Forward: SSH to Another System
|
| In this example, we will assume that our firewall, Host-A, handles traffic for an internal network, 10.10.10.0/24, and a DMZ network, 192.168.1.0/24. On the DMZ network we have two servers, Host-B (192.168.1.10) and Host-C (192.168.1.11), that we will DNAT SSH sessions to. The first example assumes our firewall only has one IP address on its external interface, and the second example assumes that the firewall has multiple IPs. When we only have one IP address, the only way to get this to work is to "run" SSH on a different port. This does not mean that we need to run sshd on different ports on our two DMZ hosts; rather we will demonstrate how to redirect ssh to different ports. Our firewall has the external IP address, 22.33.44.55. Port 2022 connections to this IP address will be forwarded to Host-B (192.168.1.10), and port 3022 connections will be forwarded to Host-C (192.168.1.11): # where eth0 is the external interface (Internet) # where eth1 is the internal interface (10.10.10.0/24) with the IP 10.10.10.1 # where eth2 is the DMZ interface (192.168.1.0/24) with the IP 192.168.1.1 EXTERNAL=eth0 INTERNAL=eth1 DMZ=eth2 HOSTB=192.168.1.10 HOSTC=192.168.1.11 # Host-B rules $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ -p tcp \ --dport 2022 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ --dport 2022 -j DNAT --to-destination $HOSTB # Host-C rules $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ -p tcp \ --dport 3022 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ --dport 3022 -j DNAT --to-destination $HOSTC Figure 13.3. Graphic showing multiple DNAT rules to multiple DMZ servers.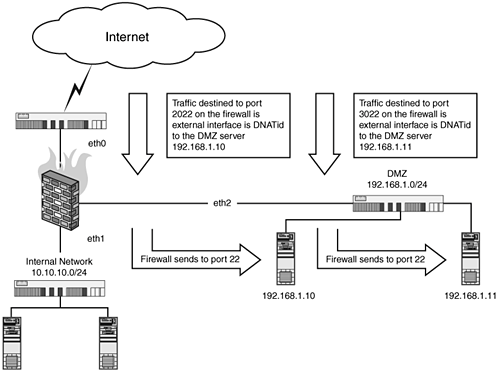 This next example assumes that our firewall has three IP addresses, 22.33.44.55, 22.33.44.56, and 22.33.44.57. Connections on port 22 on the IP 22.33.44.55 will go to the firewall itself; connections to 22.33.44.56 will be forwarded to 192.168.1.10; and connections to 22.33.44.57 will be forwarded to 192.168.1.11 (see Figure 13.4). Figure 13.4. Graphic showing a firewall with three external IP address, DNAT-ing SSH traffic.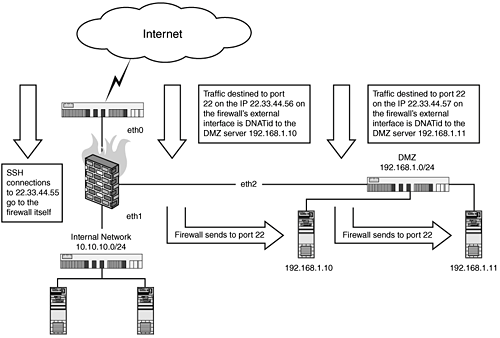 # where eth0 is the external interface (Internet) with the IP's # 22.33.44.55 -> local # 22.33.44.56 -> 192.168.1.10 # 22.33.44.57 -> 192.168.1.11 # where eth1 is the internal interface (10.10.10.0/24) with the IP 10.10.10.1 # where eth2 is the DMZ interface (192.168.1.0/24) with the IP 192.168.1.1 EXTERNAL=eth0 INTERNAL=eth1 DMZ=eth2 HOSTB=192.168.1.10 HOSTC=192.168.1.11 IP_HOSTB=22.33.44.56 IP_HOSTC=22.33.44.57 # Host-B rules $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ \ -d $IP_HOSTB -p tcp --dport 22 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ -d $IP_HOSTB --dport 22 -j DNAT \ --to-destination $HOSTB # Host-C rules $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ \ -d $IP_HOSTC -p tcp --dport 22 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ -d $IP_HOSTC --dport 22 -j DNAT \ --to-destination $HOSTC And finally, the previous examples using name-based chains to restrict access, we will only allow access to both systems from the IP addresses 33.44.55.66 and 44.55.66.77: # where eth0 is the external interface (Internet) # where eth1 is the internal interface (10.10.10.0/24) with the IP 10.10.10.1 # where eth2 is the DMZ interface (192.168.1.0/24) with the IP 192.168.1.1 EXTERNAL=eth0 INTERNAL=eth1 DMZ=eth2 HOSTB=192.168.1.10 HOSTC=192.168.1.11 $IPTABLES -N USERS $IPTABLES -A USERS -s 33.44.55.66 -j RETURN $IPTABLES -A USERS -s 44.55.66.77 -j RETURN $IPTABLES -j DROP # Host-B rules $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ -p tcp \ --dport 2022 -m state \ --state NEW,ESTABLISHED,RELATED -j USERS $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ -p tcp \ --dport 2022 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ --dport 2022 -j DNAT --to-destination $HOSTB # Host-C rules $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ -p tcp \ --dport 3022 -m state \ --state NEW,ESTABLISHED,RELATED -j USERS $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ -p tcp \ --dport 3022 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ --dport 3022 -j DNAT --to-destination $HOSTC And again, the same filtering method is applied against our multi-IP configuration: # where eth0 is the external interface (Internet) with the IP's # 22.33.44.55 -> local # 22.33.44.56 -> 192.168.1.10 # 22.33.44.57 -> 192.168.1.11 # where eth1 is the internal interface (10.10.10.0/24) with the IP 10.10.10.1 # where eth2 is the DMZ interface (192.168.1.0/24) with the IP 192.168.1.1 EXTERNAL=eth0 INTERNAL=eth1 DMZ=eth2 HOSTB=192.168.1.10 HOSTC=192.168.1.11 IP_HOSTB=22.33.44.56 IP_HOSTC=22.33.44.57 $IPTABLES -N USERS $IPTABLES -A USERS -s 33.44.55.66 -j ACCEPT $IPTABLES -A USERS -s 44.55.66.77 -j ACCEPT $IPTABLES -j DROP # Host-B rules $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ \ -d $IP_HOSTB -p tcp --dport 22 -m state \ --state NEW,ESTABLISHED,RELATED -j USERS $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ \ -d $IP_HOSTB -p tcp --dport 22 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL -p tcp \ -d $IP_HOSTB --dport 22 -j DNAT \ --to-destination $HOSTB # Host-C rules $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ \ -d $IP_HOSTC -p tcp --dport 22 -m state \ --state NEW,ESTABLISHED,RELATED -j USERS $IPTABLES -A FORWARD -i $EXTERNAL -o $DMZ \ -d $IP_HOSTC -p tcp --dport 22 -m state \ --state NEW,ESTABLISHED,RELATED -j ACCEPT $IPTABLES -t nat -A PREROUTING -i $EXTERNAL \ -d $IP_HOSTC-p tcp --dport 22 -j DNAT \ --to-destination $HOSTC |
|