Accept Only SMTP Connections from Specific Hosts (ISP)
|
| This configuration assumes that you are running an internal mail server, set up either internally or on a DMZ segment. This mail server is acting perhaps as a local mail spool only or smart host and only needs to send/receive mail to an upstream mail serverat an ISP for example. The first example assumes that your firewall, Host-A, is only going to allow SMTP connections from the upstream ISP mail server, mailserver.isp.com. All other connections are to be rejected. This example rule assumes you have a default DROP policy: $IPTABLES -P INPUT DROP # where eth0 is your Internet interface $IPTABLES -A INPUT -i eth0 -p tcp dport 25 \ -s mailserver.isp.com -j ACCEPT This second example assumes you have a firewall (Host-A) forwarding SMTP connections to an internal mail server (Host-B, 192.168.1.25) on the DMZ segment 192.168.1.0/24. The internal network address space is 10.10.10.0/24. We will only allow connections from mailserver.isp.com. Figure 14.4. SMTP from mailserver.isp.com being forwarded to a DMZ server.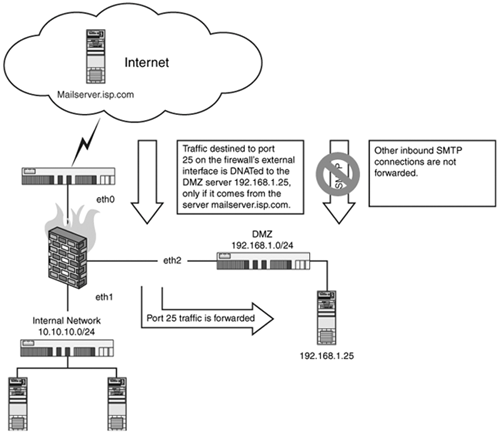 # where eth0 is your external Internet facing interface # where eth1 is your internal network, 10.10.10.0/24 # where eth2 is your DMZ network, 192.168.1.0/24 EXTERNAL=eth0 INTERNAL=eth1 DMZ=eth2 MAILSERVER=192.168.1.25 $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ -p tcp \ --dport 25 -s mailserver.isp.com -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ --dport 25 -j DNAT --to-destination $MAILSERVER |
|