Section 6.3. IEEE 802.11 Wireless Standard
6.3. IEEE 802.11 Wireless StandardEach wireless LAN user in Figure 6.2 (b) has a wireless LAN adapter for communication over the wireless medium. This adapter is responsible for authentication, confidentiality, and data delivery. To send data to a user in the wired LAN, a user in the wireless LAN first sends the data packet to the access point. The access point recognizes the wireless user through a unique ID called the service-set identification (SSID). SSID is like a password-protection system that enables any wireless client to join the wireless LAN. Once the wireless user is authenticated, the access point forwards data packets to the desired wired user through the switch or hub. Access points build a table of association that contains the MAC addresses of all users in the wireless network. The access point uses this information for forwarding data packets in the wireless network. Figure 6.3 shows a setup whereby the LANs in two buildings are interconnected by wireless bridges . A wireless bridge is basically the same as a regular bridge but is equipped with a wireless transceiver. The most common medium for wireless networks is radio waves at a frequency of 2.4 GHz band . Wireless bridges are also used to interconnect LANs in different buildings. The access range of wireless LANs can be extended by deploying a greater number of access points. Figure 6.3. Connecting two LANs through wireless bridges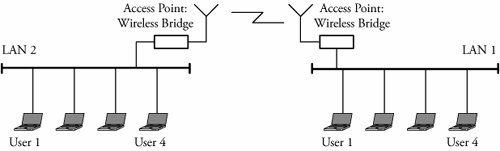 Figure 6.4 shows multiple access points being used to extend the connectivity range of the wireless network. The area of coverage of each access point can be overlapped to adjacent ones to provide seamless user mobility without interruption. Radio signal levels in a wireless LAN must be maintained at an optimum value. Normally, a site survey must be conducted for these requirements. Site surveys can include both indoor and outdoor sites. The surveys are normally needed for power requirements, placement of access points, RF coverage range, and available bandwidth. Figure 6.4. Use of multiple access points to extend the range of wireless access The transmission media used in high-speed LANs are twisted pair and fiber- optic cables. The use of wireless media presents a few advantages, such as user mobility and reduced cost of transmission media. User mobility enables users to access the network resources from any point in the geographic area. Wireless LANs must be reliable and secure in order to be widely deployed. The standards for wireless LANs include 802.11 and its family: 802.11a, 802.11b, and 802.11g. Standard 802.11 typically uses the Carrier Sense Multiple Access with collision avoidance (CSMA/CA) method (see Chapter 5). With this method, each user listens for traffic coming from other users and transmits data if the channel is idle. If the channel is busy, the user waits until the channel becomes idle. The user then transmits data after a random back-off time . This is done to prevent all users from transmitting at the same time when the channel becomes idle. The details of the 802.11 standards are explained further in the next two subsections. The IEEE 802.11 wireless LAN standard defines services for physical, MAC layer, and MAC management protocols. The physical layer is responsible for transmitting raw data over RF or infrared media. The MAC layer resolves access control issues and ensures privacy of transmitted data and reliability of data services. The management protocols ensure authentication and data delivery. 6.3.1. 802.11 Physical LayerIEEE 802.11 operates in the 2.4 GHz band and supports data rates of 1 Mb/s to 2 Mb/s. IEEE 802.11a operates in the 5 GHz band and supports data rates of up to 54 Mb/s. IEEE 802.11b operates in the 2.4 GHz band and supports data rates of 5.5 Mb/s to 11 Mb/s. IEEE 802.11g operates at 2.4 GHz and supports even higher data rates. The IEEE 802.11 physical layer is of four types.
IEEE 802.11a uses OFDM, which uses 12 orthogonal channels in the 5 GHz range. This reduces the interference from other home appliances, unlike the case with 802.11b. The two standards 802.11a and 802.11b can operate next to each other without any interference: 802.11a equipment is more expensive and consumes more power, as it uses OFDM. The frequency channels are nonoverlapping. IEEE 802.11a operates in the 5 GHz band. The achievable Mb/s data rates are 6, 9, 12, 18, 24, 36, 48, and 54. Convolution coding is used for forward error correction. IEEE 802.11b uses DSSS but supports data rates of up to 11 Mb/s. The modulation scheme employed is called complementary code keying (CCK). The operating frequency range is 2.4 GHz and hence can interfere with some home appliances. IEEE 802.11g achieves very high data rates compared to 802.11b and uses the 2.4 GHz frequency band. A combination of encoding schemes is being used in 802.11g. An 802.11g client can operate with an 802.11b access point; similarly, an 802.11b client can operate with an 802.11g access point. 6.3.2. 802.11 MAC LayerIEEE 802.11 provides several key functionalities: reliable data delivery, media access control, and security features. Reliable data delivery is a key feature available in the MAC layer of IEEE 802.11. The imperfections of the wireless medium, such as noise, interference, and multipath effects, may lead to frame loss. IEEE 802.11 uses acknowledgment (ACK) to ensure reliable data delivery. When a source sends a data frame, the destination responds with an ACK to acknowledge receipt of the frame. If the source does not receive an ACK for a certain period of time, it times out the process and retransmits the frame. The request-to-send / clear-to-send (RTS/CTS) scheme also is used to further enhance reliability. When it has data to send, a source sends an RTS signal in the form of a frame to the destination. The destination sends a CTS signal if it is ready to receive data. The source sends the data frame after receiving the CTS signal from the destination. The destination then responds with an ACK to indicate successful receipt of data. This four-way handshake leads to a greater reliability of data delivery. When a source sends an RTS frame, users within the reception range of the source avoid sending any frames during this interval, to reduce the risk of collisions. For the same reason, when the destination sends a CTS frame, users in the reception range of the destination refrain from sending any frames during this interval. Another key functionality is media access control (MAC). Media-access algorithms are of two types: distributed access and centralized access . In distributed-access protocols, media access control is distributed among all the nodes. Nodes use a carrier-sense mechanism to sense the channel and then transmit. Distributed-access protocols are used in ad hoc networks with highly bursty traffic. In centralized-access protocols, the media-access issues are resolved by a central authority. Central-access protocols are used in some wireless LANs that have a base-station backbone structure and in applications that involve sensitive data. The IEEE 802.11 MAC algorithm provides both distributed- and centralized-access features. Centralized access is built on top of distributed access and is optional. The MAC layer consists of two sublayers : the distributed-coordination function (DCF) algorithm and the point-coordination function algorithm (PCF). Distributed Coordination Function (DCF) AlgorithmThe DCF algorithm uses contention resolution, and its sublayer implements the CSMA scheme for media access control and contention resolution. As explained in Chapter 5, a CSMA sender listens for traffic on the medium. If it senses that the medium is idle, it transmits; otherwise , if the medium is busy, the sender defers transmission until the medium becomes idle. DCF has no provisions for collision detection, which is difficult in wireless networks because of the hidden-node problem. To overcome this problem, the interframe space (IFS) technique is used. IFS is a delay whose length is based on frame priority. IFS has three timing levels. The steps in the algorithm follow. Begin DCF Algorithm for Wireless 802.11 MAC
The IFS time-interval technique is based on the priority of the data. The three timing intervals used for IFS are:
Point Coordination FunctionThe point-coordination function (PCF) provides a contention-free service. PCF is an optional feature in IEEE 802.11 and is built on top of the DCF layer to provide centralized media access. PCF includes a polling feature implemented at the centralized polling master (point coordinator). The point coordinator uses the PIFS interval to issue polls . Since this interval is greater than the DIFS interval, the coordinator effectively restrains all asynchronous traffic when issuing a poll. The protocol defines an interval called the superframe interval , which consists of a contention-free period that the point coordinator used to issue polls. The other interval is the contention period used for stations to send normal asynchronous data. The next superframe interval begins only after the medium becomes idle. The point coordinator has to wait during this period to gain access. MAC FrameThe frame format for the 802.11 MAC is shown in Figure 6.5 and is described as follows .
Figure 6.5. IEEE 802.11 MAC frame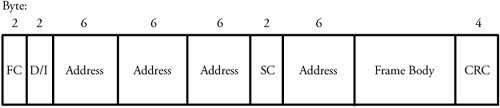 The three frame types in IEEE 802.11 are control frames , data-carrying frames , and management frames . Control frames ensure reliable data delivery. The types of control frames are
Management frames are used to monitor and manage communication among various users in the IEEE 802.11 LAN through access points. 6.3.3. WiFi Technology and 802.11Wireless fidelity (WiFi)a term trademarked by the WiFi Alliancetechnology is a set of standards for wireless local area networks (WLANs). WiFi allows mobile devices, such as laptop computers, digital cameras , and personal digital assistants (PDAs), to connect to local area networks. WiFi is also intended for Internet access and wireless voice over IP (VoIP) phones. Computers can also have built-in WiFi, allowing offices and homes to be networked without expensive wiring. Figure 6.6 shows three WiFi networks connected to the Internet through wireless routers with gateway/bridge . A wireless router with gateway/bridge is a router that can provide radio communications to certain wireless access points, as well as routing to wired Internet devices. Such router/gateways can also communicate with one another. For example, in Figure 6.6, routers A and B are communicating directly to establish connection for WiFi users 1 and 2; these two users could also be connected through the Internet. However, because an Ethernet uses contention access in WiFi, all users wanting to pass data through an access point contend for its attention on a random basis. This can cause nodes distant from the access point to be interrupted by closer nodes, resulting in reducing their throughput. Figure 6.6. Connectivity of wireless users to WiFi access points to reach the Internet and direct wireless connections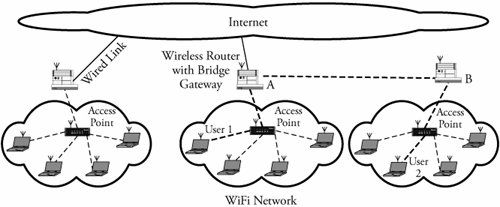 The connection is made by radio link signals. A hotspot is defined as an access point in a geographical region covered by WiFi. The range of an access point built into a typical WiFi home router is 50 meters indoors and 90 meters outdoors. WiFi is based on the IEEE 802.11 standard. The most widespread version of WiFi is based on IEEE 802.11b/g operating over 11 channels (5 MHz each), centered on Channel 1 at 2,412 MHz all the way to Channel 11 at 2,462 MHz. In the United States, maximum transmitter power is 1 watt, and maximum effective radiated power is 4 watts. Several routing protocols are used to set up WiFi devices. One of these protocols is the Optimized Link State Routing (OLSR) protocol developed for mobile networks. OLSR operates as a table-driven and proactive protocol (see Chapter 19 for details). Thus, it regularly exchanges topology information with other nodes of the network. Nodes are selected as multipoint relays by some neighboring nodes. They exchange this information periodically in their control messages. With WiFi, most networks rely heavily on open source software or even publish their setup under an open source license. WiFi allows LANs to be deployed without cabling, thereby lowering the cost of network deployment and expansion. WiFi may be used in places where cables cannot be laid. However, the use of the 2.4 GHz WiFi band does not require a license in most of the world, provided that one stays below the local regulatory limits and accepts interference from other sources, including interference that causes devices to no longer function. However, the 802.11b and 802.11g standards over the 2.4 GHz spectrum used for WiFi are crowded with other equipment, such as Bluetooth devices, microwave ovens, and cordless phones. This may cause degradation in performance, preventing the use of open access points by others. In addition, the power consumption is fairly high compared to that for other standards, making battery life and heat a concern. |
EAN: 2147483647
Pages: 211
- Telecommunications and Network Security
- Security Architecture and Design
- Business Continuity Planning and Disaster Recovery Planning
- Appendix C The Information System Security Architecture Professional (ISSAP) Certification
- Appendix D The Information System Security Engineering Professional (ISSEP) Certification
