Module Objectives
On completion of this module you will be familiar in dealing with malicious code in the form of Trojans and backdoors.
We will begin with:
-
Terms of reference for various malicious code
-
Defining Trojans and Backdoors
-
Understanding the various backdoor genre
-
Overview of various Trojan tools
-
Learning effective prevention methods and countermeasures
-
Overview of Anti-Trojan software
-
Learning to generate a Trojan program
| |
A Trojan horse is:
-
An unauthorized program contained within a legitimate program. This unauthorized program performs functions unknown (and probably unwanted) by the user .
-
A legitimate program that has been altered by the placement of unauthorized code within it; this code performs functions unknown (and probably unwanted) by the user.
-
Any program that appears to perform a desirable and necessary function but that (because of unauthorized code within it that is unknown to the user) performs functions unknown (and definitely unwanted) by the user.
| |
There are several definitions put forth for a Trojan program. Through it all, the common underlying feature is that it is a malicious code.
| Concept | A Trojan horse may be:
|
Trojan horses can do anything that the user who executes the program on the remote machine can. This includes deleting files, transmitting to the intruder any files that can be read, changing any files that can be modified, installing other programs such as programs that provide unauthorized network access that the user is entitled to and executing privilege-elevation attacks; that is, the Trojan horse can attempt to exploit a vulnerability to increase the level of access beyond that of the user running the Trojan horse. If this is successful, the Trojan horse can operate with the increased privileges and go about installing other malicious code.
If the user has administrative access to the operating system, the Trojan horse can do anything that an administrator can.
A compromise of any system on a network may have consequences for the other systems on the network. Particularly vulnerable are systems that transmit authentication material, such as passwords, over shared networks in clear text or in a trivially encrypted form, which is very common.
If a system on such a network is compromised via a Trojan (or another method), the intruder may be able to record usernames and passwords or other sensitive information as it navigates the network.
Additionally, a Trojan, depending on the actions it performs, may falsely implicate the remote system as the source of an attack by spoofing and thereby cause the remote system to incur liability.
| |
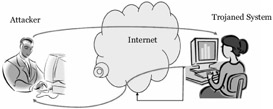
-
Attacker gets access to the trojaned system as the system goes online
-
By way of the access provided by the trojan attacker can stage attacks of different types.
| |
| Concept | Trojans work similar to the client-server model. Trojans come in two parts , a Client part and a Server part. The attacker deploys the Client to connect to the Server, which runs on the remote machine when the remote user (unknowingly) executes the Trojan on the machine. The typical protocol used by most Trojans is the TCP/IP protocol, but some functions of the Trojans may make use of the UDP protocol as well. |
When the Server is activated on the remote computer, it will usually try to remain in a stealth mode, or hidden on the computer. This is configurable - for example in the Back Orifice Trojan, the server can be configured to remain in stealth mode and hide its process. Once activated, the server starts listening on default or configured ports for incoming connections from the attacker. It is usual for Trojans to also modify the registry and/or use some other auto starting method.
| Note | To exploit a Trojan, attackers need to ascertain the remote IP address to connect to the machine. Many Trojans have configurable features like mailing the victim's IP, as well as messaging the attacker via ICQ or IRC. This is relevant when the remote machine is on a network with dynamically assigned IP address or when the remote machine uses a dial-up connection to connect to the Internet. DSL users on the other hand, have static IPs so the infected IP is always known to the attacker. |
Most of the Trojans use auto-starting methods so that the servers are restarted every time the remote machine reboots / starts. This is also notified to the attacker. As these features are being countered, new auto-starting methods are evolving. The start up method ranges from associating the Trojan with some common executable files such as explorer.exe to the known methods like modifying the system files or the Windows Registry. Some of the popular system files targeted by Trojans are Autostart Folder, Win.ini, System.ini, Wininit.ini, Winstart.bat, Autoexec.bat Config.sys. Could also be used as an auto-starting method for Trojans
Explorer Startup - This is an auto-starting method for Windows95, 98, ME and if c: \explorer.exe exists, it will be started instead of the usual c: \Windows\Explorer.exe, which is the common path to the file.
Registry is often used in various auto-starting methods. Here are some known ways:
-
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run]
" Info "="c:\directory\Trojan.exe"
-
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce]
"Info"="c:\directory\Trojan.exe"
-
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices]
"Info"="c:\directory\Trojan.exe"
-
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce]
"Info="c: \directory\Trojan.exe"
-
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
"Info"="c:\directory\Trojan.exe"
-
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce]
"Info"="c:\directory\Trojan.exe"
Registry Shell Open methods
-
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
-
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell\open\command]
A key with the value "%1 %*" should be placed there and if there is some executable file placed there, it will be executed each time a binary file is opened. It is used like this: trojan.exe "%1 %*"; this would restart the Trojan.
ICQ Net Detect Method
-
[HKEY_CURRENT_USER\Software\Mirabilis\ICQ\Agent\Apps\]
This key includes all the files that will be executed if ICQ detects Internet connection. This feature of ICQ is frequently abused by attackers as well.
ActiveX Component method
-
[HKEY_LOCAL_MACHINE\Software\Microsoft\ActiveSetup\InstalledComponents\KeyName] StubPath=C: \directory\Trojan.exe
These are the most common Auto-Starting methods using Windows system files, and the Windows registry.
| |
-
Remote Access Trojans
-
Password Sending Trojans
-
Keyloggers
-
Destructive
-
Denial Of Service (DoS) Attack Trojans
-
Proxy/Wingate Trojans
-
FTP Trojans
-
Software Detection Killers
| |
Let us take at the different types of Trojan that have been detected and based on their functionality.
| Attack Methods | – Remote Access Trojans These are the Trojans usually seen referred to in the media and hence gain high visibility because of their ability to give the attackers the power to do more things on the victim's machine than the victim itself, while standing in front of the machine. Most of these Trojans are often a combination of the other variations discussed below. |
| Attack Methods | – Password Sending Trojans These Trojans are directed towards extracting all the cached passwords and also capture other passwords entered by the victim and email them across to an attacker specified mail address, without the victim realizing it. The password harvest may include passwords for ICQ, IRC, FTP, HTTP or any other application that require a user to enter a login and password. Most of them do not restart when Windows is loaded, as the objective is to gather as much info about the victim's machine as passwords, mIRC logs, ICQ conversations and mail them to the attacker. |
| Attack Methods | – Keyloggers These Trojans log the keystrokes of the victim and then let the attacker search for passwords or other sensitive data in the log file. They usually come with two functions such as online and offline recording. As with the previous group , these Trojans can be configured to send the log file to a specific e-mail address on a regular basis. |
| Attack Methods | – Destructive The only function of these Trojans is to destroy and delete files. They can deliberately delete core system files (for example: .dll, .ini or .exe files, possibly others) on the target machine. The Trojan is activated by the attacker or sometimes works like a logic bomb and starts on a specific day and at specific hour . |
| Attack Methods | – Denial of Service (DoS) Attack Trojans These Trojans used by attackers to issue a denial of service. A distributed denial of service may also be issued if the attacker has gathered enough victims. WinTrinoo is a DDoS tool that has become popular recently, and if the attacker has infected many ADSL users, major Internet sites could be shut down as a result. Another variation of a DoS Trojan is the mail-bomb Trojan, whose main aim is to infect as many machines as possible and simultaneously attack specific e-mail address/addresses with random subjects and contents which cannot be filtered. |
| Attack Methods | – Proxy/Wingate Trojans Underground sites are known to announce freely available proxy servers. These Trojans turn the victim's computer into a proxy/Wingate server available to the whole world or to the attacker only. It is used for anonymous Telnet, ICQ, IRC, etc., and also to register domains with stolen credit cards and for other illegal activities. This gives the attacker complete anonymity and the chance to do everything and point the trail to the victim. |
| Attack Methods | – FTP Trojans These Trojans open port 21(the port for FTP transfers) and lets anybody or just the attacker connect to the machine. They may be password protected so only the attacker is able connect to the computer. |
| Attack Methods | – Software Detection Killers There are such functionalities built into some Trojans, but there are also separate programs that will kill Zone Alarm, Norton Anti-Virus and many other (popular anti-virus/firewall) programs, that protect the target machine. When they are disabled, the attacker has full access to the machine to perform some illegal activity or use the computer to attack others and often disappear. |
| |
-
ICQ
-
IRC
-
Attachments
-
Physical Access
-
Browser And E-mail Software Bugs
-
NetBIOS (File Sharing)
-
Fake Programs
-
Un-trusted Sites And Freeware Software
| |
Having seen the various types of Trojans, let us take a look at the means by which they can infect the target.
-
ICQ
People can also get infected while chatting / talking / video messaging over ICQ or any other Instant Messenger Application. It is a risk that the user undertakes when it comes to receiving files no matter from whom or where it comes.
-
IRC
Here also, the threat comes from exchange of files no matter what they claim to be or where they come from. It is possible that some of these are infected files or disguised files.
-
Attachments
Any attachment, even if it is from a known source should be screened as it is possible that the source was infected earlier and is not aware of it.
-
Physical Access
Physical access to a target machine is perhaps the easiest way for an attacker to infect a machine. The motive may be a prank or just plain curiosity .
-
Browser and E-mail Software Bugs
Having outdated applications can expose the system to malicious programs such as Trojans without any other action on behalf of the attacker.
-
NetBIOS (File Sharing)
If port 139 is opened, the attacker can install trojan .exe and modify some system file, so that it will run the next time the system is rebooted. To block file sharing in Windows version, go to: Start->Settings->Control Panel->Network->File and Print Sharing and uncheck the boxes there.
| |
-
It is a companion virus that can spread over the network.
-
It also has a "backdoor" that will enable a remote user to connect to and control the computer using port 7597.
-
It may have originally been sent out by email.
-
Rename notepad to note.com
-
Modifies the registry key:
HKLM\software\Microsoft\Windows\Current Version\Run
| |
| Tools | W32.HLLW.Qaz.A was first discovered in China in July 2000. This Trojan gained more media coverage for its hack on Microsoft. The means of its spread was a much debated topic, as it was found on several computers on Microsoft's LAN. Much speculation surrounded the possibility of a hacker probing a system during a download and injecting the Trojan. |
It is a companion virus that can spread over the network. It also has a "backdoor" that will enable a remote user to connect to and control the computer using port 7597. Because the virus cannot spread to computers outside of the network, it may have originally been sent out by email.
W32.HLLW.Qaz.A was originally known as Qaz Trojan. It was renamed to W32.HLLW.Qaz.A on August 10, 2000. There exist variants to this companion virus. When W32.HLLW.Qaz.A is launched, it searches for and renames Notepad.exe to Note.com. W32.HLLW.Qaz.A then copies itself to the computer as Notepad.exe. Each time Notepad.exe is executed, it runs the virus code and the original Notepad, which is renamed to Note.com, to avoid being noticed. The virus adds the following string value:
startIE "notepad qazwsx.hsq" to the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
W32.HLLW.Qaz.A enumerates through the network neighborhood and attempt to find a computer to infect. When it finds a computer, it infects it by searching for Notepad.exe and making the same modifications as previously described. It does not require any mapped drives to infect other computers. Once the computer is infected, its IP address is emailed to a remote user. The backdoor payload in the virus uses WinSock and awaits connection. This enables a hacker to connect to and gain access to the infected computer.
| |
http://ntsecurity.nu/toolbox/tini
-
It is a very tiny trojan program which is only 3 kb and programmed in assembly language. It takes minimal bandwidth to get on victim's computer and takes small disk space.
-
Tini only listens on port 7777 and runs a command prompt when someone attaches to this port. The port number is fixed and cannot be customized. This makes it easier for a victim system to detect by scanning for port 7777.
-
From a tini client you can telnet to tini server at port 7777
| |
| Tools | Tini is a simple and very small (3kb) backdoor for Windows, coded in assembler by Arne Vidstrom. It listens at TCP port 7777 and gives anybody who connects a remote Command Prompt. |
The reason why this application has been discussed here is that this application creates the possibility of remotely controlling a machine without any validation or authentication mechanisms. Though the author does not consider this a Trojan, its application in creating a backdoor was seen during the gator exploit. The Gator installer Plug-in allowed any software to be installed.
The vulnerability existed in a plug-in which installed the actual software. This plug-in was scriptable and an HTML page could be used to specify the location of the Gator installation. The installation file downloaded is checked for the filename. If the filename was setup.exe, it was then decompressed and executed. If the file was not compressed it would still be executed. Using this method, a malicious user could easily create an HTML page which makes use of the rogue ActiveX component to point at a Trojan file.
This Trojan demonstrates how a backdoor can be used to remotely access the system at a later time. A backdoor's goal is to remove the evidence of initial entry from the systems log. An effective backdoor will allow the attacker to retain access to a machine it has penetrated even if the intrusion factor has in the meantime been detected by the system administrator. Resetting passwords, changing disk access permissions or fixing original security holes in the hope of remedying the problem may not be a proper solution at all times.
| |
-
Outbound or inbound connections, TCP or UDP, to or from any ports
-
Ability to use any local source port
-
Ability to use any locally-configured network source address
-
Built-in port-scanning capabilities, with randomizer
-
Built-in loose source-routing capability
| |
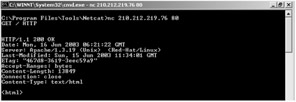
| Tools | The original version of Netcat was written by hobbit and the NT version was done by Weld Pond. |
Using netcat, the attacker can set up a port or a back door that will allow him to telnet into a DOS shell. With a simple command such as C: \>nc -L -p 5000 -t -e cmd.exe, the attacker can bind port 5000. This is detailed later. Let us first take a look at some of the features that netcat provides.
With netcat, the user can create outbound or inbound connections, TCP or UDP, to or from any port. It provides for full DNS forward/reverse checking, with appropriate warnings. Additionally, it gives the ability to use any local source port, any locally-configured network source address and comes with built-in port-scanning capabilities. It has a built-in loose source-routing capability and can read command line arguments from standard input. Another feature is the ability to let another program service inbound connections.
Given these features, some of the applications of netcat can be enumerated as an enabling script backend, port scanner and enumerator, used as backup handlers and for file transfers, firewall testing, proxy gatewaying, simulating servers, testing network performance and testing address spoofing. It is not without reason that this is called a network Swiss army knife .
Let us take a closer look at the command. On a Windows server when the following command is issued (i.e. from the directory that contains netcat)
nc -1 -p4444 -d -e cmd.exe -L
The -1 puts netcat into a listening mode, the -p4444 tells netcat to use port 4444, the -d allows netcat to run detached from the console, the -e cmd.exe tells netcat to execute the cmd.exe program when the connection is established, and the -L will restart Netcat with the same command line when the connection is terminated .
On the client system the following command
C:\>nc -v [ip address of target] 4444
causes netcat to connect to the server whose IP is specified on port 4444. The user is then given a console connection to the destination server. Netcat can also make an outbound connection and then run a program or script on the originating end, with input and output connected to the same network port.
On the target system, the attacker can choose to rename the executable or recompile it with a different name . To remain hidden he can choose to detach from the console option (-d) or use a port that is well known and allowed through any firewalls between the two systems. This will not arouse suspicions till later on.
A scanning example from Hobbit is "nc -v -w 2 -z target 20 “30". Netcat will try connecting to every port between 20 and 30 [inclusive] at the target, and inform about an FTP server, telnet server, and mailer it has come across in the range. The -z switch prevents sending any data to a TCP connection and very limited probe data to a UDP connection. This makes it useful as a fast scanner to see what ports the target is listening on. To limit scanning speed if desired, -i will insert a delay between each port probe.
To receive a file named targetfile on the target system start netcat with the following command:
nc -1 -p 4444 >targetfile
To send a file named myfile to the target system from the source system use the following command:
nc target 4444 <myfile
Issue a Ctrl+C on the source system and the session is over.
| |
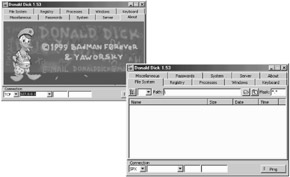
The attacker uses the client to send command through TCP or SPX to the victim listening on a pre defined port.
Donald Dick uses default port either 23476 or 23477
Donald Dick is a tool that enables a user to control another computer over a network.
It uses a client server architecture with the server residing on the victim's computer.
| |
| Tools | Donald Dick is a remote control system for workstations running Windows 95, 98 or NT 4.0 First, it was implemented to replace well-known Trojans, and to be invisible for existing antivirus. The first implementation could only open and close CDROM tray. |
Donald Dick consists of two parts - client and server. To install server on the destination computer, the user must launch the executable file. Running a Donald Dick server on a computer, gives full access to all resources to the attacker. The attacker can control it with Donald Dick client via TCP or SPX network protocol. He can also restrict access to the server with a password.
Under Windows9X Donald Dick server becomes operational immediately after rebooting. Under Windows NT the server is loaded as a service process.
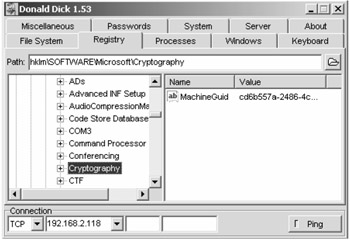
With Donald Dick, the attacker has full access to the file system. He can browse, create, and remove directories; erase, rename, copy, upload, download files; set date/time of file. He can control the processes and threads running on the system. He can choose to browse, terminate or run programs. He can set priority for processes and suspend or resume threads. The Trojan gives complete access to the registry where the attacker can browse, create, remove keys and values or even set values.
Other things that he can do to affect the target system is to set the system time, shutdown the machine, cause it to reboot or log off and even switch the power off. He can query the system for information and even set system parameters. With regard to the display, he can get a list of windows; query and set system colors; get screenshot or the shot for particular window; and even send messages to the window.
The Trojan lets the attacker read and write CMOS (Windows 9x); simulate keystrokes, remap, disable keys, and view keyboard input (all features except keystroke simulation are not implemented under Windows NT). Using the services provided by the server and the GUI client the attacker can query passwords for screensaver, BIOS and shared resources, and make folders sharable . The Trojan can also cause deletion of the HKLM \software key from the registry. If this is done, programs slowly fail and when system is restarted, it shows installation screen and asks for a serial number. But the installation will not proceed from there.
| |
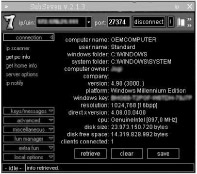
-
SubSeven is a backdoor program that enables others to gain full access to Windows 9x systems through network connection.
-
The program consists of three different components : Client (SubSeven.exe), Server (Server.exe) and a Server configuration utility (EditServer.exe).
-
The client is a GUI used to connect to server through a network or internet connection.
| |
| Tools | Since its debut in February, 1999, SubSeven has become a favorite tool of intruders targeting Windows machines. |
It is a RAT (Remote Administration Tool) that provides more options for attack than other Trojans like Back Orifice or NetBus. The SubSeven Trojan is consists of three programs: the SubSeven server, client and server editor. It has a DDoS potential and like other Trojans, SubSeven can be used as perfectly benign remote administration program.
The server must be run on the target computer to allow the attacker's computer to connect to the machine and have total access to it. The server editor (EditServer Program) helps configure the infection characteristics. This allows the hacker to specify whether the compromised system should send an email or ICQ notification to the attacker when the target is online, whether the program should "melt server after installation" and which ports the attacker can use to connect to the server. Once installed, SubSeven's friendly user-interface allows the attacker to easily monitor a victim's keystrokes, watch a computer's web cam, take screen shots, eavesdrop through the computer's microphone, control the mouse pointer, read and write files, and sniff traffic off the victim's local network.
The address book feature makes it possible to check whether a victim is presently online, the process manager feature allows aborting any running process on the victim's computer, "text2speech" allows the attacker to type any text which is then spoken on the victim's computer and the ability to completely takeover a victim's ICQ account.
A SubSeven server can also be programmed to announce itself over ICQ or Internet Relay Chat (IRC), and groups of servers can be remotely controlled as one. That makes the program particularly useful for launching distributed denial of service attacks (DDoS), in which constellations of systems are simultaneously directed to flood a single site with an overwhelming volume of traffic, as had happened to Yahoo!, CNN.com, and other online giants in February 2000. More damaging features of SubSeven are the port redirector and the port scanner. The port redirector allows an attacker to use the victim's system to launch attacks into other systems by configuring ports on the infected computer to point to new targets. The port scanner feature converts the infected machine into a personal port scanner that can be used to gain access to the corporate LAN and disguise the attacks.
The new version of SubSeven offers script kiddies increased flexibility in the user interface, a revamped mechanism for customizing the server, and for the first time runs smoothly on Windows NT and Windows 2000. The client is not downward compatible with previous versions of the program. SubSeven 2.2 signatures will likely be quickly be integrated into antivirus updates.
| |
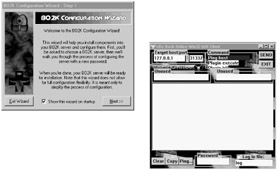
Back Orifice accounts for highest number of infestations on Microsoft computers.
The BO2K server code is only 100KB. The client program is 500KB.
Once installed on a victim PC or server machine, BO2K gives the attacker complete control of the system.
BO2K has stealth capabilities, it will not show up on the task list and runs completely in hidden mode.
| |
| Tools | BO2K was written by DilDog of the Cult of the Dead Cow. Many of the commands that B02K comes with were directly ported from Sir Dystic's original Back Orifice source code. The document says that it was written with a two-fold purpose: "To enhance the Windows operating system's remote administration capability and to point out that Windows was not designed with security in mind." |
B02K is an almost complete rewrite of the original Back Orifice. By default, B02K comes with the capability to talk over TCP as well as UDP, and supports strong encryption through plug-ins. It has added functionality in the areas of file transfer and registry handling. It has hacking features, such as dumping certain cached passwords. It can be configured to be stealthy.
Like other Trojans, Back Orifice is a client/server application which allows the client software to monitor, administer, and perform other network and multimedia actions on the machine running the server. To communicate with the server, either the text based or GUI client can be run on any Microsoft Windows machine.
The B02K server installed without any plugins is ~100K and leaves a small footprint. The client software is ~500K. The whole suite will fit on a single 1.44MB floppy disk. B02K 1.0 will currently run on Windows 95, Windows 98, Windows ME, Windows NT, Windows 2000, and Windows XP systems. All of the various parts of the BO2K suite have been tested and found to be working on all of these platforms. It only runs on Intel platforms at the moment.
To install, the server, the target must execute the server on his machine. When the server executable is run, it installs itself and then deletes itself, which makes it virtually hidden. Once the server is installed on a machine, it will be started every time the machine boots. If the target is running a server already, the attacker can simply upload the new version of the server to the remote host, and use the Process spawn command to execute it. When run, the server will automatically kill any programs running as the file it intends to install itself as, install itself over the old version, run itself from its installed position, and delete the updated exe that was run.
The attacker can choose to configure the server before installation. This includes the filename that Back Orifice installs itself as, the port the server listens on, and the password used for encryption using the boconf.exe utility. If the server is not configured, it defaults to listening on port 31337, using no password for encryption (packets are still encrypted), and installing itself as ".exe" (space dot exe).
The client communicates to the server via encrypted UDP packets. Back Orifice can communicate over any available port. Therefore, if the firewall lets through any UDP packets at all, two-way communication can be established. If packets are being filtered or a firewall is in place, it may be necessary to send from a specific port that will not be filtered or blocked. Since UDP communication is connectionless, the packets might be blocked either on their way to the server or the return packets might be blocked on their way back to the client. As for file transfers originating at the remote machine, Back Orifice can use TCP to send data out through the firewall.
Actions are performed on the server by sending commands from the client to a specific IP address. Back Orifice can sweep a range of IP addresses and network blocks to hunt for installations of its server software. It can be located by using the sweep or sweeplist commands from the text client, or from the GUI client using the "Ping" dialog, or by putting a target IP. If by sweeping a list of subnets, a server machine responds, the client will look in the same directory as subnet list and will display the first line of the first file it finds with the filename of the subnet.
It must be noted that Back Orifice does not rely on the user for its installation. To install it, it simply needs to be run. It takes advantage o f some actual exploits in the Windows OS functionality. This brings about several ways the program could be run on a windows computer, not only without the user's approval, but without the user's knowledge.
| |
-
BO2K functionality can be extended using BO plug-ins.
-
BOPeep (Complete remote control snap in)
-
Encryption (Encrypts the data sent between the BO2K GUI and the server)
-
BOSOCK32 (Provides stealth capabilities by using ICMP instead of TCP UDP)
-
STCPIO (Provides encrypted flow control between the GUI and the server, making the traffic more difficult to detect on the network)
| |
| BO Peep - This plugin gives you a streaming video of the machine's screen that the server is running on. Also provides remote keyboard and mouse accessibility. |
| Serpent Encryption - This is a very fast implementation of the non-export-restricted 256 bit-SERPENT encryption algorithm. |
| CAST-256 Encryption - This internationally available plugin provides strong encryption using the CAST-256 algorithm. |
| IDEA Encrypt - This internationally available plugin provides strong encryption using the IDEA algorithm. 128 Bit Encryption. |
| RC6 Encryption - This internationally available plugin provides strong encryption using the RC6 algorithm. Provides 384 bit encryption. |
| STCPIO - TCPIO communications plugin with an encrypted flow control system to make BO2K TCP traffic virtually impossible to detect. |
| Rattler notifies a specified user as to the whereabouts of a Back Orifice 2000 server via e-mail. Rattler will send an e-mail each time it detects an IP address addition/modification. |
| rICQ is a plugin for Back Orifice 2000 that operates in a similar fashion to Rattler except that the notification message is sent via ICQ's web pager service. |
| The Butt Trumpet 2000 plugin for BO2K, once installed and started, sends you an email with the host's IP address. A nice alternative to Rattler. |
| BoTool provides a graphical file browser and registry editor to the BO2K interface. Makes common tedious BO2K tasks point-and-click simple. |
| |
| |
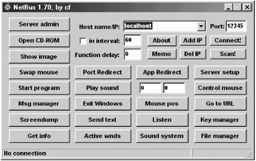
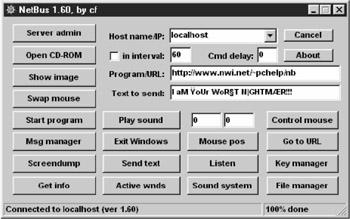
| Tools | NetBus was written by a Swedish programmer, Carl-Fredrik Neikter, in March 1998. Version 1.5 in English appeared in April. NetBus apparently received little media attention but it was in fairly wide use by the time BO was released on 3 August. |
NetBus consists of two parts: a client-program ("netbus.exe") and a server-program often named: "patch.exe" (or "SysEdit.exe" with version 1.5x), which is the actual backdoor. Version 1.60 uses the TCP/UDP-Port # "12345" which can't be altered. From the version 1.70 and higher the port be configured. If it is installed by a "game" called "whackamole" (file name is: "whackjob.zip" (contains the NetBus 1.53 server) its name is "explore.exe". There is also a file called whackjob17.zip, which installs the server of NetBus 1.70 and uses the port 12631. Additionally it is password protected (PW: "ecoli"). The NetBus Server is installed by "game.exe" during the setup routine; the name of the server actually is "explore.exe" located in the windows directory.
To start the server automatically, there is an entry in the registry at: "\HKEY_LOCAL_MACHINESOFTWARE\Microsoft\Windows\CurrentVersion\Run" normally used with the option "/nomsg". If this entry is deleted, the server won't be started with windows.
The NetBus server is about 4 times as large as the Back Orifice server, and generally less "stealthy." Unlike BO, NetBus is not designed to attach virus-like to legitimate files or applications.
Like BO, the NetBus server can have practically any filename. The usual way it is installed is through simple deception; the program is sent to the victim, or offered on a website, and falsely represented as something it is not. Occasionally it may be included in a setup package for a legitimate application and executed in the process of that setup.
The unsuspecting victim runs the program either directly or by way of the application used as camouflage, and it immediately installs itself and begins to offer access to intruders.
NetBus will always reveal its presence by way of an open port, viewable with netstat.exe. Because of this, many intruders delete netstat.exe from the victim's hard drive immediately upon gaining access. Creating a copy or two of netstat using other names is a good precaution against its loss. A regular check for the presence of netstat.exe, including the file's size and date, is advisable and is one means of spotting intrusions. Attackers may use BO as a means of installing Netbus on the target system. This is because NetBus is sophisticated yet easy to use.
Once access is gained, the intruder will often install other backdoors, ftp or http daemons which open victim's drive(s) to access or he may enable resource sharing on the Net connection
The v1.53 server opens two TCP ports numbered 12345 and 12346. It listens on 12345 for a remote client and apparently responds via 12346. It will respond to a Telnet connection on port 12345 with its name and version number.
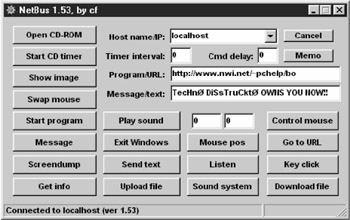
NetBus v1.53 is not extremely stealthy, but it is certainly functional and effective.
This utility also has the ability to scan "Class C" addresses by adding "+Number of ports" to the end of the target address. Example: 255.255.255.1+254 will scan 255.255.255.1 through 255.
By default, the v1.6o server is named Patch.exe. It may be renamed. Its size is 4 61K (472,576 bytes). When this program is run, it remains where it is and nothing appears to happen. Unlike v1.53, it can then be deleted uneventfully. However, it is functional. It copies itself to the Windows directory, extracts from within itself a file called KeyHook.dll and activates both programs.
Run without added parameters, v1.6o is persistent; that is, it will execute on its own when the computer is restarted. It makes changes to the Registry; it creates the keys
HKEY_CURRENT_USER\PATCH, where PATCH is the filename before the extension; and by default, it places a value in the key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Version 1.60, like v1.53, also creates the Registry keys
HKEY_CURRENT_USER\NETBUS; and HKEY_CURRENT_USER\NETBUS\Settings and places basically the same series of values in the Settings key.
The v1.60 server opens two TCP ports numbered 12345 and 12346. It listens on 12345 for a remote client and apparently responds via 12346. It will respond to a Telnet connection on port 12345 with its name and version number.
Among the new features are greatly expanded file-handling capabilities, an interactive message dialog, password setting and other server controls, and new ways to tamper with the keyboard. Most of its tricks are evident from this console display.
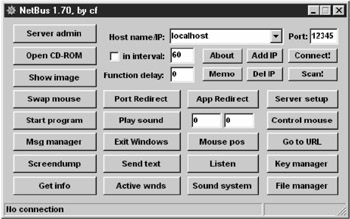
Netbus 1.7 was released to the public on 11/14/98. It is basically the same program as version 1.6, but with an ultra -fast port scanner, capable of redirecting data to another host and port, option to configure the server-exe with some options, like TCP-port and mail notification, ability redirect I/O from console applications to a specified TCP-port and restricting access to only a few IP- numbers .
By default, the v1.70 server is named Patch.exe. It may be renamed. Its default size is 483K (494,592 bytes). With configuration added, its size increases , usually by a couple of hundred bytes. By default, the v1.70 server opens two TCP ports numbered 12345 and 12346. It listens on 12345 for a remote client and apparently responds via 12346. It will respond to a Telnet connection on port 12345 with its name and version number. It can however be readily configured to use any other virtual port from 1 to 65534. The port configuration can be pre-set by the sender, and/or it can be changed from remote. It will also open the next-numbered port in sequence, which it apparently uses for responses to the client.
When the v1.70 server is contacted by a remote user, it creates two files named Hosts.txt and Memo.txt and places them in the same directory as the running server. Hosts.txt lists hosts that have contacted the server, if logging is enabled. The remote user can leave a memo here for self using Memo.txt.
If the server file has been pre-configured by the sender, it will create yet another file, which it always places in the Windows directory. IP.txt lists all text and commands received on the port on which NetBus is listening, showing date, time and originating IP address.
It can be instructed to send an email when it is run for the first time, to notify its owner of its installation. If IP logging is enabled, it will write all commands and IP addresses to IP.TXT. Another file is called "Access.txt", and contains the list of IP addresses permitted to connect to the Netbus server.
NetBus is now capable of redirecting input to a specified port to another IP address via the server machine. This means the remote user can do mischief on a third machine someplace on the Net, and his connection will appear to come from the redirecting address.
NetBus 2.0 Pro", (often just called "NetBus 2.0") the latest version of this well known backdoor program has been released after Spector took over Netbus. Therefore the new version is a shareware and needs remote user's permission for installation. However, hackers have released variations such as Retail_10.exe which fakes the incomplete patch of ICQ. Instead it installs the "NetBus 2.0 Server" in the invisible and auto starting mode. It even deletes the data logged by the server.
| |
-
How does an attacker get BO2K or any trojan installed on the victim's computer? Answer: Using Wrappers
-
A wrapper attaches a given EXE application (such as games or orifice application) to the BO2K executable.
-
The two programs are wrapped together into a single file. When the user runs the wrapped EXE, it first installs BO2K and then runs the wrapped application.
-
The user only sees the latter application.
I can send a birthday greeting which will install BO2K as the user watches a birthday cake dancing across the screen.
| |
| Note | Wrappers are used to bind the Trojan executable with a legitimate file. The attacker can compress any (DOS/WIN) binary with tools like "petite.exe". This tool decompresses an exe-file (once compressed) on runtime. This makes it possible for the Trojan to get in virtually undetected, as most antivirus are not able to detect the signatures in the file. |
The attacker can place several executables to one executable as well. These wrappers may also support functions like running one file in the background while another one is running on the desktop.
Technically speaking though, wrappers can be considered to be another type of software "glueware" that is used to attach together other software components. A wrapper encapsulates a single data source to make it usable in a more convenient fashion than the original unwrapped source.
Users can be tricked into installing Trojan horses by being enticed or frightened. For example, a Trojan horse might arrive in email described as a computer game. When the user receives the mail, they may be enticed by the description of the game to install it. Although it may in fact be a game, it may also be taking other action that is not readily apparent to the user, such as deleting files or mailing sensitive information to the attacker.
| |

| |
| Tools | Graffiti.exe is an example of a legitimate file that can be used to drop the Trojan into the target system. This program runs as soon as windows boots up and on execution keep the user distracted for a given period of time by running on the desktop. |
This will allow the Trojan executable to run in the background and make the necessary changes it needs to. The program in itself does not mess with registry, as all modifications are in one .ini file created in the same folder with software. The only options available to the viewer are:
-
Left Mouse Click- Exit Graffiti
-
Esc and Space- Exit Graffiti
-
Right Mouse Click- Display next message
-
Alt-N- Display next message
| |
http://homepage.ntlworld.com/chawmp/elitewrap/
-
Elite Wrap is an advanced EXE wrapper for Windows 95/98/2K/NT used for SFX archiving and secretly installing and running programs.
-
With EliteWrap one can create a setup program that would extract files to a directory and execute programs or batch files to display help, copy files, etc.
| |
| Tools | eLiTeWrap is an EXE wrapper, used to pack files into an archive executable that can extract and execute them in specified ways when the packfile is run. For example, you could create a setup program that would extract files to a directory and execute programs or batch files to display help, copy files, etc. |
The advantages eLiTeWrap has over other common self-extractor programs and EXE wrappers are:
Programs in the packfile can be extracted without starting. Unlike many EXE wrappers, files can be automatically extracted into a temporary directory, from where other programs in the packfile or on the user's system can manipulate them.
Programs inside the packfile and on the user's system can be automatically started. Unlike many self-extractor utilities, eLiTeWrap has the ability to start any number of programs, contained in the packfile, or existing on the user's system.
Programs (packed and external) can be started visibly, or hidden from the user. Programs that do not require user input can be started completely hidden from the user. Programs can be started synchronously or asynchronously. The packfile can be made to wait for a program to finish before the rest of the files are processed . Script files can be written to automate the creation of packfiles.
Full CRC-32 checking is built in 32-bit cyclic redundancy checks are preformed to ensure that files are complete, undamaged, and that they have not been tampered with. Packfiles are produced with an icon. Providing CRC-32 checking is disabled, you can change the icon in any resource editor, such as those provided with Microsoft and Borland development environments.
| |
IconPlus can be used to change icons in EXE files
| |
| Tools | Icon Plus is a conversion program for translating icons between various formats. |
Icon Plus now can read and save Windows XP icons. Icon Plus can also be worked at from the command prompt. This kind of application can be used by an attacker to disguise his malicious code or Trojan so that users are tricked into executing it.
There are numerous icon libraries available on the Internet that allows a user to change icons to suit various operating systems by aping their look and feel.
| |
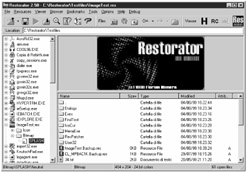
| |
| Tools | It is a versatile skin editor for any Win32 programs: change images, icons, text, sounds, videos , dialogs, menus , and other parts of the user interface. Using this one can create one's own User-styled Custom Applications (UCA). |
The relevance of discussing this tool here arises from its ability to modify the user interface of any Windows 32-bit program and thus create UCA's. The user can view, extract, and change images, icons, text, dialogs, sounds, videos, menus and much more.
Technically speaking, it lets the user edit the resources in many file types, for example exe, dll, res, ocx (Active X), scr (Screen Saver) and others. Screensavers have been popular as Trojan carriers . The attacker can distribute his modifications in a small, self-executing file - the ResPatcher.
It is small in size and people who use it need not have Restorator installed. It is not necessary to give away the complete exe or dll file either, which makes it a powerful tool. It is a stand alone program which redoes the modifications made to a program.
Restorator has many built-in tools. Powerful find and grab functions lets the user retrieve resources from all files on their disks.
One example is where a program can be modified using restorator and sent across to the intended victim. This may be a screensaver, a skin for a media player or even an innocent looking attachment.
| |
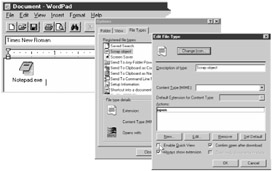
| |
It has been seen how notepad has been used by QAZ. In windows, we have seen OLE to be a simple concept that allows the inclusion of data from one type of file or document, within another. Moreover, it allows multiple applications on the same desktop to share information.
This makes it possible to transport "objects" which are embedded in an application, from one place to another, embedding them as deemed fit. OLE provides for this, using a file format of its own which contains the embedded data in a sort of "wrapper." We will look at how WordPad can be used to hide notepad and execute it on being opened.
| Attack Methods | To begin, open WordPad. Using the mouse, drag and drop Notepad.exe into the WordPad window. On double-click the embedded icon, Notepad will open. Now, right-click on the Notepad icon within the WordPad and copy it to the desktop. |
The icon that appears is very similar to the default text icon. We can change the icon by using the properties box. By default, the file is named simply "Scrap" -- even if Windows is set to show all file extensions. Rename it to "Read me". Now it can pass easily for a genuine text file. On double-click the file, the Notepad program that's within the scrap object will open.
Even if the object in a scrap file is not executable, a command can be associated with the object, which will be executed when it is double-clicked. This makes it simple for files to masquerade as another file type.
| |
-
When you place a CD in your CD-ROM drive, it automatically starts with some set up interface. An Autorun.inf file that is placed on such CD's is responsible for this action which would look like this:
[autorun] open=setup.exe icon=setup.exe
-
Therefore it is quite possible that while running the real setup program a trojan could be run very easily.
-
Turn off the Auto-Start functionality by doing the following:
Start button-> Settings-> Control Panel-> System-> Device Manager-> CDROM-> Properties -> Settings
| |
Is it possible for an attacker to trick the target into loading the Trojan either while booting or installing any other application?
| Attack Methods | Obviously, this has been thought of in more than one way. One way of infecting the target machine is to use the auto start CD function. This may be done by "gifting" a CD, lending an infected CD or by having physical access to the system. |
The Autorun.inf file that is placed on such CD's can be configured to execute the Trojan. This makes it possible to infect a machine while running the real setup program. It looks like this:
[autorun] Open= setup.exe Icon= setup.exe
Countermeasure is to stop auto start functionality by doing the following:
Start Button-> Settings-> Control Panel-> System-> Device Manager-> CDROM->Properties- > Settings
Turn off the reference to Auto Insert Notification
| |
-
Popular delivery vehicle for NetBus/BO servers is a game called Whack-A-Mole which is a single executable called whackamole.exe
-
Whack-A-Mole installs the NetBus/BO server and starts the program at every reboot.

| |
| Tools | When NetBus is installed by a "game" called "whackamole" (file name is: " whackjob.zip" (contains the NetBus 1.53 server) its name is "explore.exe". There is also a file called whackjob17.zip, which installs the server of NetBus 1.70 and uses the port 12631. Additionally it is password protected (PW: "ecoli"). |
The Game "whackamole.exe" file size 314,636 credited to "John" alias <ecoli_@hotmail.com>, is actually the Netbus Trojan. It is contained within Whackjob.zip and installs "patch.exe",(the Netbus Server portion) within the install shield script for the game install. The program Netbus.exe is renamed Explore.exe during the install. This can arbitrarily be installed using the "DotLess IP address" (better known as the "Buffer Overrun" exploit). Version 2.0 runs on Port 20043 with the "added feature" of automatically clearing the log file every time the PC is rebooted.
REGISTRY KEYS ADDED: HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.dl_ REGISTRY KEY VALUES ADDED: HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.dl_\@="exefile" HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.dl_\ContentType="application/x- msdownload" It also adds Rundll32:Reg_SZ:rundll2.dl_to HKLM \SW\MSoft\Windows\CurrentVer\Run
| |
-
Soon after BO appeared, a category of cleaners emerged, claiming to be able to detect and remove BO.
-
BOSniffer turned out to be one such Trojan that in reality installed Back Orifice under the pretext of detecting and removing it.
-
Moreover, it would announce itself on the IRC channel #BO_OWNED with a random username.
| |
Ken Williams noted in a post to bugtraq that "BoSniffer.zip" which the author claimed to be capable of blocking key points in the registry from BO as well as search for existing installs of the backdoor, was in fact a Trojan.
His detailed examination has revealed that this is actually a BO server with the "SpeakEasy" plug-in installed. If "BoSniffer.exe" is run, the BoSniffer executable (BO Server Trojan w/ SpeakEasy) will "attempt to log into a predetermined IRC server on channel #BO_OWNED with a random username. It then proceeds to announce its IP address and a custom message every few minutes." This program, "BoSniffer.zip" is being widely distributed as a "cure for Back Orifice infections". It is likely that it is being distributed with other software packages and under other names as well. Listed below are relevant details about this program.
File Sizes (in bytes) - 231068 BoSniffer.exe, 108573 BoSniffer.zip
Evidence that BoSniffer.zip is really BO Server with SpeakEasy Plug -in:
sector 0X028C38 irc.lightning.net:7000:Hey MASTER where are u!!! sector 0x0303F0 - sector 0x0306D8 sector 0x031848 SpeakEasy.dll sector 0x0318A8 - sector 0x031980 #BO_OWNED with IRC commands: Own Me @ .NOTICE JOIN #BO_OWNED host server :Owned USERNICK BO .QUIT Psssst...Speakeasy was told to shut down .NOTICE #BO_OWNED :Psssst...Speakeasy just started up
| |
-
FireKiller 2000 will kill (if executed) any resistant protection software.
-
For instance, if you have Norton Anti-virus auto scan in your taskbar, and ATGuard Firewall activated, this program will KILL both on execution, and makes the installations of both UNUSABLE on the hard drive; which would require re-installation to restore.
-
It works with all major protection software like AtGuard, Conseal, Norton Anti-Virus, McAfee Anti-Virus etc.
Tip Use it with an exe binder to bind it to a trojan before binding this file (trojan and firekiller 2000) to some other dropper.
| |
| Tools | FireKiller, written by Iridium is a Trojan that on execution kills any resistant protection software on execution. For instance, if Norton Antivirus Auto-Protect option is running in the taskbar, and the AT Guard Firewall is activated, this program will kill both on execution, and make the installations of both unusable on the machine. To reuse it, the user will have to reinstall it. |
It has been noted to work with all major protection software like AT guard, Conceal, Norton Antivirus, and McAfee Antivirus etc. Later patches detect this Trojan. It is typically used in conjunction with an .exe binder, which binds it to a Trojan before binding this file (Trojan and firekiller2000) to some other dropper.
The same author has written another Trojan called FireCracker. It automatically detects AT Guard, Zone Alarm and or McAfee Firewall, deactivates it and deletes it from the hard disk. The original Firewall Icons remain in the taskbar all the time, so it looks like nothing is happened. It also reloops the functions that the victim must reboot the CPU to reinstall the firewall(s).
| |
-
Covert Channels are methods in which an attacker can hide the data in a protocol that is undetectable.
-
Covert Channels rely on techniques called tunneling, which allows one protocol to be carried over another protocol.
-
ICMP tunneling is a method of using ICMP echo-request and echo-reply as a carrier of any payload an attacker may wish to use, in an attempt to stealthily access, or control a compromised system.
| |
| Note | The Internet Control Message Protocol is an adjunct to the IP layer. It is a connectionless protocol used to convey error messages and other information to unicast addresses . ICMP packets are encapsulated inside of IP datagram. The first 4-bytes of the header are same for every ICMP message, with the remainder of the header differing for different ICMP message types. There are 15 different types of ICMP messages. |
The ICMP types we are concerned with are type ox8 and type 0x8. ICMP type 0x0 specifies an ICMP_ECHOREPLY (the response) and type 0x8 indicates an ICMP _ECHO (the query). The normal course of action is for a type 0x8 to elicit a type 0x0 response from a listening server. (Normally, this server is actually the OS kernel of the target host. Most ICMP traffic is, by default, handled by the kernel). This is what the ping program does.
The concept of ICMP Tunneling involves arbitrary information tunneling in the data portion of ICMP_ECHO and ICMP_ECHOREPLY packets and using them to carry the payload.
| Attack Methods | Covert Channels are methods in which an attacker can hide the data in a protocol that is undetectable. Covert Channels rely on techniques called tunneling, which allows one protocol to be carried over another protocol. A covert channel is a vessel in which information can pass, but this vessel is not ordinarily used for information exchange. |
Therefore, as a matter of consequence, covert channels are impossible to detect and deter using a system's normal (read: unmodified) security policy. In theory, almost any process or bit of data can be a covert channel. In practice, it is usually quite difficult to elicit meaningful data from most covert channels in a timely fashion.
This makes it an attractive mode of transmission for a Trojan. The attacker can use the covert channel and install the backdoor on the target machine.
| Concept | The concept of ICMP Tunneling is simple: arbitrary information tunneling in the data portion of ICMP_ECHO and ICMP_ECHOREPLY packets. This exploits the covert channel that exists inside of ICMP_ECHO traffic. This channel exists because network devices do not filter the contents of ICMP_ECHO traffic. They simply pass them, drop them, or return them. The Trojan packets themselves are masqueraded as common ICMP_ECHO traffic. We can encapsulate (tunnel) any information we want. |
| |
(www.phrack.com)
-
Loki was written by daemon9 to provide shell access over ICMP making it much more difficult to detect than TCP or UDP based backdoors.
-
As far as the network is concerned, a series of ICMP packets are shot back and forth: Ping, Pong-response. As far as the attacker is concerned, commands can be typed into the loki client and executed on the server.
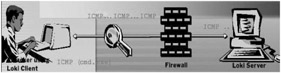
| |
| Tools | This program is a working proof-of-concept to demonstrate that data can be transmitted rather stealthily across a network by hiding it in traffic that normally does not contain payloads. The example code in the original Phrack magazine can tunnel the equivalent of a Unix RCMD/RSH session in either ICMP echo request (ping) packets or UDP traffic to the DNS port. This is used as a back door into a UNIX system after root access has been compromised. Presence of LOKI on a system is evidence that the system has been compromised in the past. |
Although the payload of ICMP packet is often timing information, there is no check by any device as to the content of the data. So, as it turns out, this amount of data can also be arbitrary in content as well. Therein lies the covert channel. A covert channel is a vessel in which information can pass, but this vessel is not ordinarily used for information exchange. Therefore, covert channels are impossible to detect and deter using a system's normal security policy.
Loki exploits the covert channel that exists inside of ICMP_ECHO traffic. This channel exists because network devices do not filter the contents of ICMP_ECHO traffic. The Trojan packets themselves are masqueraded as common ICMP_ECHO traffic. It can be used as a backdoor into a system by providing a covert method of getting commands executed on a target machine. The LOKI packet with a forged source IP address will arrive at the target (and will elicit a legitimate ICMP_ECHOREPLY, which will travel to the spoofed host, and will be subsequently dropped silently) and can contain the 4-byte IP address of the desired target of the Loki response packets, as well as 51-bytes of malevolent data.
The important aspect of Loki is that routers, firewalls, packet-filters, dual- homed hosts all can serve as conduits for Loki. A surplus of ICMP_ECHOREPLY packets with a garbled payload can be ready indication the channel is in use. The standalone Loki server program can be easily detected. However, if the attacker can keep traffic on the channel down to a minimum, and was to hide the Loki server inside the kernel, detection is almost impossible.
| |
-
Configure your firewall to block ICMP incoming and outgoing echo packets.
-
Blocking ICMP will disable ping request and may cause inconvenience to users.
-
So you need to carefully decide on security Vs convenience.
-
Loki also has the option to run over UDP port 53 (DNS queries and responses.)
| |
Stateful firewalls are the enhanced version of packet filters. It still does the same checking against a rule table and only routes if permitted, but it also keeps track of the state information such as TCP sequence numbers. Some pay attention to application protocols to ensure only legitimate traffic passes through. These filters can get UDP packets (e.g. for DNS and RPC) securely through the firewall to a great extent more so because UDP is a stateless protocol. And it is more difficult for RPC services. However, this does not solve the problem in case of ICMP covert channels as ICMP echo are also subject to firewall rules.
If there is no rule to allow ping, then all such packets get dropped. If the ping came over a tunnel and interface is not configured to force tunnel traffic up to the proxies, then the ping packets are sent unmodified.
There are a few countermeasures that may help keep Loki at bay.
| Countermeasure | – Disable external ICMP_ECHO traffic entirely. This does have serious implications to normal network management since it does affect network communication management within the local segment. However, this can be configured to allow internal ping traffic and disable packets coming from the outside. |
| Countermeasure | – Disable ICMP_ECHO_REPLY traffic on a Cisco router. Security implications make this a prudent choice. |
| Countermeasure | – Ensure that the routers are configured to not send ICMP_UNREACHABLE error packets to hosts that do not respond to ARPs. |
| |
-
Reverse WWW shell allows an attacker to access a machine on your internal network from the outside.
-
The attacker must install a simple trojan program on a machine in your network, the Reverse WWW shell server.
-
On a regular basis, usually 60 seconds, the internal server will try to access the external master system to pick up commands.
-
If the attacker has typed something into the master system, this command is retrieved and executed on the internal system.
-
Reverse WWW shell uses standard http protocol.
-
It looks like internal agent is browsing the web.
| |
| Attack Methods | This Trojan can work through any firewall which allows users to access the Internet. It is the reverse of a straight HTTP tunnel. The program is run on the internal host, which spawns a child every day at a special time. The child program appears as a user to the firewall, which in turn allows it to access the Internet. However, this child program executes a local shell and connects to the web server owned by the attacker on the internet through a legitimate looking http request and sends it 'ready' signal. The legitimate looking answer of the web server owned by the attacker is in reality the commands the child will execute on its machine's local shell. All traffic will be converted into a Base64 like structure and given as a value for a cgi-string to prevent caching. |
Example of a connection:
-
Slave
GET /cgi-bin/order?M5mAejTgZdgYOdgIOoBgFfVYTgjFLdgxEdbiHe7krj HTTP/1.0
-
Master replies with
g5mAlfbknz
For instance, The GET of the internal host (SLAVE) is just the command prompt of the shell; the answer is an encoded "Is" command from the hacker on the external server (MASTER). The SLAVE tries to connect daily at a specified time to the MASTER if needed; the child is spawned because if the shell hangs for whatever reason the attacker can check and fix it the next day.
In case the administrator sees connects to the attacker's server and connects to it himself he will just see a broken web server because there's a Token (Password) in the encoded cgi GET request; WWW Proxies (e.g. squid) are supported; program masks it's name in the process listing. The programs are reasonably small with the master and slave program just one 260-lines perl file Usage is simple: edit rwwwshell.pl for the correct values, execute "rwwwshell.pl slave" on the SLAVE, and just run "rwwwshell.pl" on the MASTER just before it is time that the slave tries to connect.
Sample of Reverse Http Shell:
Http Http Internal------------>PROXY-->FIREWALL<---------->Attacker SLAVE MASTER
| Countermeasure | Countermeasure It is clear that a tight application gateway firewall with a strict policy is essential. Ideally DNS resolving should be only done on the WWW/FTP proxies and access given to WWW with prior proxy authentication only. Mails should be on a separate server. A secure solution would be to set up a second network which is connected to the internet, and the real one kept separated. |
| |
-
Most commercial ant-virus products can automatically scan and detect backdoor programs before they can cause damage (Eg. before accessing a floppy, running exe or downloading mail)
-
An inexpensive tool called Cleaner (http://www.moosoft.com/cleanet.html) can identify and eradicate 1000 types of backdoor programs and trojans.
-
Educate your users not to install applications downloaded from the internet and e-mail attachments.
| |
Perhaps the old adage 'Prevention is better than cure' holds the greatest relevance here.
| Countermeasure | The first line of defense is to educate users regarding the dangers of installing applications downloaded from the Internet and to take great caution if they have to open any mail attachment. |
| Countermeasure | The second line of defense can be antivirus products that are capable of recognizing Trojan signatures. Ensure that these updates are regularly applied over the network. |
| Countermeasure | The third line of defense comes from keeping application version updated by following security patches and vulnerability announcements. |
An inexpensive tool called Cleaner (http://www.moosoft.com/cleanet.html) can identify and eradicate 1000 types of backdoor programs and Trojans. Some of the other anti-Trojan software is:
-
TDS-3 (http://tds.diamondcs.com.au)
-
Hacker Eliminator (http://www.lockdown2000.com)
-
TFAK5 (http://www.snake- basket .de/tfak/TFAK5.zip)
-
Trojan Remover (http://www.simplysup.com/tremover/details.html)
-
Pest Patrol (http://www.safersite.com/)
-
Anti-Trojan (http://www.anti-trojan.net)
-
Tauscan (http://www.agnitum.com/products/tausean)
-
The Cleaner (http://www.moosoft.com)
-
PC Door Guard (http://www.trojanclinic.com/pdg.html)
-
Trojan Hunter (http://www.mischel.dhs.org/trojanhunter.jsp)
-
LogMonitor (http://www.logmon.bitrix.ru/logmon/eng/)
| |
| |
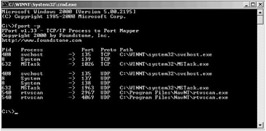
| Tools | fport supports Windows NT4, Windows 2000 and Windows XP. fport reports all open TCP/IP and UDP ports and maps them to the owning application. This is the similar to the information seen using the 'netstat-an' command. However, it also maps those ports to running processes with the PID, process name and path. Fport can be used to quickly identify unknown open ports and their associated applications. The applications are not shown by netstat -a command. |
Usage:
C:\>fport Pid Process Port Proto Path 392 svchost -> 135 TCP C:\WINNT\system32\svchost.exe 8 System -> 139 TCP 8 System -> 445 TCP 508 MSTask -> 1025 TCP C:\WINNT\system32\MSTask.exe 392 svchost -> 135 UDP C:\WINNT\system32\svchost.exe 8 System -> 137 UDP 8 System -> 138 UDP 8 System -> 445 UDP 224 lsass -> 500 UDP C:\WINNT\system32\lsass.exe 212 services -> 1026 UDP C:\WINNT\system32\services.exe
The program contains five (5) switches. The switches may be utilized using either a '/' or a ' -' preceding the switch. The switches are;
/? usage help, /p sort by port, /a sort by application, /i sort by pid, /ap sort by application path.
| |
| |
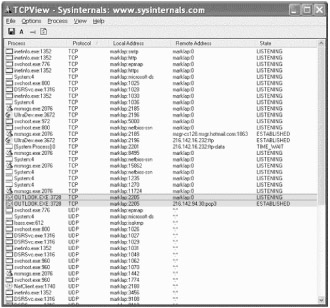
| Tools | TCPView is a Windows program that will show detailed listings of all TCP and UDP endpoints on the system, including the local and remote addresses and state of TCP connections. On Windows NT, 2000 and XP TCPView also reports the name of the process that owns the endpoint. |
TCPView provides a more informative and conveniently presented subset of the Netstat program that ship with Windows. TCPView works on Windows NT/2000/XP and Windows 98/ME. Using TCPView
When TCPView is run, it will enumerate all active TCP and UDP endpoints, resolving all IP addresses to their domain name versions. On Windows XP systems, TCPView shows the name of the process that owns each endpoint.
By default, TCPView updates every second. Endpoints that change state from one update to the next are highlighted in yellow; those that are deleted are shown in red, and new endpoints are shown in green. The user can close established TCP/IP connections (those labeled with a state of ESTABLISHED) and save TCPView's output window to a file as well.
A similar utility TDImon allows the user to monitor TCP and UDP activity on your local system. It is the most powerful tool available for tracking down network- related configuration problems and analyzing application network usage. On Windows NT and Windows 2000, simply execute the TDImon program file (tdimon.exe) and TDImon will immediately start capturing TCP/IP activity. As events are printed to the output, they are tagged with a sequence number.
| |
| |
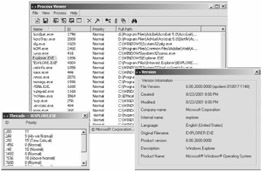
| Tools | PrcView is a process viewer utility that displays detailed information about processes running under Windows. For each process it displays memory, threads and module usage. For each DLL it shows full path and version information. |
PrcView comes with a command line version that allows the user to write scripts to check if a process is running, kill it, etc. The main window shows a list of running processes including information process Id, priority, and full path to the process module. The user can sort columns by clicking on the column header
With the Process Finder Tool one can find the process corresponding to a selected window. The Process Tree shows the process hierarchy for all running processes. The desired task can be selected by clicking on the process item in the Process Tree window.
Module Usage gives information about all loaded modules in the system including the module name, the module base address in process space, the module size and full to the loaded module path. Selecting a module from the module list shows only processes which use a selected module.
Kill process is just another way to kill a selected process. Note that killing a process can cause undesired results including loss of data and system instability. The process will not be given a chance to save its state or data before it is terminated. It is advisable to try the "Notify" button in the "Kill" dialog to close a GUI-based application first (via WM_SYSCOMMAND)
| |
http://ntsecurity.nu/cgi-bin/download/inzider.exe.pl
-
This is a very useful tool that lists processes in your Windows system and the ports each one listen on.
-
For instance, under Windows NT/2K, BO2K injects itself into other processes, so it is not visible in the Task Manager as a separate process.
-
When you run Inzider, you will see the port BO2K has bound in its host process
| |
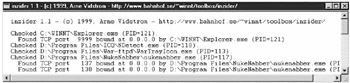
| Tools | Insider allows the user to see applications running on his system along with the listening ports they are using. Inzider is not infallible. It is possible for an application which is holding open a listening port to hide from Inzider probes. Still, Inzider provides a quick health check which may help in identifying some of the less advanced Trojans that are floating around. |
Inzider does not perform any registry or INI file changes which make it easily portable as well (as it is less than 100K). Inzider can find running applications missed out by netstat sometimes. The "PID" shown is the Process ID" used by the system to identify the running program from others that are running at the same time. Inzider can also verify which program is holding open a listening port.
Unfortunately Inzider is not 100% effective. Inzider will run on Win95, Win98 and NT based systems. However, on Windows NT/2000/XP, Inzider is still unable to check processes started as services. While Inzider is useful for making a first look at the system's health, some additional checks are in order to insure that the system is secure.
| |
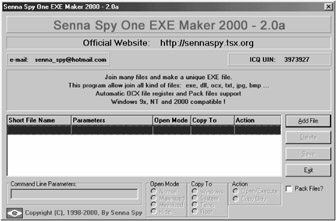
http://sennaspy.cjb.net/
-
Senna Spy Generator 2.0 is a trojan generator. Senna Spy Generator is able to create a Visual Basic source code for a trojan based on a few options.
-
This trojan is compiled from generated source code, anything could be changed in it.
Server Features
Change wallpaper
Chat with server
Execute DOS commands
Find files
FTP server
Hang up Internet connection
Open/close CD-Rom
Play AVI or WAV
Reset windows
Send keys
| |
| Tools | Senna Spy Trojan generator is a program that's a world first; in that it can actually make a customized Trojan for the user in a matter of minutes. This Trojan is controlled by telnet making it possible for any operating system to run. The default port which this Trojan opens is port 11000 but this is configurable. Another feature of this Trojan is the ability to access the infected computers file system with an ftp client such as cute ftp or Ws ftp, this aspect of senna spy is pretty scary because it gives the hacker power to download and upload any file of choice. The tool also comes with its own generator and uses VB script. |
| |
http://www.hackology.com/programs/hdkp/ginfo.shtml
-
The Hard Drive Killer Pro series of programs offer one the ability to fully and permanently destroy all data on any given Dos or Win3.x/9x/NT/2000 based system. In other words 90% of the PCs worldwide.
-
The program, once executed, will start eating up the hard drive, and or infect and reboot the hard drive within a few seconds.
-
After rebooting, all hard drives attached to the system would be formatter (in an un recoverable manner) within only 1 to 2 seconds, regardless of the size of the hard drive.
| |
| Tools | The Hard Drive Killer Pro series of programs offer one the ability to fully and permanently destroy all data on any given Dos or Win3.x/9x/NT/2000 based system. After it is run, it is goes about destroying every existing Hard Drive in the computer. The person only needs to run it for a few seconds, and then even if they exit the program without letting it stuff up their hard drive, it will continue from where it left off when it restarts. So there is no escape. |
The program, once executed, will start eating up the hard drive, and/or infect and reboot the hard drive within a few seconds. After rebooting, all hard drives attached to the system would be formatted (in an unrecoverable manner) within only 1 to 2 seconds, irregardless of the size of the hard drive.
HDKP 4.0 EXE on the other hand, is the same as HDKP 4.0's .bat edition, in the EXE version is a compressed version of the BAT file, and when executed, extracts the bat file from the exe file and executes the bat file. Hard Drive Killer Pro 5.0 is also due to be released in DOS (exe) and DOS (bat) versions. These editions should be noticeably smaller in size.
The Hard Drive Killer Pro (and some of its previous versions) totally eliminates data on the Hard Drive and kills the FAT (that's, File Allocation Table, we are not talking about Fat Cells ) of the computer it's used on.
| |
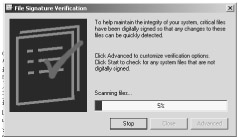
-
Windows 2000 introduced Windows File Protection (WFP) which protects system files that were installed by Windows 2000 setup program from being overwritten.
-
The hashes in this file could be compared with the SHA-1 hashes of the current system files to verify their integrity against the 'factory originals '
-
sigVerif.exe utility can perform this verification process.
| |
| Countermeasure | In Windows 2000, Windows File Protection prevents the replacement of protected system files such as .sys, .dll, .ocx, .ttf, .fon, and .exe files. Windows File Protection runs in the background and protects all files installed by the Windows 2000 setup program. This includes roughly 660 files under %systemroot%. Windows 2000 hashes these files with SHA-1 algorithm and stores these hashes in %systemroot% \system32\dllcache\nt5.cat |
Windows File Protection detects attempts by other programs to replace or move a protected system file. Windows File Protection checks the file's digital signature to determine if the new file is the correct Microsoft version. If the file is not the correct version, Windows File Protection either replaces the file from the backup stored in the Dllcache folder or from the Windows 2000 CD. If Windows File Protection cannot locate the appropriate file, it prompts you for the location. Windows File Protection also writes an event to the event log, noting the file replacement attempt.
File Signature Verification checks to see which system files are digitally signed and display its findings. To start File Signature Verification, click Start, click Run, and then type sigverif.
System File Checker (sfc.exe) is a command line utility that scans and verifies the versions of all protected system files after you restart your computer. If System File Checker discovers that a protected file has been overwritten, it retrieves the correct version of the file from the %systemroot%\system32\dllcache folder, and then replaces the incorrect file.
Syntax:
sfc [/scannow] [/scanonce] [/scanboot] [/cancel] [/quiet] [/enable] [/purgecache] [/cachesize=x]
| |
-
Tripwire will automatically calculate cryptographic hashes of all key system files or any file that you want to monitor for modifications.
-
Tripwire software works by creating a baseline "snapshot" of the system
-
It will periodically scan those files, recalculate the information, and see if any of the information has changed. If there is a change an alarm is raised.
| |
| Countermeasure | Originally released in 1992 by Gene Kim and Dr. Eugene Spafford (from the COAST Laboratory at Purdue University), Tripwire for Servers is one of the first examples of a general file integrity assessment tool. Written for the UNIX environment, and now available for Windows NT/2000, it provides system administrators the ability to monitor file systems for added, deleted, and modified files. Tripwire software works by creating a baseline "snapshot" of the system. |
It stores the snapshot in a database, and then verifies the system's integrity by checking its current state against the baseline. By comparing the current system to a snapshot of how the system should look, Tripwire software quickly and accurately identifies any added, changed, or deleted files. The program monitors key attributes of files that should not change, including binary signature, size, expected change of size, etc.
| |
-
Beast is a powerful Remote Administration Tool (AKA trojan) built with Delphi 7.
-
One of the distinct features of the Beast is that is an all-in-one trojan (client, server and server editor are stored in the same application).
-
An important feature of the server is that is using the injecting technology.
| |
| Tools | Beast is a powerful Remote Administration Tool (AKA trojan) built with Delphi 7. One of the distinct features of the Beast is that is an all-in-one trojan (client, server and server editor are stored in the same application). |
An important feature of the server is that is using the injecting technology. At the first run the server is injecting in the memory of winlogon.exe (on 9x systems in systray.exe). Afterwards, from winlogon.exe injections are performed in explorer.exe or Internet Explorer, according with the options chosen when building the server.
The main benefits of this type of running is that from winlogon.exe are monitoring the other injected applications and, by example, if the Internet Explorer is closed, from winlogon.exe will be started again and injected with the dll. If the server is injected in explorer.exe it won't be visible on any Task Manager. When the server is injected in Internet Explorer will be running under the System account on NT, will be visible in Task Manager, but in this way the firewalls could be more easily by-passed. It is not a big deal if it is visible in TaskMgr because in the case when the IE process is closed will be automatically run again.
The same running procedure will be performed when the injection occurred in explorer.exe. The server stability is almost 100%, the explorer.exe can't be crashed by closing the client during a file transfer or other operations). The server (dll) is residing in the windows/system directory and writes few registry entries, so the victim must have the appropriate privileges on NT platform. If the victim is a restricted user then the server won't run on NT (2k, XP).
The single way to get rid of Beast is booting in Safe Mode. Whenever the injected process (IE or explorer.exe) is closed, from the winlogon.exe the server will be injected again. All the servers (loaders) are locked from winlogon.exe, so cannot be deleted. The registry settings are also overwritten at every few seconds... The most easily way to uninstall the server is to connect from the client and click the Kill Server button.
| |
-
Trojans are malicious pieces of code that carry cracker software to a target system
-
Trojans are used primarily to gain and retain access on the target system
-
Trojans often reside deep in the system and make registry changes that allow it to meet its purpose as a remote administration tool
-
Popular Trojans include back orifice, netbus, subseven, beast etc.
-
Awareness and preventive measures are the best defense against Trojans.
| |
EAN: N/A
Pages: 109