Module 3: Scanning
Overview
| |

Tim had got the much needed break he was looking for. He was going to be assisting the systems administrator of his division in securing their information systems. It was a dream come true for him as he was always interested in incident response.
Tim began by browsing through the system architecture. Yes, they had the usual systems - firewall, mail server, NIDS and a couple of servers that were always up for remote users. At first sight, traffic seemed normal and there was nothing amiss. Anyway, he decided that he would just monitor the systems in his neighborhood for any abnormal activity.
-
where do you think Tim should begin with his security initiative?
-
What would the first signs that his systems are under attack?
| |
Tim had occasionally browsed some of the popular discussion forums for security related matters. He recalled some of the posts there about scanners and their use in auditing networks. He brought up this during a chat with the systems administrator Frank.
Frank informed Tim that he had indeed used scanners on their network and usually submitted the scan reports to the administration. Tim asked if he could take a look at the same. Frank agreed. This would be a great learning opportunity thought Tim.
Next day, when Tim checked the scan reports, he noticed that these were standard printouts from the commercial scanner they had used, with very little in terms of interpretation. Moreover, Tim noticed that the scanning pattern used by Burn was almost always the same. There were hardly any variations and Tim suspected they might be dealing with a security threat here itself.
Tim had experimented with a few scanners at home. He wondered if they would show up anything different. He had an idea... he would try to penetrate the network from outside. He figured that this would give him a better perspective. The only dilemma seemed to be whether he should seek Frank's approval before doing so? How would Frank react to this proposal?
Do you think that Tim should be seeking permission? Where do you think Tim should begin with his initiative and what would be the signs that his network is being compromi sed?
| |
-
Detecting 'live' systems on target network.
-
Discovering services running/ listening on target systems.
-
Understanding port scanning techniques.
-
Identifying TCP and UDP services running on target network.
-
Discovering the operating system
-
Understanding active and passive fingerprinting.
-
Automated discovery tools.
| |
On completion of this module you will gain an in-depth understanding of the hacking techniques involved in scanning and subsequent fingerprinting. The learning objectives of this module are to present the reader with the ability to:
-
Detect active systems on a target network
-
Discover services running / listening on the target system
-
Understand the techniques of port scanning
-
Identify TCP and UDP services running on the target network
-
Discover the operating system running on the target host
-
Understand active and passive fingerprinting techniques
-
Know more about automated discovery tools
It is strongly recommended that the reader possess a firm understanding of the various protocols such as TCP, UDP, ICMP and IP to understand this module better.
Once an attacker has identified his target system and does the initial reconnaissance as discussed in the previous module on footprinting, he concentrates on getting a mode of entry into the target system. It should be noted that scanning is not limited to intrusion alone. It can be an extended form of reconnaissance where the attacker learns more about his target, such as what operating system is used, the services that are being run on the systems and whether any configuration lapses can be identified. The attacker can then strategize his attack factoring these aspects.
| |
Why?
-
To determine the perimeter of the target network /system
-
To facilitate network mapping
-
To build an inventory of accessible systems on target network
Tools
-
War Dialers
-
Ping Utilities
| |
Let us continue with the reconnaissance phase detailed in the previous module. Once an attacker has gained sufficient information using any of the footprinting techniques, aided by various tools or utilities, he would like to know more about the individual systems.
| Note | A good attacker takes time to build an attack plan and also phases his attack so that he is undetected. The primary step in mapping a target network will be to find the limits of the network and assess the perimeter defenses. The attacker will seek to means of entry by building an inventory of the target network. This will give him an indication regarding any vulnerability that can be exploited and how well the network perimeters are guarded . An attacker might intrude with minimal footprint and lie low to assess what measures are being taken by the target network to detect the intrusion and defend it. |
| Attack Methods | Two categories of tools that can be used for this purpose are war dialers and ping utilities. War dialers try to exploit an unsecured modem to gain access into the system, while ping utilities try to ping the system to assess its current state and assess the presence of any packet filtering devices on the network. There are several freeware and commercial war dialers available. The silent rise in the number of war dialers appearing on the Internet is an indication that it is still possible to penetrate systems over an unsecured phone line. |
For instance, TBA, a war dialer for the Palm OS platform requires just a Palm Pilot and a Palm Modem or an external modem - providing a new war dialing platform option with a very small footprint. Commercial modem scanners such as PhoneSweep and TeleSweep Secure provide detection of both modems and faxes, identification by name of many systems found, automated reporting and the ability to dial in parallel from one pool of phone numbers using multiple modems.
| |
-
A war dialer is a tool used to scan a large pool of telephone numbers to detect vulnerable modems to provide access to the system.
-
A demon dialer is a tool used to monitor a specific phone number and target its modem to gain access to the system.
-
Threat is high in systems with poorly configured remote access products providing entry to larger networks.
-
Tools include THC-Scan, ToneLoc, TBA etc.
| |
| Concept | The term war dialing implies the exploitation of an organization's telephone, dial, and private branch exchange (PBX) systems to infiltrate the internal network and use of computing resources during the actual attack. It may be surprising why we are discussing war dialing here as more PBX systems are coming with increased security configurations. However, the fact remains that there are as many insecure modems out there that can be compromised to gain access into the target system. What had initially caught the fancy of hackers in the movie 'war games', still manages to find carriers leading to compromise of systems. The war dialer in War Games is not very sophisticated as it only finds phone numbers which are suspected to be computer dial-in lines. A more aggressive version might actually attempt to determine the operating system, and a very aggressive version might attempt to perform some automated break -in attempts itself. If A real scanner with this functionality will attempt to analyze the carrier information, the negotiation and presence of protocols and/or banners to attempt to determine the remote system. It will then attempt to use default username/password combinations for that system. |
The relevance of war dialers today arises from the fact that though internet connections have firewalls and intrusion detection systems installed, modems are still unsecured. As remote users are increasing, so are remote dial in connections to networks. Some of these remote users may not be using security precautions such as not storing passwords or personal firewalls, thereby allowing intruders to access the main network.
| Threat |
|
| |
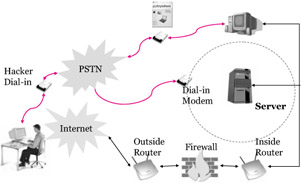
| |
We have seen that the attacker dials a number / pool of numbers he has discovered during his reconnaissance phase about a target network in order to connect to systems behind the target's firewall or perimeter defenses. War dialing involves the use of a modem with hacking software to penetrate the modem-based systems of an organization by repeatedly dialing the pool of telephone numbers. In this attack, the attacker attempts to find a 'dangerous user' within the network. A 'dangerous user' is one who poses a security threat due to lack of awareness and not because of intent. Usually, this user is someone who has an open connection through a modem - possibly unknown to the system personnel. In fact this user might be a well meaning employee who would like to access his system from home for putting in some extra work. He may use a remote access product such as pcAnywhere for dialing up the work PC from a remote location.
| Attack Methods | In the figure above, there is an 'out of band' connection established to the system on the network. An out of band connection is an alternative method to telnet or SSH for accessing a device remotely. The difference is that with an out of band connection, console port is used to access the device rather than going thorough the network. Also note the dial-in modem - usually allowed by organizations for maintenance. An attacker can access the network and find a list of vulnerable modems or use a password cracker to crack through those attached to a router. |
It is likely that there are unwatched modems with straight login prompts and pcAnywhere w/o passwords out there. There may be PCs with batch scripts to perform payroll, Sabre (airline reservation) systems, PCs that control the environment for buildings , and routers with modems attached to the console (which makes it easy to reboot on firmware so that the attacker can reset the 'enable' password). Add the fact that most companies do not have a plan for incident response. And, if they do, the modems are not watched in a centralized manner along with the systems personnel.
| |
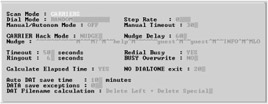
| |
For the purpose of study we will look at one of the most popular war dialers - THC Scan. Van Hauser, the brain behind the war dialer THC (The Hacker's Choice) points out that his tool is still able to do what really matters i.e., to find carriers.
| Tools | THC-Scan is a free war dialer released by "van Hauser" of The Hacker's Choice (THC), a European hacker/phreaker group . The current version, 2.0, was released in late 1998. THC -Scan was coded as a set of MSDOS-based programs that are designed to be run from the DOS command line with as much automation as possible. What sets THC Scan apart from other commercial dialers is the flexibility of its internal configuration that decides what to scan for and in which way to interpret the results. It does not serve the purpose of phone scanning alone, as it should and will show any number which behaves unusually if properly configured and used. |
| Attack Methods | An attacker can use THC-SCAN with THC Login Hacker to brute force systems that have been discovered. Being an open source code product, the dialer is often used by hackers as they are able to glean the workings of the application. The war dialer can dial telephone numbers from either a pre-determined range or from a given list. The scanner also possesses simple identification techniques that can be used to detect answering computer systems or voice mail boxes (VMBs). A manual mode is also available for users to dial the modem with the speaker enabled. THC-SCAN will automatically redial busy numbers up to a preset limit. |
An interesting feature is that THC has features that are designed to facilitate covert use, such as a "BOSS KEY" that replaces the computer's screen with an incongruous bitmap and ceases all dialing operation. THC-SCAN will automatically determine the parity of dial-up systems. The program does this by analyzing the parity of banner messages received after a remote system has been contacted. This is especially useful to an attacker who wants to call back a discovered system and attempt further penetration.
| |
-
Ping send out an ICMP Echo Request packet and awaits an ICMP Echo Reply message from an active machine.
-
Alternatively, TCP/UDP packets are sent if incoming ICMP messages are blocked.
-
Ping helps in assessing network traffic by time stamping each packet.
-
Ping can also be used for resolving host names .
-
Tools include Pinger, WS_Ping ProPack, NetScan Tools, HPing, icmpenum
| |
In the last module we have discussed traceroute. We saw the significance of time to live (TTL) in this regard. In this module, we start with a similar concept - Ping. The genesis of ping can be traced to the ARPANET days of Internet. It has been termed as Packet Internet Groper by some, while the author states it was named after the sonar concept. The functioning of Ping is very similar to the latter.
| Concept | This utility which is distributed across almost all platforms acts like a roll call for systems; where a system that is active on the network answers the ping query sent out by another system. |
| Note | To understand ping better, one should be able to understand the TCP/IP packet well. When a system does a ping, a single packet is sent across the network to a specific IP address. This packet contains 64 bytes - 56 data bytes and 8 bytes of protocol header information. |
The sender then waits or listens for a return packet from the target system. If the connections are good and the target computer is ' alive ', a good return packet can be expected. However, if there is a disruption in the communication, this will not be the case.
Ping also details the number of hops that lie between the two computers and the amount of time it takes for a packet to make the complete trip. This is called the 'roundtrip' time.
Ping can also be used for resolving host names - in this case, if the packet bounces back when sent to the IP address but not when sent to the name, then it is an indication that the system is unable to resolve the name to the specific IP address. Alternatively, ping can be used with the resolution switch.
Let's take a look at a Ping Packet
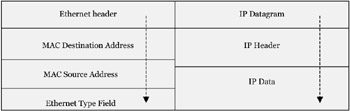
When we use the default ping setting of pinging with 32 bytes data, the actual ping length is 72 bytes, because it is comprised of the Ethernet Header, IP Datagram (IP Header and IP Data). The first fourteen bytes constitute the Ethernet Header. In this, the first six bytes are the MAC address of the destination system. The next six bytes denote the MAC address of the source system. The last two bytes in the Ethernet header indicates the Ethernet type.
The next sixty bytes of the packet forms the IP datagram - which can be further differentiated into the IP header (twenty bytes) and IP data (forty bytes). The IP header contains information such as IP Version occupies the first fourteen bytes, the IP header length occupies the next fourteen bytes, the source IP address is contained in four bytes and the destination IP address occupies the last four. The forty bytes of IP data includes 32 bytes of Echo Data. This is the ICMP Echo Request.
| Concept | Try to relate this to the TCP/IP protocol stack and the OSI layers . In the figure below, the first block is network media dependent and links to the data link layer (OSI layer 1 and 2). The second block is the IP protocol header and links to the inter-network layer (OSI layer 3), the third block relates to the transport protocol header and links to the transport layer (OSI layer 4), the fourth block relates to the application level data, largely depends on the network media and application state and links to the application layer (OSI layers 5 “7) and the last block is the data link trailer which is network dependent. |
| Source and destination MAC address information, upper layer protocol code. | Source and destination IP address, IP version number, Type of service, Time to live, header, checksum etc. | Source and destination port number information, header checksums TCP: sequence and acknowledge numbers, control flags | Optional application header, application data |
Readers are advised to read RFC 768 (UDP Protocol), 791 (IP Protocol), 792 (ICMP Protocol), 793 (TCP Protocol), 826 (Ethernet Protocol) to understand the protocols better.
| Note | From a security point of view, Ping can help deduce if packets are being dropped, duplicated or rehashed. However, it cannot determine exactly where in the network this has occurred or by whom or sometimes even why. This functionality is achieved by placing a unique sequence number on each packet transmitted. Ping allows detection of malformed or damaged packets as it performs a checksum on every packet exchanged. Ping helps in assessing network traffic by time stamping each packet. The Round Trip Time (RTT) indicates the time taken for the packet exchange between the two systems. Ping can also be used to echo other ICMP messages that are otherwise not reported by the system software. The various types and codes are shown below. |
| TYPE | CODE | Description | Query | Error |
|---|---|---|---|---|
|
|
| Echo Reply | X | |
| 3 |
| Network Unreachable | X | |
| 3 | 1 | Host Unreachable | X | |
| 3 | 2 | Protocol Unreachable | X | |
| 3 | 3 | Port Unreachable | X | |
| 3 | 4 | Fragmentation needed but no frag. bit set | X | |
| 3 | 5 | Source routing failed | X | |
| 3 | 6 | Destination network unknown | X | |
| 3 | 7 | Destination host unknown | X | |
| 3 | 8 | Source host isolated (obsolete) | X | |
| 3 | 9 | Destination network administratively prohibited | X | |
| 3 | 10 | Destination host administratively prohibited | X | |
| 3 | 11 | Network unreachable for TOS | X | |
| 3 | 12 | Host unreachable for TOS | X | |
| 3 | 13 | Communication administratively prohibited by filtering | X | |
| 3 | 14 | Host precedence violation | X | |
| 3 | 15 | Precedence cutoff in effect | X | |
| 4 |
| Source quench | ||
| 5 |
| Redirect for network | ||
| 5 | 1 | Redirect for host | ||
| 5 | 2 | Redirect for TOS and network | ||
| 5 | 3 | Redirect for TOS and host | ||
| 8 |
| Echo request | X | |
| 9 |
| Router advertisement | ||
| 10 |
| Route solicitation | ||
| 11 |
| TTL equals 0 during transit | X | |
| 11 | 1 | TTL equals 0 during reassembly | X | |
| 12 |
| IP header bad ( catchall error) | X | |
| 12 | 1 | Required options missing | X | |
| 13 |
| Timestamp request (obsolete) | X | |
| 14 | Timestamp reply (obsolete) | X | ||
| 15 |
| Information request (obsolete) | X | |
| 16 |
| Information reply (obsolete) | X | |
| 17 |
| Address mask request | X | |
| 18 |
| Address mask reply | X |
| |
| |
| Tools | Pinger is one of the fastest ICMP sweep scanners. Before we can discuss Pinger, let us take a look at the role of ICMP queries. Readers are encouraged to refer to RFC 792 to understand the ICMP (Internet Control Message Protocol) better. A quick recap: ICMP is for error reporting, gathering network information, flow control, and packet rerouting. The Ping and Traceroute -Unix uses UDP by default - utilities use ICMP. |
| Concept | RFC 792 states that the ICMP Identifier field can be used like a port in TCP or UDP to identify a session (though it does not use a port) and that the ICMP Sequence Number field can be incremented on each echo request sent. Therefore, ICMP Identifier field can be used to differentiate between ICMP Query messages sent to different hosts and the ICMP Sequence Number field can be used to differentiate between the ICMP query messages sent to the same host. |
ICMP packets can be used to determine whether a target IP address is alive or not, by simply sending an ICMP ECHO request (ICMP type 8) packets to the targeted system and waiting to see if an ICMP ECHO reply (ICMP type o) is received. If an ICMP ECHO reply is received, it means that the target is alive; No response could mean one of four different things: target is down, query was lost in transit, the traffic is being filtered or the system is configured not to respond. Querying multiple hosts using this method is referred to as Ping Sweep.
| Attack Methods | Ping Sweep is the most basic step in mapping out a network and considered an older approach to scanning a network. A ping sweep (also known as an ICMP sweep) is a basic network scanning technique used to detect live hosts from a range of IP addresses. |
The pinger's advantage lies in its ability to send multiple ICMP ECHO packets concurrently and wait for the response. It therefore helps resolve host names and save the output to a file. Pinger is designed for running on the Microsoft operating machines.
There is a need to point out that while UNIX and Linux follow the RFC suggestions in their deployment of the ping utility, MS shows a variation. MS systems keep the ICMP identifier as constant and use the sequence number field to differentiate between machines in their ping utility. For each ICMP Echo Request the ICMP Sequence Number is a unique number. The gap between one ICMP Sequence Number field value to another is 100 hex/256 decimal.
The implementation of the ping utility in MS systems sees the ICMP datagram fields as signed values based on the OS system used. This is in contrast with the UNIX systems which uses the values of the utility instead. Therefore whenever an ICMP Query datagram with an ICMP Identifier field value of 256/512/768 is generated, it indicates that the underlying operating system is MS based. This assumes significance as all security holes are operating system dependant and identifying which operating system runs on the target host / machine can shorten the attack phase.
Examples are:
-
Microsoft Windows NT - 256
-
Microsoft Windows 98/98SE - 512
-
Microsoft Windows 2000 - 512
-
Microsoft Windows ME - 768
-
Microsoft Windows 2000 Family with SP1 - 768
Logically, the next question should be the information that can be obtained from the sequence numbers. The MS ping implementation allows its OS to set the ICMP sequence number filed to 256 initially. In contrast, UNIX and related systems set their value to o on its first query to a host and will increase this number only if sequential queries are sent to the system. In other words, each time the ping command is used, the value o will be returned to the first query sent.
In MS based systems on the other hand, the value is incremented by 256 for each query sent. Therefore, to find the number of ICMP Query messages a Windows based OS has issued since the last boot time, simply divide the ICMP Sequence number field value with 256.
| |
Ping sweeps form a basic step in network mapping by polling network blocks and/or IP address ranges.
Ping Utilities include:
-
WS_PingProPack ( www.ipswitch.com )
-
NetScan Tools ( www.nwpsw.com )
-
Hping ( http://www.hping.org/download.html )
-
icmpenum ( www.nmrc.org/files/sunix/icmpenum-1.1.1.tgz )
Ping Sweep Detection Utilities include:
-
Network based IDS ( www.snort.org )
-
Genius ( www.indiesoft.com )
-
BlackICE ( www.networkice.com )
-
Scanlogd ( www.openwall.com/scanlogd )
| |
Ping sweeps form a basic step in network mapping by polling network blocks and/or IP address ranges. A ping sweep (also known as an ICMP sweep) is a basic network scanning technique used to detect live hosts from a range of IP addresses. It differs from a single ping in that while a single ping will indicate the availability of one specified host computer on the network, a ping sweep detects multiple hosts. A ping sweep consists of ICMP (Internet Control Message Protocol) ECHO requests sent to multiple hosts. If a given address is live, it will return an ICMP ECHO reply. Absence of a reply is taken as an indication that the system is not available on the network.
| Tools | There are a number of tools that can be used to do a ping sweep, such as, gping, and nmap for UNIX systems, and the Pinger software from Rhino9, fping and Ping Sweep from SolarWinds for Windows systems. Ping sweep utilities send multiple packets at the same time and allow the user to resolve host names and save the output to a file. |
Why are we dealing with ping sweeps outside our forthcoming discussion on port scans ? The answer likes in the protocol. ICM P does not use ports and hence does not fall under port scanning. Moreover, ping sweeps are a small part of network scanning (discovery) which has to be done before any port scanning.
| Concept | As discussed earlier under Pinger, windows systems don't respond to IC MP broadcasts while many older UNIX implementations still do. What if a firewall installed at the target network has blocked ICMP Echo requests? The attacker can still gain information by using ICMP type 13 messages (TIMESTAMP) and type 17 (Address Mask Requests). Readers interested in learning more can refer to Ofir Arkin's paper on "ICMP Usage in Scanning or Understanding some of the ICMP Protocol's Hazards". He also has a tool called Xprobe that uses ICMP to scan the network _ |
| Tools | Xprobe is an active OS fingerprinting tool based on Ofir Arkin's "ICMP Usage in Scanning" Research project. Xprobe is an alternative to some tools which are heavily dependent upon the usage of the TCP protocol for remote active operating system fingerprinting. Xprobe I combine various remote active operating system fingerprinting methods using the ICMP protocol, into a simple, fast, efficient and a powerful way to detect an underlying operating system a targeted host is using. Xprobe2 is an active operating system fingerprinting tool with a different approach to operating system fingerprinting. Xprobe2 rely on fuzzy signature matching, probabilistic guesses, multiple matches simultaneously , and a signature database. We will be detailing fingerprinting later in this module. Let us take a look at some of the ping utilities discussed here. |
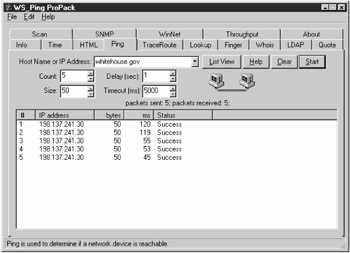
| Tools | WS_Ping ProPack WS_Ping ProPack implements a 32 bit graphical PING client for Windows replacing the old freeware WSPING32 application. Additional functionality of this program is the inclusion of Traceroute, Domain Name Service (DNS) lookup, Finger, Whois, LDAP, SNMP and SCAN IP. |
| Tools | NetScan Tools NetScan Tools Pro 2003 has added features to the standard ping utility such as subnet masking, where the tool sends an ICMP Address Mask request to the tar get and reports results. |
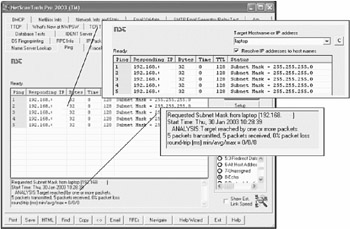
It is worth mentioning that these tools include several other features. Ping and Traceroute now include graphing capability. This means that we can now show the packet verses the response time. Another example is MAC address gathering from Windows computers via NetBIOS. It also gathers ARP and subnet mask information. The data gathered during a sweep can be viewed in report form by double clicking on a target. All drilldown info can be merged and exported. There is a full hosts file editor.
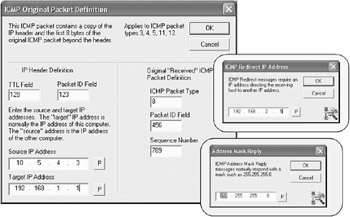
The custom ICMP Generator is a tool for generating any ICMP packet type o -31 including the usual codes. This option can synthesize a packet completely including "source" and "destination" IP addresses that would appear in the "original" packet that would have caused the generation of the packet in the first place. See screenshots below.
Let us adopt an information gather's perspective here. The Ping is not restricted to just knowing if the system is alive. It can reveal much more information depending on the needs of the user. For instance, what does a subnet mask and IP reveal?
In our discussion on ping we had seen how the hexdump of a ping packet can reveal MAC address and IP of the machine. If we can obtain the subnet mask, we can decipher the network address. Let us take a look at an example.
| Note | Suppose we discover the subnet mask of an IP Address: 178.241.153.93 as 255.255.252.0 |
Converting this IP into binary form we read as: 10110010.11110001.1 0011001.01011101 Similarly, the subnet mask can be converted as: 11111111.11111111.11111100.00000000 The network address can be computed by adding these binary forms to obtain 10110010.11110001.10011000.0000000 or an IP of 178.241.152.0
Similarly, we can obtain the broadcast address by adding the OR of the subnet mask to the IP address. Using the same IP as above, on adding the OR of the subnet mask we get:
10110010.11110001.10011001.01011101 + 0000000.00000000.00000011.11111111 = 10110010.11110001.10011011.11111111 which is 178.241.155.255 or the broadcast address.
| Tools | hping hping is a command-line oriented TCP/IP packet assembler/analyzer. It supports TCP, UDP, ICMP and RAW-IP protocols, provides a traceroute mode, and can be downloaded from http://www.hping.org/download.html |
Written by Salvatore Sanfilippo (Antirez), the utility can also be used for firewall testing, advanced port scanning, network testing, using different protocols, TOS, fragmentation, manual path MTU discovery, advanced traceroute, under all the supported protocols, remote OS fingerprinting, remote uptime guessing and TCP/IP stacks auditing among other things.
The output from the target system is displayed in the format:
[size] bytes from [ip]: flags=[flags] seq=[x] ttl=[y] win=[z] time=[t]ms
The options available are:
| usage: hping host [options] |
|---|
| c - packets count |
| I - wait |
| n - numeric output |
| q - quiet |
| I - interface name |
| p-destination port (default o) [ctrl+z inc, double ctrl+z dec] |
| s - base source Port (default random) |
| T - ttl (default 64) |
| w - winsize (default 512) |
| h - show this help ) |
| v - show version |
| F- set FIN flag S - set SYN flag |
| R - set RST flag P - set PUSH flag |
| A - set ACK flag U - set URG flag |
| X - set X unused flag (0x40) Y = set Y unused flag (0x80) |
| f- split packets in two fragments (may pass weak acl) |
| x - set more fragments flag (maybe uselessness) |
| O - set fake tcp) data offset (instead of tcphdrlen / 4) |
| r - relativize id field (to estimate host traffic) |
| z - bind ctrl+z to ttl |
| Z - unbind ctrl+z |
| Tools | icmpenum We have seen how ICMP queries can be used for gathering more information regarding the target system / network. Sometimes, packet filtering devices such as IDS can block ICMP queries coming from outside the perimeter of the network. These filtering devices could be mis-configured and allow certain ICMP types such as those used by icmpenum . icmpenum not only uses ICMP Echo packets to probe networks, but also ICMP Timestamp and ICMP Information packets as well. This is particularly useful for have probing systems that have failed to block Timestamp or Information packet, despite having a filtering device. Additionally, it supports spoofing and promiscuous listening for reply packets. Another use is for upstream sniffing of trusted addresses. Running icmpenum -h gives the following screen: # ./icmpenum -h USAGE: ./icmpenum [opts] [-c class C] [-d dev] [-i 1-3] [-s src] [-t sec] hosts opts are h n p r v -h this help screen -n no sending of packets -p promiscuous receive mode -r receiving packets only (no -v verbose -c class C in x.x.x.0 form -i icmp type to send/receive, types include the following: 1 echo/echo reply (default) 2 timestamp request/reply 3 info request/reply -d device to grab local IP or sniff from, default is eth0 -s spoofed source address -t time in seconds to wait for all replies (default 5) host(s) are target hosts (ignored if using -c) |
Examples:
[Host A]# icmpenum 192.168.1.112 192.168.1.202
This will use the default of Echo packets to try and determine if 192.168.1.112 and 192.168.1.202 are live and available on the network.
[Host A]# icmpenum -i 2 -v 192.168.1.112
This will enumerate the specified host using Timestamp (option 2 under flag -i) packets in verbose mode.
[Host A]# icmpenum -i 3 -s 192.168.1.120 -p -v 192.168.1.118
This will enumerate host 192.168.1.118 using Information packets with a spoofed address of 192.168.1.120, and use the -p option to listen for the replies promiscuously. There are advanced uses of icmpenum, which will be detailed in later modules.
| Note | Remember that the ICMP protocol allows for error messages that would otherwise go unnoticed if another protocol is used. For instance, the verbose mode of icmpenum will not only report the total number of expected packets received (when in a receiving mode), but also "unexpected" ICMP packets being sent to the addresses being targeted. A network that has deployed countermeasures to trace the intruder will notice these ping packets in the "unexpected" count. IDS for example, can detect any further queries from the outside source and thereby check unauthorized flow of information. The threat lies in an attacker's ability to forge probes from authorized sources such as business partners and customers to start a denial of service (DoS ). |
Let's now take a look at ping sweep detection utilities.
| Tools | Snort An intrusion detection system is one way of detecting ping sweeps. There are several solutions such as snort. Snort is an open source IDS that is resourceful and lightweight. |
The primary distribution site for Snort is http://www.snort.org . Authored by Martin Roesch, Snort is a cross-platform, lightweight network intrusion detection tool that can be deployed to monitor small TCP/IP networks and capable of detecting a range of suspicious network traffic. Snort features rules based logging to perform content pattern matching and detect a variety of attacks and probes, such as buffer overflows, stealth port scans, CGI attacks, SMB probes etc. Snort also has real-time alerting capability.
| Note | Snort has three primary uses. It can be used simply as a packet sniffer such as tcpdump or as a packet logger useful for network traffic debugging. It can also be used as a complete network intrusion detection system. Snort logs packets as either tcpdump binary format or as Snort's decoded ASCII format to logging directories. These directories are named based on the IP address of the external host. There are also several plug-ins' which allow detection and reporting subsystems to be extended. E.g.: SnortSnarf is a statistic tool for Snort logs downloadable from http://www.silicondefense.com/software/snortsnarf/index.htm , ACID (Analysis Console for Intrusion Databases) is a database analysis tool for Snort which can be found at http://www.cert.org/kb/acid/ . |
bsd# snort -?
The output of the command is as follows .
-*> Snort! <*- Version 1.6.3 By Martin Roesch (roesch@clark.net, www.snort.org) USAGE: snort [-options] Options: -A Set alert mode: fast, full, or none (alert file alerts only) 'unsock' enables UNIX socket logging (experimental). -a Display ARP packets -b Log packets in tcpdump format (much faster!) -c Use Rules File -C Print out payloads with character data only (no hex) -d Dump the Application Layer -D Run Snort in background (daemon) mode -e Display the second layer header info -F Read BPF filters from file -g Run snort gid as 'gname' user or uid after initialization -h Home network = -i Listen on interface -1 Log to directory -n Exit after receiving packets -N Turn off logging (alerts still work) -o Change the rule testing order to PassAlertLog -0 Obfuscate the logged IP addresses -p Disable promiscuous mode sniffing -P set explicit snaplen of packet (default: 1514) -q Quiet. Don't show banner and status report -r Read and process tcpdump file -s Log alert messages to syslog -S Set rules file variable n equal to value v -t Chroots process to after initialization -u Run snort uid as 'uname' user (or uid) after initialization -v is verbose -V Show version number -? Show this information are standard BPF options, as seen in TCPDump
| Tools | Genius Another software that offers network and internet utility as a package is Genius. Written by Coda Hale in Delphi it has several online features. It is available under the GNU Public License and downloadable at http://www.indiesoft.com/genius322.exe . The package is efficient in aiding the user to use several popular Internet protocols swiftly from a single host. The other interesting aspect of this tool is its ability to assist the user in determining the level of activity the host registers on the connected network. At the time of writing, the available version is 3.2.2. Utilities include Finger client, FTP client (normal or passive mode capable), HTTP client (text-based), Ping client (ICMP), SMTP client, TELNET client, Time client, Traceroute client, Whois client, Current Connections tool, IP Scanner, Nslookup tool, POP3 Cleaner, Port lookup tool and Portscan detection routine. The IP scanner allows a user to perform a port scan that is configurable to a certain degree as shown in the screenshot below. While the speeds of the scan or the protocols used are not adjustable, the user can select target TCP ports through a simple Graphic User Interface (GUI). |
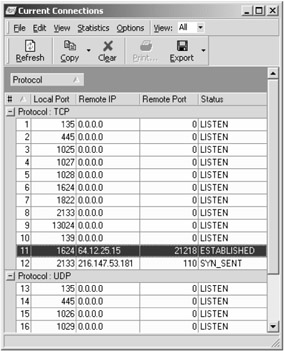
With the IP scanner, a user can scan a range of IP numbers or scan a list of IP numbers, check for any specified services running on each IP - ports can also be checked if specified, resolve hostnames, specify the number of packets to ping each IP, specify the packet size and how long to listen for a reply on each port. The user can also specify the number of milliseconds Genius will try to connect to each port for. After that time has expired , Genius will consider that port to be closed. The TTL can also be specified.
Once the scan is started, the program sends the set number of ICMP echo request to determine if a host is active for each IP address in the given range. If no ICMP echo reply is received, the application stops its efforts and moves onto the next IP. If a host replies, it is displayed in the IP Scanner window. For each active host, the statistics for the ICMP echoes is displayed, followed by information (including banners) that is made available for each TCP port that is found open.
| Tools | BlackICE BlackICE Defender is not just a firewall. Its primary function is that of an intrusion detection system. BlackICE Defender is, in reality, a "hybrid" between intrusion detection and firewall protection. The underlying technology of any firewall is to block the traffic at the port level. BlackICE Defender combines firewall technology with intrusion detection technology. This means that BlackICE uses more than one method to protect the system. BlackICE monitors /inspects the actual traffic, as well as employing port blocking, in order to detect malicious traffic and provide more complete security for your system. |
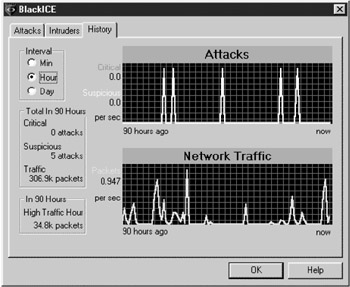
Black Ice Defender is an Intrusion Detection Device, not a Packet filter (per se). It is worthwhile to note that BlackICE be deployed on a clean system for maximum effectiveness.
| Tools | Scanlogd Written by Solar Designer and Steffen Dettmer, scanlogd is a program that detects port scans and writes one line per scan via the syslog(3) mechanism. This description is as sourced from the man pages. If a source address sends multiple packets to different ports in a short time, the event will be logged. |
The format of the messages is:
saddr[:sport] to daddr [and others,] ports port[, port...], ..., flags[, TOS TOS][, TTL TTL] @HH:MM:SS
The fields in square brackets are optional; sport, TOS, and TTL will only be displayed if they were constant during the scan.
The flags field represents TCP control bits seen in packets coming to the system from the address of the scan. It is a combination of eight characters , with each corresponding to one of the six defined and two reserved TCP control bits (see RFC 793).
Control bits that were always set are encoded with an uppercase letter, and a lowercase letter is used if the bit was always clear. A question mark is used to indicate bits that changed from packet to packet. Please note that due to the nature of port scans, both false positives (detecting a scan when there isn't one) and false negatives (not detecting a scan when there's one) are possible. In particular, false positives may occur when many small files are transferred rapidly with passive mode FTP.
As the name indicates, scanlogd only logs port scans. It does not prevent them. It will only deliver summarized information in the system's log. Obviously, the source address of port scans can be spoofed. Sometimes IP addresses are shared between many people; this is the case for ISP shell servers, dynamic dialup pools, and corporate networks behind NAT (masquerading).
| |
Why?
-
To determine live hosts in the event of ICMP requests being blocked by host.
-
To identify potential ports for furthering the attack.
-
To understand specific applications / versions of a service.
-
To discover operating system details.
Tools
-
Port Scanners
| |
| Concept | If "pinging" a system can determine if the system is active, where does the need for scanning arise? Ping was originally developed to use UDP packets but this would not generate an error message as the ICMP protocol does. This section focuses on port scanning. We have seen the nature of information that can be obtained from a ping sweep. |
| Attack Methods | However, an attacker would like to explore what ports exist on the target machine and whether any of the ports are open. Once he can detect an open port, he will attempt to discover the nature of service running on the port. This gives him an indication of any vulnerability (based on the service) that can be exploited to gain access into the target system. Another objective an attacker might have would be to discover the operating system details running on the target system. The category of tools used for this are the port scanners. While IDS or firewall can check port scanning to a great extent - if properly configured; it is not hacker proof entirely. Recall the reference to firewalk in the preceding module. |
Most often system administrators are misled into thinking that a firewall implementation can secure their systems. The popular categories of firewall deployment are the application proxies and the packet filtering gateways, with the former considered to render more security to the network. The biggest exploit vulnerability in any firewall is mis-configuration. How does an attacker probe a firewall? Now, every firewall has a unique way of identifying itself.
| Threat | Scanning and banner grabbing allow attackers to take advantage of this identification sequence. They may even be able to identify the version, type, and maybe even some certain rules. This may not seem relevant outwardly, however, once the firewall's strategic points are mapped, the attacker can probe further for weaknesses. Before furthering any discussion, let's take a look at the basics. |
| |
| |
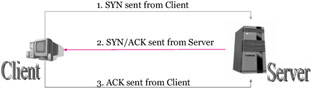
| Concept | To understand port scanning techniques better, it is essential to know how TCP connection is established between two systems as most scanners take advantage of this 'three -way handshake'. |

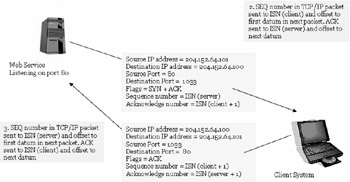
Once the three-way handshake has been completed, there is bi -directional communication over the connection.
The significance of TCP based applications is that TCP supports packet re-ordering, repeat transmission of lost packets, acknowledges packets and has flow control, which is important for message based applications.
| Note | The three-way handshake helps to synchronize the connection between two systems and use sequence and acknowledgment numbers to indicate data transmission and reception . The TCP flags control the flow of the session and this is technically what a port scanning program takes advantage of. These flags can be used t o collect port information. |
Port numbers, unlike IP numbers are not unique - though, they are unique to the system. They form the communication end points between systems. While the client system uses arbitrarily assigned port numbers, the server uses fixed port numbers to facilitate communication simultaneously with various systems. Readers are encouraged to read RFC 1700 to familiarize themselves with assigned port numbers. Within a network however, local hosts look up the "services" file for port number mappings. In UNIX, this is the text file names /etc/services while on Windows it is %windir%\system32\drivers\etc\services . The format is <service name> <port number>/<protocol>[aliases...][#<comment>] .An attacker getting access to this file to gets an entire communication mapping of the system.
| |
-
Port Scanning is one of the most popular reconnaissance techniques used by hackers to discover services that can be compromised.
-
A potential target computer runs many 'services' that listen at 'well-known' 'ports'.
-
By scanning which ports are available on the victim, the hacker finds potential vulnerabilities that can be exploited.
-
Scan techniques can be differentiated broadly into Vanilla , Strobe, Stealth, FTP Bounce, Fragmented Packets, Sweep and UDP Scans .
| |
| Note | One of the primary activities that an attacker undertakes while attempting to penetrate the system is to compile an inventory of open ports using any of the port scanning techniques. On completion, this list helps the attacker identify various services that are running on the target system using a RFC compliant port list (discussed before under the services file). This allows further strategizing leading to system compromise. |
We have discussed that ports form the communication ends between systems. Port numbers are 16-bit unsigned numbers and can be broadly classified into three categories. Port 0 “1023 is "well known ports", 1024 - 49151 are "registered ports" and 49152 - 65535 is "dynamic or private ports".
Port scanning usually means scanning for TCP ports, which being a stateful protocol - based on acknowledgement , gives good feedback to the attacker.
One problem with port scanning is that it is effortlessly logged by the services listening at the scanned ports. This is because they detect an incoming connection, but do not receive any data, thereby generating an application error log.
UDP, or connection-less (without acknowledgement) traffic, responds in a different manner. In order to scan for UDP ports, the attacker generally sends empty UDP datagram at the port. If the port is listening, the service will send back an error message or ignore the incoming datagram. If the port is closed, then the operating system sends back an "ICM P Port Unreachable" (type 3) message. Here, by the method of exclusion, the attacker can find open ports. Usually UDP ports are high end ports.
| |

Port Scanning Techniques can be broadly classified into:
-
Open scan
-
Half- open scan
-
Stealth scan
-
Sweeps
-
Misc
| |
| Concept | Port scanning techniques can be broadly differentiated into open scan, half-open scan and stealth scan. There are other techniques such as ICMP echo and FTP bounce, and these are covered under sweeps and miscellaneous scans. It is assumed that the reader is familiar with the various protocols as advised in the RFC reference discussed e arlier. |
How does an attacker decide on which scan to adopt? Well, this depends largely on the knowledge gained by the attacker during his reconnaissance regarding the type of network topology, IDS and other logging features present on the system. Predictably, an attacker would like to keep his actions undetected.
For the discussion on scanning techniques, the term 'client' will be used to denote the machine that opens an arbitrary port and the term 'server' will be the machine that uses standard ports.
| Concept | Open Scan / TCP Connect ( ) Scan 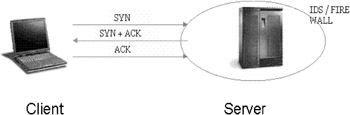 |
Let us discuss open scan first. These are also known as vanilla scans where a full connection is opened to the target system by a three-way TCP/IP handshake. Therefore, these are easiest to detect as well as to block on the network. However, the information gathered with an open scan is as best as it can get in determining the port state.
We have seen that the client sends a SYN flag, which is replied by a SYN+ACK flag by the server and which in turn is acknowledged back with an ACK flag by the client to complete the connection. This three-way handshake establishes connection from both ends and likewise be terminated from both ends individually.
In vanilla scanning, once the handshake is completed, the connection is terminated by the client allowing a new socket to be created or called. This confirms an open port. This automatically allows the next port to be scanned for a running service or 'listening' state. This goes on till the maximum port threshold is reached.
On the other hand if the port is closed or 'not listening' the server responds with a RST+ACK flag, (RST stands for 'Reset the connection') to which the client responds with a RST flag, thereby closing the connection. This is created by TCP connect () system call and thus identifying instantaneously if the port is open or closed.
The disadvantage of this scan technique to an attacker is that he cannot spoof his identity as spoofing would require sending a correct sequence number as well as setting the appropriate return flags to set up data connection. Moreover, most stately intrusion detection systems and firewalls detect and log this scan, exposing both the attempt and the attacker's IP address as it opens a complete connection that can be filtered or blocked. The advantage it renders is fast accurate scans that require no additional user privileges.
As with any scan, the challenge to the security professional will be to disallow the attacker knowledge of the machines and configuration behind the firewall, as well as the services which might be vulnerable to an attack. In this event, an attacker will attempt an inverse mapping technique.
| Concept | Inverse Mapping One of the first stealth scans to appear was the Inverse Mapping scan, which was reported in 1998 by the CERT Coordination Center. Inverse mapping indicates whether the target machine is alive or not from the absence of a response. In other words, absence of a predicted response indicates that the converse holds true. |
The modus operandi was to use packets with customized flags (RST (Reset) and SYN-ACK packets and DNS response packets) to find the response that target machine would broadcast. This type of scan did not find out information about the ports specifically that were open. A computer that was alive on the network would respond to the request, while a non-existent computer would generate an ICMP host unreachable error message. In this manner, an attacker could stealthily map out a network.
For instance, if a scanned port returns a RST response, it is an indication that the port is closed. In an inverse mapping scenario, absence of a RST response indicates that the port is open. However, this increases the possibility of registering false positives i.e. a false inference of a port being open even when it is closed. This could be due to the presence of a firewall or a packet filtering device that drops such scan packets.
| Concept | Ident Scanning Reverse ident scanning is a rather old form of scanning and mostly seen on UNIX and related machines. Most of these systems have applied patches and such scans are detected easily now. This technique involves emanating a response to the ident/auth daemon, which is usually on port 113 to query the service running there for the owner of the running process. The primary objective behind this scan is to discover root and exploit a vulnerable overflow or probe the system further. However, a system that is not a root might hold little to interest the user. |
Another reason this can be used is to gather miscellaneous information such as user information, entities, objects and processes that will otherwise remain private. This takes advantage of the identification protocol if it is acting as an authentication mechanism. Ideally, it should not be used as an access control service nor relied upon added host/username authenticity.
The formal syntax taken from RFC 1413 reveals the following EBNF:
FORMAL SYNTAX <request> ::= <port-pair> <EOL> <port-pair> ::= <integer> "," <integer> <EOL> ::= "015 012" ; CR-LF End of Line Indicator, octal \r\n equivalents <integer> ::= l*5<digit> ; 1-5 digits.
Using this grammar applied to the data sent to a server piped to the ident/auth port will reveal the process owner running on a given port, even though the client has initiated the connection. Needless to say, this is a fast scan requiring no additional privileges while returning important information.
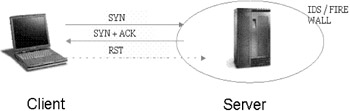
| Concept | Half-Open Scan We have seen that a TCP connect () scan can be easily logged as the IDS can detect a complete connection being initiated from outside and being established. One way hackers began evading this detection while meeting their objective was to do a half open scan. In a half open scan, a complete TCP connection is not established. Instead, as soon as the server acknowledges with a SYNACK response, the client tears down the connection by sending a RST (or reset connection) flag. This way, the attacker detects an open port listening / running a service from the ACK response, and at the same time succeeds in not establishing a full connect ( ) system call by sending the RST from the kernel level. |
Logically, a RST response indicates a closed port. However, sophisticated IDS and firewall systems are now capable of detecting a SYN packet from the void and prevent such scans from taking place. This is because like a TCP connect () system call, the half open scan initiates with a SYN flag, which can be easily monitored . Another drawback this scan holds for the attacker is that he has to make a custom IP packet to do this scan. Making a custom IP packet requires access to SOCK_RAW (getprotbyname('raw'); under most systems) or /dev/bpf (Berkeley packet filter), /dev/nit (Sun 'Network Interface Tap'). This generally requires privileged user access.
Generally a uid of o or administrative privileges is needed to use SOCK_RAW, /dev/bpf, /dev/nit and the like. This is a security precaution taken by most systems to prevent users from accidental creating such packets and broadcasting them on the network.
| Concept | IP Header a.k.a "Dumb" Scan This is an interesting scan technique that was first reported by Antirez. This takes advantage of the IP Header structure. This is considered a stealth scan as the source IP can be spoofed. However, this is a time consuming scan and requires a dumb intermediary host. The term 'dumb host' is used to indicate a host that has little or no activity. Usually such hosts are detected in modem sub pools where some system has been left up all night without any activity. Let us take a look at how this scan works. |
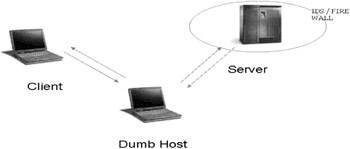
In this scan, the client detects a dumb host by some host sweeping and on detecting one, pings the dumb host. The analysis of the ID field, encapsulated within the IP header (recall discussion on ping packet) shows an increment of one with each sequential ping. For instance a dumb host ping packet analysis will read as:
-
32 bytes from Dumb host IP: seq=1 ttl=64 id=+1 win=o time=44 ms
-
32 bytes from Dumb host IP: seq=2 ttl=64 id=+1 win=o time=45 ms
-
32 bytes from Dumb host IP: seq=3 ttl=64 id=+1 win=o time=42 ms
Note that the window size (win) is zero and the time to live (ttl) is 64. This is just a note to the reader as these fields assume significance in later scan techniques. Now, the client spoofs a packet with a SYN flag and the dumb host's IP and sends it to the server. He also continues to ping the dumb host simultaneously. The server replies with an SYNACK or a RST response as the case may be to the dumb host (due to the spoofed IP). The IDS / Firewall of the server will register the scan attempt, but with the dumb host's IP as the source of the scan. The dumb host on its part has not initiated the connection and sends a RST bit (kernel initiated) to the server if it receives a SYNACK packet from the server. In case the server sends a RST response, the dumb host just ignores it.
-
32 bytes from Dumb host IP: seq=11 ttl=64 id=+1 win=o time=46 ms
-
32 bytes from Dumb host IP: seq=12 ttl=64 id=+3 win=o time=49 ms
-
32 bytes from Dumb host IP: seq=13 ttl=64 id=+2 win=o time=47ms
The client has been monitoring the ping packet of the dumb host and notices an increase of more than one in the id field if the dumb host is sending a RST flagged bit to the server, thereby inferring that there is an open port on the server. Incase there is no increase in the id field; the client can infer that the dumb host has not sent any response to the server. This would indicate that the server had sent an RST packet indicating a closed port.
This is indeed an innovative scan technique, but very time consume as the client has to first scan for a dumb host. However, this scan is not restricted to just the SYN flag. The occurrence of false positives can be minimized only if the traffic on the dumb host is minimal.
We have seen how the dumb host responded to a SYNACK flagged bit from the server. What if a scan is initiated with a SYNACK flag instead of a SYN flag? Would that be stealth enough?
| Concept | Stealth Scan Initially half open scans were considered stealth, however as intrusion detection software evolved, these scans were easily logged. Now, the term stealth refers to a category of scans where the packets are flagged with a particular set of flags other than SYN, or a combination of flags, no flags set, with all flags set, appearing as normal traffic, using fragmented packets or avoiding filtering devices by any other means. All these techniques resort to inverse mapping to determine open ports. |
| Concept | - SYNACK Scan 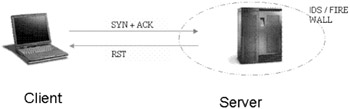 As seen in the discussion on dumb hosts, a SYNACK flagged bit sent to a closed port elicits a RST response, while an open port will not reply. This is because the TCP protocol requires a SYN flag to initiate the connection. |
This scan has a tendency to register fairly large false positives. For instance , packets dropped by filtering devices, network traffic, timeouts etc can given a wrong inference of an open port while the port may or may not be open. However, this is a fast scan that avoids a three-way handshake.
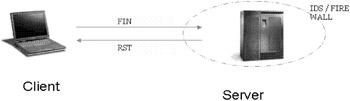
| Concept | - FIN Scan This works very similar to the SYNACK scan, with inverse mapping used to determine open or closed ports. The basis is that closed ports are required to reply to the probe packet with an RST, while open ports must ignore the packets in question (see RFC 793 pp 64). The scan attempts to exploit vulnerabilities in BSD code. Since most OS are based on BSD or derived from BSD, this was a scan that returned fairly good results. However, most OS have applied patches to correct the problem. However, there remains a possibility that the attacker may come across one where these patches have not been applied. |
| Concept | - ACK Scan This scan was first described by Uriel Maimon in his article 'TCP Port Stealth Scanning'. The scan takes advantage of the IP routing function to deduce the state of the port from the TTL value. This is based on the fact that IP function is a routing function. Therefore, ttl value will be decremented by one by an interface when the IP packet passes through it. However, this scan works on most UNIX related operating systems. |
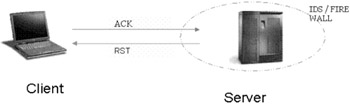
packet 1: client IP port 78: F:RST -> ttl: 68 win: o => unfiltered
packet 2: client IP port 79: F:RST -> ttl: 68 win: o => unfiltered
packet 3: client IP port 80: F:RST -> ttl: 50 win: o => filtered
packet 4: client IP port 81: F:RST -> ttl: 68 win: o => unfiltered
Notice that the ttl value returned for the third packet is less and hence indicates a filtered port. In other words, any ttl value less than 64 would indicate a filtered port. However, this may not work on all target machines. In earlier versions of BSD, the window field was also used to detect a filtered port. For example, any non-zero value for the window field would indicate a filtered port.
packet 1: client IP port 20: F:RST -> ttl: 64 win: o => unfiltered
packet 2: client IP port 21: F: RST -> ttl: 64 win: o => unfiltered
packet 3: client IP port 22: F:RST -> ttl: 64 win: 512 =>filtered
packet 4: client IP port 23: F:RST -> ttl: 64 win: o => unfiltered
Here, notice that the third sequential packet returns a window field with a non -zero value and hence indicates a filtered port. Also note that here the ttl value remains 64, and does not give away the filtered port. Remember - the scan does not show an open or closed state of port - but merely a filtered state of the port. While this scan is fast and avoids most detection systems, it is not compatible with all OS and relies more on the bug in the BSD code, which has been patched by most vendors .
Systems vulnerable to this include at least some versions of AIX, Amiga, BeOS, BSDI, Cray, Tru6 4 UNIX, DG/UX, OpenVMS, Digital UNIX, FreeBSD, HP- UX, OS/2, IRIX, MacOS, NetBSD, OpenBSD, OpenStep, QNX, Rhapsody, SunOS 4.X, Ultrix, VAX, and VxWor.
This scan is also popular among attackers to determine the firewall rulesets. Attackers can map out firewall rulesets and determine whether the perimeter of the system is guarded by a stateful firewall or a simple packet filtering device that blocks incoming ICMP and SYN packets.
| Concept | NULL Scan In a null scan, as the name indicates, the packet is set without any flags set. This tries to take advantage of RFC 793. Therefore the Null scan turns off all flags. However, the RFC does not specify how the system should respond. Most UNIX and UNIX related systems respond with a RST (if the port is open) to close the connection. However, Microsoft's implementation does not abide with this standard (based on their interpretation of the standard) and reacts differently to such a scan. In a UNIX like machine, a packet sent with none of the flags set, the BSD networking code informs the kernel to drop the incoming call if the port is open. An RST response indicates a closed port. |
However, an attacker can use this to differentiate between a Windows machine and others by collaborating with other scan results. For instance, if a -sF,-sX,or -sN scan shows all ports closed, yet a SYN (-sS) scan shows ports being opened, the attacker can infer that he is scanning a windows machine. This is not an exclusive property though, as this behavior is also shown by Cisco, BSDI, HP/UX, MVS, and IRIX. Also note that the reserved bits (RES1, RES2) do not affect the result of any scan, whether or not they are set. Therefore this scan will work only with UNIX and related systems, though it avoids detection and the three -way handshake.
| Concept | Xmas Scan In a Xmas scan, all the flags are set in contrast to the null scan. All the available flags in the TCP header are set (ACK, FIN, RST, SYN, URG, PSH) to give the scan an ornamental look - and hence the name. |
The scan initializes all the flags and transmits the packet to the target system. This scan will work on UNIX and related systems - similar to the NULL scan - and cause the kernel to drop the packet in case the receiving port is an open/listening port. A closed port will send a RST response. As with the scans seen above, inverse mapping is relied upon to deduce port state and hence the possibility of false positives. Note that dropped packets can also mean that there exists a firewall or packet filtering device. Therefore this scan will work only with UNIX and related systems, though it avoids detection and the three-way handshake.
| Concept | TCP Fragmenting This approach to scanning evolved primarily from a need to avoid false positives arising from other scans due to a packet filtering device present on the target machine. For any transmission, a minimally allowable fragmented TCP header must contain a destination and source port for the first packet (8 octet, 64 bit), the initialized flags in the next, which allows the remote host to reassemble the packet upon receipt through an internet protocol module that identifies the fragmented packets by the field equivalent values of source, destination, protocol and identification. |
The scan works by splitting the TCP header into small fragments and transmitting it over the network. However, there is a possibility that IP reassembly on the server-side may result in unpredictable and abnormal results - such as fragmentation of the data in the IP header. Some hosts may be incapable of parsing and reassembling the fragmented packets and thus may cause crashes, reboots, or even network device monitoring dumps.
Some firewalls may have rulesets that block IP fragmentation queues in the kernel (like the CONFIG_IP_ALWAYS_DEFRAG option in the Linux kernel) - though this is not widely implemented due to the adverse affect on performance. Since several intrusion detection systems use signature-based mechanisms to signify scanning attempts based on IP and/or the TCP header, fragmentation is often able to evade this type of packet filtering and detection. There is a high possibility of causing network problems on the target network.
EAN: N/A
Pages: 109