Exam 70-124: Objective 6.3: Malware Issues
|
|
Knowledge of Microsoft systems and malware should go hand in hand. One of the most common problems with Microsoft-based systems on a network is that they are constantly attacked with malware. Malware, code that has been written specifically to be malicious, has existed for quite some time, even before the days of the Internet. Since the world has embraced the Internet, malware has become more common and has been able to spread more effectively than ever. In this section, we look at common forms of malware and its effects on not only systems in general, but Microsoft systems in particular.
For years Microsoft has been under the gun to tighten up its systems to make them less prone to attack. The many bugs inherent in Microsoft systems were such a problem in terms of security that not even a flurry of hotfixes, updates, and service packs could contain them. Microsoft listened to users' complaints, and things have changed. Some anti-Microsoft users will disagree with this statement, but the truth is that nowadays there are no more problems with Microsoft systems than with any other systems. In fact, Cisco and Linux systems have recently been found to be just as potentially susceptible to malware as Microsoft's systems are. Because of Microsoft's recent interest in improving security, successful malware attacks against Microsoft systems have in fact dropped dramatically in number. The important thing to remember here is that Microsoft is dealing with malware, bugs, and other problems, and for the exam you need to be aware of what the company has done to counter these problems.
In this section of the chapter we cover viruses, worms, and Trojan horses and look at how they affect Microsoft systems. When we discuss Trojan horses, we talk about some of the Trojans that you might expect to see or find as well as take a look at why they are so dangerous. We also talk about what happens to your systems if they are breached and cover DoS attacks in detail. In discussing these types of problems, we also take a look at some tools such as SMBdie and Back Orifice 2000.
Viruses
A computer virus is defined as a self-replicating computer program that interferes with a computer's hardware, operating system, or application software. Viruses are designed to replicate and to elude detection. Like any other computer program, a virus must be executed ( loaded into the computer's memory) to function and then the computer must follow the virus's instructions. Those instructions are referred to as the payload of the virus. The payload can disrupt or change data files, display a message, or cause the operating system to malfunction.
Using that definition, let's explore exactly what a virus does and what its potential dangers are. Viruses spread when the instructions (executable code) that run programs are transferred from one computer to another. A virus can replicate by writing itself to diskettes, hard drives, legitimate computer programs, or even across networks. The positive side of a virus is that a computer attached to an infected computer network or one that downloads an infected program does not necessarily become infected. Remember, the code has to actually be executed before your machine can become infected. On the downside, chances are good that if you download a virus to your computer and do not execute it, the virus can probably trick your operating system into running the viral program. Other viruses have the ability to attach themselves to otherwise legitimate programs. This could occur when programs are created, opened, or even modified. Then when that program is run, so is the virus.
Some types of viruses can modify or interfere with your code. Unfortunately, developers can do little to prevent these attacks. A developer cannot write tighter code to protect against a virus. It is simply not possible. Developers can, however, detect modifications that have been made or perform a forensic investigation. They can also use encryption and other methods to protect your code from being accessed in the first place. Let's take a closer look at the six different categories that a virus could fall into and the definitions of each:
-
Parasitic Parasitic viruses infect executable files or programs in the computer. This type of virus typically leaves the contents of the host file unchanged but appends to the host in such a way that the virus code is executed first.
-
Bootstrap sector Bootstrap sector viruses live on the first portion of the hard disk, known as the boot sector. (This also applies to diskettes.) This virus replaces either the programs that store information about the disk's contents or the programs that start the computer. This type of virus is most commonly spread via the physical exchange of diskettes.
-
Multipartite Multipartite viruses combine the functionalities of the parasitic virus and the bootstrap sector virus by infecting either files or boot sectors.
-
Companion Instead of modifying an existing program, a companion virus creates a new program with the same name as an already existing legitimate program. It then tricks the OS into running the companion program.
-
Link Link viruses function by modifying the way the OS finds a program, tricking it into first running the virus and then the desired program. This virus is especially dangerous because entire directories can be infected. Any executable program accessed within the directory will trigger the virus.
-
Data file: A data file virus can open, manipulate, and close data files. Data file viruses are written in macro languages and automatically execute when the legitimate program is opened.
Worms
A worm is a self-replicating program that does not alter files but resides in active memory and duplicates itself by means of computer networks. Worms use the facilities of an operating system that are meant to be automatic and invisible to the user. It is common for worms to be noticed only when their uncontrolled replication consumes system resources, which then slows or halts other tasks. Some worms are not only self-replicating but also contain a malicious payload.
Worms can be transmitted in one of two ways: either by e-mail or through an Internet chat room. The most famous worm, the "I Love You" bug, originated in May 2000. The swiftness with which this bug moved caused migraines in more than a few network administrators. The "I Love You" worm was first detected in Europe and then in the United States. The initial analysis of the bug quickly determined that it was Visual Basic code that came as an e-mail attachment named Love-Letter-For-You.txt.vbs. When a user clicked the attachment, the virus used Microsoft Outlook to send the virus to everyone in the user's address book. The virus then contacted one of four Web pages in the Philippines. From the contacted Web page, a Trojan horse file, WIN-BUGSFIX.EXE, was then downloaded and collected usernames and passwords stored them on the user's system. It then sent all the usernames and passwords to an e-mail address. The bug quickly spread throughout the United States within 12 hours after it first manifested itself in Europe. The "I Love You" bug bit an estimated half million computers. This is the most legendary example of a worm-based malware attack.
Trojan Horses
A Trojan horse (or Trojan for short) closely resembles a virus but is actually in a category of its own. The Trojan horse is often referred to as the most elementary form of malicious code. A Trojan horse is used in the same manner as it was in Homer's Iliad; it is a program containing malicious code that appears on the outside to be harmless data or programming. It is most often disguised as something fun, such as a cool game such as elf bowling. The malicious program is hidden, and when called to perform its functionality, it can actually ruin your hard disk or disable your system by deleting or altering files. More vicious Trojans lie dormant until called on to perform evil deeds such as turning your system into one of thousands of "zombies" to partake in an Internetwide attack on an unsuspecting victim in a distributed DoS attack! (More on this subject later in the chapter.)
Not all Trojan horses are that malicious in content, but they can be, and the intent of the program is usually to cause as much damage as possible. One saving grace of a Trojan horse, if there is one, is that it does not propagate itself from one computer to another. Such self-replication is the charming way of the worm.
A common way for you to become the victim of a Trojan horse is for someone to send you e-mail with an attachment claiming to do something it can't or be something it is not. It could be a screen saver (most common with a *.scr extension) or a computer game, or even something as simple as a macro quiz. With the naked eye, it will most likely not be clear that anything untoward has happened when the attachment is launched or executed. However, the reality is that the Trojan has been installed (or initialized) on your system. In Figure 11.1, we purposely installed a Trojan on the system; it is hidden as a screen saver so you can see it running. We sent it to ourselves from a POP3 account so you could see what it would look like as an e-mail with an attachment.
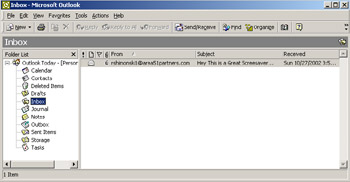
Figure 11.1: Getting the Trojan Payload in an E-Mail
Unfortunately, time has not made people any wiser to the ways of predators on the Internet. We usually spend 5 minutes a week constructing an e-mail that we send to the everyone in the corporation we work for to kindly remind them that if they get e-mails from people they don't know (such as u903jlkf@spazmail.com), they probably should not open the message. If they do, we also educate them that they really are not supposed to download or install anything that came in over the Internet. Most people tell me that as long as you block and filter at the firewall, proxy, and e-mail level, you will be fine, but the people who say this obviously don't know users all that well. If there is a will, there is a way, and users will find it. There are quite a few workarounds to bypassing enterprise-level security, and for that reason, we still like to send out a "user education" e-mail alerting users to possible social engineering attacks or malware that can damage the machines at work. Most of these users forward the email home so they can protect their home machines, too. The point is, it's a great idea to make people aware of the dangers lurking in their e-mailbox.
As you saw in Figure 11.1, we received an e-mail from a potentially dangerous individual. Now, if we were smart, we would not open this e-mail, because it just looks like a malware attack. But what about Betty in Sales who just loves new screen savers? Chances are, she can't stop herself from opening this e-mail! So let's pretend for a minute that Betty does in fact open this e-mail.
Betty opens the e-mail and it says, "Double-click on the screen saver to see beautiful flowers and a waterfall." Betty double-clicks. Nothing happens. Because Betty figures it's a dud, she deletes the e-mail and forgets about it.
Figure 11.2 shows you what really happened behind the scenes. A nice piece of malware now resides on the system, waiting for its master (the attacker) to call on it to do its bidding.
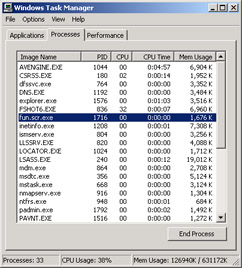
Figure 11.2: An Executed, Running, and Able Agent of Destruction
Problems like this happen all too often. Taking a hard look in your Task Manager, as shown in Figure 11.2, will show you running a server object for a tool such as Back Orifice-or any other available Trojan, for that matter. At this point, all that matters is that you are infected.
One way to protect your system from becoming infected in this manner is to have solid enterprisewide antivirus software running on your network and systems. This is a must. Most times, outbreaks and contagions can be eliminated that way. The problem is, you would be surprised at the number of companies that still think security is simply a buzzword to strike fear into the minds of nonsecurity personnel, or, worse yet, a means of attacking their bloated pocketbooks. Such attacks are not a game but a worldwide cancer that can consume your systems and infrastructure.
| Note | On the Internet, we have found items such as HP Jet Direct cards on remote systems that are willing and able to accept my commands, NetBIOS-enabled systems telling me everything about those systems, and, worse, routers with nothing more than a password of Cisco. Be afraid, be very afraid. |
To continue with our discussion of Microsoft security, let's look at a tweak you can perform that will make it obvious when a Trojan is in your e-mail or on your system. This is done by simply making sure that your system is configured not to hide anything from you. Because Microsoft feels that you shouldn't see things by default, it configures programs that end in specific extensions, such as .com, .exe, and .bat, to be hidden from you. For that reason, an .exe program won't show up if the Trojan is named fun.scr. In this case, the .exe would be hidden by default. If we looked at the file in the Task Manager, this would not in fact be the case. Most end users at least have enough common sense to know what an .exe file is, because they have probably installed software a few times at home. Figure 11.3 shows how to adjust your system so you can see almost anything that sneaks up on you. To make these adjustments, go to Start | Programs | Accessories | Windows Explorer. Once you have opened Windows Explorer, go to the Tools Menu and select Folder Options. Select the View tab, as shown in Figure 11.3. Click the radio button Show hidden files and folders, then click the Apply to All Folders button at the top of the screen.
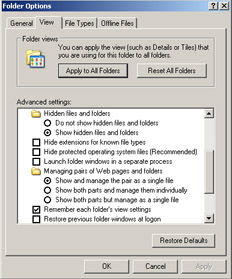
Figure 11.3: Removing the Options to Have All Your Files Hidden from You
In general, this concept is something that you as a MCP should definitely master. It is integral to your system's security. Be aware that Trojans (and malware in general) can cause your systems a great deal of harm.
Now that we have looked at how Trojans make their way into your network and onto your systems, let's think about what could happen if they were not caught. What makes this type of attack scary is that it contains the possibility that it is a remote control program that could be used to attack or take over your system. After you have launched this attachment, anyone who uses the Trojan horse as a remote server can now connect to your computer. Hackers have advanced tools to determine what systems are running remote control Trojans. After using a specially designed port scanner to find your system, all your files are open to that hacker. Two common Trojan horse remote control programs are Back Orifice and NetBus.
Trojan Awareness
A Trojan can cause massive damage to you and your systems and, worse yet, could turn your system into a virtual killing machine as well! Let's look at Back Orifice specifically so we can highlight the reasons that a tool like this can get ugly if it is installed on your systems.
Back Orifice consists of two key pieces: a client application and a server application. Back Orifice works like this: The client application runs on one machine and the server application runs on a different machine. The client application connects to another machine using the server application. The confusing part here is the fact that the server is what is installed on the victim. Many people confuse this because it doesn't seem logical, but that's how it works. The only way for the server application of Back Orifice to be installed on a machine is for it to be deliberately installed. Obviously, the Trojan does not come with a default installation of Windows 2000, so the attacker must find a way to get the victim to install it. Think of our discussion of how Betty installed that beautiful screen saver that was obviously (to you, if not to her) the BO2K.exe server. In Figure 11.4 you can see the server configuration object configured with snap-ins.
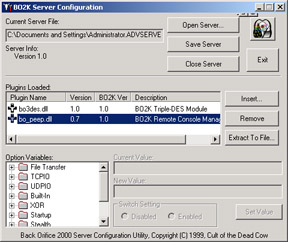
Figure 11.4: Working with the BO2K Server Configuration
Newer versions of the server executable are downright sneaky. The executables don't show up, because they are transparent. This is an evolving tool-evolving into total stealth mode for any attacker to take advantage of your systems. You really need to be aware of not only this tool but also any Trojan like it. BO2K just happens to be one of the most popular and well known. Figure 11.5 shows you that the tool is highly configurable and intuitive. Knowledge of C++ programming and shell scripting is not needed here! This makes it one of the script kiddies' favorite tools to deploy and use to cause mischief.
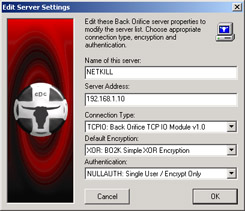
Figure 11.5: Adding Servers to the Server List
The attacker either has to install the server application on the target machine him- or herself or trick the user of the target machine into doing so-it's more likely that it will be a trick. This is the reason that the server application (BO2K.exe) is commonly disguised as a Trojan horse. After the server application has been installed, the client machine can transfer files to and from the target machine, execute an application on the target machine, restart or lock up the target machine, and log keystrokes from the target machine. All these operations are of value to a hacker.
The server application is a single executable file, just over 122KB in size. The application creates a copy of itself in the Windows system directory and adds a value containing its filename to the Windows Registry under the key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
The specific Registry value that points to the server application is configurable. That way, the server application always starts whenever Windows starts, so it is always functioning. One additional benefit of Back Orifice is that the application will not appear in the Windows task list, rendering it invisible to the naked eye. After first being initialized, it does its owner a favor and drops out of sight. Sneaky, huh?
Another common remote control Trojan horse is named the Subseven Trojan. This Trojan is also sent as an e-mail attachment, and after it is executed, it can display a customized message that is intended to mislead the victim. This particular program allows someone to have nearly full control of a victim's computer with the ability to delete folders and/or files. It also uses a function that displays something like a continuous screen cam, which allows the hacker to see screen shots from the victim's computer.
In general, be aware of the types of malware and how they can get on your systems. For the exam, be aware of the general malware concepts. In everyday system security, make sure that you are very aware of the damage that malware can cause your Microsoft systems.
Back Orifice
The Back Orifice Trojan horse server creates hell for any network, but it takes a little network knowledge to get it operational. The makers of Back Orifice, Cult of the Dead Cow (CDC, whose logo is shown in Figure 11.6), made the tool to exploit the Windows-based operating system, plain and simple, with the possible intent of it being a useful tool. Many could argue in the days of Back Orifice's inception that it was nothing more than a remote access tool, but if you think about the tool's functionality and where it came from, it was more than merely a tool for remote access-it was a wakeup call to Microsoft that its systems were just as susceptible to UNIX-based Root Kit type of applications. All it took was a little know-how and the tool, and attackers were in business.

Figure 11.6: The Logo of Cult of the Dead Cow, Makers of Back Orifice
There are some limitations, though. Possibly the two most critical limitations to the Back Orifice Trojan horse are that the attacker must know the IP address of the target machine and that there cannot be a firewall between the target machine and the attacker. A firewall makes it virtually impossible for the two machines to communicate, most likely because the firewall is blocking a port that the B02K Trojan would be operational on. Newer versions of the tool are known to operate on a wider range of ports, but that goes back to our initial discussion on how most companies haven't invested in their networks' security, nor do they have people on staff who know this information. That's really where the problem stems from. As you can see in Figure 11.7, this is not a cheesy tool-it's a GUI-based hacking nightmare. It even has wizards that walk you through initial configuration. How can it get easier than that?
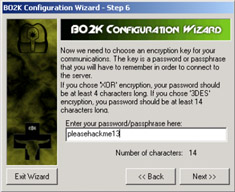
Figure 11.7: The Back Orifice Configuration Wizard
Denial of Service
In this section we cover DoS attacks and their distributed form, the DDoS. DDoS stands for distributed denial of service. A DoS attack is simply the denial of available network and systems services from clients by an attacker with malicious intent. This attack is usually launched from a single system. The distributed form of the attack (DDoS) involves using many systems to carry out the same attack, thereby making it a stronger attack coming from many sources instead of just one.
To understand a DDoS attack and its consequences, we first need to grasp the fundamentals of DoS attacks. The progression from understanding DoS to DDoS is quite elementary, although the distinction between the two is important. Given its name, it should not come as a surprise that a DoS attack is aimed squarely at ensuring that the service a computing infrastructure usually delivers is negatively affected in some way. This type of attack does not involve breaking into the target system. Usually a successful DoS attack reduces the quality of the service delivered by some measurable degree, often to the point where the target infrastructure of the DoS attack cannot deliver a service at all.
A common perception is that the target of a DoS attack is a server, but this is not always the case. The fundamental objective of a DoS attack is to degrade service, whether it be hosted by a single server or delivered by an entire network infrastructure.
A DoS attack attempts to reduce a site's ability to service clients, whether physical users or logical entities such as other computer systems. This goal can be achieved by either overloading the ability of the target network or server to handle incoming traffic or by sending network packets that cause target systems and networks to behave unpredictably. Unfortunately for the administrator, unpredictable behavior usually translates into a hung or crashed system.
Numerous forms of DoS attack exist, some of which can be difficult to detect or deflect. Within weeks or months of the appearance of a new attack, subtle copycat variations along the same theme begin appearing elsewhere. By this stage, defenses be deployed for the primary attack as well as its more distant cousins.
Many DoS attacks take place across a network, with the perpetrator seeking to take advantage of the lack of integrated security within the current iteration of Internet Protocol (IP), IP version 4 (IPv4). Hackers are fully aware that security considerations have been passed on to higher-level protocols and applications. An attempt to rectify this problem has resulted in IP version 6 (IPv6), which includes a means of validating the source of packets and their integrity using an authentication header. You don't need IPv6 to implement simple AH, but it is made easier in this version of the IP protocol. Although the continuing improvement of IP is critical, it does not resolve today's problems, because IPv6 is not in widespread use.
DoS attacks not only originate from remote systems, they are also local to the machine. Local DoS attacks are generally easier to locate and rectify because the parameters of the problem space are well defined (local to the host). A common example of a local-based DoS attack includes fork bombs that repeatedly spawn processes to consume system resources.
Although DoS attacks do not in themselves generate a risk to confidential or sensitive data, they can act as an effective tool to mask other, more intrusive activities that could take place simultaneously. Although administrators and security officers attempt to rectify what they perceive to be the main problem, the real penetration could be happening elsewhere. In the confusion and chaos that accompanies system crashes and integrity breaches, experienced hackers can slip in undetected.
The financial and publicity implications of an effective DoS attack are hard to measure-at best they are embarrassing and at worst, a deathblow. In the world of e-commerce, a customer's allegiance is fleeting. If a site is inaccessible or unresponsive, an alternate virtual shop front is only a few clicks away. Companies reliant on Internet traffic and e-purchases are at particular risk from DoS and DDoS attacks. The Web site is the engine that drives e-commerce, and customers are won or lost on the basis of the site's availability and speed. A hacker, regardless of motive, knows that the real place to hurt an e-business is to affect its Internet presence in some way. Unfortunately, DoS attacks can be an efficient means of achieving this end. The next sections cover two elemental types of DoS attacks: resource consumption attacks (such as SYN flood attacks and amplification attacks) and malformed packet attacks. SYN is the bit setting for TCP and stands for synchronize, when a system is doing a three-way handshake to establish communications with another system.
In Exercise 11.01 we look at performing a DoS attack on a Windows 2000 server with a tool called SMBdie. This exercise shows you how easy it is for a script kiddie to render your servers completely unusable with the click of a mouse.
BSOD with SMBdie
So, you want to truly create some mischief? Of course you don't, because of your white-hat status, but that won't stop all the kiddies on the network from playing games with you! If you start seeing your servers blue screen-which occurs when you see only the BSOD, or blue screen of death-without reason, you should be aware of some of the downloadable click-kiddie "aggravationware" that is freely available on the Internet! Yes, you too can download SMBdie, the Windows-based operating system crasher we examine in Exercise 11.01. Just run an Internet search on it and there it is. This tool, when executed on a network, provides the attacker with a way to send specially crafted packets to your systems to crash them. This is, of course, the very nature of a DoS attack; if the servers aren't up and serving, no service is provided to your network clients. Fortunately for you, good enterprise-level antivirus software will find and quarantine this little monster for you. The problem is, you have to ensure that every device on the network has antivirus software on it. Test this theory by sneaking into a network closet with some open hub ports and a laptop. Within minutes, the servers are down. As an MCP and a white-hat security analyst, you must be aware of problems such as this one.
Exercise 11.01: Performing a DoS with SMBdie
-
Download the SMBdie tool by either searching for it on the Internet or from the following link: http://packetstorm.decepticons.org/filedesc/SMBdie.zip.html.
-
Once you open the tool, you can run it as is. Simply double-click the executable to use the tool. (You might want to turn off your antivirus software because it could quarantine the tool.)
-
Enter the IP address of the system you want to launch the attack on in the Computer (IP address) field of the tool, as shown in Figure 11.8.
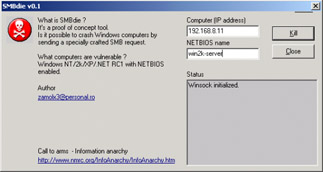
Figure 11.8: Using the SMBdie Tool -
Enter the NetBIOS name of the system you want to launch the attack on in the NETBIOS name field, as shown in Figure 11.8.
-
Once you have added all appropriate information, launch the attack by clicking the Kill button. That's it. You will see the server on which you launch the attack via a screen dump (BSOD).
To continue our discussion of DoS, we need to look at the resources on your system and how Trojans and attackers executing and launching attacks can eat up all the resources on your servers. Computing resources are by their very nature finite (although we wish it could be otherwise!). Administrators around the world bemoan the fact that their infrastructure lacks network bandwidth, CPU cycles, RAM, and secondary storage. Invariably the lack of these resources leads to some form of service degradation that the computing infrastructure delivers to the clients. The reality of having finite resources is highlighted even further when an attack is orchestrated to consume these precious resources.
The consumption of resources (and in this instance, bandwidth is considered a resource) involves the reduction of available resources, whatever their nature, using a directed attack. One of the more common forms of DoS attack targets network bandwidth. In particular, Internet connections and the supporting devices are a prime target of this type of attack due to their limited bandwidth and visibility to the rest of the Internet community. Very few businesses are in the fortunate position of having too much Internet bandwidth. (Does such a thing exist?) When a business relies on the ability to service client requests quickly and efficiently, a bandwidth consumption attack can drive home how effectively that bandwidth can be used to bring the company to its knees.
Launching a Distributed DoS
DDoS attacks advance the DoS conundrum one more painful step forward. DoS attacks have evolved beyond single-tier (SYN flood) attacks, in which the attack comes from one source, and two-tier (Smurf) attacks, where you have redirection of attacks. Modern attack methodologies have now embraced the world of distributed multitier computing. One of the significant differences in methodology of a DDoS attack is that it consists of two distinct phases. During the first phase, the perpetrator compromises computers scattered across the Internet and installs specialized software on these hosts to aid in the attack. In the second phase, the compromised hosts, referred to as zombies, are then instructed through intermediaries (called masters) to commence the attack. In Figure 11.9 we look at the simplified explanation of a DDoS attack, which generally follows this pattern:
-
The cracker plans his or her attack. The first step is to recruit zombies to do the dirty work.
-
The cracker then crafts a Trojan (like the one we looked at earlier) that can be planted on unsuspecting machines. E-mails are sent and machines are infected; once infected, these machines are recruited into the zombie horde.
-
The cracker plans an attack once the army has been built. An unsuspecting victim site is chosen. In our example scenario, www.hackme.com is the unlucky site.
-
The cracker launches a flood of traffic to hackme.com, which is so flooded with bogus traffic from hundreds of machines that it can't serve up requests for any real visitors to the site. This attack can vary from SYN floods to pings of death; it doesn't matter what the attack is, the point is mapping out that this single person just planted all these Trojans, launched a massive attack, and sat back and watched it happen from the safety of his or her own home.
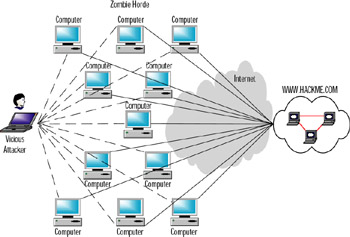
Figure 11.9: A View of Recruiting Zombies
Thanks to the zombie horde, the cracker walks away free of any worry that he or she will be caught, because a packet never left the attacker's machine to attack hackme.com.
Hundreds, possibly thousands, of zombies can be co-opted into the attack by diligent hackers. Using the control software, each of these zombies can then be used to mount its own DoS attack on the target. The cumulative effect of the zombie attack is to either overwhelm the victim with massive amounts of traffic or exhaust resources such as connection queues.
Additionally, this type of attack obfuscates the source of the original attacker: the commander of the zombie hordes. The multitier model of DDoS attacks and their ability to spoof packets and to encrypt communications can make tracking down the real offender a tortuous process. Even worse, it's almost impossible to be able to defend against the attack, which can be a ping flood unless you use certain systems (such as Cisco equipment) that can actually notice an ICMP flood starting and shut itself down.
The command structure supporting a DDoS attack can be quite convoluted, and it can be difficult to determine a terminology that describes it clearly. One of the more understandable naming conventions for a DDoS attacks structure and the components involved is detailed here.
Software components involved in a DDoS attack include:
-
Client The control software used by the hacker to launch attacks. The client directs command strings to its subordinate hosts.
-
Daemon Software programs running on a zombie that receives incoming client command strings and acts on them accordingly. The daemon is the process responsible for actually implementing the attack detailed in the command strings.
Hosts involved in a DDoS attack include:
-
Master A computer from which the client software is run.
-
Zombie A subordinate host that runs the daemon process.
-
Target The recipient of the attack.
In sum, as a Microsoft Certified Professional responsible for a network's security, you should be very aware of these issues. You could face massive problems and embarrassment when it is found out that your 30 IIS 5.0 Web servers took part in the activity of taking Yahoo.com out of service. It does happen if you are not aware of what your systems are doing.
|
|
EAN: 2147483647
Pages: 162