Information Security Management Concepts and Principles
As a CISSP candidate, you must fully understand the three fundamental information security concepts that comprise the C-I-A triad and form the basis of information security (see Figure 6-1):
-
Confidentiality
-
Integrity
-
Availability
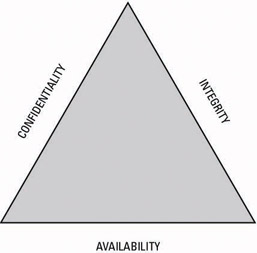
Figure 6-1: The C-I-A triad.
As the figure suggests, all three sides of this triangle depend on each other. If one piece falls apart, the whole thing falls apart. Additionally, all other domains within the CISSP Common Body of Knowledge (CBK) are based on these three important concepts.
Where security is concerned, you also need to understand the defense-in-depth concept, how to avoid single points of failure, and how to incorporate these concepts into security planning.
Confidentiality
Confidentiality prevents the unauthorized use or disclosure of information, ensuring that information is accessible only to those who are authorized access to the information. Privacy is a closely related concept that’s most often associated with personal data. Various U.S. and international laws exist to protect the privacy (confidentiality) of personal data. (Read more on this subject in Chapter 12.)
Instant Answer Privacy ensures the confidentiality of personal data.
Integrity
Integrity safeguards the accuracy and completeness of information and processing methods. It ensures that
-
Modifications to data aren’t made by unauthorized users or processes.
-
Unauthorized modifications to data aren’t made by authorized users or processes.
-
Data is internally and externally consistent; that is, a given input produces an expected output.
Availability
Availability ensures that authorized users have reliable and timely access to information and associated assets when necessary.
Instant Answer The opposite of C-I-A is D-A-D: disclosure, alteration, and destruction.
Defense-in-depth
Defense-in-depth is an information security strategy based on multiple layers of defense. It is often the (desired) result of a holistic approach to information security. Here’s a rundown of the integral parts of a defense-in-depth strategy:
-
Security management principles: These include data classification, personnel security policies and practices, and information security awareness programs.
-
Security technologies: These include firewalls, antivirus software, and intrusion detection systems.
-
Vendor solutions: These include software solutions that are implemented in your technology infrastructure.
For example, to achieve defense-in-depth, an organization might deploy antivirus software from one vendor on servers and a completely different vendor’s antivirus software on user workstations.
Although using multiple solutions increases the management burden for these systems (different support issues and requirements, incompatible logs, and so on), it does produce a blended, in-depth defense. In short, a security posture that doesn’t rely on any single vendor or solution is more likely to be a successful one.
Cross-Reference See Chapter 7 for more on defense-in-depth.
Avoiding single points of failure
A single point of failure is any part of a system, process, or network that will cause the whole system to be unavailable if that component fails. The technical lexicon is full of strategies and solutions that attempt to address single points of failure: reliable systems design, high-availability (HA), clustering, mirroring, and more.
In reality, there are numerous single points of failure in any system, process, or network. To the extent possible, effective security planning attempts to identify and eliminate these single points of failure and thereby avoid a selfinflicted denial of service because of a weak architecture.
When conducting security planning for any new or existing system, process, or network, try brainstorming to identify as many possible single points of failure as you can. Consider the following examples:
-
Systems: Does the system have redundant power supplies and cooling fans? What about separate power sources? Are hard drives configured for RAID? Are components hot-swappable? Can (and should) the system be clustered? Can data be replicated to another system/location in real time?
-
Networks: Do your routers and firewalls fail over automatically? Do they fail back? Do your routers have multiple paths available to your network destinations? Do you have multiple service providers? Do they share the same network POPs (points-of-presence)? What happens if the connection to your telecommunication provider’s central office is cut? Do your multiple telecommunication providers’ networks go through the same telecommunications hotel?
-
Processes: Do your personnel security policies and practices create single points of failure? (Perhaps you’ve instituted a separation of duties and responsibilities but you haven’t established a corresponding rotation of duties and responsibilities. If this sounds familiar, you may actually be causing a process to rely on a single person - that’s a single point of failure!) Do you have contingency processes in place in case a primary system or process isn’t available?
EAN: 2147483647
Pages: 242