a wireless LAN connection profile using your WLAN network adapter client utility, such as the ORiNOCO Client Manager or the Cisco ACU. We use an ORiNOCO network adapter for this example.
-
Open the Client Manager and click Actions | Add/Edit Configuration Profile, as shown in Figure 7.11.
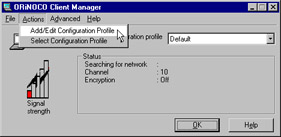
Figure 7.11: Configuring a New Profile -
Click Add to start the process of creating a new profile.
-
Enter the Profile Name and Network Type, as shown in Figure 7.12, and click Next.
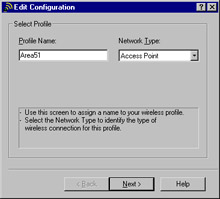
Figure 7.12: Specifying a New Profile -
Enter the Network Name and click Next. This is the SSID of the network.
-
Select Enable Data Security and enter your WEP key or keys, as shown in Figure 7.13. Click Next to continue.
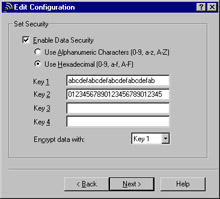
Figure 7.13: Configuring the WEP Properties -
Configure the power management function you want and click Next.
-
Configure to renew the IP address of the network adapter upon connecting as desired and click Next.
Exam 70-124: Objective 3.3: Additional Security Measures for Wireless LANs
Although 802.1x authentication provides good security through the use of dynamically generated WEP keys, security administrators might want to add more layers of security. Additional security for wireless networks can be introduced through the design of the network itself. As we stated previously, a wireless network should always be treated as an untrusted network. This fact has implications for the design and topology of the wireless network.
| Test Day Tip | The extra security measures and best practices discussed over the next several pages are presented for your reference should you find yourself faced with the task of implementing a wireless network. Don't expect to be directly tested on any of this material during your exam. |
Using a Separate Subnet for Wireless Networks
Many wireless networks are set up on the same subnets as the wired network. Furthermore, to make life easier for administrators and users alike, both wired and wireless clients are often configured as DHCP clients and receive IP address configurations from the same DHCP servers. There is an obvious security problem with this approach. This configuration makes it easy for hackers to acquire valid IP address configurations that are on the same subnet as the corporate networks, posing a significant threat to network security.
The solution is to place wireless access points on their own separate subnets, creating, in effect, a kind of DMZ for the wireless network. The wireless subnet could be separated from the wired network by either a router or a full-featured firewall, such as ISA Server. This approach has a number of advantages. When the wireless network is placed on a separate subnet, the router can be configured with filters to provide additional security for the wireless network. Furthermore, through the use of an extended subnet mask on the wireless network, the number of valid IP addresses can be limited to approximately the number of valid wireless clients. Finally, in the case of potential attack on the wireless network, you can quickly shut down the router and prevent any further access to the wired network until the threat has been removed.
If you have to support automatic roaming between wireless zones, you will still want to use DHCP on the wireless subnets. However, if you don't need to support automatic roaming, you might want to consider not using DHCP and manually configuring IP addresses on the wireless clients. This solution will not prevent a hacker from sniffing the air for valid IP addresses to use on the wireless subnet, but it will provide another barrier for entry and consume time. Additionally, if a hacker manually configures an IP address that is in use by another wireless client, the valid user will receive an IP address conflict message, providing a crude method for detecting unauthorized access attempts.
Using VPNs for Wireless Access to Wired Networks
In high-security networks, administrators might want to leverage the separate subnet by only allowing access to the wired network through a VPN configured on the router or firewall. In order for wireless users to gain access to the wired network, they would first have to successfully authenticate and associate with the AP and then create a VPN tunnel for access to the wired network.
Some vendors, such as Colubris, offer VPN solutions built into wireless devices. These devices can act as VPN-aware clients that will forward only VPN traffic from the wireless network to the wired network, or they can provide their own VPN server for wireless clients. However, it is not necessary to use a proprietary hardware-based solution. One solution is to use a freeware solution known as Dolphin from www.reefedge.com that will turn a PC into an appliance that will encrypt wireless traffic with IPSec.
| Note | For more information on this technology, see www.colubris.com/en/support/whitepapers. |
When a VPN is required for access to the corporate network from the wireless network subnet, all traffic between the two networks is encrypted within the VPN tunnel. If you are using static WEP, a VPN will ensure a higher degree of confidentiality for your traffic. Even if the WEP encryption is cracked, the hacker would then have to crack the VPN encryption to see the corporate traffic, which is a much more difficult task. If a wireless laptop is stolen and the theft unreported, the thief would have to know the laptop user's credentials to gain access to the VPN.
| Note | It is important to ensure that the user doesn't configure the VPN connection to save the username and password. Although this makes it more convenient for the user, who doesn't have to type the account name and password each time he or she uses the VPN connection, it provides a thief with the credentials needed to access the VPN. |
Of course, this kind of configuration is still vulnerable to attack. If, for example, the attacker has somehow acquired usernames and passwords (or the user has saved them in the VPN connection configuration), the hacker can still access the wired network through the VPN. Another consideration is the additional overhead of encryption used in the VPN tunnel. If you are also using WEP, the combined loss of bandwidth as a result of the encryption could easily be noticeable. Again, administrators will have to compare the benefits of implementing a VPN for wireless clients in a DMZ against the cost of deployment in terms of hardware, software, management, loss of bandwidth, and other factors.
Setting up this kind of configuration can be a relatively complex undertaking, depending on a number of factors. If, for example, you are using 802.1x authentication, you might have to ensure that 802.1x-related traffic can pass between the wireless and wired networks without a VPN tunnel. If you are using ISA Server to separate the networks, you would have to publish the RADIUS server on the corporate network to the wireless network. You can find information on setting up ISA Server for this kind of configuration throughout this book.
Temporal Key Integrity Protocol
As we noted earlier, the use of WEP, even in combination with 802.1x authentication and EAP-TLS, provides a much higher standard of security but does not mitigate all the potential threats to the confidentiality and integrity of the data. As an interim solution, until the IEEE 802.11i standard is implemented and finalized, many vendors are using or considering using a temporary solution called Temporal Key Integrity Protocol (TKIP) to enhance the security of wireless networks. The TKIP standard has been accepted by the Wi-Fi Alliance for inclusion in 802.11b Wi-Fi certified devices and is being called Wi-Fi Protected Access, or WPA. Cisco has been using TKIP for some time now in its Aironet line of products.
TKIP can be used with or as an alternative to 802.1x authentication. TKIP comprises a set of algorithms that enhance WEP. It provides more security than WEP through the use of key mixing, an extended IV, a message integrity check (MIC), and rekeying. A primary advantage of TKIP is that it can be implemented through firmware updates of current devices (another reason that you should only purchase devices capable of firmware updates). TKIP addresses the problem of static WEP keys by frequently changing the temporal key used for the encryption process every 10,000 packets.
Additionally, the use of TKIP addresses another vulnerability of static WEP: the use of the same shared key by all the wireless devices. TKIP ensures that each wireless station uses a different key for the encryption process. TKIP accomplishes this task by using a 128-bit temporal key that is shared between the wireless workstations and the AP. The temporal key is then combined with the MAC address of each of the wireless devices to provide the encryption key used for RC4 encryption on the wireless network by that device. This also adds another layer of encryption to reduce the vulnerability to attacks based on the fact that the IV is sent in the clear in standard WEP implementations.
Message Integrity Code
Another vulnerability of WEP is that it is a relatively easy matter for a knowledgeable and determined attacker to modify (flip) bits in an intercepted message, recalculate the appropriate CRC (also known as the integrity check value, or ICV), and then send the altered message to the AP. Because the CRC is spoofed, the AP will accept the altered message and reply to it, providing information that the attacker could use to crack the WEP encryption. This form of attack was described in a paper, Intercepting Mobile Communications: The Insecurity of 802.11, by Nikita Borisov, Ian Goldberg, and David Wagner.
MIC, which is also part of the TKIP algorithms, provides a much stronger mechanism for checking the message for evidence of tampering by adding a MIC value that is encrypted and sent with the message. When the message is received, the MIC value is decrypted and compared with the expected value. MIC is, in reality, a form of Message Authentication Code, often referred to as MAC, which is a standard cryptographic term. However, because the acronym MAC is already used quite frequently with regard to wireless networks in regard to the Media Access Control address, MIC is used to differentiate the two.
| Note | To add to the confusion, MIC is variously referred to as message integrity code or message integrity check. As with TKIP, MIC is a technology originally developed by Cisco (which uses the term check) for use in its products and is not widely available at the time of this writing. |
The IEEE 802.11i Standard
The negative response to WEP's weaknesses has been vociferous and strong. To address the criticisms leveled at WEP and to provide a stronger standards-based security mechanism that vendors can implement in their products, the IEEE 802.11i task group is working on the upcoming 802.11i standard.
Although the standard is not finalized, some things about its final form are fairly certain. The standard will combine into a single, coherent standard the best of the available technologies for securing wireless networks. The following are expected to be included in the standard:
-
The 802.11i standard will require the use of 802.1x authentication based on EAP.
-
The 802.11i standard will also likely require the use of TKIP and MIC.
-
For new devices, the standard will also require the use of Advanced Encryption Standard (AES) as a replacement for the compromised RC4 algorithm.
AES provides much stronger encryption than RC4. However, because of the additional processing power required for AES encryption, the addition of a coprocessor in the hardware of wireless devices will likely be necessary. When this technology becomes available in the marketplace, replacing legacy wireless devices could result in a significant expenditure. As with all other security measures, administrators and managers will have to compare the costs of implementation against the threats the implementation will mitigate.
Exam 70-124: Objective 3.3: Implementing Wireless LAN Security: Common Best Practices
As we have seen from the previous discussion, wireless security is a large, complex topic. Administrators who want to implement wireless networks should exercise due care and due diligence by becoming as familiar as they can with operation and vulnerabilities of wireless networks and the available countermeasures for defending them. Installing a wireless network opens the current wired network to new threats. The security risks created by wireless networks can be mitigated, however, to provide an acceptably safe level of security in most situations.
In some cases, the security requirements are high enough that the wireless devices require proprietary security features. This might include, for example, the ability to use TKIP and MIC, which is currently only available on some Cisco wireless products but might become available on other products in the near future. In many cases, however, standards-based security mechanisms that are available on wireless products from a wide range of vendors are sufficient.
Even though many currently implemented wireless networks support a wide range of features that can potentially be enabled, the sad fact is that most administrators do not use them. The media is full of reports of the informal results of site surveys conducted by war drivers. These reports provide worrisome information—for example, that most wireless networks are not using WEP and that many wireless networks are using default SSIDs. Many of these networks are located in technology-rich areas such as Silicon Valley, where you would think people would know better, making the information a potential source of serious concern.
There is really no excuse for not minimizing the security threats created by wireless networks through the implementation of security features that are available on most wireless networks. The following is a summary of common best practices that could be employed now on many current or future wireless networks:
-
Carefully review the available security features of wireless devices to see if they fulfill your security requirements. The 802.11 and Wi-Fi standards specify only a subset of features that are available on a wide range of devices. Over and above these standards, there is a great deal of divergence among supported features.
-
At a minimum, wireless access points and adapters should support firmware updates, 128-bit WEP, MAC filtering, and the disabling of SSID broadcasts.
-
Wireless vendors are continually addressing the security weaknesses of wireless networks. Check the wireless vendors' Web sites frequently for firmware updates and apply them to all wireless devices. You could leave your network exposed if you fail to update even one device with the most recent firmware.
-
In medium- to high-security environments, wireless devices should support EAP-based 802.1x authentication and, possibly, TKIP. Another desirable feature is the ability to remotely administer the wireless AP over a secure, encrypted channel. Being able to use IPSec for communications between the AP and the RADIUS server is also desirable.
-
Always use WEP. Although it is true that WEP can be cracked, doing so requires knowledge and time. Even 40-bit WEP is better than no WEP.
-
Always rotate static WEP keys frequently. If this is too great an administrative burden, consider purchasing devices that support dynamic WEP keys.
-
Always change the default administrative password you use to manage the AP. The default passwords for wireless APs are well known. If possible, use a password generator to create a difficult and sufficiently complex password.
-
Change the default SSID of the AP. The default SSIDs for APs from different vendors are well known, such as tsunami and Linksys for Cisco and Linksys APs, respectively. A fairly inclusive listing of default SSIDs can be found at www.area51partners.com/files/SSID.txt.
-
Do not put any kind of identifying information in the SSID, such as your company name, address, products, divisions, and so on. If you do so, you provide too much information to potential hackers and let them know whether your network is of sufficient interest to warrant further effort.
-
If possible, disable SSID broadcasts. This will make your network invisible to site survey tools such as NetStumbler. However, disabling SSID broadcasts will cause an administrative burden if you are heavily dependent on Windows XP clients being able to automatically discover and associate with the wireless network.
-
If using DHCP for your wireless clients, strongly consider the use of a separate DHCP scope and subnet for wireless clients. In this way you can lock wireless clients into a specific subnet. Wireless clients should always be treated as untrusted and placed in a controlled environment, such as DMZ, if possible.
-
Do not use shared-key authentication. Although it can protect your network against specific types of DoS attacks, it allows other kinds of DoS attacks. Shared-key authentication exposes your WEP keys to compromise.
-
Enable MAC filtering. It's true that MAC addresses can be easily spoofed, but your goal here is to slow potential attackers. If MAC filtering is too great an administrative headache, consider using port-based authentication available through 802.1x.
-
Consider placing your wireless network in a wireless demilitarized zone (WDMZ), separated from the corporate network by a router or a firewall.
-
In a WDMZ, restrict the number of hosts on the subnet through an extended subnet mask, and do not use DHCP.
-
Learn how to use site survey tools such as NetStumbler and conduct frequent site surveys to detect the presence of rogue APs and vulnerabilities in your own network.
-
Don't place the AP near windows. Try to place it in the center of the building so that interference will hamper the efforts of war drivers and others trying to detect your traffic. Ideally, your wireless signal would radiate only to the outside walls of the building, not beyond. Try to come as close to that ideal as possible.
-
If possible, purchase an AP that allows you to reduce the size of the wireless zone (cell sizing) by changing the power output.
-
Educate yourself as to the operation and security of wireless networks.
-
Educate your users about safe computing practices, in the context of the use of both wired and wireless networks.
-
Perform a risk analysis of your network.
-
Develop relevant and comprehensive security policies, and implement them throughout your network.
|
|
EAN: 2147483647
Pages: 162