Module Objectives
This module introduces the enumeration phase of hacking to the reader. It details different aspects of enumeration. On completing this module, you will be familiar with the following topics:
-
Understanding Windows 2000 enumeration
-
How to Connect via Null Session
-
How to disguise NetBIOS Enumeration
-
Disguise using SNMP enumeration
-
How to steal Windows 2000 DNS information using zone transfers
-
Learn to enumerate users via CIFS/SMB
-
Active Directory enumerations
The reader is urged to note that there is no 'one sure shot way' for hackers to approach a system. This is the basis behind stating that while countermeasures are suggested here, they are proposed in the light of the generic approach of hackers towards a system.
| |
-
If acquisition and non intrusive probing have not turned up any results, then an attacker will next turn to identifying valid user accounts or poorly protected resource shares.
-
Enumeration involves active connections to systems and directed queries.
-
The type of information enumerated by intruders:
-
Network resources and shares
-
Users and groups
-
Applications and banners
-
| |
We had seen in the previous modules how the attacker can gather necessary information about his target without really getting on the wrong side of the legal barrier . If all the previously discussed attempts fail to generate relevant or useful information, the attacker can extend his efforts by actually probing the target. This is significant in that the attacker crosses over to the target territory to unearth information about the network, shares users, groups, applications and banners.
| Note | The objective of the attacker will be to identify valid user accounts or groups where he can remain inconspicuous once he has compromised the system. Enumeration involves active connections being made to the target system, or subjecting it to directed queries made to a system. Normally, an alert and secure system will log such attempts. Often the information gathered is what the target might have made public - such as a DNS address. However, it is possible that the attacker stumbles upon a remote IPC share such as the IPC$ in windows, that can be probed with a null session and shares and accounts enumerated. |
| Concept | On ascertaining the security posture of the target, the attacker can turn this information to this advantage by exploiting some resource sharing protocol or compromising an account. The type of information enumerated by hackers can be loosely grouped into the following categories:
|
| |
-
The null session is often refereed to as the Holy Grail of Windows hacking. Null Sessions take advantage of flaws in the CIFS/SMB (Common Internet File System/ Server Messaging Block).
-
You can establish a Null Session with a Windows (NT/2000/XP) host by logging on with a null user name and password.
-
Using these null connections allows you to gather the following information from the host:
-
List of users and groups
-
List of machines
-
List of shares
-
Users and host SIDs (Security Identifiers)
-
| |
In the preceding modules we have seen how the attacker gleans information about the target without actually penetrating into the system. While port scanning has a degree of intrusiveness , the process of enumeration ranks higher in this context.
| Concept | In the enumeration phase, the attacker gathers information such as network user and group names , routing tables, and Simple Network Management Protocol (SNMP) data. In this module we will explore how an attacker can enumerate the network and what countermeasures can be taken to check this phase of attack. |
| Concept | Before we can get into the details of the attack, let us try to understand the underlying concept of null sessions. The windows operating system relies on the 'user' account for authentication. As the operating systems of this family have evolved, we have seen the addition of groups, policies, rights and other additional security measures being added in order to enhance the authentication process. |
However, in addition to the standard user, the OS also supports a unique type of user called the 'null' user, which is basically a pseudo-account that has no username or password, but is allowed to access certain information on the network.
The Null user is capable of enumerating account names and shares on domain controllers, member servers, and workstations. This makes the Null user, a user with no credentials, a potential means of attack by crackers to elicit information and compromise the system.
Let us take a look at a typical LANMAN sessions on Windows NT 4.0
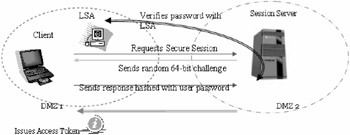
Remote machines establish a session with the Windows NT server using a challenge response protocol. The security of the information channel is ensured through a sequence of communications as outlined below.
-
The remote machine (or session requestor / client) sends a request to the session server (or session acceptor). This may be within the same domain or across domains.
-
The session server responds by sending across a random 64-bit challenge question to the client. The client responds to the question with a 24-bit answer which is hashed with the password of the user account that is requesting the session.
-
The session server accepts the response and verifies with the local security authority regarding the authentication of the user account and password.
-
The LSA confirms the identity of the requestor by verifying that the response was hashed with the correct password for the user that the requestor purports to be. This confirmation occurs locally if the requestor's account is a local account on the server. However, if the requestor's account is a domain account, the response is forwarded to the concerned domain controller for authentication.
-
On authenticating the response, an access token is generated by the session server and sent across to the client.
-
The client then uses this access token to connect to resources on the server till the newly established session is terminated .
Access tokens are executive objects that are managed by the operating system. These tokens cache information about a logon session for a particular user and holds true till the user logs out or uses another machine to access the particular resources. This eliminates the need for another authentication handshake when accessing related resources. This means network authentication protocols such as NTLM are only required when hopping from one machine to another. The NT security model can be viewed as shown below.
Once produced, the token provides two basic services: it stores the Security ID (SID) of the user that it represents and a cache of user information such as authorization information (groups and privileges).
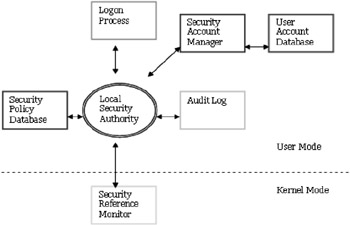
Windows NT 4.0 provided two key groups whose membership could be controlled by the administrator: Administrators and Users. There was one group, Everyone, whose membership was controlled by the operating system or domain. Every user who was authenticated by the domain was a member of the Everyone group.
Windows 2000 provides three groups whose membership is controlled by the administrator: Users, Power Users, and Administrators. The group whose membership is controlled by the operating system or domain is Authenticated Users. It is the same as the Everyone group, except that it does not contain anonymous users or guests. Unlike the Everyone group in Windows NT 4.0, the Authenticated Users group is not used to assign permissions. Only groups controlled by the administrator, primarily Users, Power Users, and members of the Administrators group, are used to assign permissions.
Now, let us take a look at a typical LANMAN sessions on Windows 2000
-
Here, the client sends a pre-authenticated (hash of user password) request along with a time stamp to the key distribution center (KDC) that resides on the domain controller (DC) of the concerned domain, requesting for a ticket granting ticket (TGT).
-
The KDC extracts the hash of the user identity from its database and decrypts the request with it, noting the time stamp as well for recentness of request. A valid user account results in successful decryption.
-
The KDC sends back a TGT, that contains among other information the session key (encrypted with users password) and the security identifiers (SID) identifying the user and the group among other things.
-
The client uses the ticket to access the required resources.
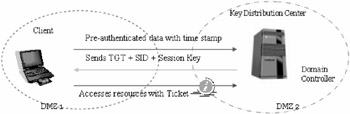
Note that the client sends a time stamped request so that the TGT may not be captured en-route and used later. The ticket thus generated primarily holds the domain name of the domain that issued the ticket and the name of the principal. Tickets also have a finite lifespan, with both the start and expiration of the session noted on it, client address and authorized access rights encrypted on it.
Having understood how windows sessions are established, let us take a look at the concept of null sessions in windows.
We have seen the role of the authenticator - the session server / KDC in ensuring that only authorized users are allowed to gain access to specified resources. What if there is no authenticator in establishing a session over the network? There is no way the particular server can ascertain who has initiated the session, whether it was hijacked or what resources were accessed. This session is therefore known as a null session.
The goal of authentication is primarily to establish a secure channel for communication and also to assure the resource provider that only an authenticated user is at the other end of the communication channel.
With null network credentials, there is no way to establish a secure session key. But since there are several instances where anonymous users may be allowed to access resources (- such as an administrator who wants to share resources among users in various domains, which are yet to be properly mapped) Windows has a built in mechanism for a null user (or a user with null network credentials to connect through what is known as a null session.
| Note | A null session is an insecure (unauthenticated) connection with no proof of identity. No user and password credentials are supplied in the establishment of the session. No session key is exchanged when establishing a null session, and hence it is impossible for the system to send encrypted or even signed messages on behalf of the user under a null session. |
When the LSA is asked to create a token for a remote client communicating via a null session, it produces a token with a user SID of S-1-5-7 (the null logon session), and a user name of anonymous logon. We have seen earlier that Everyone is included in all tokens, and the null session is classified as a network logon. This gives the null user access to file system shares and named pipes.
| Threat | Other areas where null sessions are considered useful is when the LMHOSTS.SAM file uses the "#INCLUDE <filename>" tag. The share point that contains the included file must be setup as a null session share. Additionally where a service, running under the local "SYSTEM" account, needs access to some network resource, a null session may be established to access these resources. |
| Threat | An interesting part is that Null sessions can also be established at the API level with languages such as C++. Null sessions can be used to establish connections to 'null session pipes', if it is allowed by the server. A 'pipe' is a facility that allows a process on one system to communicate with a process on another system, while a inter process communication share allows communication between two processes on the same system. |
| Threat | Null sessions can also be used to establish connections to shares, including such system shares as \\ servername \IPC$. The IPC$ is a special hidden share. It may be noted that the IPC$ share is an interface to the 'server' process on the machine, also associated with a pipe so it can be accessed remotely. Null sessions make the enumeration of users, machines, and resources easier for administrative purposes especially across domains. This is the lure for the attacker who intends to use a null session to connect to the machine. |
In the last module we have seen how port scanning is used to discover ports that are running services or in a listening state. During port scanning, the attacker takes note of any response from TCP port 139 and 445. Why would these ports interest an attacker? The answer lies in the SMB protocol.
The SMB (Server Message Block) protocol is known for its use in file sharing on Windows NT / 2000 series among other things. Attackers can potentially intercept and modify unsigned SMB packets then modify the traffic and forward it so that the server might perform undesirable actions. Alternatively, the attacker could pose as the server or client after a legitimate authentication and gain unauthorized access to data.
| Concept | SMB is the resource sharing protocol supported by many Microsoft operating systems; it is the basis of network basic input/output system (NetBIOS) and many other protocols. SMB signing authenticates both the user and the server hosting the data. In Windows NT it ran on top of NBT (NetBIOS over TCP/IP), making it a bulky protocol with a large header as well as consuming greater time. In Windows NT, it used the ports 137, 138 (UDP) and 139 (TCP). In Windows 2000, SMB was allowed to directly run over TCP/IP, without the extra layer of NBT. Therefore, port 445 started being used for this purpose. |
If the client has NBT enabled, it will always try to connect simultaneously to the server at both port 139 and 445. If there is a response from port 445, it sends a RST to port 139, and continues its SMB session to port 445 alone. However, if there is no response from port 445, it will continue its SMB session to port 139 alone on eliciting a response from the port. Needless to say, the session will completely fail if there is no response from either of the ports.
If the client has NBT disabled, it will always try to connect to the server at port 445 alone. If the server answers on port 445, the session will be established and continue on that port. The session fails in the absence of a response. This is the case if the server runs Windows NT 4.0.. In essence, if the server has NBT enabled, it listens on UDP ports 137, 138, and on TCP ports 139, 445. If it has NBT disabled, it listens on TCP port 445 only.
| Threat | Each SMB session consumes server resources. Establishing numerous null sessions will slow or possibly crash the server even in Windows 2003. An attacker could repeatedly establish SMB sessions until the server stops responding. SMB services will become slow or unresponsive . |
| |
-
Anyone with a NetBIO S connection to your computer can easily get a full dump of all your usernames, groups, shares, permissions, policies, services and more using the Null user.
-
The above syntax connects to the hidden Inter Process Communication 'share' (I PC $) at IP address 192.34.34.2 with the built- in anonymous user (/u:"") with ("") null password.
-
The attacker now has a channel overwhich to attempt various techniques.
-
The CIFS/SMB and NetBIOS standards in Windows 2000 include API s that return rich information about a machine via TCP port 139 - even to unauthenticated users.
C: \>net use \192.34.34.2 \IPC$ "" /u: ""
| |
Gaining NULL session access to a Win NT\W2K system is the number one method for attackers to enumerate information about a Win NT\W2K machine.
From a NULL session attackers can call APIs and use Remote Procedure calls to enumerate information. These sessions can provide information on passwords, groups, services, users and even active processors. NULL session access can also be used for escalating privileges and performing DoS attacks. A null session can only be made to TCP port 139, but other ports such as 135 (RPC endpoint mapping), 137 (NETBIOS Name Service) and 138 (NETBIOS datagram service) are often required for code to be called effectively.
The original purpose of null sessions was to allow unauthenticated machines to obtain browse lists from servers. As both NT and W2K coordinate systems based on the domain architecture concept, it was considered that null sessions would facilitate inter-domain browsing where the domain controllers did not share the same database of user and machine accounts - but still needed to browse for information across the domains.
Instances of such requirement are: need to acquire a browse list from a server in a different domain, authenticate a user in a different domain etc. Establishing trust relationships have solved this problem to a great extent, yet there remained much to be desired on the inter-connectivity front. Later, WINS, DNS, LMHOSTS, AD (Active Directory) were put forth to address this problem. However, Null sessions make this process much easier to accomplish, because they allow direct enumeration of machines and resources in a domain from an unauthenticated machine with little prior knowledge.
| Threat | The enumeration of machines and resources in a domain also makes it easier for an attacker to break in. If he is able to anonymously obtain the names of all of the machines in a domain, and then list the resource shares on those machines, it is only a matter of time before he finds a share which is open to "Everyone". Other possibilities include password cracking for a username that was enumerated, planting a backdoor for later access, dumping sensitive information etc. |
| Attack Methods | In the following pages we will try to see how this null session can be used by attackers to enumerate the system. Let us see how a null session is established and how a remote computer can be enumerated from the command line prompt of a windows machine. In the example shown below, we can see that establishing a null session on the target host reveals that the system root can be easily compromised as the default setting of 'Everyone' may not have been changed, and the shares are visible to all. |
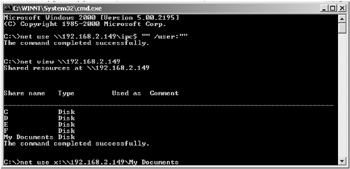
In a NULL session, the TCP/IP connection to port 139 is made first with the following: net use \\127.0.0.1.i\ipc$ "" /user:"". This is followed by using the session layer protocols SMB and NetBIOS to access the hidden remote IPC share IPC$. The IPC$ is a special hidden share which allows communication between two processes on the same system (Inter Process Communication). The IPC$ share is an interface to the 'server' process on the machine. It is also associated with a pipe so it can be accessed remotely. This technique was programmatically written into an old exploit called the Red Button attack. This was addressed and fixed by Microsoft in Service Pack 3 for NT 4.0.
RedButton revealed the resources available to the 'Everyone' group, determined the name of the built-in Administrator account (even if it has been renamed ), read various Registry entries ( revealing the registered owner's name and other information), and listed all shared resources (including hidden shares). In short, RedButton divulged sensitive information about an NT system. Null Sessions take advantage of flaws in the CIFS/SMB (Common Internet File System/Server Messaging Block) architecture.
Once the attacker has a list of the remote shares, he could then attempt to map to a remote share. An example of the command structure for the attack is shown in the screenshot above. This attack will only work if the share is not password protected or shared out to the 'everyone' group.
| Threat | Access to the hard drive is a serious security breach. Even if the attacker does not map a drive, he can gather sensitive information such user accounts, password policy and similar data that he can exploit later to continue his attack on the system. This may not be apparent to the victim initially, and the attacker can take the advantage of the time lapse for more information gathering and planting malicious code such as a virus or a Trojan. The open file share attack generally makes Trojan planting extremely easy to do. For instance, an intruder might try to place a key logger batch into the start-up folder to collect further information and perhaps log on later as an authenticated user. |
| |
-
Null sessions require access to TCP 139 and/ or TCP 445 ports.
-
You could also disable SMB services entirely on individual hosts by unbinding WINS Client TCP/IP from the interface.
-
Edit the registry to restrict the anonymous user.
-
Open regedt32, navigate to HKLM\SYSTEM\CurrentControlSet\LSA
-
Choose edit add value
value name: ResticAnonymous
Data Type: REG WORD
Value: 2
-
| |
| Countermeasure | "HKLM" refers to the hive "HKEY_LOCAL_MACHINE". If this is set to "1" anonymous connections are restricted. However, an anonymous user can still connect to the IPC$ share, though he is restricted as to which information is obtainable through that connection. A value of "1" restricts anonymous users from enumerating SAM accounts and shares. A Value of "2", added in Windows 2000, restricts all anonymous access unless clearly granted. Therefore, the first registry key to check would be: HKLM\System\CurrentControlSet\Control\Lsa\RestrictAnonymous The other keys to inspect are: HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters \NullSessionShares and HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters\NullSessionPipes |
These are MULTI_SZ (multi-line string) registry parameters that list the shares and pipes, respectively, that are open to null sessions. These keys should be verified so that no unwarranted shares or pipes are open. Moreover, those open should be secured such that only 'SYSTEM' or "Administrators' have access to modifying these keys.
In Windows 2000, the domain security policy lays down the protection measures for the domain controller. On systems that are not domain controllers, the 'Local Security Policy' must be configured to restrict anonymous connections. The value "No access without explicit anonymous permission" is the most secure and the equivalent of 2 in the registry value of the key HKLM\System\CurrentControlSet\Control\Lsa\RestrictAnonymous discussed above.
| Countermeasure | Another step that is advisable is to disallow remote access completely except for specific accounts and groups. It would be prudent to block NetBIOS ports on the firewall or border router to increase network security. Blocking the following ports will prevent against Null Sessions (as well as other attacks that use NetBIOS) |
135 TCP DCE/RPC Portmapper
137 TCP/UDP NetBIOS Name Service
138 TCP/UDP NetBIOS Datagram Service
139 TCP NetBIOS Session Service
445 TCP Microsoft-DS (Windows 2000 CIFS/SMB)
| Countermeasure | In Windows Server 2003, the policies called Network access: Do not allow anonymous enumeration of SAM accounts and Network access: Do not allow anonymous enumeration of SAM accounts and shares replace the Windows 2000 setting. They manage registry values called RestrictAnonymousSAM and RestrictAnonymous respectively, both located in the HKLM\System\CurrentControlSet\Control\Lsa\ registry key. |
| Countermeasure | A best practice that comes in handy is to stop all services that are not otherwise required for the functioning of the system. |
| |
-
NBTscan is a program for scanning IP networks for NetBIOS name information.
-
For each responded host it lists IP address, NetBIOS computer name, logged-in user name and MAC address.
-
The first thing a remote attacker will try on a Windows 2000 network is to get list of hosts attached to the wire.
-
net view / domain,
-
nbstat -A <some IP>
-

| |
| Note | The first step towards enumerating a windows machine would be to take advantage of the NetBIOS API. NetBIOS stands for Network Basic Input Output System .It was originally developed by IBM and Sytek as an Application Programming Interface (API) for client software to access LAN resources. |
We have seen how we can establish null sessions using NET.exe to connect to the IPC$ of remote machines. We have also seen how port scanning tools such as nmap can detect open ports and identify operating systems.
If an attacker notes a windows OS with port 139 open, he would be interested in checking what resources he can access or view on the remote system. This is shown in the screenshot above. However, to enumerate the NetBIOS names, the remote system must have enabled File and Printer Sharing.
Using these techniques the attacker can launch two types of attack on the remote computer having NetBIOS. He can choose to read/write to a remote computer system depending on the availability of shares. Alternatively he can launch a denial of service.
A recent instance was reported in August 2002 when Microsoft issued an advisory stating that an attacker could seek to exploit an unchecked buffer in network share provider on machines that have anonymous access enabled by sending a malformed SMB request to a target computer and crashing it.
| Attack Methods | Let us adopt an attacker's perspective to his port scan results. |
On finding port 139 open, the attacker can first use the nbtstat command
Usage: nbtstat [-a RemoteName] [-A IP_address] [-c] [-n] [-R] [-r] [-S] [-s] [interval]
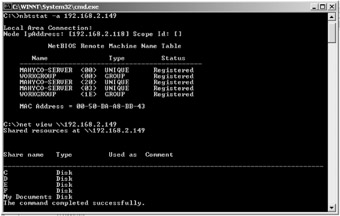
Note that an attacker will take particular interest in the id <03>. We try to connect to this remote machine using a null session. Usage: net use \\IP\IPC$ "" /user: "" This command connects to the machine using a null user and null password as signified by the empty quotes. The IPC$ is the hidden share on the particular IP that we will try to access in order to list any shared resources. Two main drawbacks of nbtstat are that it is restricted to operating on a single user and its rather inscrutable output. The tool NBTScan addresses these issues.
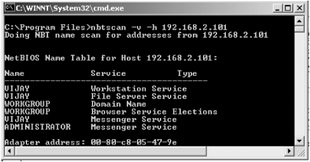
| Tools | A tool that can be used for such exploits is NBTScan written by Alla Bezroutchko and available at http://www.inetcat.org/software/nbtscan.html. NBTscan is a program for scanning IP networks for NetBIOS name information. It sends NetBIOS status query to each address in supplied range and lists received information in human readable form. For each responded host it lists IP address, NetBIOS computer name, logged-in user name and MAC address. NBTscan uses port 137 UDP for sending queries. If the port is closed on destination host destination will reply with ICMP "Port unreachable" message. See screenshot below. |
| |
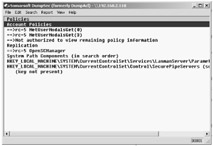
DumpSec reveals shares over a null session with the target computer.
| |
| Tools | DumpSec, presently available as freeware from SomarSoft and downloadable at http://www.systemtools.com/somarsoft/ , is a security auditing program for Windows systems. It dumps the permissions (DACLs) and audit settings (SACLs) for the file system, registry, printers and shares in a concise , readable listbox (text) format, so that holes in system security are readily apparent. DumpSec also dumps user, group and replication information. |
DumpSec takes advantage of the NetBIOS API and works by establishing NULL session to the target box as the Null user via the [net use \\server "" /user:""] command. It then makes NET* enumeration application program interface (API) calls like NetServerGetInfo (supported by the Netapi32 library).
It allows users to remotely connect to any computer and dump permissions, audit settings, and ownership for the Windows NT/2000 file system into a format that is easily converted to Microsoft Excel for editing. Hackers can choose to dump either NTFS or share permissions. It can also dump permissions for printers and the registry.
The highlight is DumpSec's ability to dump the users and groups in a Windows NT or Active Directory domain. There are several reporting options and the hacker can choose to dump the direct and nested group memberships for every user, as well as the logon scripts, account status such as disabled or locked out, and the 'true' last logon time across all domain controllers. The user can also get password information such as 'Password Last Set Time' and 'Password Expires Time'. To summarize, Dumpsec can pull a list of users, groups, and the NT system's policies and user rights.
| |
-
The NetBIOS Auditing Tool (NAT) is designed to explore the NetBIOS file-sharing services offered by the target system.
-
It implements a stepwise approach to gather information and attempt to obtain file system-level access as though it were a legitimate local client.
-
If a NETBIOS session can be established at all via TCP port 139, the target is declared "vulnerable".
-
Once the session is fully set up, transactions are performed to collect more information about the server including any file system "shares" it offers.
| |
| Tools | The NetBIOS Auditing Tool (NAT), written by Andrew Tridgell is designed to explore the NETBIOS file-sharing services offered by the target system. It implements a stepwise approach to gather information and attempt to obtain file system-level access as though it were a legitimate local client. |
The auditing tool starts a UDP query to the target, which usually elicits a reply containing the NetBIOS "computer name". This is needed to establish a session. The reply also can contain other information such as the workgroup and account names of the machine's users.
Next, TCP connections are made to the target's NetBIOS port [139], and session requests using the derived computer name are sent across. Various guesses at the computer name are also used, in case the status query failed or returned incomplete information. If all such attempts to establish a session fail, the host is assumed invulnerable to NETBIOS attacks even if TCP port 139 was reachable .
If a connection is established NetBIOS "protocol levels" are negotiated across the new connection. This establishes various modes and capabilities the client and server can use with each other, such as password encryption and if the server uses user-level or share-level security. If the server requires further session setup to establish credentials, various defaults are attempted. Completely blank usernames and passwords are often allowed to set up "guest" connections to a server; if this fails then guesses are tried using fairly standard account names such as ADMINISTRATOR, and some of the names returned from the status query. Extensive username/password checking is not done at this point, since the aim is just to get the session established, but it should be noted that if this phase is reached at all many more guesses can be attempted and likely without the owner of the target being immediately aware of it.
| Attack Methods | Once the session is fully set up, transactions are performed to collect more information about the server including any file system "shares" it offers. |
Attempts are then made to connect to all listed file system shares and some potentially unlisted ones. If the server requires passwords for the shares, defaults are attempted as described above for session setup. Any successful connections are then explored for writeability and some known file-naming problems.
If a NETBIOS session can be established at all via TCP port 139, the target is declared "vulnerable" with the remaining question being to what extent.
Information is collected under the appropriate vulnerability at most of these steps, since any point along the way be blocked by the security configurations of the target. Most Microsoft-OS based servers and Unix SAMBA will yield computer names and share lists, but not allow actual file-sharing connections without a valid username and/or password. A remote connection to a share is therefore a possibly serious security problem, and a connection that allows writing to the share almost certainly so. Let's take a look at an output from NAT.exe
C:\nat>nat 192.168.2.176 [*]--- Checking host: 192.168.2.176 [*]--- Obtaining list of remote NetBIOS names [*]-- Remote systems name tables: JOHN WORKGROUP JOHN JOHN WORKGROUP ................. [*]--- Attempting to connect with name: JOHN [*]--- CONNECTED with name: JOHN ................. [*]--- Attempting to establish session [*]--- Obtained server information: Server= [JOHN] User= [] Workgroup= [WORKGROUP] Domain= [WORKGROUP] [*]--- Obtained listing of shares: Sharename Type Comment --------- ---- ------ D Disk: IPC$ IPC: Remote Inter Process Communication [*]--- Attempting to access share: \JOHN\D [*]--- WARNING: Able to access share: \JOHN\D [*]--- Checking write access in: \JOHN\D [*]--- WARNING: Directory is writeable: \JOHN\D [*]--- Attempting to exercise... bug on: \JOHN\D
| |
-
SNMP is simple. Managers send requests to agents, and the agents send back replies.
-
The requests and replies refer to variables accessible to agent software.
-
Managers can also send requests to set values for certain variables.
-
Traps let the manager know that something significant has happened at the agent's end of things:
-
a reboot
-
an interface failure,
-
or that something else that is potentially bad has happened.
-
-
Enumerating NT users via SNMP protocol is easy using snmputil
| |
| Note | SNMP (Simple Network Management Protocol) is the system used on the Internet to manage all the equipment that makes up the Internet. The equipment that makes up the Internet consists of devices call "routers" that are interconnected via high speed phone lines. The most common use of SNMP is when an application sends queries at those routers requesting performance information on those lines. The goal is to detect which lines are congested (due to high traffic volume) in order to upgrade them to higher speed lines. |
SNMP is the most popular network management protocol in the TCP/IP protocol suite. It is a simple request/response protocol that communicates management information between two types of SNMP software entities: SNMP applications (also called SNMP managers) and SNMP agents.
| Concept | SNMP consists primarily of two objects: a manager and an agent. An agent consists of a piece of software embedded in a machine. SNMP agents exist for almost any piece of equipment. However, the installed agent doesn't do anything for the machine until queried by the manager. This is separate program that a network manager runs on their own computer that queries the agent (across the network) for information. |
A set of information is called a MIB (Management Information Base). Almost every agent has a minimal MIB that allows the manager to view the packets going into/out of the system. Beyond this basic MIB, each agent supports a different MIB that contains information about its particular purpose. For example, the Windows NT/2000 MIB will report on the current users on the machine, which drives are shared, and so forth.
SNMP lets TCP/IP-based network management clients use a TCP/IP-based inter-network to exchange information about the configuration and status of nodes. For security reasons, the SNMP agent validates each request from an SNMP manager before responding to the request, by verifying that the manager belongs to an SNMP community with access privileges to the agent.
An SNMP community is a logical relationship between an SNMP agent and one or more SNMP managers. The community has a name, and all members of a community have the same access privileges: either read-only (members can view configuration and performance information) or read-write (members can view configuration and performance information, and also change the configuration). The TRAP operation sends a message to the Management Station when a change occurs in a managed object (and that change is deemed important enough to generate an alert message).
| Concept | The default community string that provides the monitoring or read capability is often "public". The default management or write community string is often "private". The SNMP exploit takes advantage of these default community strings to allow an attacker to gain information about a device using the read community string "public", and the attacker can change a systems configuration using the write community string "private". In this section we will explore the SNMP Util tool for enumeration. |
| |
| |
| Threat | The security threat comes from Windows 2000 servers and workstations having SNMP support enabled and failing to change the default read-only community string 'Public'. However, changing this does not exempt it from attackers sniffing it from the network or to subjecting it to a dictionary or brute force attack. This may not seem troublesome but the Windows 2000 SNMP variables contain a wealth of information for the sniffing cracker. Some of the tables that are available when one has READ access to the SNMP tree in a Windows 2000 box are listed below:
|
Here, we will look at an SNMP utility called SNMPutil.exe which is a part of the Windows 2000 resource kit. Let us take a look at what we can discover with it from the command line prompt.
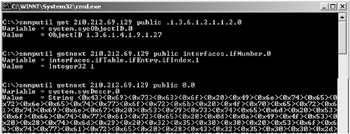
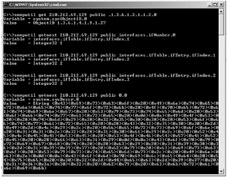
usage: snmputil [get getnext walk] target host community OID
In this output, the variable is called 1.3.6.1.2.1.1.2.0, and we 'get' its value, which turns out to be 1. The variable name (1.3.6.1.2.1.1.2.0) is called an object identifier or OID. An alternative to this is found in the second line of the output shown here. The 'interfaces.ifNumber.o' is the same OID, but is more easily readable. The second and third arguments to SNMPUTIL designate the host to which the SNMP request will be sent (210.212.69.129), and community (authentication string or password) to use (public). The 'public' community is the default when SNMP support is installed on a Windows 2000 host, and it allows the user to read all variables present. Since even the number of interfaces in a host is sensitive data, the threat is evident. Let us look at some of the other variables that might be of interest to an attacker and a security professional.
IpForwarding (1.3.6.1.2.1.4.1.0) - Is the host forwarding? This is not a good sign for a workstation.
IcmpInRedirects (1.3.6.1.2.1.5.7) - Is the host redirecting icmp messages?
TcpOutRsts (1.3.6.1.2.1.6.15) - A counter indicating the number of RSTs send by the box. This counter will increase rapidly when port-scanned.
UdpNoPorts (1.3.6.1.2.1.7.2) - A counter indicating traffic to ports where no service was present. Also a possible port-scan signal.
SNMP walk automates the whole process of getting the variables and can be redirected to an output file. To summarize, Snmputil can reveal details about services that are running, share names, share paths, any comments on shares, usernames and domain names etc.
| |
| |
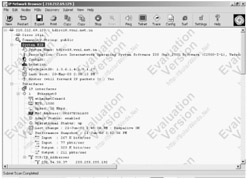
| Tools | SolarWinds IP Network Browser is an interactive network discovery tool. IP Network Browser can scan a subnet and show the details about the devices on that subnet. Each IP address is PINGed. For each responding address, IP Network Browser attempts to gather more information. It does this using SNMP (Simple Network Management Protocol). An SNMP agent must be active on the remote devices in order for IP Network Browser to gather details about the device. |
It is possible for an attacker to scan the entire subnet and discover more about the target network. For instance, he may stumble upon a router that may contain routing tables, details about TCP / IP networks, and other sensitive information.
The point to moot here is that a legitimate network discovery tool can be used for exploiting vulnerabilities in networks by crackers looking for sensitive information that can make their job easier. The degree of threat depends on the attacker's skills, knowledge, resources, authority, and motives. However, it is the vulnerability in victims that allow a threat to become effective.
With IP Network Browser it is possible to extract information from a poorly configured Windows system. These include server name and primary domain/workgroup, OS version, CPU type (and if it's multiprocessor or not), SNMP contact and location information (if defined), system uptime, system date/time, list of all user accounts, total ram, storage devices, volume label, device type, and partition type, running processes and process id's, installed applications and the date they were each installed, list of services, list of network interfaces (description, hw address, int speed, IP address, netmask , bytes in/out, status), list of all share names, file system location, and comments, routing table, TCP connections and listening ports and UDP listening ports.
| |
-
Simplest way to prevent such activity is to remove the SNMP agent or turn off the SNMP service.
-
If shutting off SNMP is not an option, then change the default 'public' community name.
-
Implement the Group Policy security option called Additional restrictions for anonymous connections.
-
Access to null session pipes and null session shares, and IPSec filtering should also be restricted.
| |
| Countermeasure | Do not install the management and monitoring windows component if it is not going to be used. In case it is required ensure that only legally authorized persons have access to it else, it might turn into an obvious backdoor. Edit the Registry to permit only approved access to the SNMP community Name. |
| Countermeasure | Change 'community' to properly configured ones - preferably with private community names (not the default "public"). Where possible, restrict access to SNMP agent. By restriction, we mean allowing SNMP requests from only specific addresses. Additionally, these requests should be restricted to read-only wherever possible. All these configurations can be done by changing the properties of the 'SNMP Service' (Start/Administrative Tools/Services). |
| Countermeasure | Authenticate/Encrypt using IPSEC - SNMP (V 1 ) may not have adequate authentication and encryption facilities built in but this is where IPSec can come to the rescue. IPSec policies can be defined in the monitored systems and management stations so that all SNMP traffic is authenticated and/or encrypted. |
| Coutermeasure | Collect Traps - If SNMP is enabled, monitor the Windows 2000 event logs. Effective auditing can actually raise the level of security. |
| |
-
For clients to locate Win 2k domain services such as Ad and kerberos, Win 2k relies on DNS SRV records.
-
Simple zone transfer (nslookup, ls -d <domainname>) can enumerate lot of interesting network information.
-
An attacker would look at the following records closely:
-
Global Catalog Service (_gc._tcp_)
-
Domain Controllers (_ldap._tcp)
-
Kerberos Authentication (_kerberos._tcp)
-
| |
| Threat | Windows server software comes pre-configured to allow zone transfers to any server. The importance of DNS lies in its analogy to a map or address book for a particular organization that has a presence on the Internet. It contains information such as host name and IP addresses of sites located on the Internet. Windows DNS is one of the fundamental services that are used by all windows 2000 networks that conform to the domain or forest tree model. Some of the functions of DNS servers include resolving host name to IP address and vice versa, instructing mail servers as to which mail server will accept and process mails for a particular Domain, identifying the official Name Servers for a particular Domain etc. |
| Concept | A zone transfer is an answer to a DNS query to list all DNS information (such as Name Servers, host names, MX records, CNAME records, glue records (delegation for child Domains), zone serial number, Time To Live (TTL) records, etc) for a Domain. The query can be made from a single host to look up information for the entire Domain. This can be done by the nslookup command we had discussed in earlier module. |
Besides this, the name servers use internal zone transfers to update its DNS data. The DNS data integrity is vulnerable during this process as a cracker can take advantage of this configuration. The default behavior for DNS zone transfer permits any host to request and receive a full zone transfer for a particular Domain. The importance of zone transfer lies in the fact that DNS data can be used by attackers to decipher the topology of the target network. The information obtained can be used for attacks such as DNS poisoning /spoofing.
| Attack Methods | DNS poisoning or spoofing is said to have occurred when someone (unauthorized) changes DNS information to something else. It can be accomplished through various methods such as man in the middle attacks (intercepting communication between two parties). Another possible method is to perform a Denial of Service attack on the Primary DNS Server making it too busy or unable to answer any DNS queries. In the meantime, another host assumes the identity of the Primary DNS Server and provides altered DNS information to the Domain's Secondary DNS Servers and the Internet community. In other words, the domain is essentially hijacked. False DNS information can then be propagated over the Internet. |
| Attack Methods | From a cracker's perspective, the cracker may launch websites to mimic the look and feel of the original website (to spoof the original) and even configured to handle secure web transactions such as SSL in order to provide users some sense of security. This can be a foil to compromise any online transactions and private information. Sensitive information may then be stolen, compromising not just the target's security posture, but its integrity and confidentiality as well. MX records may be changed to some other mail servers. All electronic mail destined to the domain can be redirected or lost, thereby compromising the mail servers. |
The FTP server may be redirected to some other server. Any data uploaded to the server can be stolen or lost. This is critical if the host's FTP server is a software repository for software drivers and patches. A step further in cracking would be to make available malicious software for download from a redirected fake FTP server. Depending on the security process of the Domain's Internet Registrar, the cracker can request the Internet Registrar to change the delegation for the domain to the fake Primary DNS server. If electronic mail is used for verification for changes and the electronic mail addresses are in the compromised domain, the delegation can be changed. The fake Primary DNS server becomes the official Primary DNS server known to the Internet and the Domain is hijacked as well.
The least a cracker can do is to redirect a corporation's web site or mail to a competitor, a non-business related web site, or nowhere. The result is still damaging .
| |
You can easily block zone transfers using the DNS property sheet as shown here.

| |
Knowing how to control zone transfers is extremely significant while securing DNS servers in a Windows environment. Windows 2000 allows for the alteration of the access lists available for each individual zone controls and zone transfer. Zone transfers are responsible for the movement of all the records for a particular zone from a domain server to the other.
| countermeasure | It is imperative to note that the forward lookup zone should not be transferred to a DNS server that conveys Windows 2000 domain information to any server outside the particular domain. This can be done in the Zone transfer tab of the properties of the specific domain name in the DNS MMC. This setting is extremely secure and does not pose a treat as there is no opportunity for the possibility of an impersonation or spoof of a clone zone transfer sever. |
| Countermeasure | Since client queries are transmitted on UDP port 53 and TCP port 53 is used for zone transfers, zone transfer port namely TCP port 53 should be blocked at the Internal, External, Firewall, and DMZ routers. If it is desired to know where the user is coming from when making a request on the DNS server it is necessary that the external DNS server has reverse DNS lookup Zones enabled. This system is used to verify where the intruder is coming from. If the DNS is configured to allow reverse lookup zone transfers between the Internal and External DNS servers the Internal Router, Firewall, and DMZ router should allow connections on TCP port 53 between the Internal and External DNS only. |
| Countermeasure | Additionally, it must be ensured that only the system and administrators have full control of the %SystemDirectory%\DNS directory and subfolders and that the all DNS servers have the registry secured. This can be achieved by ensuring that HKEY_LOCAL_MACHINE\System\Current Control Set\Services\DNS is assigned only to administrators and system as having full control. |
| |
-
Two powerful NT/2000 enumeration tools are:
-
sid2user
-
user2sid
-
-
They can be downloaded at (www.chem.msu.su/^rudnyi/NT/)
-
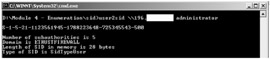
These are command line tools that look up NT SIDs from username input and vice versa.
| |
| Tools | user2sid and sid2user are two small utilities for Windows NT/2000 that allows the user to query SAM and to find out a SID value for a given account name and vice versa. These utilities are actually command line interfaces to WIN32 functions, LookupAccountName and LookupAccountSid. It happens that to use these functions a user have just to be EVERYONE. It means that an ordinary user can find without a problem a built-in domain administrator name, which MS recommends us to rename from administrator to something else. |
User2sid.exe can retrieve a SID from the SAM (Security Accounts Manager) from the local or a remote machine Sid2user.exe can then be used to retrieve the names of all the user accounts and more. Windows NT/2000 keeps track of User accounts and groups with Security Identifiers or SIDs. All SIDs are unique within a given system and are issued by what is known as an "Authority" such as a domain. There are five authorities:
-
SECURITY_NULL_SID_AUTHORITY (null user)
-
SECURITY_WORLD_SID_AUTHORITY (everyone)
-
SECURITY_LOCAL_SID_AUTHORITY (local user)
-
SECURITY_CREATOR_SID_AUTHORITY (creator owner /group)
-
SECURITY_NT_AUTHORITY
Note the default SIDs that captures a cracker's interest.
-
Administrator S-1-5-21-<........................>-500 and Guest S-1-5-21-<........................>-501
-
Domain Admins S-1-5-21-<........................>-512
-
Domain Users S-1-5-21-<........................>-513
-
Domain Guest S-1-5-21-<........................>-514
| Attack Methods | Let us take a look at the attack. |
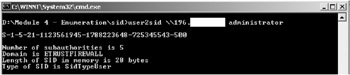
Here we try for the default built-in Administrator account - and we get access to more information such as domain and number of sub authorities.
Had we found the default guest account, we could escalate it to the Administrators group by changing the RID using the sid2user.
c:\>sid2user \196.xxx.xxx.xx 5 21 1123561549 1788223846 725345447 500
This will change the guest account to that of an administrator account. The last three digits (here 500) is the registered ID. Once a RID has been issued it will never be used again. Any group or user that is not created by default will have a RID of 1000 or greater.
Net use, user2sid and sid2user all operate over TCP port 139 - NetBIOS session. The reason why these utilities work despite having ACLs in place is that LookupAccountName and LookupAccountSID don't have ACL on them.
| |
-
Available for download from http:// razor .bindview.com
-
enum is a console-based Win32 information enumeration utility.
-
Using null sessions, enum can retrieve user lists, machine lists, share lists, name lists, group and membership lists, password and LSA policy information.
-
enum is also capable of rudimentary brute force dictionary attack on individual accounts.
| |
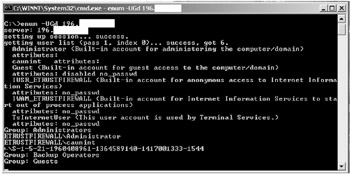
| Tools | enum is a tool written by Jordan Fitter to enumerate, using null and user sessions, Win NT/2000 information. enum is a console-based Win32 information enumeration utility. Using null sessions, enum can retrieve userlists, machine lists, sharelists, namelists, group and member lists, password and LSA policy information. enum is also capable of a rudimentary brute force dictionary attack on individual accounts. |
Usage:
enum <-UMNSPGLdc> <-u username> <-p password> <-f dictfile> <hostnameip> -U is get userlist -M is get machine list -N is get namelist dump (different from -U -M) -S is get sharelist -P is get password policy information -G is get group and member list -L is get LSA policy information -D is dictionary crack, needs -u and -f -d is be detailed, applies to -U and -S -c is don't cancel sessions -u is specify username to use (default"") -p is specify password to use (default"") -f is specify dictfile to use (wants -D)
| |
-
Userinfo is a little function that retrieves all available information about any known user from any NT/Win2k system that you can hit 139 on.
-
Specifically calling the NetUserGetInfo API call at Level 3, Userinfo returns standard info like
-
SID and Primary group
-
logon restrictions and smart card requirements
-
special group information
-
pw expiration information and pw age
-
-
This application works as a null user, even if the RA set to 1 to specifically deny anonymous enumeration.
| |
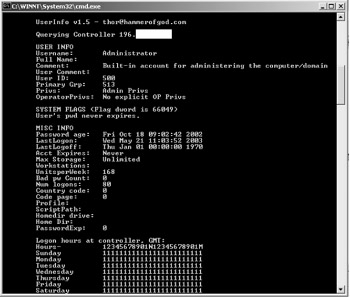
| Tools | UserInfo is a little function that retrieves all available information about any know user from any NT/Win2k system that has its port 139 open. The utility works as a null user, even if the system has RA set to 1 to specifically deny anonymous enumeration. |
There are other functions that also have poor ACL's on them, even after RA (Restrict Anonymous) is set to 1: NetServerTransportEnum and NetUserGetInfo. NetUserGetInfo, has different "levels" that can be designated as: Level 0 ~ Username, Level 1 ~ Username, age, homedir, etc, Level 2 ~ More details, Level 3 ~sensitive information. The utility specifically calls the NetUserGetInfo API call at Level 3.
UserInfo gets the low-down on the user account. It retrieves password age, full name and comments, userid (RID), last logon/ logoff , role privileges, operator privileges , user flags: all extended user attributes, account locked out, account disabled, password never expires, user can't change password, etc. It also works on Win2K, making it upwardly compatible to get Win2k extended attributes such as smartcard required and trusted for delegation, etc.
| FullName | Full name of the user. |
| Password | User's password. |
| Comment | Comment associated with the user. |
| UserComment | A second comment field. |
| HomeDirDrive | Drive where home directory resides. |
| HomeDir | Directory for user's home. |
| Profile | User Profile File. |
| LogonScript | User Logon Script name. |
| AccountDisable | Yes/No. Disables or enables the user's account. |
| Lockout | No. Clears the account lockout flag if the security system has locked it.out |
| PasswordExpired | Yes/No. Indicates that the user's password has expired . |
| PasswordNotRequiredaccount. | Yes/No. Indicates that a password is not required to log onto the |
| PasswordCannotChange | Yes/No. Indicates that the user is permitted to change their password. |
| PasswordDoesNotExpire | Yes/No. Indicates that the user's password doesn't expire. |
| Note | PasswordDoesnotExpire takes precedence over PasswordExpired. If PasswordDoesnotExpire is set, Windows NT/2000/XP ignores whether or not PasswordExpired is set. |
| |
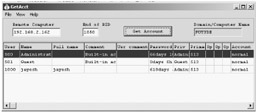
GetAcct sidesteps "RestrictAnonymous=1" and acquires account information on Windows NT/2000 machines.
Downloadable from (www.securityfriday.com)
| |
| Tools | GetAcct sidesteps "RestrictAnonymous=1" and acquires account information on Windows NT/2000 machines. Input the IP address or NetBIOS name of a target computer in the "Remote Computer" column. Input the number of 1000 or more in the "End of RID" column. The RID is user's relative identifier by which the Security Account Manager gives it when the user is created. Therefore, it is input as 1100, if there are 100 users. |
| Attack Methods | By opening an anonymous logon session, users can sometimes retrieve sensitive information about users and accounts on PDCs and other servers. GetAcct shows the information that leaks by opening an anonymous login and showing the following information:
|
| |
-
All the existing users and groups could be enumerated with a simple LDAP query.
-
The only thing required to perform this enumeration is to create an authenticated session via LDAP.
-
Connect to any AD server using ldp.exe port 389
-
Authenticate yourself using Guest /pr any domain account
-
Now all the users and built in groups could be enumerated.
| |
The most fundamental change introduced by Win 2000 is the addition of a lightweight Directory Access Protocol (LDAP) - based directory service that Microsoft calls Active Directory (AD).
| Concept | The active directory is a lot like any normal windows registry, except that the directory exists on the network and a windows network depends on the directory to function well. A cause for concern is that by default, authenticated users can view a number of things within the directory which they should not be able to view in a secure environment. For instance, users can view the domain configuration (DC=domain, DC=com), the schema (CN=Schema, CN=Configuration, DC=domain, DC=com), the configuration naming context (CN=Configuration, DC=domain, DC=com) etc. The schema is a section of the directory that defines what else can be stored in the directory. |
AD is designed to contain a unified, logical representation of all the objects relevant to the corporate technology infrastructure. The Windows 2000 simple LDAP client called the Active Directory Administration Tool (ldp.exe) that connects to an AD server and browses the contents of the directory.
| Threat | Simply pointing ldp at a Win 2000 domain controller will enumerate all of the existing usersand groups with a simple LDAP query. |
| Attack Methods | It connects over TCP port 389. An attacker finding this can use ldp.exe to create an authenticated session with the target using a known domain user account or a built in account or even a null session. This will give him the opportunity to enumerate all domain users and explore for other vulnerabilities. This is a real threat when the default setting of using clear text authentication is not changed. Other things available on the default settings include X.500 naming, DNS names and internal IP addresses, system time etc. |
| Attack Methods | Let us take a look at the attack. The attacker runs Ldp.exe (found in the Support \Reskit\Netmgmt\Dstool folder on the Windows 2000 CD-ROM). He can also write a script and run it against the target machine. He connects to the target server and verifies that the port setting is set to 389. Once the connection is complete, server-specific data is displayed in the right pane. |
On the Connection menu, he can choose to bind (as he does have access to the guest account in our scenario). There he types the user name, password, and domain name (in DNS format) in the appropriate boxes. If the binding is successful, he receives an authentication message. Now he can use "Search" found on the browse menu to gather information.
He can search for objects such as users, computers, contacts, groups, file volumes , and printers. Else, he can choose sites, subnets, site links, site link bridges, and forest structure. What would be interesting to him though will be the User Profile Path and Logon Script path of users.
An example of the output would be as follows :
>> Dn: CN=user1,CN=Users,DC=targetdomain,DC=com > profilePath: \w2k-dc-01\profiles\user1; > scriptPath: users.vbs; >> Dn: CN=user2,CN=Users,DC=targetdomain,DC=com > profilePath: \w2k-dc-01\profiles\user2; > scriptPath: users.vbs;
| Threat | These are sensitive material stored in a nicely centralized, organized, viewable container. For example, from here, the attacker can list all domain controllers. Information such as the drive and path of the sysvol on a particular domain controller, will aid an attacker to place files he needs to be replicated across the domain. Once this information has been obtained, these servers can be targeted individually if desired, as they are all listed within the DNS. |

| |
-
How is this possible with a simple guest account?
-
The Win 2k dcpromo installations screen prompts if the user wants to relax access permissions on the directory to allow legacy servers to perform lookup:
-
Permission compatible with pre-Win2k
-
Permission compatible with only with Win2k
-
-
Choose option 2 during AD installation.
| |
The active directory is similar to a windows registry, except that the active directory exists on the network and a windows network depends on the directory to function well. Therefore the implication of mishandling the registry holds good here also. Any mishandling of the active directory will render the entire network unusable. If an attacker alters objects in the active directory that he shouldn't it will affect the entire network. The good part of LDAP in is that one has to login just once to have access to all resources - which in turn is the security problem.
| CounterMeasure | Countermeasures include closing ports 389 and 3268 and upgrading all systems to Win2k before migrating to Active Directory. |
| Countermeasure | This will allow the sysadmin to "set permissions compatibility with Win2k only" when the dcpromo installation screen runs the option to allow legacy servers to perform look up. |
| Threat | If the AD network is installed with permissions compatible with pre-Windows 2000 networks, it grants most of the enumeration options that were available on NT 4 networks when an attacker established a null or IPC$ connection. This connection allows an attacker to gather information about users on the domain and can include listing of services on the server, which ones are running, descriptions of those services, and several other things. |
| |
-
Enumeration involves active connections to systems and directed queries.
-
The type of information enumerated by intruders includes network resources and shares, users and groups and applications and banners.
-
Null sessions are used often by crackers to connect to target systems.
-
NetBIOS and SNMP enumerations can be disguised using tools such as snmputil, nat etc.
-
Tools such as user2sid, sid2user and userinfo can be used to identify vulnerable user accounts.
| |
EAN: N/A
Pages: 109