Formulating an Enterprise Privacy Strategy
Formulating an Enterprise Privacy Strategy
Building a privacy vision and an execution strategy for an enterprise is a full-time job and a serious undertaking. Privacy should not be treated as an afterthought, a part-time job, or a short-term project for an organization. Even if your company is not collecting any type of sensitive information, your customers will want to understand your company s position on privacy.
Creating a Privacy Organization
Many consumers are aware of the importance of privacy today. However, many companies are not prepared to respond to consumer privacy concerns in an effective manner. Often a group within a company will respond to a privacy issue autonomously without consulting with company executives or their legal department. Sometimes multiple people from a company will attempt to respond to the same issue without coordination. This can lead to conflicting and sometimes incorrect messages being given to customers. A group within a company should not assume the task of providing the corporate position on privacy issues. This can cause negative press coverage and damage a company s image, which can result in a loss of sales.
The privacy strategy for a company should come from the executive ranks and should be adopted by all groups within a company. In small organizations, the Chief Information Officer (CIO), Chief Operations Officer (COO), Chief Technology Officer (CTO), or another executive can take this on as part of her role. This executive might have to rely more heavily on industry experts for guidance to make up for her lack of experience in the privacy arena. Larger organizations should hire a Chief Privacy Officer (CPO) who is familiar with privacy practices and legislation. The CPO would work with the legal and public relations departments to create a corporate privacy strategy.
Figure 28-1 shows an example of an organizational structure for a privacy department. The CPO reports to a corporate executive and works closely with the public relations and legal departments. The CPO might also be in charge of a corporate privacy group.
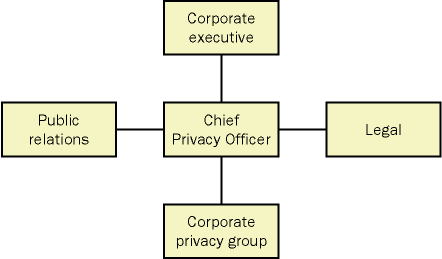
Figure 28-1. A corporate privacy team
The Role of the Chief Privacy Officer
The CPO is the person ultimately responsible for developing a privacy strategy for the company and disseminating it to all employees. He should ensure that all privacy issues are brought to his attention. In addition, all responses to issues should be reviewed by the virtual privacy team, which should include representatives from the legal and public relations departments and a privacy advocate from every major group in the company.
To be effective, the CPO needs to have a good understanding of how the company operates. He should know what data is collected by the company and how it is used. The CPO should work closely with the marketing and Internet teams because they are the departments that normally use customer information the most.
To stay current with privacy trends, the CPO will need to subscribe to trade journals, work with government agencies, participate in privacy organizations, and meet with CPOs from other companies. A list of privacy organizations can be found at http://www.epic.org/privacy/privacy_resources_faq.html. One good way to determine how well your company is doing with regard to privacy awareness is to compare your company s privacy position to the positions of your competitors. Another good measure of how aware your company is of privacy issues is to track the number of privacy complaints that the company receives.
The Role of the Privacy Advocate
The privacy advocate (PA) is an individual who works within a particular group at a company and is responsible for the implementation of the privacy plan for the group. The PA works closely with the CPO to understand the privacy strategy for the company and determines how that strategy will apply to her group. Within the group, the PA assists with privacy training, creating a privacy policy, resolving privacy issues, and ensuring the group s compliance with corporate privacy policy.
In a small company, the PA might be a member of the corporate privacy group and might be responsible for a certain number of groups within the company. In large companies, each group should have their own PA. Figure 28-2 shows an example of how this could be structured.
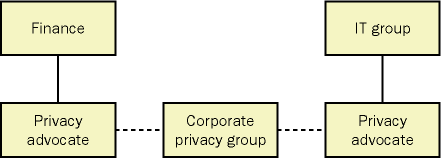
Figure 28-2. Privacy advocate relationships with the corporate privacy group
Assigning a Managing Privacy Advocate
Large departments might have several PAs that work with or for a managing privacy advocate in the department, who in turn works with the CPO as a traditional PA would. The managing privacy advocate is responsible for the privacy plan for the department and works with the various PAs in the department to execute the plan.
Responding to Privacy Issues
If your company is collecting personal information, has a Web site that tracks visitors browsing habits, or sends e-mail messages to individuals outside the company, you will eventually run into privacy issues. These issues can arise in the form of news articles, e-mails from angry customers, a complaint filed at a privacy organization such as TRUSTe, or litigation. When these issues arise, you need to respond quickly and effectively. The best way to do this is to have a plan in place for handling privacy issues.
Employees in your company should not try to respond to privacy issues without working with the corporate privacy group on an appropriate response. Letting teams handle privacy issues on their own can result in incorrect, insensitive, incomplete, or libelous responses to customer complaints. You should not place individual teams in the position of representing the privacy policy for the company. Always get the corporate privacy group involved in resolving privacy issues. Employees in your company should be trained to have the corporate privacy group involved as soon as possible when a privacy issue occurs.
To prevent your organization s privacy issues from being highlighted by the media, or to prevent your customers from contacting an outside organization for resolution (such as the U.S. Federal Trade Commission or TRUSTe), make it easy for consumers to contact your company. Provide an e-mail address as part of the privacy statement on your Web site, and include contact information in privacy statements that you send to your customers via e-mail or postal mail.
Building a Privacy Response Center
To establish a centralized and formalized way of handling privacy issues, companies should create their own privacy response center (PRC). Set up a PRC as the first line of defense for all privacy issues for your company. The PRC should be staffed by key privacy personnel, including public relations, legal, and privacy representatives as well as representatives from groups that are prone to privacy issues. Information for all privacy issues should be stored in a central database system. A bug tracking system would work well for this purpose. The tracking system should have the ability to attach documents and store links to Web pages and file shares. A PRC can provide the following benefits:
-
Centralized processing of issues
-
Reduction in the duplicate processing of issues
-
Faster processing of repeat issues
-
Easier reporting and trend analysis
-
Ability to link to department databases
Figure 28-3 shows a sample workflow for a PRC. The response desk for the PRC might receive word of a privacy issue from many sources. As mentioned, information about each issue that comes in should be placed into a tracking database. If a complaint comes in from an individual, a response should be sent to him as soon as possible to show that his issue is important and being processed. Try not to use auto-responders for this purpose. The owner should investigate the issue and propose a resolution. The resolution might require a change in policy, application, Web page, or other resource. The owner should work with the PRC team to draft an appropriate response to the originator of the issue. A representative from your company should then make sure that the response is delivered to the originator of the issue. Each step of this issue resolution should be noted in the tracking database.
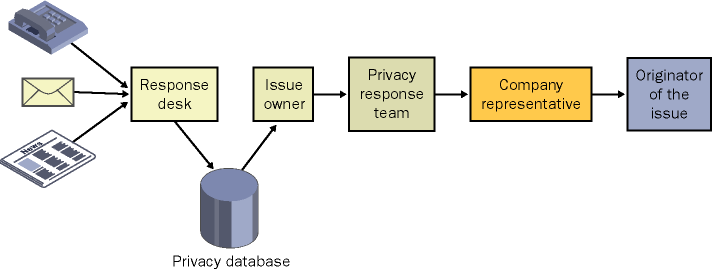
Figure 28-3. The workflow for a privacy response center
EAN: 2147483647
Pages: 189