Threats and Attacks
|
Ensuring a physically secure network environment is the first step in controlling access to your network's important data and system files, but it is only part of a good security plan. This is truer today than in the past because networks have more ways in than they once did. A medium-sized or large network can have multiple dial-in servers, virtual private network (VPN) servers, and a dedicated full-time Internet connection. Even a small network is likely to be connected to the Internet part of the time.
Physical Security
One of the most important and at the same time most overlooked aspects of a comprehensive network security plan is physical access control. This matter is often left up to facilities managers and plant security departments or outsourced to security guard companies. Network administrators concern themselves with sophisticated software and hardware solutions that prevent intruders from accessing internal computers remotely while doing nothing to protect the servers, routers, cable, and other physical components of the network from direct access. In far too many supposedly security-conscious organizations, computers are locked away from employees and visitors all day, only to be left open at night to the janitorial staff, who have keys to all offices. It is not at all uncommon for computer espionage experts to pose as members of cleaning crews to gain physical access to machines that hold sensitive data. This is a favorite ploy for several reasons:
-
Cleaning services are often contracted out, and workers in the industry are often transient, so your company employees might not be easily aware of who is or isn't a legitimate member of the cleaning company staff.
-
Cleaning is usually done late at night, when all or most company employees are gone, making it easier to surreptitiously steal data.
-
The cleaning crew members are often paid little or no attention by company employees, who take their presence for granted and think nothing of their being in areas where the presence of others would normally be questioned.
Physically breaking into the server room and stealing the hard disk on which sensitive data resides might be a crude method of breaching security; nonetheless, it happens. In some organizations, it could be the easiest way to gain unauthorized access, especially for an intruder who has help "on the inside."
It is beyond the scope of this book to go into great detail about how to physically secure your network, but it is important for you to make physical access control the outer perimeter of your security plan. This means:
-
Controlling physical access to the servers
-
Controlling physical access to networked workstations
-
Controlling physical access to network devices
-
Controlling physical access to the cable
-
Being aware of security considerations with wireless media
-
Being aware of security considerations related to portable computers
-
Recognizing the security risk of allowing data to be printed
-
Recognizing the security risks involving floppy disks, CDs, tapes, and other removable media
There is also a special type of external intruder who physically breaks into your facility to gain access to your network. Although not a true "insider" because he or she is not authorized to be there and does not have a valid account on the network, this person has many of the advantages of those discussed in the section on internal security breaches. Your security policy should take into account the threats posed by these "hybrid" types of intruders.
Network Security
Virtual intruders never set foot on your organization's property and never touch your computers. They can access your network from across the street or from halfway across the world. But they can do as much damage as the thief who breaks into your company headquarters to steal or destroy your data—and they are much harder to catch. In the following sections, we examine specific network security risks and ways to prevent them.
With the growth of the Internet, many organizations focused their security efforts on defending against outside attackers (that is, those originating from an external network) who are not authorized to access the systems. Firewalls were the primary focus of these efforts. Money was spent on building a strong perimeter defense, resulting in what Bill Cheswick from Bell Labs famously described years ago as "a crunchy shell around a soft, chewy center." Any attacker who succeeded in getting through (or around) the perimeter defenses would then have a relatively easy time compromising internal systems. This situation is analogous to the enemy parachuting into the castle keep instead of breaking through the walls (the technology is off by a few centuries, but you get the idea!). Perimeter defense is still vitally important, given the increased threat level from outside the network. However, it is simply no longer adequate by itself.
Various information security studies and surveys have found that the majority of attacks actually come from inside the organization. The internal threat can include authorized users attempting to exceed their permissions or unauthorized users trying to go where they should not be at all. The insider is potentially more dangerous than outsiders because he or she has a level of access that the outsider does not—to both facilities and systems. Many organizations lack the internal preventive controls and other countermeasures to adequately defend against this threat. Networks are wide open, servers could be sitting in unsecured areas, system patches might be out of date, and system administrators might not review security logs.
The greatest threat, however, arises when an insider colludes with a structured outside attacker. The outsider's skills, combined with the insider's access, could result in substantial damage or loss to the organization.
Attacks can be divided into three main categories:
-
Reconnaissance attacks Hackers attempt to discover systems and gather information. In most cases, these attacks are used to gather information to set up an access or a DoS attack. A typical reconnaissance attack might consist of a hacker pinging IP addresses to discover what is alive on a network. The hacker might then perform a port scan on the systems to see which applications are running as well as try to determine the operating system and version on a target machine.
-
Access attacks An access attack is one in which an intruder attempts to gain unauthorized access to a system to retrieve information. Sometimes the attacker needs to gain access to a system by cracking passwords or using an exploit. At other times, the attacker already has access to the system but needs to escalate his or her privileges.
-
DoS attacks Hackers use DoS attacks to disable or corrupt access to networks, systems, or services. The intent is to deny authorized or valid users access to these resources. DoS attacks typically involve running a script or a tool, and the attacker does not require access to the target system, only a means to reach it. In a distributed DoS (DDoS) attack, the source consists of many computers that are usually spread across a large geographic boundary.
Recognizing Network Security Threats
In order to effectively protect your network, you must consider the following question: from who or what are you protecting it? In this section, we approach the answer to that question from two perspectives:
-
Who Types of network intruders and their motivations
-
What Types of network attackers and how they work
First we look at intruder motivations and classify the various types of people who have the skill and desire to hack into others' computers and networks.
Understanding Intruder Motivations
There are probably as many different specific motives as there are hackers, but we can break the most common intruder motivations into a few broad categories:
-
Recreation Those who hack into networks "just for fun" or to prove their technical prowess; often young people or "antiestablishment" types.
-
Remuneration People who invade the network for personal gain, such as those who attempt to transfer funds to their own bank accounts or erase records of their debts; "hackers for hire" who are paid by others to break into the network. Corporate espionage is included in this category.
-
Revenge Dissatisfied customers, disgruntled former employees, angry competitors, or people who have a personal grudge against someone in the organization.
The scope of damage and extent of the intrusion is often—although by no means always—tied to the intruder's motivation.
Recreational Hackers
Teen hackers who hack primarily for the thrill of accomplishment often do little or no permanent damage, perhaps only leaving "I was here" messages to "stake their claims" and prove to their peers that they were able to penetrate your network's security.
There are more malevolent versions of the fun-seeking hacker, however. These are the cybervandals who get their kicks out of destroying as much of your data as possible or causing your systems to crash.
Profit-Motivated Hackers
Hackers who break into your network for remuneration of some kind—either directly or indirectly—are more dangerous. Because money is at stake, they are more motivated than other hackers to accomplish their objective. Furthermore, because many of them are "professionals" of a sort, their hacking techniques could be more sophisticated than those of the average teenage recreational hacker.
Monetary motivations include:
-
Personal financial gain
-
Third-party payment
-
Corporate espionage
Those motivated by the last goal are almost always the most sophisticated and the most dangerous. Often big money is involved in theft of trade secrets. Corporate espionage agents could be employees who have been approached by your competitors and offered money or merchandise or even threatened with blackmail or physical harm.
In some instances, hackers working for competitors will go "undercover" and seek a job with your company in order to steal data that they can take back to their own organizations. To add insult to injury, these "stealth spies" are then paid by your company at the same time they're working against you to the benefit of your competitor.
There are also "professional" freelance corporate spies. They can be contacted and contracted to obtain your company secrets, or they might do it on their own and auction the data off to your competitors.
These corporate espionage agents are often highly skilled. They are technically savvy and intelligent enough to avoid being caught or detected. Fields that are especially vulnerable to the threat of corporate espionage include:
-
Oil and energy
-
Engineering
-
Computer technology
-
Research medicine
-
Law
Any company that is on the verge of a breakthrough that could result in large monetary rewards or worldwide recognition, especially if the company's involvement is high profile, should be aware of the possibility of espionage and take steps to guard against it.
Vengeful Hackers
Hackers motivated by the desire for revenge are dangerous as well. Vengeance seeking is usually based on strong emotions, which means that these hackers could go all-out in their efforts to sabotage your network.
Examples of hackers or security saboteurs acting out of revenge include:
-
Former employees who are bitter about being fired or laid off or who quit their jobs under unpleasant circumstances
-
Current employees who feel mistreated by the company, especially those who are planning to leave soon
-
Current employees who aim to sabotage the work of other employees due to internal political battles, rivalry over promotions, and the like
-
Outsiders who have grudges against the company, such as dissatisfied customers or employees of competing companies who want to harm or embarrass the company
-
Outsiders who have personal grudges against someone who works for the company, such as employees' former girlfriends or boyfriends, spouses going through a divorce, and other relationship-related problems
Luckily, the intruders in this category are generally less technically talented than those in the other two groups, and their emotional involvement could cause them to be careless and take outrageous chances, which makes them easier to catch.
Hybrid Hackers
Of course, the three categories of hacker can overlap in some cases. A recreational hacker who perceives himself as having been mistreated by an employer or in a personal relationship could use his otherwise benign hacking skills to impose "justice" for the wrongs done to him, or a vengeful ex-employee or ex-spouse might pay someone else to do the hacking.
It is beneficial to understand the common motivations of network intruders because, although we might not be able to predict which type of hacker will decide to attack our networks, we can recognize how each operates and take steps to protect our networks from all of them.
Even more important than the type of hacker in planning our security strategy, however, is the type of attack. In the next section, we examine specific types of network attacks and ways in which you can protect against them.
Categorizing Security Solutions
A multi-layer security plan incorporates multiple security solutions. Security is not a "one size fits all" issue, so the options that work best for one organization are not necessarily the best choices for another. Security solutions can be generally broken down into two categories: hardware solutions and software solutions.
Back to Basics: TCP/UDP Well-Known Ports
The official well-known port assignments are documented in RFC 1700, available on the Web at www.freesoft.org/CIE/RFC/1700/index.htm. The port assignments are made by the Internet Assigned Numbers Authority (IANA). In general, a service uses the same port number with User Datagram Packet (UDP) as with TCP, although there are some exceptions. The assigned ports were originally numbered from 0–255, but the numbers were later expanded to 0–1023.
Some of the most used well-known ports are:
-
TCP/UDP port 20: FTP (data)
-
TCP/UDP port 21: FTP (control)
-
TCP/UDP port23: Telnet
-
TCP/UDP port 25: SMTP
-
TCP/UDP port 53: DNS
-
TCP/UDP port 67: BOOTP server
-
TCP/UDP port 68: BOOTP client
-
TCP/UDP port 69: TFTP
-
TCP/UDP port 80: HTTP
-
TCP/UDP port 88: Kerberos
-
TCP/UDP port 110: POP3
-
TCP/UDP port 119: NNTP
-
TCP/UDP port 137: NetBIOS name service
-
TCP/UDP port 138: NetBIOS datagram service
-
TCP/UDP port 139: NetBIOS session service
-
TCP/UDP port 194: IRC
-
TCP/UDP port 220: IMAPv3
-
TCP/UDP port 389: LDAP
Ports 1024–65,535 are called registered ports; these numbers are not controlled by IANA and can be used by user processes or applications. However, that does not mean that they, too, are not vulnerable to attack. For example, port 1433 is used by SQL, which might be of interest to hackers.
There are a total of 65,535 TCP ports (and the same number of UDP ports); they are used for various services and applications. If a port is open, it responds when another computer attempts to contact it over the network. Port-scanning programs such as Nmap are used to determine which ports are open on a particular machine. The program sends packets for a wide variety of protocols and, by examining which messages receive responses and which don't, creates a map of the computer's listening ports.
Port scanning in itself does no harm to your network or system, but it provides hackers with information they can use to penetrate a network. Potential attackers use port scans in much the same way that a car thief might try the doors of parked vehicles to determine which ones are unlocked. Although this activity does not, in itself, constitute a serious offense, what the person conducting the scan does with the information can present a big problem.
| Note | The intrusion and attack reporting center at www.doshelp.com/PC/trojanports.htm is an excellent resource for information on ports that should be closed, filtered, or monitored because they are commonly used for Trojan and intrusion programs. |
IP Half-Scan Attack
Half scans (also called half-open scans or FIN scans) attempt to avoid detection by sending only initial or final packets rather than establishing a connection. A half scan starts the SYN/ACK process with a targeted computer but does not complete it. Software that conducts half scans, such as Jakal, is called a stealth scanner. Many port-scanning detectors are unable to detect half scans.
IP Spoofing
IP spoofing involves changing the packet headers of a message to indicate that it came from an IP address other than the true source. The spoofed address is normally a trusted port, which allows a hacker to get a message through a firewall or router that would otherwise be filtered out. Modern firewalls protect against IP spoofing.
Spoofing is used whenever it is beneficial for one machine to impersonate another. It is often used in combination with one of the other types of attacks. For example, a spoofed address is used in the SYN flood attack to create a "half-open" connection, in which the client never responds to the SYN/ACK message because the spoofed address is that of a computer that is down or doesn't exist. Spoofing is also used to hide the true IP address of the attacker in ping of death, teardrop, and other attacks. IP spoofing can be prevented using source address verification on your router, if it is supported.
Source-Routing Attack
TCP/IP supports source routing, which is a means to permit the sender of network data to route the packets through a specific point on the network. There are two types of source routing:
-
Strict source routing The sender of the data can specify the exact route (rarely used).
-
Loose source record route (LSRR) The sender can specify certain routers (hops) through which the packet must pass.
The source route is an option in the IP header that allows the sender to override routing decisions that are normally made by the routers between the source and destination machines. Source routing is used by network administrators to map the network or to troubleshoot routing and communications problems. It can also be used to force traffic through a route that will provide the best performance. Unfortunately, source routing can also be exploited by hackers.
If the system allows source routing, an intruder can use it to reach private internal addresses on the Local Area Network (LAN) that normally would not be reachable from the Internet, by routing the traffic through another machine that is reachable from both the Internet and the internal machine. Source routing can be disabled on most routers to prevent this type of attack.
Other Protocol Exploits
The attacks we have discussed so far involve exploiting some feature or weakness of the TCP/IP protocols. Hackers can also exploit vulnerabilities of other common protocols, such as HTTP, DNS, Common Gateway Interface (CGI), and other common protocols.
Active-X controls, JavaScript, and VBScript can be used to add animations or applets to Web sites, or even to HTML e-mail messages, but hackers can exploit these to write controls or scripts that allow them to remotely plant viruses, access data, or change or delete files on the hard disks of unaware users who visit the page and run the script. Both Web browsers and e-mail client programs that support HTML mail are vulnerable.
System and Software Exploits
System and software exploits allow hackers to take advantage of weaknesses of particular operating systems and applications (often called bugs). Like protocol exploits, they are used by intruders to gain unauthorized access to computers or networks or to crash or clog up the systems to deny service to others.
Common "bugs" can be categorized as follows:
-
Buffer overflows Many common security holes are based on buffer overflow problems. Buffer overflows occur when the number of bytes or characters input exceeds the maximum number allowed by the programmer in writing the program.
-
Unexpected input Programmers might not take steps to define what happens if invalid input (input that doesn't match program specifications) is entered. Such input could cause the program to crash or open up a way into the system.
-
System configuration bugs hese are not really "bugs" per se; rather, they are ways of configuring the operating system or software that leaves it vulnerable to penetration.
Popular software such as Microsoft's Internet Information Server (IIS), Internet Explorer (MSIE), and Outlook Express (MSOE) are popular targets of hackers looking for software security holes that can be exploited.
Major operating system and software vendors regularly release security patches to fix exploitable bugs. It is very important for network administrators to stay up to date in applying these fixes and/or service packs to ensure that their systems are as secure as possible.
| Note | Microsoft issues security bulletins and makes security patches available as part of TechNet. See the Web site (www.microsoft.com/technet/treeview/default.asp?url=/technet/security/default.asp). |
Trojans, Viruses, and Worms
Intruders who access your systems without authorization or inside attackers with malicious motives could plant various types of programs to cause damage to your network. There are three broad categories of malicious code:
-
Trojans
-
Viruses
-
Worms
Trojans
The name, short for Trojan horse, refers to a software program that appears to perform a useful function but in fact performs actions that the program user did not intend or was not aware of. Trojan horses are often written by hackers to circumvent the security of a system. Once the Trojan is installed, the hacker can exploit the security holes it creates to gain unauthorized access, or the Trojan program could perform some action such as:
-
Deleting or modifying files
-
Transmitting files across the network to the intruder
-
Installing other programs or viruses
Basically, the Trojan can perform any action that the user has privileges and permissions to perform on the system. This means that a Trojan is especially dangerous if the unsuspecting user who installs it is an administrator and has access to the system files.
Trojans can be very cleverly disguised as innocuous programs, utilities, screensavers, or the like. A Trojan can also be installed by an executable script (JavaScript, a Java applet, Active-X control, etc.) on a Web site. Accessing the site can initiate the installation of the program if the Web browser is configured to allow scripts to run automatically.
Viruses
Viruses include any programs that are usually installed without the user's awareness and perform undesired actions (often harmful, although sometimes merely annoying). Viruses can also replicate themselves, infecting other systems by writing themselves to any floppy disk that is used in the computer or sending themselves across the network. Viruses are often distributed as attachments to e-mail or as macros in word processing documents. Some viruses activate immediately on installation; others lie dormant until a specific date or time or when a particular system event triggers them.
Viruses come in thousands of varieties. They can do anything from popping up a message that says "Hi!" to erasing the computer's entire hard disk. The proliferation of computer viruses has also led to the phenomenon of the virus hoax, which is a warning—generally circulated via e-mail or Web sites—about a virus that does not exist or that does not do what the warning claims it will do.
Real viruses, however, present a real threat to your network. Companies such as Symantec and McAfee make anti-virus software that is aimed at detecting and removing virus programs. Because new viruses are created daily, it is important to download new virus definition files, which contain information required to detect each virus type, on a regular basis to ensure that your virus protection stays up to date.
Worms
A worm is a program that can travel across the network from one computer to another. Sometimes different parts of a worm run on different computers. Worms make multiple copies of themselves and spread throughout a network. The distinction between viruses and worms has become blurred. Originally the term worm was used to describe code that attacked multi-user systems (networks) and virus was used to describe programs that replicated on individual computers.
The primary purpose of the worm is to replicate. Worm programs were initially used for legitimate purposes in performing network management duties, but their ability to multiply quickly has been exploited by hackers who create malicious worms that replicate wildly and might also exploit operating system weaknesses and perform other harmful actions.
Classifying Specific Types of Attacks
The attack type refers to how an attacker gains entry to your computer or network and what he does once he has gained entry. In this section, we discuss some of the more common types of hack attacks, including:
-
Social engineering attacks
-
DoS attacks
-
Scanning and spoofing
-
Source routing and other protocol exploits
-
Software and system exploits
-
Trojans, viruses, and worms
When you have a basic understanding of how each type of attack works, you will be better armed to guard against them.
| Note | In this chapter, we use the words attacker, intruder, or hacker to refer to a person who compromises the security of a network by gaining unauthorized access or who compromises the accessibility of a network by preventing authorized access. |
Social Engineering Attacks
Unlike the other attack types, social engineering does not refer to a technological manipulation of computer hardware or software vulnerabilities and does not require much in the way of technical skills. Instead, this type of attack exploits human weaknesses—such as carelessness or the desire to be cooperative—to gain access to legitimate network credentials. The talents that are most useful to the intruder who relies on this technique are so-called "people skills," such as a charming or persuasive personality or a commanding, authoritative presence.
What Is Social Engineering?
Social engineering is defined as obtaining confidential information by means of human interaction (Business Wire, August 4, 1998). You can think of social engineering attackers as specialized con artists. They gain the trust of users (or even better, administrators) and then take advantage of the relationship to find out the user's account name and password, or they have the unsuspecting users log them on to the system. Because this type of attack is based on convincing a valid network user to "open the door," social engineering can successfully get an intruder into a network that is protected by high-security measures such as biometric scanners.
Social engineering is, in many cases, the easiest way to gain unauthorized access to a computer network. The social engineering competition at a Defcon annual hackers' convention in Las Vegas attracted hundreds of attendants eager to practice their manipulative techniques. Even hackers who are famous for their technical abilities know that people make up the biggest security vulnerability on most networks. Kevin Mitnick, convicted computer crimes felon and celebrity hacker extraordinaire, tells in his lectures how he used social engineering to gain access to systems during his hacking career.
| Note | For more information on Mitnick's lectures, see "Mitnick Teaches Social Engineering," at www.zdnet.com/filters/printerfriendly/0,6061,2604480-2,00.html. |
These "engineers" often pose as technical support personnel, either in-house or pretending to work for outside entities such as the telephone company, the Internet service provider, the network's hardware vendor, or even the government. They often contact their victims by phone, and they usually spin a complex and plausible tale of why they need the user to divulge his or her passwords or other information (such as the IP address of the user's machine or the computer name of the network's authentication server).
Protecting Your Network Against Social Engineers
Protecting against social engineering attacks is especially challenging. Adopting strongly worded policies that prohibit divulging passwords and other network information to anyone over the telephone and educating your users about the phenomenon are obvious steps you can take to reduce the likelihood of this type of security breach. Human nature being what it is, however, some users on every network will always be vulnerable to the social engineer's con game. A talented social engineer is a master at making users doubt their own doubts about his legitimacy.
The "wannabe" intruder could regale the user with woeful stories of the extra cost the company will incur if he spends extra time verifying his identity. He could pose as a member of the company's top management and take a stern approach, threatening the employee with disciplinary action or even loss of job if he doesn't get the user's cooperation. Or he might try to make the employee feel guilty by pretending to be a low-level employee who is just trying to do his job and who will be fired if he doesn't get access to the network and get the problem taken care of right away. A really good social engineer is patient and thorough. He will do his homework, and he will know enough about your company, or the organization he claims to represent, to be convincing.
Because social engineering is a human problem, not a technical problem, prevention must come primarily through education rather than technological solutions.
| Note | For more information about social engineering and how to tell when someone is attempting to pull a social engineering scam, see the preview chapter "Everything You Wanted to Know about Social Engineering—But Were Afraid to Ask" at the Happy Hacker Web site, located at www.happyhacker.org/uberhacker/se.shtml. |
Denial-of-Service Attacks
In February 2000, massive DoS attacks brought down several of the biggest Web sites, including Yahoo.com and Buy.com. DoS attacks are one of the most popular choices for Internet hackers who want to disrupt a network's operations. Although they do not destroy or steal data as some other types of attacks do, the objective of DoS attackers is to bring down the network, denying service to its legitimate users. DoS attacks are easy to initiate; software is readily available from hacker Web sites and warez newsgroups that will allow anyone to launch a DoS attack with little or no technical expertise.
| Note | Warez is a term used by hackers and crackers to describe bootlegged software that has been "cracked" to remove copy protections and made available by software pirates on the Internet, or in its broader definition, to describe any illegally distributed software. |
The purpose of a DoS attack is to render a network inaccessible by generating a type or amount of network traffic that will crash the servers, overwhelm the routers, or otherwise prevent the network's devices from functioning properly. Denial of service can be accomplished by tying up the server's resources—for example, by overwhelming the CPU and memory resources. In other cases, a particular user or machine can be the target of DoS attacks that hang up the client machine and require it to be rebooted.
| Note | DoS attacks are sometimes referred to in the security community as nuke attacks. |
Distributed Denial-of-Service Attack
Distributed DoS (DDoS) attacks use intermediary computers, called agents, on which programs called zombies have previously been surreptitiously installed. The hacker activates these zombie programs remotely, causing the intermediary computers (which can number in the hundreds or even thousands) to simultaneously launch the actual attack. Because the attack comes from the computers running the zombie programs, which could be on networks anywhere in the world, the hacker is able to conceal the true origin of the attack.
Examples of DDoS tools used by hackers are Tribe FloodNet (TFN), TFN2K, Trinoo, and Stacheldraht (German for barbed wire). Early versions of DDoS tools targeted UNIX and Solaris systems, but TFN2K can run on both UNIX and Windows systems.
| Note | An excellent article that provides details on how TFN, TFN2K, Trinoo, and Stacheldraht work is available on the NetworkMagazine.com Web site. You'll find the article, Distributed Denial of Service Attacks, at www.networkmagazine.com/article/NMG20000512S0041. |
It is important to note that DDoS attacks pose a two-layer threat. Not only could your network be the target of a DoS attack that crashes your servers and prevents incoming and outgoing traffic, but your computers could be used as the "innocent middlemen" to launch a DoS attack against another network or site.
DNS DoS Attack
The DNS DoS attack exploits the difference in size between a DNS query and a DNS response, in which all the network's bandwidth is tied up by bogus DNS queries. The attacker uses the DNS servers as "amplifiers" to multiply the DNS traffic.
The attacker begins by sending small DNS queries to each DNS server, which contain the spoofed IP address of the intended victim (see "IP Spoofing" in this chapter). The responses returned to the small queries are much larger in size, so if there are a large number of responses returned at the same time, the link will become congested and denial of service will take place.
One solution to this problem is for administrators to configure DNS servers to answer with a "refused" response, which is much smaller in size than a name resolution response, when they receive DNS queries from suspicious or unexpected sources.
| Note | Detailed information on configuring DNS servers to prevent this problem are contained in the U.S. Department of Energy's Computer Incident Advisory Capability information bulletin J-063, available at www.ciac.org/ciac/bulletins/j-063.shtml. |
SYN and LAND Attack
Synchronization request (SYN) attacks exploit the TCP three-way handshake, the process by which a communications session is established between two computers. Because TCP (unlike UDP) is connection-oriented, a session, or direct one-to-one communication link, must be created prior to sending data. The client computer initiates the communication with the server (the computer that has the resources it wants to access).
The handshake includes the following steps:
-
The client machine sends a SYN segment.
-
The server sends an acknowledge (ACK) message and a SYN, which acknowledges the client machine's request that was sent in Step 1 and sends the client a synchronization request of its own. The client and server machines must synchronize each other's sequence numbers.
-
The client sends an ACK back to the server, acknowledging the server's request for synchronization. When the two machines have acknowledged each other's requests, the handshake has been successfully completed and a connection is established between the two computers.
Figure 1.1 illustrates how the process works.
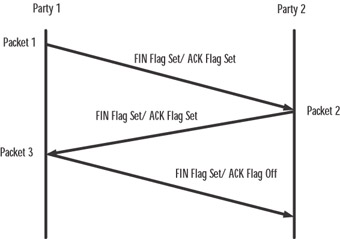
Figure 1.1: TCP Uses a "Three-Way Handshake" to Establish a Connection between Client and Server
This is how the process normally works: a SYN attack uses the handshake process to flood the system targeted as the victim of the attack with multiple SYN packets that have bad source IP addresses, which causes the system to respond with SYN/ACK messages. The problem comes in when the system, waiting for the ACK message from the client that normally comes in response to its SYN/ACK, puts the waiting SYN/ACK messages into a queue. This is a problem because the queue is limited in the number of messages it can handle. When the queue is full, all subsequent incoming SYN packets will be ignored. In order for a SYN/ACK to be removed from the queue, an ACK must be returned from the client or an interval timer must run out and terminate the three-way handshake process.
Because the source IP addresses for the SYN packets sent by the attacker are no good, the ACKs for which the server is waiting never come. The queue stays full, and there is no room for valid SYN requests to be processed. Thus service is denied to legitimate clients attempting to establish communications with the server.
The LAND attack is a variation on the SYN attack. In the LAND attack, instead of sending SYN packets with IP addresses that do not exist, the flood of SYN packets all have the same spoof IP address—that of the targeted computer. The LAND attack can be prevented by filtering out incoming packets for which source IP addresses appear to be from computers on the internal network.
Ping of Death
Another type of DoS attack is the ping of death (also known as the large packet ping). The ping of death attack is launched by creating an IP packet (sometimes referred to as a killer packet) larger than 65,536 bytes, which is the maximum allowed by the IP specification. This can cause the target system to crash, hang, or reboot.
Teardrop
The teardrop attack works a little differently from the ping of death but with similar results. The teardrop program creates IP fragments, which are pieces of an IP packet into which an original packet can be divided as it travels through the Internet. The problem is that the offset fields on these fragments, which are supposed to indicate the portion (in bytes) of the original packet that is contained in the fragment, overlap.
For example, normally two fragments' offset fields might appear as shown here:
Fragment 1: (offset) 100 – 300
Fragment 2: (offset) 301 – 600
This indicates that the first fragment contains bytes 100 through 300 of the original packet, and the second fragment contains bytes 301 through 600.
Overlapping offset fields would appear something like this:
Fragment 1: (offset) 100 – 300
Fragment 2: (offset) 200 – 400
When the destination computer tries to reassemble these packets, it is unable to do so and could crash, hang, or reboot.
Variations on the teardrop include:
-
NewTear
-
Teardrop2
-
SynDrop
-
Boink
All these programs generate some sort of fragment overlap.
Ping or ICMP Flood
The ping flood or ICMP flood is a means of tying up a specific client machine. It is caused by an attacker sending a large number of ping packets (ICMP echo request packets) to the Winsock or dialer software. This action prevents the software from responding to server ping activity requests, which causes the server to eventually time out the connection. A symptom of a ping flood is a huge amount of modem activity, as indicated by the modem lights. This attack is also referred to as a ping storm.
The fraggle attack is related to the ping storm. Using a spoofed IP address (which is the address of the targeted victim), an attacker sends ping packets to a subnet, causing all computers on the subnet to respond to the spoofed address and flood it with echo reply messages.
| Note | During the Kosovo crisis in Eastern Europe, the fraggle attack was frequently used by pro-Serbian hackers against U.S. and NATO sites to overload and bring down their networks. |
You can use programs such as NetXray or other IP tracing software to record and display a log of the flood packets. Firewalls can be configured to block ping packets and prevent these attacks.
Smurf Attack
The Smurf attack is a form of "brute force" attack that uses the same method as the ping flood but that directs the flood of ICMP echo request packets at the network's router. The destination address of the ping packets is the broadcast address of the network, which causes the router to broadcast the packet to every computer on the network or segment. This can result in a very large amount of network traffic if there are many host computers, creating congestion that causes a denial of service to legitimate users.
| Note | The broadcast address is normally represented by all 1s in the host ID. This means, for example, that on class C network 192.168.1.0, the broadcast address is 192.168.1.255 (255 in decimal represents 11111111 in binary), and in a class C network, the last or z octet represents the host ID. A message sent to the broadcast address is sent simultaneously to all hosts on the network. |
In its most insidious form, the Smurf attack spoofs the source IP address of ping packet. Then both the network to which the packets are sent and the network of the spoofed source IP address become overwhelmed with traffic. The network to which the spoofed source address belongs is deluged with responses to the ping when all the hosts to which the ping was sent answer the echo request with an echo reply.
Smurf attacks can generally do more damage than some other forms of DoS, such as SYN floods. The SYN flood affects only the ability of other computers to establish a TCP connection to the flooded server, but a Smurf attack can bring an entire ISP down for minutes or hours. This is because a single attacker can easily send 40 to 50 ping packets per second, even using a slow modem connection. Because each packet is broadcast to every computer on the destination network, the number of responses per second is 40 to 50 times the number of computers on the network, which could be hundreds or thousands. This is enough data to congest even a T-1 link.
One way to prevent a Smurf attack from using your network as the broadcast target is to turn off the capability to transmit broadcast traffic on the router. Most routers allow you to turn off this option. To prevent your network from being the victim of the spoofed IP address, you need to configure your firewall to filter out incoming ping packets.
UDP Bomb or Flood
An attacker can use the UDP and one of several services that echo packets on receipt to create service-denying network congestion by generating a flood of UDP packets between two target systems. For example, the UDP chargen service on the first computer (which is a testing tool that generates a series of characters for every packet that it receives) sends packets to another system's UDP echo service, which echoes every character it receives. By exploiting these testing tools, an endless flow of echoes goes back and forth between the two systems, congesting the network. This is sometimes called a UDP packet storm.
In addition to port 7, the echo port, an attacker can use port 17, the quote-of-the-day service (quotd), or the daytime service on port 13. These services also echo packets they receive. UDP chargen is on port 19. Disabling unnecessary UDP services on each computer (especially those mentioned) or using a firewall to filter those ports and services will protect you from this type of attack.
UDP Snork Attack
The snork attack is similar to the UDP bomb. It uses a UDP frame that has a source port of either 7 (echo) or 9 (chargen), with a destination port of 135 (Microsoft location service). The result is the same as that of the UDP bomb: a flood of unnecessary transmissions that can slow performance or crash the systems that are involved.
Mail Bomb Attack
A mail bomb is a means of overwhelming a mail server, causing it to stop functioning and thus denying service to users. This is a relatively simple form of attack, accomplished by sending a massive quantity of e-mail to a specific user or system. Programs available on hacking sites on the Internet allow a user to easily launch a mail bomb attack, automatically sending floods of e-mail to a specified address while protecting the attacker's identity.
A variation on the mail bomb program automatically subscribes a targeted user to hundreds or thousands of high-volume Internet mailing lists, subsequently filling the user's mailbox and/or the mail server. Bombers call this attack list linking. Examples of these mail bomb programs include Unabomber, Extreme Mail, Avalanche, and Kaboom.
The solution to repeated mail bomb attacks is to block traffic from the originating network using packet filters. Unfortunately, this solution does not work with list linking, because the originator's address is obscured; the deluge of traffic comes from the mailing lists to which the victim has been subscribed.
Scanning and Spoofing
The term scanner, in the context of network security, refers to a software program that hackers use to remotely determine the TCP/UDP ports that are open on a given system and thus vulnerable to attack. Scanners are also used by administrators to detect vulnerabilities in their own systems in order to correct them before an intruder finds them. Network diagnostic tools such as the famous Security Administrator's Tool for Analyzing Networks (SATAN), a UNIX utility, include sophisticated port-scanning capabilities.
A good scanning program can locate a target computer on the Internet (one that is vulnerable to attack), determine the TCP/IP services running on the machine, and probe those services for security weaknesses.
| Note | A common saying among hackers is, "A good port scanner is worth a thousand passwords." |
You can find excellent resources for information about the history of scanning, how scanners work, and some popular scanning programs available as freeware on the Internet.
Port Scanning
Port scanning refers to a means of locating "listening" TCP or UDP ports on a computer or router and obtaining as much information as possible about the device from the listening ports. TCP and UDP services and applications use a number of well-known ports, which are widely published. The hacker uses his knowledge of these commonly used ports to extrapolate information.
For example, Telnet normally uses port 23. If the hacker finds that port open and listening, she knows that Telnet is probably enabled on the machine. She can then try to infiltrate the system by, for example, guessing the appropriate password in a brute force attack.
For example, a traditional Ethernet hub sends all data out every port on the hub. An intruder who has access to the hub can plug a packet-sniffing device (or a laptop computer with sniffer software) that operates in "promiscuous mode" (in which packets can be captured and read regardless of their source or destination) into a spare port and capture data sent to any computer on the segment, as shown in Figure 1.2.
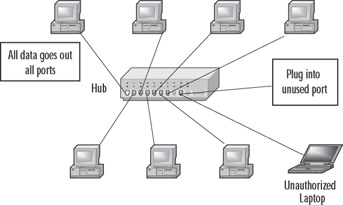
Figure 1.2: An Intruder with Access to the Hub Can Easily Intercept Data
| Note | Packet sniffers are also called protocol analyzers or network analyzers. Sniffer and Sniffer Pro are two packet-sniffer products marketed by Network Associates. |
Although switches and routers are somewhat more secure than hubs, any device through which the data passes is a point of vulnerability. Replacing hubs with switches and routers makes it more difficult for an intruder to "sniff" on your network, but it is still possible to use techniques such as Address Resolution Protocol (ARP) spoofing. This technique is also sometimes called router redirection, in which nearby machines are redirected to forward traffic through an intruder's machine by sending ARP packets that contain the router's IP address mapped to the intruder's machine's Media Access Control (MAC) address. This results in other machines believing the intruder's machine is the router, so they send their traffic to it. A similar method uses ICMP router advertisement messages.
It is also possible, with certain switches, to overflow the address tables with multiple false MAC addresses or send a continuous flow of random garbage through the switch and trigger it to change from bridging mode to repeating mode. This means that all frames would be broadcast on all ports, giving the intruder the same opportunity to access the data that he or she would have with a regular hub. This practice is called switch jamming.
Finally, if the switch has a special monitor port designed to be used with a sniffer for legitimate (network troubleshooting) purposes, an intruder who has physical access to the switch can simply plug into this port and capture network data.
Due to the existence of devices like the ones described here, your network devices should be placed in a locked room or closet and protected in the same manner as your servers.
How Packet Sniffers Work
Packet sniffer and protocol analyzer devices and programs are not used solely for nefarious purposes, although intruders use them to capture unencrypted data and clear-text passwords that will allow them to break into systems. Despite the fact that these devices can be used to "steal" data as it travels across the network, they are also invaluable troubleshooting tools for network administrators. The sniffer captures individual data packets and allows you to view and analyze the message contents and packet headers. This can be useful in diagnosing network communications problems and uncovering network bottlenecks that are impacting performance. Packet sniffers can also be turned against hackers and crackers and used to discover unauthorized intruders.
The most important part of the sniffer is the capture driver. This is the component that captures the network traffic, filters it (according to criteria set by the user), and stores the data in a buffer. The packets can then be analyzed and decoded to display the contents.
It is often possible to detect an unauthorized packet sniffer on the wire using a device called a time domain reflectometer (TDR), which sends a pulse down the cable and creates a graph of the reflections that are returned. Those who know how to read the graph can tell whether and where unauthorized devices are attached to the cable.
Other ways of detecting unauthorized connections include monitoring hub or switch lights, using Simple Network Monitoring Protocol (SNMP) managers that log connections and disconnections, or using one of the many tools designed for the specific purpose of detecting sniffers on the network. These include the following:
-
Antisniff (www.l0pht.com/antisniff)
-
neped (www.apostols.org/projectz/neped)
-
Sentinel (www.packetfactory.net/Projects/sentinel)
In addition, several techniques using PING, ARP, and DNS could help you catch unauthorized sniffers. The use of these techniques is beyond the scope of this book, but you can find instructions for using them (and much more excellent information on packet sniffing) at Robert Graham's Sniffing FAQ Web site, located at www.secinf.net/info/misc/sniffingfaq.html. You can even automate the sending of alerts (messages of notification to the administrator) when the presence of a packet sniffer is detected.
|
EAN: 2147483647
Pages: 240