Chapter 6: Authentication and Authorization
|
6.1 The basics
Let's imagine that I worked for NASA (spaceships are cool). I would get a key card and a nametag that I could show off to other people and use as bragging rights. Additionally, the keycard and nametag would tell every-body how important I was within NASA. This might work for me and against me, in that I'd be authenticated to enter the building, but not authorized to enter every room. This is essentially the same way in which the internet works. As businesses implement networked information strategies that call for controlling access to information resources in the networked environment, authentication and access management are emerging as major issues that must be developed, implemented, and supported. There are two primary access issues that must be dealt with: authentication and authorization. Authentication and authorization have very specific definitions.
"Authentication" is the process where a user (via any type of physical access PC, network, remote) establishes a right to an identity. I log in to a system with my user name and password, and the system now knows who I am.
| Note | User name = Bubba Joe Smith |
"Authorization" is the process of determining whether a user is permitted to perform some action or access to a resource. I log in to a system with my user name and password, and the system knows who I am and now can grant or deny access to certain databases.
| Note | User name = Bubba Joe Smith Access to the Fishing Database = Bubba Joe Smith |
Figure 6.1 shows you the difference. Bubba Joe has authenticated with the server, and the server now knows who Bubba Joe is. With this information the server can control access to each resource. Within each database (DB) the server administrator can control via "authorization." Bubba Joe is not authorized to open the payroll and accounting DB, but he is authorized to open the fishing DB.
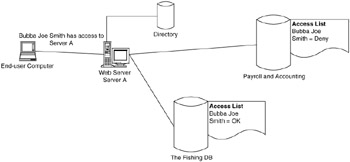
Figure 6.1
This whole process sounds really simple but, unfortunately, it is not. Authentication and authorization are very complex subjects that take a lot of time and money to implement and support. So our job (and we do choose to accept it) is to help you understand the issues and complexity of authentication and authorization.
One issue that we have not covered is the "directory attack" (aka "dictionary attack"). The directory attack is one of the simplest types of hacker attacks. Using a "footprinting" process, a hacker will get a list of user names. Then, using a tool with a directory word list (e.g., from a dictionary), the hacker will start accessing the URL with a list of possible passwords. This type of attack is a general threat to all passwords. Since passwords are typically short (in character length), the password can often be determined by brute force. Depending on the system, the password, and the skills of the hacker, such an attack can be completed in days, hours, or perhaps only a few seconds.
|