Integrating ISA Server with Other Services
|
ISA Server software does not operate in a vacuum; it must interoperate with other services and applications on the computer and on your network. In this section, we look at some common interoperability and integration issues. Specifically, we examine how ISA works in conjunction with:
-
Windows Active Directory Services
-
Windows Routing and Remote Access Services (RRAS)
-
Internet Information Server (IIS)
-
The IP Security protocol (IPsec)
-
Windows NT 4.0 domains
It is also important to be aware of those services with which ISA Server cannot peacefully coexist. For example, you cannot use Internet Connection Sharing or the Windows 2000 Network Address Translation (NAT) functions to provide Internet connectivity on a computer that is running ISA Server. ISA replaces ICS/NAT, providing translation services along with security and caching.
Understanding Interoperability with Active Directory
The Windows 2000 Active Directory is a hierarchical database that is stored on Windows 2000 domain controllers. It holds information about objects on the network (users, groups, computers, printers, files, and other network resources). The Active Directory controls logon authentication, serving the same function as the Security Accounts Management (SAM) database in Windows NT. Active Directory Services provides for easy accessibility to network resources by authorized users.
Stand-Alone versus Array Member
The way in which ISA Server interacts with the Windows 2000 Active Directory is dependent on how ISA is installed: as a stand-alone server or as a member of an array.
When ISA is installed as a stand-alone system, its configuration information is saved to the Registry on the local machine. However, if you install ISA as an array member (or promote a stand-alone server to array membership status), the ISA configuration information is then stored in Active Directory. This means that information will be replicated to all domain controllers in the domain. This system obviously provides a measure of fault tolerance that a stand-alone server does not have.
The Active Directory Schema
Active Directory is governed by a set of rules called the schema, which define object classes and attributes (these are called metadata because they describe "data about data"). The content of the schema is controlled by a single domain controller that holds the role of schema master.
When Windows Active Directory is installed, the schema contains a basic set of metadata. However, the schema can be extended; members of the schema administrators group can define new classes or new attributes for existing classes. The schema is also extended by some programs, which need new object classes and/or attributes in order to function.
| Note | Programmers use the Active Directory Service Interfaces (ADSI), available in the Windows 2000 SDK, to write programs that extend the schema. |
When the first member of an ISA Server array is to be installed, you must first initialize the enterprise. This automatically makes the necessary extensions to the Active Directory schema.
ISA Server and Domain Controllers
Although the ISA configuration is stored on the Windows 2000 domain controllers, you do not have to install ISA Server on a domain controller. It is actually preferable that the ISA computer not be a domain controller, for a couple of reasons:
-
Performance of the ISA server will be improved if the computer is not a domain controller, because domain controller tasks require significant resources.
-
Security of the domain controller is improved if you place the domain controller (s) behind the ISA server on the local network, thus allowing the ISA server to protect the domain controller (s) from unauthorized access.
Because Active Directory is required in order to install ISA Server as an array member, ISA servers cannot be array members in a Window NT 4.0 domain.
Understanding Interoperability with Routing and Remote Access Services
Windows 2000 Routing and Remote Access Services (RRAS) provide a collection of services that allow a Windows 2000 server to function as a full-fledged software router, forwarding IP packets from one subnet or network to another, or as a dial-up server and to create and control dial-up networking policies and virtual private networking connections across WAN links.
RRAS Components
The RRAS console allows you to configure a number of components, including:
-
Enabling IP Routing to allow the server to function as a router on the local network and as a demand-dial router
-
Configuring the server to assign IP addresses via DHCP or a static address pool
-
Enabling the remote access server service
-
Enabling support for multilink PPP, Bandwidth Allocation Protocol (BAP), Link Control Protocol (LCP) extensions, and/or software compression
-
Selecting an authentication method for remote access clients and demand-dial routers, using Windows authentication or RADIUS
-
Selecting one or more authentication protocols (EAP, MS-CHAPv1 or v2, CHAP, SPAP, PAP) and allowing remote access without authentication
-
Configure remote access logging properties
-
Create demand-dial routing interfaces
-
View remote access client connections
-
Configure ports (modem, PPTP/L2TP, parallel routing)
-
Add and configure routing protocols (IGMP, NAT, RIP, OSPF)
-
Configure a DHCP relay agent
-
Create remote access policies
-
Configure static routes and view the Windows 2000 routing table
RRAS and ISA Server
RRAS can be enabled on an ISA Server computer. The ISA server can also function as a remote access server or VPN server.
However, there is one RRAS feature that is not compatible with the ISA Server software. You cannot use the NAT protocol on a server that is running ISA Server. The reason for this is that ISA Server provides its own translation service, which is more sophisticated and robust than the Windows NAT.
| Note | Although the ISA address translation service provides sophisticated NAT functionality, some tasks that ISA's S-NAT cannot do, such as port mapping, can be done using Windows 2000's NAT. |
If NAT is installed on a server on which you want to install ISA, you should delete it. The same is true of Internet Connection Sharing (ICS), a "light" form of NAT that is also included with Windows 2000 Server and is configured on a connection via the Network and Dialup Connections properties.
Understanding Interoperability with Internet Information Server
Microsoft Proxy Server required the presence of IIS in order to function. However, ISA does not require that IIS be installed on the ISA server, although you can install IIS on your ISA computer if you desire.
IIS Functionality
Windows 2000 Server includes IIS 5.0, and it is installed by default when you install the operating system. However, you can elect not to install it in a custom installation, or you can remove it later using the Add/Remove Programs applet in the Control Panel.
| Note | IIS 5.0 will not be installed by default if you upgraded to Windows 2000 from Windows NT 4.0 and IIS 4.0 was not installed on the NT system. |
IIS is Microsoft's Web server software, which also includes NNTP, FTP, and SMTP functionality. IIS 5.0 supports Active Server Pages (ASP); Windows Media Services (WMS), which is installed separately as a Windows component from Add/Remove Programs; distributed authoring and versioning; and other advanced features. IIS can be used to make documents and Web objects available over the Internet or on an intranet.
Publishing IIS to the Internet
If you do choose to install IIS on the ISA computer, there are two ways you can publish IIS to the Internet:
-
Using Web publishing rules
-
Using packet filters
Using Web Publishing Rules
The first way to publish the Web server that runs on the ISA Server computer is by configuring Web publishing rules. Note that you need to configure IIS not to use the ports that are used by ISA Server for outgoing and incoming Web requests (ports 8080 and 80, respectively, by default). You can also configure IIS to listen on a different IP address.
| Note | When using Web publishing rules, you must associate the Web server with an internal IP address and change the port it uses to a different port number. |
Using Packet Filters
You can allow IIS to continue using TCP port 80 to listen for Web requests if you configure an IP packet filter to map incoming requests on that port to IIS. In this case, you should ensure that ISA's autodiscovery is not set to listen on port 80. If you use this method, you should not create Web publishing rules to publish the Web server.
Note that this is not the preferred method of publishing, because it cannot take advantage of dynamic packet filtering.
| Note | When you install ISA Server, the World Wide Web Publishing Service (w3svc) will be stopped. After you finish the installation, you should first change the port on which IIS will listen, and then restart the w3svc. |
Understanding Interoperability with IPSecurity
The IP Security Protocol (IPsec) support is a new feature in Windows 2000 that was not included in Windows NT 4.0. IPsec is an Internet standard, developed by the Internet Engineering Task Force (IETF).
| Note | IPsec specifications are defined in RFC2401. |
IPsec provides security for data as it travels across a TCP/IP network. Although there are other methods of encrypting data, IPsec enjoys a distinct advantage: It operates at the Network layer (Layer 3) of the OSI model. This means that, unlike Application layer encryption protocol uses, there is no requirement for the network applications to be IPsec aware.
IPsec uses cryptographic security services to provide for confidentiality and integrity of transmitted data and authentication of the identity of the sender.
How IPsec Works
To secure and authenticate transmissions, IPsec uses two protocols:
-
Authentication Header (AH) AH signs the entire data packet, providing authentication and integrity but not confidentiality, because it doesn't encrypt the data. AH can be used alone when it is not necessary that the message be kept secret—only that you ensure that it cannot be modified and that the sender's identity is verified.
-
Encapsulating Security Payload (ESP) ESP does not sign the entire packet (except in the case of tunneled data), but it does encrypt the data, providing confidentiality.
Both protocols support two modes: transport (which provides end-to-end security) and tunnel (which provides gateway-to-gateway security).
IPsec uses Security Associations (SAs) to establish a secure connection. An SA is a combination of policy and keys that define how data will be exchanged and protected. The Internet Security Association and Key Management Protocol (ISAKMP) is used in conjunction with the Oakley key generation protocol, in compliance with IETF standards. ISAKMP/Oakley uses a two-stage process that employs negotiated encryption and authentication algorithms, which are agreed on by the sending and receiving (or source and destination) computers.
In Windows 2000's implementation of IPsec, properties of security associations are governed by IPsec policies.
How IPsec Is Configured in Windows 2000
Windows 2000 allows you to set IPsec policies via Group Policy, which can be configured on a local machine via the Local Security Settings administrative tool or for a domain by editing the domain's Group Policy Object (GPO), as shown in Figure 25.24.
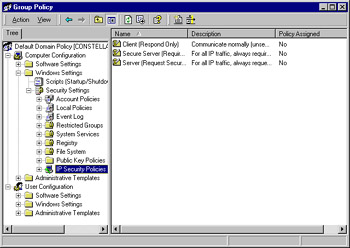
Figure 25.24: IPsec Policies Are Configured Via Windows 2000 Group Policy
One option you have when editing the properties of an IPsec policy is to select which of the two IPsec protocols will be used. The Security Method Wizard allows you to configure the security method (Microsoft uses the term security methods to refer to the IPsec protocols), as shown in Figure 25.25.
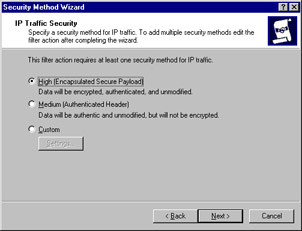
Figure 25.25: You Can Select the IPsec Protocol to Be Used Via the Security Method Wizard
You can use ESP and AH together to provide added security if you want the data encrypted and the entire packet signed. However, you cannot specify both protocols during the wizard process; you must edit the filter action afterward to add a second security method.
| Note | IPsec is a complex topic; exploring all facets of its operation is beyond the scope of this book. For more information, see RFC2401 or IP Security for Windows 2000 Server at www.microsoft.com/windows2000/techinfo/howitworks/security/ip_security. |
Microsoft implements IPsec in Windows 2000 via the IPSec driver. Let's take a look at this component.
IPsec and ISA Server
The IPsec driver can be enabled on a computer running ISA Server. Doing so is necessary if the ISA server is functioning as a VPN server using the Layer 2 Tunneling Protocol (L2TP). L2TP uses IPsec for data encryption, to ensure confidentiality of the communications sent across the internetwork via the tunnel, thus making the virtual network a "private" one.
When IPsec is not enabled on the ISA server, the ISA policy determines which packets are allowed or blocked. However, if IPsec is enabled, AH and ESP protocols (which are IP protocols 30 and 51, respectively) are controlled by the IPsec driver instead of the ISA Server packet filter driver. The IPsec driver allows only valid AH and ESP traffic to enter the network.
Note that when ISA Server is configured to block IP fragments, AH and ESP fragments will be blocked along with all others, even when IPsec is enabled on the server.
NAT is incompatible with protocols that use IP addresses in fields other than the standard TCP/IP header fields. IPsec encapsulates the TCP/IP headers; thus IPsec cannot be used through an ISA server. IPsec can only be used to encrypt L2TP traffic using the ISA Server machine as the endpoint for a VPN.
| Note | When IPsec is used to encrypt data in an L2TP tunnel, public key computer certificates are used for authentication. At least one computer-level certificate must be configured on each computer (VPN client or server). |
Integrating an ISA Server into a Windows NT 4.0 Domain
You can install Windows 2000 Server as a stand-alone or member server on a computer that is a member of a Windows NT 4.0 domain. (A Windows 2000 server cannot be a domain controller in an NT domain; when you promote a Windows 2000 computer to domain controller status, Active Directory is automatically installed and you must create or join a Windows 2000 domain.)
ISA Server can be installed in stand-alone mode only on a Windows 2000 server in an NT domain. The reason for this is that ISA arrays require Active Directory, and there is no Active Directory in an NT domain.
If you want to provide firewall protection to users who belong to an NT domain and you also want the benefits of ISA array membership (fault tolerance and distributed caching), you can set up a separate Windows 2000 domain on the same network and create a trust relationship between the new domain and the NT domain. Then, you can install an ISA Server array in the new domain.
|
EAN: 2147483647
Pages: 240