Securing Your Remote Access Strategy
You can use IAS authentication, authorization, and accounting to secure your remote access solutions. You can also implement security precautions to protect your IAS server and IAS-related traffic. Figure 7.11 illustrates this process.
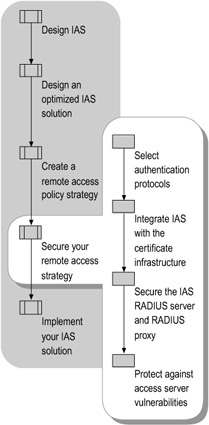
Figure 7.11: Securing Your Remote Access Strategy
Select Authentication Protocols
Windows Server 2003 IAS can perform authentication on behalf of any access server that is configured as a RADIUS client. You can use one of a number of protocols to authenticate dial-up, VPN, wireless, and authenticating switch users before allowing them access to the network.
Before you deploy IAS, determine which authentication protocols you will use to authenticate remote access clients. Use the most secure protocols that your network access servers and clients can support. If you need a high degree of security, you can configure IAS to accept only a few very secure authentication protocols. Alternatively, if your organization requires more flexibility, you can configure IAS to accept less secure authentication protocols when attempts to use more secure authentication protocols are unsuccessful.
Table 7.2 lists the authentication protocols that IAS supports and summarizes the conditions for which each protocol is used and the requirements for each protocol.
| Protocol | Type of Authentication | Protocol Characteristics | Protocol Requirements |
|---|---|---|---|
| Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) | Certificate-based | Works for dial-up, VPN, wireless access, and authenticating switch access. Provides authentication by means of a registry-based user certificate or a smart card. Provides mutual authentication. Generates cryptographic keys, which are needed for wireless LAN connections and for dial-up and VPN connections that use Microsoft Point-to-Point Encryption (MPPE). Enables uninterrupted transfer between wireless access points (user does not need to re-enter credentials when moving between access points). Enables unauthenticated access for visitors. | IAS must be a member of a Windows 2000 or Windows Server 2003 domain. Both client and server must support this protocol. The IAS server must have a certificate installed in the certificate store. The certificate must contain the Server Authentication purpose in EKU extensions. The certificate must meet all other certificate requirements. The client computer or user certificate must contain the Client Authentication purpose in EKU extensions. The certificate must meet all other certificate requirements. The certificate can be installed in the client computer certificate store or on a smart card. |
| Protected Extensible Authentication Protocol (PEAP) | Certificate and password-based (depending upon the selected authentication method) | Currently for 802.1X wireless and authenticating switch clients only. PEAP does not specify an authentication method, but provides a secure "wrapper" for other EAP authentication protocols, such as EAP-MS-CHAPv2, that operate within the outer TLS-encrypted channel provided by PEAP. Enables uninterrupted transfer between wireless access points (user does not need to re-enter credentials when moving between access points). Does not allow unauthenticated access for visitors. | Both client and server must support this protocol. The IAS server must have a certificate installed in the certificate store. The certificate must contain the Server Authentication purpose in EKU extensions. The certificate must meet all other certificate requirements. |
| Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAPv2) | Password-based | Provides mutual authentication. Generates cryptographic keys, which are needed for dial-up and VPN connections that use MPPE. Enables you to change passwords. Works for dial-up and VPN access. | Both client and server must support this protocol. |
| EAP-MSCHAPv2 | Password-based | Provides mutual authentication. Generates cryptographic keys, which are needed for dial-up and VPN connections that use MPPE. Enables you to change passwords. | IAS must be a member of a Windows 2000 or Windows Server 2003 domain. Both client and server must support this protocol. |
| Microsoft Challenge Handshake Authentication Protocol (MS-CHAP) | Password-based | Provides encrypted authentication for Microsoft Windows 98, Microsoft Windows Millennium Edition operating system, or Microsoft Windows NT 4.0 (with the latest dial-up networking upgrade). Generates cryptographic keys, which are needed for dial-up and VPN connections that use Microsoft Point-to-Point Encryption (MPPE). Enables you to change passwords. | Both client and server must support this protocol. |
| Extensible Authentication Protocol-Message Digest 5 (EAP-MD5) | Password-based | Provides less security than EAP-TLS. Does not generate cryptographic keys. Works for dial-up and authenticating switch-based access, but not wireless or PPTP-based VPN access. | Requires a reversibly encrypted password to be stored in the account database (local Security Accounts Manager (SAM) or domain). IAS can be a member of a Windows NT 4.0 domain, a Windows 2000 domain, or a Windows Server 2003 domain. Both client and server must support this protocol. |
| Challenge Handshake Authentication Protocol (CHAP) | Password-based | Provides encrypted authentication for a combination of different operating systems, such as Macintosh or UNIX operating systems. Does not generate cryptographic keying material. | Requires a reversibly encrypted password to be stored in the account database (local SAM or domain). Both client and server must support this protocol and reversibly encrypted passwords. |
| Password Authentication Protocol (PAP) | Password-based | Provides unencrypted authentication. Use only if clients do not support other protocols. Does not generate cryptographic keying material. | Both client and server must support this protocol. |
| Unauthenticated Access | Grants access when the remote access client does not supply authentication credentials. Does not generate cryptographic keying material. | Both client and server must support this protocol. |
Before the IAS server can access Active Directory-based domains to authenticate user credentials and user access account properties, the IAS server must be registered in those domains.
Integrate IAS with the Certificate Infrastructure
Whether you need a certificate infrastructure for IAS depends on whether you are using EAP-TLS as your authentication protocol. If you are using EAP-TLS, you need a certificate infrastructure for your clients. Otherwise, you do not.
A certificate infrastructure consists of the following components:
-
One or more certificate servers
-
An IAS server with a certificate
-
Clients with certificates
For more information about how to design a certificate infrastructure, see "Designing a Public Key Infrastructure" in Designing and Deploying Directory and Security Services of this kit.
When planning how to distribute certificates to clients, decide the following:
-
Whether to use a computer certificate or a user certificate. Computer certificates are available in Windows Server 2003 and Windows 2000. Use them for servers and for computers on a LAN that do not often move. User certificates are new for Windows Server 2003. Use them for roaming users, such as wireless users.
-
How to install the certificate. After the certification authority (CA) is configured, you can install a certificate in three ways. Table 7.3 shows each method and when to use it.
Table 7.3: Selecting a Certificate Installation Method Installation Method
When to Use
By using Group Policy to configure auto-enrollment of computer certificates to computers in a Windows Server 2003 domain.
Use this method if you have large numbers of domain member clients that you need to enroll. In this case, setting up a group policy takes less time than manually obtaining certificates.
This method has the advantage that after auto-enrollment is configured and enabled, all domain member computers receive computer certificates when Group Policy is refreshed next, whether the refresh is triggered manually with the gpupdate command, or by logging on to the domain.
If you use auto-enrollment for user certificates, any user with a valid password can obtain a certificate. This makes your certificate authentication the same as password-based authentication.
By using Certificate Manager to obtain a computer certificate.
Use this method if you have only a few computers, such as IAS servers.
By using Microsoft Internet Explorer and Web-based enrollment.
Use this method if the client is not a member of the domain.
Use this method or smart cards for user certificates.
For specific information about how to perform these steps, see "Computer certificates for certificate-based authentication" in Help and Support Center for Windows Server 2003.
For more information about certificate enrollment methods and domain membership, see "Network access authentication and certificates" in Help and Support Center for Windows Server 2003.
Install Computer Certificates for IAS Servers
If you are using PEAP-EAP-MS-CHAPv2 or EAP-TLS, you must install a computer certificate on your IAS servers. That certificate must be issued from a CA that can follow a certificate chain to a root CA that is trusted by the access clients. Likewise, the IAS server must trust the root CA of the CA that issued the user or computer certificate to the access client.
You can install multiple computer certificates on the IAS servers and configure separate remote access policies to use different computer certificates. However, you can select only a single certificate for all remote access policies that specify authentication by using EAP-TLS.
The server certificate must also contain the Server Authentication purpose in Enhanced Key Usage extensions, and meet other certificate requirements for PEAP and EAP authentication.
To install a certificate on the IAS server, you can use Group Policy and auto-enrollment, the CA Web enrollment tool provided with Certificate Services for Windows Server 2003, or you can request a certificate by using the Certificates snap-in.
For more information about certificate requirements for PEAP and EAP, see "Network access authentication and certificates" in Help and Support Center for Windows Server 2003.
Install Computer Certificates for Access Clients
In addition to adding a certificate to your IAS servers, you must add a certificate to any computer that uses EAP-TLS or PEAP-EAP-TLS authentication. The certificate must be issued from a certification authority (CA) that can follow a certificate chain to a root CA that is trusted by the IAS server.
The computer certificate must also contain the Client Authentication purpose in Enhanced Key Usage extensions and meet other certificate requirements for PEAP and EAP authentication.
For more information about creating a certificate infrastructure, see "Designing a Public Key Infrastructure" in Designing and Deploying Directory and Security Services of this kit.
Secure the IAS RADIUS Server and RADIUS Proxy
It is important to secure your IAS server. Regardless of whether you configure your IAS server as a RADIUS server or a RADIUS proxy, you must apply a number of basic security precautions.
Use strong shared secrets
RADIUS supports a simple password called a secret. Configure strong shared secrets to prevent dictionary attacks, and change them frequently. RADIUS secrets are combined with a 16-byte random number and then passed through a one-way Message Digest 5 (MD5) hash to create a 16-byte encryption value. The 16-byte encryption value is stored with the password entered by the remote access user.
Include RADIUS secrets in your remote access design when you are mutually authenticating RADIUS computers and you encrypt the remote user password. It is best to specify RADIUS secrets that are at least 16 characters in length and that include uppercase letters, lowercase letters, numbers, and punctuation.
Use the Message-Authenticator attribute
Use the Message-Authenticator attribute (also known as a digital signature or the signature attribute) for connection requests that use the PAP, CHAP, MS-CHAP, and MS-CHAPv2 authentication protocols. This attribute ensures that an incoming RADIUS Access-Request message was sent from a RADIUS client configured with the correct shared secret. You must enable the use of the Message-Authenticator attribute on both the IAS server (as part of the configuration of the RADIUS client) and the RADIUS client (the network access server or RADIUS proxy). Ensure that the RADIUS client supports the Message-Authenticator attribute before you enable the attribute. The Message-Authenticator attribute is always used with EAP, regardless of whether it is enabled on the IAS server and access server.
Configure your Internet firewall
In the most common configuration, the Internet firewall is situated on your perimeter network between your secure network and the Internet. The perimeter network (also known as a screened subnet) is an IP network segment that contains resources (such as Web and VPN servers) that are available to Internet users. In this configuration, the IAS server is an intranet resource that is connected to the perimeter network.
If your IAS server is on a perimeter network, configure your Internet firewall to allow RADIUS messages to pass between your IAS server and RADIUS clients on the Internet. You might need to configure an additional firewall that is placed between your perimeter network and your intranet, which allows traffic to flow between the IAS server on the perimeter network and domain controllers on the intranet.
If your IAS server is on the perimeter network, it might use either of the following to contact a domain controller on the intranet:
-
An interface on the perimeter network and an interface on the intranet (IP routing is not enabled).
-
A single interface on the perimeter network. In this configuration, IAS communicates with intranet domain controllers through another firewall that connects the perimeter network to the intranet.
For more information about Internet firewalls, see "Deploying ISA Server" in this book.
Enable remote access account lockout
Enable remote access account lockout to protect against online dictionary attacks. Remote access account lockout disables network access for user accounts after a configured number of failed connection attempts has been reached.
Remote access account lockout can also be used to prevent a malicious user from intentionally locking out a domain account by attempting to make multiple dial-up or VPN connections with the wrong password. You can set the number of failed attempts for remote access account lockout to a number that is lower than the number of logon retries for domain account lockout. By doing this, remote access account lockout occurs before domain account lockout, which prevents the domain account from being intentionally locked out.
For more information about account lockout, see "Remote access account lockout" in Help and Support Center for Windows Server 2003.
Protect Against Access Server Vulnerabilities
Some access servers expose the network to unwanted visitors who can gain access to your network. For example, intruders might connect to an authenticating switch accessible from a conference room network port, set up their own access server to connect to your network, and access your resources. To protect against this form of attack, configure mutual authentication by using PEAP-EAP-MS-CHAPv2 or EAP-TLS as the authentication method for network access connections. For more information about configuring mutual authentication, see "PEAP" in Help and Support Center for Windows Server 2003.
Authenticating RADIUS clients and RADIUS servers also protects against this type of network attack. You can use three methods to authenticate RADIUS clients and RADIUS servers.
RADIUS shared secrets
Include RADIUS shared secrets in your network access design. Specify RADIUS secrets that are at least 22 characters in length and consist of a random sequence of uppercase letters, lowercase letters, numbers, and punctuation.
Secure RADIUS traffic with IPSec
Securing RADIUS traffic with Internet Protocol security (IPSec) provides you with the ability to secure RADIUS servers against unwanted traffic by filtering on specific network adapters (allowing or blocking specific protocols) and enabling you to choose source IP addresses from which traffic is allowed. For organizational units, you can create IPSec policies, which are stored in Active Directory, or you can create local policies on RADIUS servers, and then apply the local policies to specific computers. If you create IPSec policies for an organizational unit, the policy is applied by using Group Policy.
You can enable IPSec between IAS proxies and IAS servers, or between RADIUS clients and IAS servers.
For more information about securing RADIUS traffic with IPSec, see "Securing RADIUS traffic with IPSec" in Help and Support Center for Windows Server 2003.
VPN tunnels
All RADIUS computers that require authorization support VPNs.
EAN: N/A
Pages: 146