Using Internet Authentication Service (IAS)
|
EXAM 70-293 OBJECTIVE 2, 2.3
While basic RRAS security is sufficient for small networks, a larger enterprise often needs a dedicated infrastructure for authentication. RADIUS is a standard for dedicated authentication servers. A RADIUS server provides centralized authentication and access control, and it can also provide detailed accounting for the use of its services. RADIUS services can be scaled to handle any enterprise’s authentication needs and extended with multiple authentication servers.
Windows Server 2003 includes Microsoft Internet Authentication Service (IAS), an implementation of a RADIUS server. IAS supports authentication for Windows-based clients, as well as for third-party clients that adhere to the RADIUS standard. IAS stores its authentication information in Active Directory (AD), and you can manage it with Remote Access Policies.
| Note | For more detailed information about configuring IAS for specific uses, such as wireless authentication, see Chapter 7. |
Advantages of IAS
While IAS requires the use of an additional server component, it provides a number of advantages over the standard methods of RRAS authentication. These advantages include centralized authentication for users, auditing and accounting features, scalability, and seamless integration with the existing features of RRAS.
Centralized User Authentication and Authorization
In the RADIUS standard, remote users do not connect directly to the RADIUS server. Instead, they connect to a network access server (typically an RRAS server), which acts as a RADIUS client, connecting to the IAS server and authenticating the user. This provides for centralized authentication. Any number of RRAS servers can connect to the same IAS server for authentication.
Centralized Auditing and Accounting
Along with authentication, IAS supports auditing features—tracking when the system is used, when errors occur, and so on—and can keep a centralized record of usage of the remote access or VPN servers. This record is stored in a log file, which you can import into a database or analyze to determine traffic patterns or potential problems.
RRAS Integration
IAS supports the same Remote Access Policy settings as RRAS. You can use these settings on a simple RRAS server in a small network, and later add an IAS server, move the policies to the IAS server, and configure one or more RRAS servers to authenticate using IAS. When using IAS for authentication, RRAS servers no longer have their own Remote Access Policies, since the IAS server manages a centralized policy.
Control via Remote-Access Policies
As with basic RRAS security, you can define remote-access policies to configure remote-access security with IAS. You can define a single set of remote-access policies on the IAS server, and they will be used by every RRAS server that uses IAS for authentication. This centralized authentication allows you to quickly define policies for the entire enterprise without the need to manage individual policies for each RRAS server.
Extensibility and Scalability
IAS provides an extensible architecture for authentication. While it provides only a small advantage over traditional Windows authentication methods when used on a small network, IAS excels in large enterprises because it provides centralized authentication. You can scale from a single IAS server to multiple IAS servers interacting with multiple RRAS servers in a global network. When you add a new RRAS server, you don’t need to configure its security separately; simply configure it to use the existing IAS server for authentication.
IAS Management
To support IAS, you will need one or more IAS servers. You can install IAS on a domain controller or member server. The server can be used for other components, such as RRAS, but if the IAS server will be heavily used, you may wish to dedicate a server for this purpose. You can use a single server or configure a second server to act as a backup. RRAS servers that authenticate using IAS can contact the backup server if they are unable to reach the primary server.
The IAS component is included with all editions of Windows Server 2003 except the Web Edition. You can install IAS on a Windows Server 2003 computer using the
Add/Remove Programs option in Control Panel. Exercise 5.05 demonstrates how to add this component to a server.
Exercise 5.05: Installing IAS
Follow these steps to install IAS on a computer running Windows Server 2003:
-
Select Start | Control Panel | Add/Remove Programs.
-
Select the Add or Remove Windows Components option.
-
Select Networking Services from the list and click Details.
-
Check the box next to Internet Authentication Service and click OK.
-
Click Next to complete the installation.
Activating IAS Authentication
When you have a working IAS server on the network, you can configure the RRAS server to use IAS authentication. This will disable the normal Remote Access Policies in the Routing and Remote Access MMC snap-in and forward all authentication to the IAS server. You can then configure security settings for all RRAS servers centrally at the IAS server. Exercise 5.06 guides you through the process of enabling IAS authentication for an RRAS server.
Exercise 5.06: Selecting IAS Authentication
To select IAS authentication, you must have already configured and enabled RRAS services on the computer. Follow these steps to enable IAS authentication:
-
Select Start | Administrative Tools | Routing and Remote Access.
-
Click the RRAS server name in the left column to highlight it. Select Action | Properties from the menu, or right-click the RRAS server name and select Properties from the context menu.
-
The Properties dialog box is displayed. Click the Security tab. The Security properties are displayed, as shown in Figure 5.11.
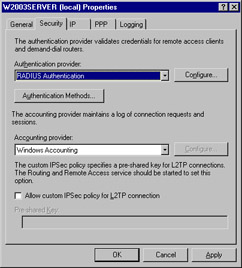
Figure 5.11: Security Properties -
In the Authentication provider drop-down list, select RADIUS Authentication.
-
Click the Configure button to display the RADIUS server options.
-
Click Add to add a RADIUS server to the list.
-
The Add RADIUS Server dialog box is displayed, as shown in Figure 5.12. Enter the name of the RADIUS server. You can optionally specify a shared secret using the Change button. Click OK.
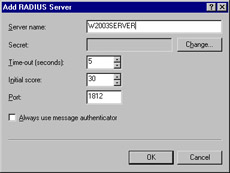
Figure 5.12: Add a RADIUS Server -
Click OK to exit the Properties dialog box.
-
A dialog box reminds you to restart RRAS to enable the new authentication method. Click OK to continue.
-
You are returned to the Routing and Remote Access MMC snap-in. Select the RRAS server in the left column and select Action | All Tasks | Restart from the menu, or right-click the server name and select All Tasks | Restart from the context menu.
RRAS is now restarted, and RADIUS authentication is enabled using the IAS server.
| Exam Warning | If you enter a shared secret (password) in the RADIUS Authentication settings of RRAS, it must be the same one you already specified in the properties of the IAS server. This password system provides a basic level of security between RADIUS clients and servers. Its primary purpose is to ensure that an unauthorized RADIUS server cannot be added to the network and used to provide incorrect authentication information. |
Using the IAS MMC Snap-in
You can manage the configuration of an IAS server using its MMC snap-in. To launch the IAS management console, select Start | Programs | Administrative Tools | Internet Authentication Service. The IAS console is shown in Figure 5.13. The left column of the window displays several components of the IAS server that you can manage, including the following:
-
RADIUS Clients Lists the clients (RRAS servers) currently configured and allows you to add new clients.
-
Remote Access Logging Lists log files and allows you to configure additional logging options.
-
Remote Access Policies Lists current policies and allows you to add policies. IAS policies are identical to those used on RRAS servers.
-
Connection Request Processing Includes options for forwarding authentication requests to another IAS or RADIUS server for processing.
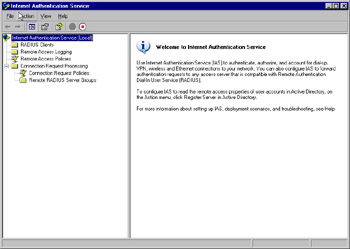
Figure 5.13: The IAS Management Console
IAS Monitoring
You can monitor the status of the IAS server using Windows Server 2003’s standard monitoring facilities, including Event Viewer and System Monitor. IAS also supports Simple Network Management Protocol (SNMP) for centralized monitoring of IAS, along with other devices and services.
IAS also adds a number of objects to the System Monitor utility when you install it. You can use the counters within these objects to monitor the performance of the IAS server. To use System Monitor, select Start | Administrative Tools | Performance, click the Add Counters (+) button, and select one of the IAS objects to view a list of the available counters.
IAS SDK
Microsoft also makes an IAS Software Development Kit (SDK) available. You can use this to create customized behaviors for IAS, control the number of network sessions available to users, and create customized methods of authorization and authentication. The SDK also includes development tools for the Extensible Authentication Protocol (EAP) to allow you to create new types of authentication. EAP is described in the next section.
Authentication Methods
The Windows Server 2003 IAS server supports a number of different authentication methods. These range from basic, unencrypted authentication to highly secure methods. Windows Server 2003 also supports an infrastructure that allows external methods of authentication, such as smart cards. In the following sections, we will discuss authentication methods supported by IAS.
PPP-based Protocols
IAS supports several simple authentication methods based on the authentication used with PPP. These are the same basic methods supported by native RRAS authentication. The following are the basic authentication methods you can select:
-
Unencrypted Password (PAP) This option uses PAP, a basic unencrypted authentication method. Since PAP transmits passwords as plaintext, it provides very little security.
-
Shiva Password Authentication Protocol (SPAP) SPAP is Shiva’s extended version of PAP and is slightly more secure. This protocol is included for use with legacy devices and systems that require it.
-
Encrypted authentication (CHAP) CHAP is a standard protocol that uses encryption to prevent password snooping. In CHAP, the server sends an encrypted challenge to the client, and the client uses the password entered by the user to decrypt it and send a response.
-
Microsoft encrypted authentication (Microsoft-CHAP) MS-CHAP is Microsoft’s extension of CHAP, which improves security and integrates with Windows authentication. Version 1 of MS-CHAP is included to support older operating systems.
-
Microsoft encrypted authentication version 2 (MS-CHAP v2) MS-CHAP version 2 is an improved version that increases security. Since version 2 is supported by all current versions of Windows, you should choose it over version 1, unless you are supporting older clients.
EAP
Another choice for Windows Server 2003 and IAS authentication is EAP. EAP is not strictly an authentication protocol; it is a structure that allows numerous plug-in authentication methods. EAP also allows clients and servers to negotiate the most secure authentication method they both can support.
The EAP Infrastructure
Authentication protocols that fit into EAP are called EAP types. Each of these types is handled by a plug-in module. When a client connects to the server and both support EAP, they negotiate an EAP type for authentication, depending on which types each of them supports. A server that responds to authentication requests is called an authenticator. The authenticator can make any number of requests for information from the client, depending on the authentication type.
Enabling EAP-based Authentication
To enable EAP authentication on an IAS server, you create a Remote Access Policy that allows EAP authentication, or you modify an existing policy. Exercise 5.07 demonstrates how to modify a policy to allow the use of MD5 CHAP authentication through EAP.
Exercise 5.07: Enabling EAP-Based Authentication
You can enable EAP authentication for any Remote Access Policy and specify the EAP types that can be used. Follow these steps to enable EAP authentication:
-
Select Start | Administrative Tools | Internet Authentication Service.
-
The IAS management console is displayed. Click to highlight Remote Access Policies in the left column.
-
In the right column, select Connections to Microsoft Routing and Remote Access Server.
-
Select Action | Properties from the menu, or right-click and select Properties from the context menu.
-
The Properties dialog box is displayed. Click the Edit Profile button.
-
The Edit Dial-in Profile dialog box is displayed. Select the Authentication tab.
-
The authentication methods supported by IAS are displayed, as shown in Figure 5.14. You can enable or disable the non-EAP authentication methods here. You can also change the order in which the selected EAP types are negotiated by moving them up or down in the list, using the Move Up and Move Down buttons.
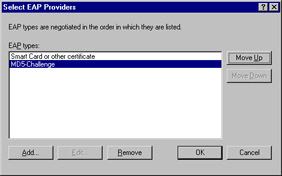
Figure 5.14: Authentication Methods -
Click the EAP Methods button. A list of the currently enabled EAP types is displayed.
-
Click Add and select MD5-Challenge from the list.
-
Click OK, then click OK in the EAP types list.
-
Click OK to exit the Edit Profile dialog box.
-
Click OK to exit the Properties dialog box.
EAP authentication is enabled as long as one or more EAP types appears in the list during this procedure. You can also remove available types from the list to disable EAP types or remove support for EAP altogether.
EAP-MD5 CHAP
EAP-MD5 CHAP is an implementation of the same challenge-response system as MS-CHAP within the EAP infrastructure. It supports the same level of security as MS-CHAP v2, but clients must support EAP in order to authenticate with this protocol. Clients that support MS-CHAP but not EAP will require the non-EAP version of this protocol.
EAP-TLS
Transport Level Security (TLS) is an authentication protocol that uses public-key encryption. All messages between the client and server are securely encrypted. The encryption is similar to that used with the Internet Secure Sockets Layer (SSL) protocol. This is the highest level of security provided by Windows Server 2003’s authentication methods.
| Test Day Tip | EAP-TLS also supports smart cards. These are hardware devices that implement public-key encryption. Smart cards answer challenges within the hardware and do not transmit the private key, so they provide higher security than simple password authentication. For more information about smart card authentication, see Chapter 7. |
EAP-RADIUS
EAP-RADIUS is not a true authentication method. This option is an interface between EAP and RADIUS. When you select EAP-RADIUS, you specify an external RADIUS server, and all requests for authentication are forwarded to the RADIUS server for processing. This provides a way for clients that only support EAP to be authenticated using the RADIUS server.
Authorization Methods
IAS supports a variety of methods of authorization, to determine whether a connection is allowed and what tasks it can perform. Custom authorization methods are also supported. The following sections discuss different types of authorization in IAS.
Dialed Number Identification Service (DNIS)
DNIS is a phone company service that identifies the number being called and allows you to authorize the connection based on that number. It is usually used with 800 and 900 numbers, where there are several different numbers that go into the same public exchange (PBX) system. In dial-up modem pools where several phone numbers can reach the same group of modems, you can use DNIS authorization to ensure that users are calling a valid number.
Automatic Number Identification (ANI) and Calling Line Identification (CLI)
You are probably familiar with caller ID, which works on consumer phone lines to provide the number from which a call originated. ANI and CLI are the business-line equivalent services. IAS can authorize connections based on ANI or CLI to allow access to valid incoming numbers.
Guest Authorization
Windows Server 2003’s IAS service can optionally allow guest access for unauthorized users using the Guest user account. Because this access is unauthenticated, its use is not recommended in most cases, and it is disabled by default.
Access Server Support
In the RADIUS standard, the RADIUS server works with one or more network access servers (NASs) that provide access to the network. In Windows terminology, this usually means RRAS servers. IAS also supports the following alternate types of access servers:
-
RADIUS access server support IAS supports RADIUS standard access servers, whether they are Microsoft servers running IAS or those from other vendors. The standards for RADIUS access servers are defined in RFCs 2865 and 2866.
-
Wireless access points IAS can also provide authentication for wireless access points using the various 802.11 protocols for wireless networking. For this to work, the access point hardware must support RADIUS authentication using an external server.
-
Authenticating switches Some Ethernet switches support RADIUS authentication to authorize nodes attached to the switch. IAS includes the Ethernet port type, which allows you to manage authentication for these switches.
Outsourced Dialing
IAS supports outsourced dialing (sometimes called wholesale dialing), a standard for the use of ISP modem pools. In this system, you contract with an ISP to provide your employees remote network access using the ISP’s existing modems. Users connect to a modem at the ISP, and a server at the ISP creates a VPN tunnel to connect them to the LAN. A RADIUS server at the ISP can forward records to your organization’s IAS server, which allows you to manage access to the modems and obtain auditing and accounting information for their use.
Outsourced dialing has a number of advantages. The ISP already maintains pools of modems, and you may be able to obtain access to them at a lower price than the cost of configuring your own modems. The ISP may also have physical presence in areas you do not have a facility to provide for local calls, and it relieves you of the burden of managing modem pools.
|
EAN: 2147483647
Pages: 173