What Is iptables ?
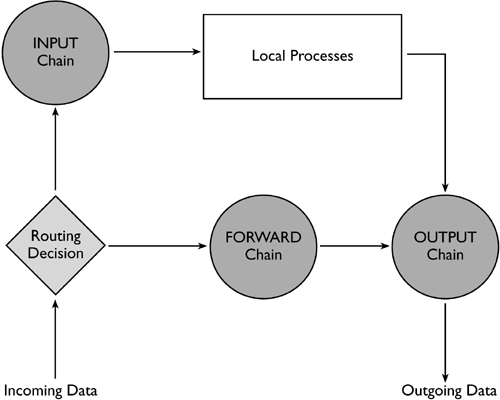
What Is iptables ?Although the details are hidden from most networking tools, the 2.4. x Linux kernel uses a procedure like that outlined in Figure 25.1 to process network packets. Early on in the process, a routing decision is made: Is the packet destined for the local computer, or should it be forwarded to another computer? Depending upon the answer to that question, the packet is passed to one of two chains: the INPUT chain or the FORWARD chain. Each of these chains can process or modify the incoming data in various ways, but the default is not to modify the data. The INPUT chain ultimately leads to what Figure 25.1 refers to as local processes. These may be network clients (Netscape, telnet , and so on) or network servers (Apache, telnetd , and so on). In most cases, these processes run in user space, but they may be kernel-based, as in the kernel's Network Filesystem (NFS) support or the kHTTPd Web server. Both the local processes and the FORWARD chain eventually lead to the OUTPUT chain, which can also manipulate data packets in ways described in this chapter. Figure 25.1. The Linux networking system provides several chains in which data packets may be manipulated. NOTE
Each of the chains shown in Figure 25.1 provides the opportunity to manipulate data packets. A chain can filter packets based on features such as the source or destination IP address, the source or destination port, or the network interface involved in the transaction. Each chain is a collection of rules, each of which is matched in turn against the input packet. If a rule matches, the rule indicates what the kernel should do with the packet by specifying a target for the rule. Predefined targets include ACCEPT (accept the packet for further processing), DROP (ignore the packet), QUEUE (pass the packet to a user-space program), and RETURN (stop processing the chain and return to the chain that called the current chain). Some additional targets that require particular kernel options to be activated include REJECT (to reject the packet, telling the sender that it was rejected), MASQUERADE (used for NAT, as described in the upcoming section "Configuring NAT with iptables"), and LOG (used to log information on packet filtering). Chains are organized into tables. The three chains shown in Figure 25.1 make up the filter table, which is what handles most standard traffic. Two other standard tables are nat (which is used for NAT, as described in the upcoming section "Configuring NAT with iptables") and mangle (which is used for specialized packet alterations). It's possible to place new chains within a table, and call these new chains from the existing chains. You might do this to create specialized and complex processing patterns to filter or alter data. These network tables and chains are features of the Linux kernel, and iptables is the user-space tool you use to manipulate them. You can use iptables to add rules to any of the chains shown in Figure 25.1, or to other chains. For instance, you might add rules to the INPUT chain to block all packets directed at specific network ports, or you might add rules to the OUTPUT chain to stop packets directed at systems with which you don't want yours communicating. By manipulating these and other chains, you can implement a packet-filter firewall, NAT, or other security and routing tools. The changes you make with iptables are transient; they disappear as soon as you reboot the computer. For this reason, you should create a script that sets your iptables rules. Some distributions, such as Red Hat and Mandrake, include tools to help you build firewall or NAT rules. You can implement such a script yourself and call it as a SysV or local startup script.
|
EAN: 2147483647
Pages: 203