ISA Deployment: Planning and Designing Issues
|
When you decide to put together an ISA Server solution for your organization, you should plan ahead. ISA Server is an integral part of your security configuration scheme, and you do not want to merely install the server and hope that everything works out right. Carpenters have an old saying: "Measure twice, cut once." If you thoroughly map out your design, you'll avoid pitfalls in your deployment and further down the line.
In this section, we focus on planning and design issues as they relate to the installation of ISA Server. The primary issues of concern are:
-
Network and hardware specifications
-
The edition of ISA Server to be installed
-
The mode in which ISA Server will be installed
-
Stand-alone versus array configurations
-
Client configuration requirements
-
ISA Server Internet connectivity
You should make firm decisions about each of these ISA Server design issues before you begin your installation. The conclusions you reach at this point will determine your choices when it comes time to install ISA Server.
Assessing Network and Hardware Requirements
Prior to installing ISA Server, you need to assess hardware requirements to meet the needs of your organization's ISA Server deployment plan. An organization that has 50 network clients and chooses to use only the Web proxy service will have very different requirements than an organization with 30,000 network clients that wants to avail itself of all the networking services ISA Server has to offer.
System Requirements
Whether you choose to install one or 100 ISA servers, each server must meet minimum hardware and software requirements. The minimum requirements for any ISA server—regardless of the role the machine might play on the network are:
-
Windows 2000 Server or Windows Server 2003 family operating system with the latest service pack installed
-
A Pentium II or K7 (Athlon) Processor running at 300MHz or faster
-
A minimum of 256MB of RAM (Microsoft recommended)
-
A minimum of 20MB for the program files
-
A minimum of 2GB for the Web cache
-
At least two network interfaces—one to the internal network and a second to an external network, such as the Internet or corporate backbone (the exception is an internal caching-only server)
-
Partitions formatted as NTFS to store the program, log, and cache files
-
A Windows 2000 domain if Enterprise Policies will be implemented
Each of these components requires thoughtful consideration before implementing the ISA Server on your network. Let's look at each in more detail.
Software Requirements
ISA Server must be installed on a Windows 2000 Server or Windows Server 2003. It will not install on Windows NT 4.0 or Windows 2000 Professional. If you try to install ISA Server on a Windows 2000 Server machine that does not have the latest service pack installed, you will get an error message during the installation, informing you that you must first install the service pack before the installation routine can continue.
ISA Server Standard Edition can be installed on any member of the Windows 2000 Server family. The Enterprise Edition of ISA Server must be installed on Windows 2000 Advanced Server, Datacenter Server, or Windows Server 2003. Therefore, if you organization has only the "Server" version of Windows 2000, not the Advanced or Datacenter versions, you need to upgrade before installing ISA Enterprise Edition.
Processor Requirements
Processor requirements are somewhat flexible. It is rather unusual to see a production server in a corporate environment running at 300MHz or less; such a server would be rather long in the tooth at this point. If your servers are even a year old, it's unlikely that they are slower than 500MHz. Because the address translation and rule processing performed by ISA Server is processor intensive, you will benefit from a more powerful processor or multiple processors.
If you configure a large number of packet filters or content and site rules, you'll want to maximize the processor configuration on your server. If you don't plan to implement a lot of rules on the server and will use it primarily for Web caching, a 300MHz machine should present no problems. Table 22.1 will help you assess your processor requirements.
| Note | The rate-limiting factor when it comes to processor requirements can be boiled down to the number of rules per second that ISA Server needs to evaluate. An ISA server with a few rules but high throughput could have roughly the same requirements as a machine that has many rules but little throughput through its external interface. Note that we cannot make a decision based on throughput on the internal interface, because it is assumed that other types of traffic that are not processed by any ISA services could flow through this interface. Therefore, you can use the speed of the external interface as a guideline for the level of processor support your ISA server requires. |
| External Interface Data Rate | Processor Requirement | Type of Connection |
|---|---|---|
| Less than 10Mb/second | Pentium II or K6-2 300MHz | ISDN, cable, or DSL |
| 10–50Mb/second | Pentium III or K7 500MHz | T3 or comparable |
| More than 50Mb/second | Pentium III or K7 500MHz; add a processor for each increment of 50Mb/second | Very Fast |
We have included AMD processor offerings along with the Intel specifications that Microsoft includes in its documentation. Microsoft still doesn't like to talk too much about AMD because of Microsoft's long association with Intel. However, AMD has closed the gap, and its K7/Athlon processors provide superior performance at lower cost. The only reservation you might have regarding the K7 series is its multiprocessor support. At this juncture, it might be wise to go with Intel when designing a multiprocessor solution.
Multiprocessor Support
Keep in mind that ISA Server, Windows 2000, and Windows Server 2003 support multiprocessor system setups. If you are configuring the server as an integrated firewall and Web cache server, and if the server is performing any other duties (such as acting as a domain controller for a dedicated ISA Server domain), you'll want to strongly consider a multiprocessor machine. ISA Server has been certified as Windows 2000 compliant, and part of the certification process included its ability to take advantage of symmetric multiprocessing. Windows 2000 Server supports up to four processors. Windows 2000 Advanced Server supports up to eight processors, and Windows 2000 Datacenter Server and Windows Server 2003 support up to 32 processors.
The number of processors determines how much you'll pay for ISA Server, because the licensing fees are based on the number of processors on the server. Since the costs can increment outrageously for a multiprocessor machine, you should consider installing ISA Server on a system with a single processor, and then carry out performance monitoring to aid you in making a cost/benefit analysis of a multiple-processor solution.
If you do not qualify for the upgrade, you should consider the cost of purchasing Proxy Server 2.0, which is very reasonably priced, and then upgrade your version of Proxy Server to ISA Server. This is especially sound advice if you intend to purchase the Enterprise Version of ISA Server. Open license and select license plans are also available; these can dramatically reduce costs. You'll have to call your local Microsoft representative for the details on these types of licensing.
RAM Configuration
Microsoft recommends that any ISA server you deploy should have at least 256MB of RAM to take advantage of all the product's features. However, we have installed ISA Server on machines with 192MB of RAM without difficulty, and it performed reasonably well in a limited laboratory environment. If you do choose to install ISA Server on machines with less than 256MB of RAM, you should not run any other memory (or processor) intensive services on that machine and should limit such configurations to very small businesses.
| Note | If you are "hardware challenged" and must use a minimal RAM configuration, you should dedicate the machine to ISA only and use it for no other services, not even file-sharing and Web services. |
The Network Address Translation (NAT) tables maintained by ISA Server are stored in RAM. Even in a large network, the NAT tables should not consume much memory. However, ISA Server offers a new feature as part of the Web proxy service: the ability to hold a large portion of the Web cache in RAM. This capability greatly improves cache performance, but you must have a large chunk of RAM to dedicate to the cache in order to realize these benefits.
Hardware designs that include less than 256MB of RAM can experience bottlenecks in Web-caching performance. This is because the ISA Server Web-caching feature takes advantage of RAM to store the Web cache. When there isn't enough RAM to store a good portion of the Web cache in memory, the server must place the files in the disk-based cache. This results in URL retrieval times that are much longer than retrieval times from RAM cache.
The size of the Web cache you want to keep in RAM correlates with the number of users on your network. Table 22.2 provides some general guidelines regarding the relationship between number of users and RAM requirements.
| Users Behind ISA Server | Total ISA Server RAM |
|---|---|
| Fewer than 250 | 192MB (Microsoft states128 MB) |
| 250–2,000 | 256MB |
| More than 2,000 | 256MB plus an incremental increase of 256MB for every 2,000 users |
Note that the Microsoft recommendation for fewer than 250 users correlates with our own recommendation for small, simple networks. However, we believe that the 128MB lower limit is set too low. RAM prices are quite volatile, but they continue to fall with time. We recommend that you get as much RAM as your hardware budget allows. You will notice considerable improvement in Web cache if the amount of RAM in the machine exceeds the size of your Web cache.
Disk Space Considerations
The amount of disk space you allot to your ISA Server configuration can be quite variable. The space required for the program files will always be about 20MB, which shouldn't be an issue on any mission-critical server on which you chose to install ISA Server. However, when you plan your disk space requirements, you must consider other important factors.
The most important issue is the amount of disk space you want to dedicate to the Web cache. Unlike that of Proxy Server 2.0, the ISA Server Web cache is stored in a single file. This single-file format is a lot more efficient than the file system-based storage used in Proxy Server 2.0.
The file system-based storage used in Proxy Server 2.0 also had some security problems because it allowed users with the appropriate permissions to easily view the contents of the cache by opening the individual files. The cache could also be indexed and searched for information that an organization might consider proprietary.
Even though SSL-protected pages were not cached on Proxy Server 2.0, most companies did not protect their internal network Web resources using SSL and used authentication-based access instead. Although access to internal Web servers was secured by requiring authentication, the contents of the interaction were cached and therefore could be made available to users without the users having to actually access the server itself.
The single-file storage system for the Web cache gets around this problem. The .CDAT file used to store cached objects on the ISA server is a database file. You cannot open this file with a text editor or Web browser. However, you can use a tool on the ISA Server CD-ROM called CacheDir.exe to view the contents of the cache and key information about the cache file entries.
Another major advantage of the single-file storage system is that the cache file is not dynamically resized. If you set the cache for a particular drive to 100MB, the .CDAT file will start as 100MB and will not change. Performance gains are realized by avoiding processor cycles required to dynamically resize the file.
Cache Size Considerations
In the past, Microsoft recommended that you begin with a Web cache of at least 100MB plus 0.5MB for each user on the network. These figures were included with the Proxy Server 2.0 documentation. The nature of the Internet and how people interact with the Internet has changed radically since the release of Proxy Server 2.0, and therefore these minimal guidelines no longer apply. To fully realize the advantages of Web caching, you need to create a much larger Web cache.
Table 22.3 provides guidelines for configuring your Web cache. These Web cache recommendations are extremely conservative. Even in small networks, you should plan for a much larger Web cache.
| Number of Users | Disk Space for Web Cache |
|---|---|
| Fewer than 250 | 2GB to 4GB |
| 250–2,000 | 10GB |
| More than 2,000 | 10GB plus another 10GB for every 2000 users |
| Note | The numbers given by Microsoft for disk space allocations are interesting because they represent disparate requirements per user, based on the number of users behind the ISA server. For example, suppose we have 200 users. Let's assume that we choose to use the top recommendation for that number of users, which is 4,000MB (4GB). The number of MB per user is therefore 4,000MB/200 users, which turns out to be 20MB per user. Now, if we have a network that has 2000 clients behind the ISA server, the number of MB per user is 10,000MB (10GB) 2,000, which equals only 5MB per user. |
You need to plan for a larger amount of disk space per user in a larger environment because there will be a wider variation in the per-user statistics. The high-end users will typically throw your averages off and have a disproportional effect on your cache requirements. We therefore recommend that you plan for at least 20MB per user, and if your hardware can support it, try for 50MB per user.
Logging and Reporting
Another factor in determining ISA Server disk space requirements includes the log files and reports that will be stored on your ISA server. The log files can grow very quickly, depending on the level of logging you have configured on your server. If you enable packet filtering and detailed Web proxy service logging, even a small network can easily generate log files in the range of 5 to 10MB per day.
If you are working on larger networks, you can expect your log files to expand at the rate of 50 to 100MB per day if you carry out detailed logging. It is a good idea to dedicate a partition of at least 1GB to your log files if you plan to carry out even a moderate amount of logging. You might also want to compress the partition on which the log files are created. Since these are plain-text files, you should be able to get a compression ratio of 4:1 or greater. Be aware that compression does require additional processor cycles and increases the amount of fragmentation on the drive. If your monitoring sessions indicate a potential processor bottleneck, you should not implement file compression.
You need a month's worth of log files to create many of the more interesting reports that ISA Server can generate. Furthermore, you might want to create reports spanning multiple months, in which case you need all the log files available on disk.
Network Interface Configuration
You should have at least two network interfaces if you plan to use the ISA server as a firewall. However, if you want to use the machine as a Web-caching server only, you can use a computer with a single, internal network interface.
If you configure multihomed computers, at least one of those interfaces will be directly connected to the Internet or to a network backbone. If you connect directly to the Internet, the interface can be an Ethernet connection (for example, to a DSL or cable modem), ISDN, or analog modem connection. For the internal network interface, you will likely use an Ethernet connection.
If you plan to use a perimeter network, that network can be connected to a third interface connected to the ISA server. That interface will be considered an external interface and must be configured with public addresses on a different subnet from the external interface. Figure 22.1 shows the configuration of such a perimeter network.
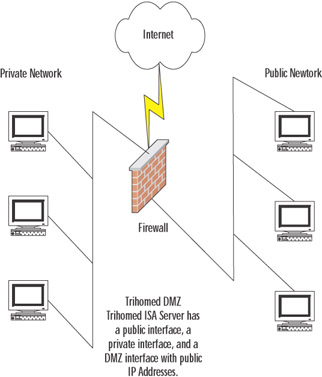
Figure 22.1: A Trihomed Server with a DMZ Network on the Third Interface
| Note | You can also configure a DMZ network between a pair of ISA servers. In this case, the DMZ network interface would be considered an internal interface for the ISA machine because an ISA machine must have at least one internal interface. |
A perimeter network can also be configured to lie between a pair of ISA servers. In this model, an ISA server lies on the edge of the network with an interface directly connected to the Internet, while a second interface is connected to a perimeter network. The second ISA server has one interface connected to the perimeter network; the second interface is connected to the internal network. Note that this intermediary network is a public network and should not be considered part of the internal network.
Figure 22.2 shows what such an intermediary DMZ network configuration might look like.
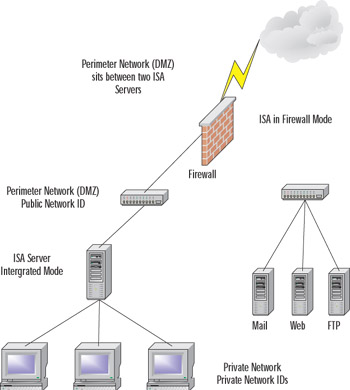
Figure 22.2: An Intermediary DMZ Network
The ISA server that acts only as a Web-caching server can get by with a single internal network interface. Network clients send their requests to the ISA server's internal interface, and the ISA server forwards those requests to its gateway to the Internet. Responses from Internet servers are returned to the single-homed Web-caching server, which in turn returns data to the ISA clients.
Figure 22.3 shows what such a single-homed network configuration might look like.
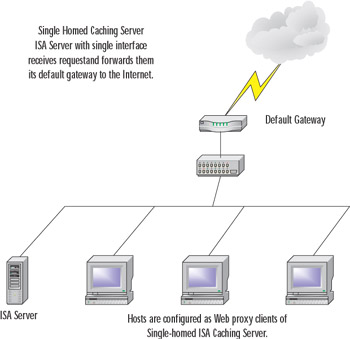
Figure 22.3: A Single-Homed Web-Caching-Only Server
The TCP/IP configuration of the interfaces should be set up correctly before the ISA server is installed. The only interface that should have a default gateway is the external interface of the ISA server. If you have multiple external interfaces that connect to your ISP(s), you can put in gateways for each of those interfaces. However, if you are using multihomed ISA servers in which one of the interfaces has a public IP address for your perimeter network, you should not configure a default gateway on that interface.
The DNS server addresses vary depending on the interface you are configuring. The interfaces connecting to your ISP need DNS entries that can resolve Internet names. These DNS server entries can be your ISP's DNS servers (which is the most typical arrangement), or you can configure the DNS entry to be any other server on the Internet that can resolve Internet addresses.
For your internal interfaces, configure the DNS entry to a server that can resolve the names of the computers on your internal network. It is critically important that you have your DNS infrastructure in place and that it is functional prior to implementing ISA Server, because inbound requests will use your internal DNS server to resolve requests for machines on the internal network.
Securing the Network Interfaces
ISA Server includes features such as packet filtering that will protect your external interface, but there are some general measures you should take in order to prevent potential security breaches.
| Note | The File and Printer Sharing for Microsoft Networks option allows you to turn off or on the Microsoft Server Service. This Server Service allows you to create shares that are accessible to other server message block (SMB) clients on the network. The flip side of the Server Service is the Workstation Server or Redirector. The Redirector (technically, the SMB Redirector) allows a machine to be a client to a machine running the Server Service. When you turn off the Redirector, it will not be able to access SMB shares on a Microsoft network. |
You should always disable file and print sharing for Microsoft networks on the external interface and even for the internal interface of the ISA computer. Due to the inherently insecure nature of the file-sharing protocol (SMB) used on Microsoft systems, you should never expose the file system to SMB access. The ISA server should be a device dedicated to firewall and/or Web-caching functions and should not be used as a file or network application server.
To disable file and print sharing on a particular interface:
-
Open the Interface Properties dialog box.
-
Remove the check mark from the File and Printer Sharing for Microsoft Networks check box.
-
Remove the check mark from the Client for Microsoft Networks option.
-
If you are using a dial-up connection and it is up when you make the changes, hang up the connection and then redial for the new settings to take effect.
Figure 22.4 shows what this process looks like.
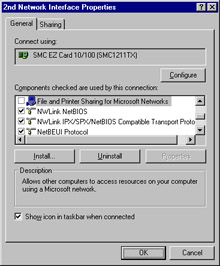
Figure 22.4: Disabling File and Print Sharing on the External Interface
You should also disable the NetBIOS interface on the external interface. No machine on the Internet needs access to the ISA server via NetBIOS over TCP/IP; such access could provide an avenue for attackers to compromise your ISA server. To disable NetBIOS over TCP/IP:
-
Open the Network Interface Properties dialog box.
-
Click the Advanced button.
-
Click the WINS tab. You will see a screen like the one in Figure 22.5.
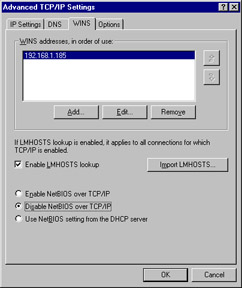
Figure 22.5: Disabling NetBIOS on the External Interface
You might also want to disable NetBIOS on the internal interface. However, you must be careful about doing so, because certain services that you might want to enable, such as the Alerter service, remain dependent on NetBIOS to communicate with stations on the internal network.
| Note | The Alerter service sends ISA messages through Windows networks, which uses NetBIOS. However, you may want to use NetBIOS only on your internal network because doing so will not allow untrusted systems to use this service. |
Note that if your external interface is a dial-up connection such as an analog modem or ISDN terminal adapter, you will not be able to disable the NetBIOS interface via the methods described. In fact, if you go into the properties of the dial-up connection you've configured, you'll not even see the NetBIOS option buttons.
Keep in mind that a dedicated ISDN connection connects to its remote router in the same way that a "dial-up" connection does. The only configuration difference is that the dedicated connection will have a static IP address affixed to the external interface. Another thing to remember is that a dial-up connection can be configured only with a single IP address. ISA Server does not provide the address-pooling features that the Windows 2000 NAT Server provides.
Keep the External Interface Off the LAT
Although this is not an interface configuration option per se, it is related to the internal and external interfaces. The Local Address Table (LAT) keeps track of the internal IP address ranges (the IP addresses used in the internal, or trusted, network). The LAT is used by the ISA server's Firewall Service to determine which networks are internal and which are external. ISA Server does not apply policies to packets destined to an internal network location. If it receives such packets, it merely forwards them.
| Note | The ISA server's LAT is a standard part of how a firewall functions. Many firewalls provide a form of NAT and the LAT is how the ISA server stores it. Linux firewalls call this IP masquerading. |
You will run into problems if the external interface on your ISA server is included in the LAT. If the external interface is seen by ISA Server as local, it assumes that any packets it receives on that interface are from internal network hosts, and it does not apply security policy to those packets. In addition, keep in mind that packet filtering is applied only to external interfaces on the ISA server. If the external interface is on the LAT, no packet filtering rules will apply.
Incorrectly configuring the NAT is a one of the quickest ways to completely disable security provided by ISA Server. Prior to installation, be sure to write down and confirm all the internal network IDs your organization uses so that the LAT is configured properly. During setup, double-check your selections when the LAT Configuration dialog box appears.
|
EAN: 2147483647
Pages: 240
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XII Web Design and E-Commerce
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XIV Product Catalog and Shopping Cart Effective Design