Four Firewall Features
| The Cisco VPN Concentrator can detect and interact with several popular firewall software vendors, such as Zone Labs, NetworkICE, Sygate (concentrator software release 4.0), and Cisco's Unity client with the Cisco Integrated Client (CIC) firewall. With the Cisco VPN Concentrator working in conjunction with the firewall clients, you can fortify your VPN's security. As the administrator, you can decide whether you want to implement this feature, and determine what level of firewall policy you wish to enforce from the concentrator.
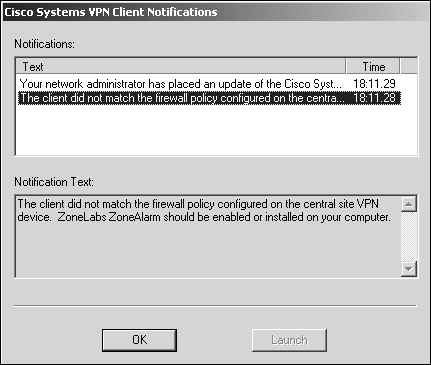
By default, the VPN Concentrator does not enforce any firewall policies to connecting clients. If you decide to turn on this feature, you are given two different options. The first option is to require the presence of an active firewall for connecting clients. If this option is selected, the VPN Concentrator detects whether the assigned firewall is present when the client is establishing its tunnel to the concentrator. If the firewall client is not present or active when connecting to the concentrator, the VPN tunnel is terminated. An alternative selection is to enable the optional firewall setting. This option is similar to the first; however, the firewall is not mandatory for a connection. This allows the administrator to be slightly lax in firewall enforcement in instances when not all connecting clients support the chosen firewall implementation, or the company might be in a state of transition to a particular firewall software feature set. If the connecting client does not have the specified firewall client, the concentrator sends the client a warning notification, as depicted in Figure 7.1. Figure 7.1. Unity client firewall warning message.
After the client has established a connection, the concentrator can implement one of three policy features. The first policy constantly seeks out the connected client and reaffirms that the firewall is still active. This feature, called Are You There (AYT), performs this function by polling the client with AYT messages sent every thirty seconds. If the client's firewall becomes inactive, the VPN Concentrator detects the firewall state as inactive and terminates the tunnel session. In the AYT feature, the firewall client's parameters can be configured and manipulated by the end-user. However, to maintain central control and administration of the client's firewall parameters, Cisco offers another feature in which the policy is pushed down to the client from the VPN Concentrator at the central office. This pushed policy, known as Central Protection Policy (CPP), involves defining traffic rules and applying them to a filter (discussed in Chapter 6, "Advanced VPN 3000 Feature Configuration"). After this filter is created, you can apply it to the policy and enforce it when members of this policy's group connect to the concentrator. As a result, when split tunneling is enabled, you, as the administrator, can determine what networks and protocols can communicate with the client.
A third policy scenario that the Cisco VPN 3000 Concentrator supports is to utilize a Zone Labs Integrity Server (IS) to enforce and maintain the firewall policies. This feature offloads the firewall monitoring responsibility to the IS server. After you define the server in the Configuration | System | Servers | Firewall configuration page, the VPN 3000 Concentrator and the IS server can communicate with each other. If for any reason the IS server requires a tunnel termination, it can interact with the concentrator and instruct it to terminate the session. There is another policy integrated with the Cisco Unity Client that is not controlled or pushed from the VPN 3000 Concentrator. The Stateful Firewall (Always On) policy can be enabled on the individual Cisco VPN Unity clients. With this policy, the Unity Client performs a stateful inspection of incoming and outgoing packets, which blocks all incoming packets that are not tunneled or a response to outgoing requests. Stateful inspection is a packet filtering technology in which session connection information (IP, ports, flags, and sequence numbers) is logged and maintained by a state table. All traffic session data is compared against the state table. If the connection information does not match the entries in the state table, the packets are dropped. If you enforce this policy on the clients themselves, attackers cannot initiate a connection to the client to compromise the device. The only exception to this rule is that incoming DHCP and ESP traffic is allowed to penetrate the stateful firewall to enable DHCP and IPSec functionality. In addition, this stateful firewall is always active and protects the client regardless of VPN tunnel connectivity. This option provides stringent security; however, it is not very flexible because you cannot configure additional incoming traffic to be permitted. |
EAN: 2147483647
Pages: 185