Using a Firewall
In the last section, you found out how potentially vulnerable your computer is to viruses and attackers from the Internet and your internal network. You also know that one way to help fight those attackers is to block access to your computer on all of the ports, which can be gateways into your computer. How exactly do you block all the ports? Use a firewall. A firewall is a special application that acts like a brick wall that is protecting all of the ports on your computer.
When a remote computer attempts to access a computer that is protected by a firewall, it is not able to connect and the data that was sent is ignored and discarded. Depending on the way the firewall is configured, when data is sent to a blocked port on your computer, the firewall will either respond to where the data was sent from with a message that the port is closed or it will do nothing, giving your computer a stealth presence. Most firewall applications are set up by default to run in a stealth mode, which provides the maximum amount of protection. Any remote computer trying to connect or send data to your computer with a firewall installed and running in stealth mode will think that your computer has gone offline because it is not getting a response.
So far, I have talked only about firewalls that block incoming attacks from the Internet. Firewalls can also block traffic originating from your computer going out to the Internet. Why would you want to do that? What if someone installed a key logger on your computer that sends all your information to a remote computer for him to use? Or how about a media player that sends a history of everything that you played to a server for their tracking purposes? With a two-way firewall, you can block outgoing traffic that you haven't authorized.
Firewalls can be a very powerful security device. In Windows Vista, a firewall configured properly can completely eliminate one way an attacker may try to gain access to your computer. The next section shows you how you can use the new and improved firewall in Windows Vista to block incoming attacks and prevent unwanted applications from sending information out.
Using the Windows Vista firewall
The firewall included in Windows Vista is much more advanced than previous Windows firewalls. Microsoft actually calls it, "Windows Firewall with Advanced Security." It has three different location profiles that allow you to customize your firewall rules based on where your computer is. If it is in a public place, you are going to want to have very strict firewall rules compared to if you are in a corporate domain at work or at a private network at home. On top of the location profiles, the firewall has a very complex rule structure that allows you maximum flexibility to create openings in your firewall to permit application or service-related network traffic. Most important, Windows Firewall now has support to block outgoing traffic as well.
The upgrades to Windows Firewall really make it a very powerful security solution that was once provided only by advanced third-party firewall software. The integration of Windows Firewall into the Network Center and other parts of Windows makes it even more powerful.
Unfortunately, Microsoft chose to hide the raw power of the new firewall from most users. You can access the advanced firewall configuration tool only if you know what it is called. Microsoft even disabled outbound filtering because Microsoft thought it would be too much of an annoyance for inexperienced users. The next two sections guide you through the basics of using the advanced firewall configuration tool and enabling the outbound firewall.
Configuring Windows Firewall
You are not going to find an easy link to the advanced firewall configuration tool anywhere in the user interface. The only way to access it is to call it directly. That is exactly what you are going to do. Click the Start button, type wf.msc in the Search box, and then press Enter. When Windows Firewall with Advanced Security window loads, you will see the complexity and the power of the new firewall. Maybe it was a good idea Microsoft decided to hide this from inexperienced users after all.
On the main screen you will see a list of the profiles, as shown in Figure 15-2. This is where you can see an overview if the firewall is on and if the inbound and outbound rules are active. The next step is to view the specific rules. You can do that by simply selecting Inbound Rules or Outbound Rules from the list on the left. Go ahead and click Inbound Rules now.
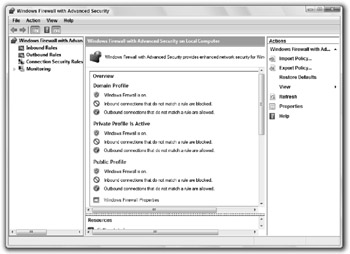
Figure 15-2: Using Windows Firewall with Advanced Security
In a few seconds you will see all of the rules currently set up on your computer. If they are enabled, they will have the green icon. If not, the icon will be gray. You can also see what firewall profiles the rule is used in, as shown in Figure 15-3 in the Profile tab. If you ever need to enable or disable a rule, just right-click it and select Enable or Disable. You can also edit an individual rule's properties by right-clicking on the rule and selecting Properties. Working with the Outbound Rules is exactly the same as working with Inbound Rules; Outbound Rules just control a different direction of traffic.
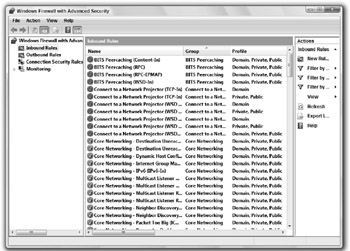
Figure 15-3: Inbound firewall rules and the profiles they are used in
For the sake of demonstrating how to add a new rule, let's say that you just installed some type of server on your computer that users will connect to on port 800. Follow these steps to open up a hole so that your users can connect:
-
If the Windows Firewall with Advanced Security window is not already open, click the Start button, type wf.msc in the Search box, and then press Enter.
-
After the firewall configuration tool loads, click Inbound Rules.
-
Under Actions in the right pane, click New Rule.
-
The new Inbound Rule Wizard loads and asks you for the type of rule you would like to create. For this scenario, you are going to select Port. Click Next when you have selected Port.
-
You are asked to specify what type of port to open. Unless you have an application that specifically requires a UDP port, nearly 100 percent of the time you will be selecting TCP. For this scenario, select TCP. Also on this screen, type 800 in the specific port box because you want to open up only port 800. Click Next when you are done.
-
The next screen asks you to define the action of the rule. You can choose to Allow the connection, Allow the connection if secure (on a network with IPSEC), or Block depending on what you want to do. Select Allow the connection and click Next.
-
You will need to select what profiles this rule will be part of. By default, all of the profiles are checked; uncheck any profiles you do not want your rule to be part of and click Next.
-
The last step is to name your new rule. Type a name and a description if you want and click Finish.
Your new rule will now appear on the Inbound Rule list. It will automatically be enabled when you click Finish.
Enabling the outbound firewall
In Windows Vista, Microsoft decided it was best to disable the outbound connection filtering because it can cause headaches for many inexperienced computer users. This may have been the right choice but not filtering your outbound traffic can increase the possibility that an application can steal important personal information and send it to a remote computer. If this application is malicious, it can be used to steal personal information such as passwords and bank account numbers. Turning on the outbound firewall filtering and enabling only the rules that grant your normal applications access to the Internet will greatly increase the security of your computer.
Enabling the outbound firewall rules on your computer is easy to do once you know where Microsoft hid the setting. Follow these steps to turn the outbound firewall back on:
-
If the Windows Firewall with Advanced Security window is not already open, click the Start button, type wf.msc in the Search box, and then press Enter.
-
When the firewall configuration tool is loaded, click Windows Firewall Properties right in the middle of the opening screen.
-
When the settings window loads, you will see a tab for each of the different firewall profiles. Select the tab for the profile on which you would like to enable outbound filtering.
-
Under the State section, locate the Outbound connections drop-down box and change it to Block.
-
Click OK when you are finished to activate the outbound firewall on the profile you specified.
Windows automatically detects any applications that try to access the Internet or other network resources that are now blocked with the outbound firewall turned on and will prompt you to automatically authorize the application to send information out to the Internet.
EAN: 2147483647
Pages: 105