Lesson 3: Analyzing the Current Technical Environment
For the purposes of this training kit, an organization's technical environment defines how it organizes and manages its technical resources. Before you can begin planning your Active Directory infrastructure you must analyze the current state of your technical environment. This lesson covers the items you need to consider when analyzing your technical environment.
After this lesson, you will be able to
- Analyze your organization's current network architecture
- Analyze your organization's current hardware
- Analyze your organization's current software
- Analyze your organization's current technical standards
- Analyze your organization's current DNS environment
- Analyze your organization's current Windows NT domain architecture
Estimated lesson time: 40 minutes
Analyzing the Current Technical Environment
By analyzing your company's current technical environment, you can determine the technical requirements for implementing Active Directory. When you analyze your organization's current technical environment, you will need to analyze each component of the current technical environment, including
- Network architecture
- Hardware
- Software
- Technical standards
- DNS environment (if applicable)
- Windows NT domain architecture (if applicable)
To analyze each component thoroughly, you'll need to use your interviewing skills to gather information from various members of your design team. One of the best ways to gather information is to develop a worksheet that outlines what you need to know about each component and then use the worksheet to interview your team members. The Supplemental Course Materials CD-ROM that accompanies this book contains blank copies of interview worksheets that you can use to conduct your own technical environment analysis. The worksheets are only a starting point; you should modify them to meet your own analysis needs.
The result of your interviews and the completed worksheets will be a technical environment analysis document that describes the current state of each component of the technical environment. When complete, this document can be distributed to each member of the design team, providing a starting point for discussion and assessing future needs. In this lesson, you will examine the completed work-sheets that constitute the technical environment analysis document for Hiabuv Toys, a fictitious toy company whose business environment we analyzed in the previous lesson.
You will use your technical environment analysis document in conjunction with your technical environment needs assessment to determine the location and function of components in your Active Directory infrastructure plan. You will learn to conduct needs assessments for your technical environment as you learn and practice each stage of the infrastructure design process in Chapters 3–6.
Analyzing the Current Network Architecture
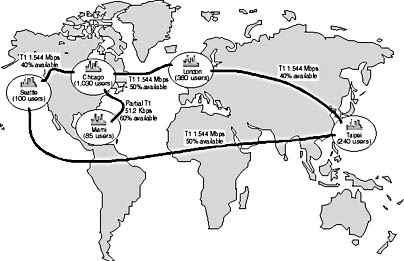
By analyzing network architecture, you portray the physical environment of your organization's network, which includes the current
- Location of points on the network
- Number of users at each location
- Network type used at each location
- Location, link speed, and percentage of average available bandwidth of remote network links
NOTE
Average available bandwidth is the amount of bandwidth that remains when you take the total bandwidth available for a link and subtract the amount of network traffic that occurs on the link during peak traffic.
- TCP/IP subnets at each location
- Speed of local network links
- Location of domain controllers
- List of servers at each location and the services that run on them
- Location of firewalls in the network
The completed Network Architecture Worksheet for Hiabuv Toys analyzes the organization's network architecture.
Hiabuv Toys Network Architecture Worksheet |
| Use this worksheet as a guide for gathering data about your organization's network architecture.
|

NOTE
A blank copy of this worksheet is located on the Supplemental Course Materials CD-ROM (\chapt02\worksheets\NetworkArch).
Analyzing the Current Hardware and Software
The purpose of analyzing the hardware and software currently in use on your network is to determine its compatibility with Windows 2000 Server. The first step in your analysis should be to conduct an inventory of the hardware and installed software.The second step is to compare your inventory with the list of hardware and software compatible with Windows 2000 Server, available at http://www.microsoft.com/windows2000/upgrade/compat/default.asp.
Your hardware inventory should include the name of each device and the manufacturer's name and model number. Depending on the device type, you may need to include more information about the device such as processor type, memory, or disk capacity. The types of devices you should consider for your inventory include audio or sound cards, computers, cameras or digital cameras, CD-R/RW, controller cards, DVD, input devices, modems, monitors, networking, printers, scanners, smart card readers, storage, TV tuners, uninterruptible power supply (UPS), USB/ 1394, video, and any other devices that are installed.
Your software inventory should include the name of the product, the version number, the manufacturer's name, and the language (for example, English or French) used in the software. Depending on the software, you may need to include more information about the software such as whether it's a service pack or patch release. The categories of software products you should consider for your inventory will depend on the individual needs of the company, but in general they include arts & entertainment, commerce, connectivity and communications, cross-platform tools/integration, data processing, data warehousing, multimedia, network infrastructure, operating systems, system management, user interface enhancements and accessibility, utilities and servers, and workflow and conferencing.
The completed Hardware and Software Worksheet for Hiabuv Toys inventories the Seattle location's hardware and the Training department's installed software and notes whether each is compatible with Windows 2000 Server.
Hiabuv Toys — Hardware & Software Worksheet |
| Use this worksheet as a guide for inventorying and analyzing your organization's hardware and installed software.
|

NOTE
A blank copy of this worksheet is located on the Supplemental Course Materials CD-ROM (\chapt02\worksheets\Hardware&Software).
Analyzing the Current Technical Standards
Your organization's technical standards are the conventions currently in place for the technical environment. Technical standards usually include
- Standard hardware configurations for desktops, servers, and other devices
- Standard software configurations for user desktops
- Naming conventions for users, groups, devices, and domains
- Network performance standards
- Security standards
The completed Standards Worksheet for Hiabuv Toys analyzes the technical standards currently in place for the Engineering department in the organization.
Hiabuv Toys Technical Standards Worksheet |
| Use this worksheet as a guide for gathering data about the technical standards currently in place in your organization.
|

NOTE
A blank copy of this worksheet is located on the Supplemental Course Materials CD-ROM (\chapt02\worksheets\TechStandards).
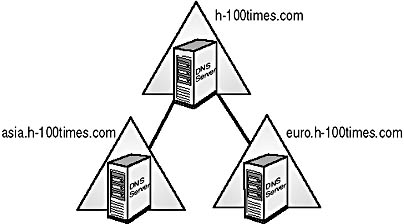
Analyzing the Current DNS Environment
A Domain Name System (DNS) service is a name resolution service used to translate host names to IP addresses in Active Directory. As you learned in Chapter 1, for Active Directory and associated client software to function correctly, you must have installed and configured Windows 2000 DNS. If your organization does not currently use DNS, there is nothing to analyze at this time. However, if your organization is already using another DNS service, it's important to find out whether the service is compatible with Active Directory and how it is currently structured.
The minimum requirement for a DNS service to be compatible with Active Directory is for the service to support service resource records (SRV RRs), as described in RFC 2052, and dynamic update, as described in RFC 2136. Many established DNS environments operate on UNIX servers running the BIND (Berkeley Internet Name Domain) implementation of DNS. If your DNS environment is running BIND version 8.1.2 or later, it supports SRV RRs and dynamic update and is compatible with Active Directory DNS requirements. If your organization is currently running Windows NT 4 DNS, your DNS service is also compatible with Active Directory DNS requirements.
NOTE
To read more about service resource records, launch an Internet search engine and run a search on "RFC 2052" and "RFC 2136." RFCs (Request for Comments) are the official documents of the Internet Engineering Task Force (IETF) that specify the details for new Internet specifications or protocols. RFC 2052 is entitled "A DNS RR for Specifying the Location of Services (DNS SRV)." RFC 2136 is entitled "Dynamic Updates in the Domain Name System (DNS Update)."
Although the DNS services described here are compatible with Active Directory, only the Windows 2000 DNS service allows you to use Active Directory as the data storage and replication engine. With some planning, you will be able to migrate from these compatible DNS services to Windows 2000 DNS.
The completed DNS Environment Worksheet for Hiabuv Toys analyzes the organization's existing DNS environment.
Hiabuv Toys DNS Environment Worksheet |
| Use this worksheet as a guide for gathering data about your organization's existing DNS environment.
|

NOTE
A blank copy of this worksheet is located on the Supplemental Course Materials CD-ROM (\chapt02\worksheets\DNSEnvironment).
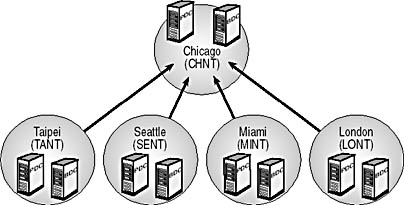
Analyzing the Current Windows NT Domain Architecture
In Windows NT, you can group users and servers into domains for administrative purposes. In Windows 2000, organizational units (OUs) have been introduced to handle administration, while domains still provide administration but hold OUs and many more objects than in Windows NT. The purpose of analyzing the current Windows NT domain architecture employed in your organization is to understand the workings of the present domain structure so that you can convert each of the domains into an Active Directory domain, tree, and forest structure. If your organization does not currently use Windows NT, there is nothing to analyze at this time.
The completed Windows NT Domain Architecture Worksheet for Hiabuv Toys analyzes the organization's existing Windows NT domain architecture.
Hiabuv Toys Windows NT Domain Architecture Worksheet |
| Use this worksheet as a guide for gathering data about your organization's Windows NT domain architecture.
|

NOTE
A blank copy of this worksheet is located on the Supplemental Course Materials CD-ROM (\chapt02\worksheets\NTDomain).
Lesson Summary
In this lesson you learned to analyze each component of your technical environment, including the current network architecture, hardware, software, technical standards, DNS environment, and Windows NT domain architecture. An organization's technical environment defines how it organizes and manages its technical resources. Your organization's technical environment has a direct effect on your Active Directory infrastructure.
You also learned to create a document, the technical environment analysis document, which describes the current state of each technical environment component in your organization. The technical environment analysis document includes the completed Network Architecture, Hardware and Software, Technical Standards, DNS Environment, and Windows NT Domain Architecture worksheets. When complete, this document can be distributed to each member of the design team, providing a starting point for discussion and assessing needs.
EAN: 2147483647
Pages: 76