Deploying Your IPSec Solution
After scoping your needs, building IPSec policies, and determining your strategy for assigning the policies to specific OUs, test the IPSec policies in a lab environment and conduct a pilot project before rolling them out for production use.
To ensure that IPSec policy functions as expected and provides the appropriate level of security, test specific IPSec policy configurations on clients and servers in a lab environment, and then conduct pilot or beta tests in a limited operational environment before conducting a full-scale deployment. Test both functional behavior and the policy assignment steps required to ensure that one end of the communication does not receive a policy that blocks communication until the other end receives a compatible policy.
Follow the steps shown in Figure 6.11 to deploy IPSec.
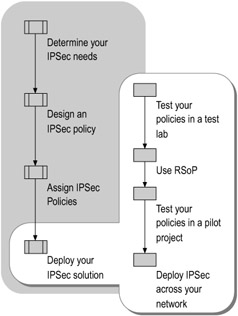
Figure 6.11: Deploying Your IPSec Solution
Testing Your Policies in a Test Lab
Before you roll out IPSec into your production environment, test your IPSec policies by following these steps:
-
Configure a lab in a controlled environment separate from your production network. Make the lab simulate your production environment as closely as possible. For example, you might want to include a perimeter network, a data center server, firewalls or filtering routers, clients with various operating systems, application test configurations, multiple domains with various OUs, and a network with varying connection speeds. Also, make sure to activate those Active Directory services that are running in your production environment.
-
Use the RSoP component of Group Policy to verify that the IPSec policies are being applied the way in which you assigned them, and that the policy you expect takes precedence if multiple policies are applied.
-
Implement your policies on the server and clients to test communication of all software and services. Use the IP Security Monitor snap-in or the netsh ipsec dynamic show mmfilter and netsh ipsec dynamic show qmfllter commands to verify that specific filters are being applied as expected. In the IP Security Monitor snap-in, the Specific Filters nodes display quick mode and main mode filters configured for persistent, local, or domain-based IPSec policies. However, default exemptions to IPSec filtering are not displayed.
-
Look for communications that have failed. Check if any network traffic was blocked by any of the IPSec polices that you have implemented.
-
Simulate a load on the network that is similar to what your network would experience, to test for performance impact.
-
Complete penetration tests to verify that the filters are configured properly and behave as you expect. Verify that the exemptions to IPSec filtering are appropriate.
Use the IP Security Monitor snap-in to gather information you can use to identify problems and optimize performance where IPSec is deployed. For example, you can view details about IPSec policies and filters, statistics about performance, and SAs.
For more information about the IP Security Monitor snap-in, see "Viewing details about active IPSec policies in IP Security Monitor" in Help and Support Center for Windows Server 2003. For more information about setting up a test environment, see "Designing a Test" in Planning, Testing, and Piloting Deployment Projects of this kit.
Using RSoP
You can use RSoP to analyze IPSec policy assignments. RSoP is a Group Policy-related snap-in that you can use to view IPSec policy assignments for a computer or for members of a Group Policy container.
To view IPSec policy assignments in RSoP, you must first open the RSoP snap-in, and then run a query. RSoP allows you to troubleshoot policy precedence issues and determine the exact set of policies that are being used by IPSec clients.
For more information about RSoP, see "Using Resultant Set of Policy to view IPSec policy assignments" in Help and Support Center for Windows Server 2003. For more information about IPSec policy precedence, see "Understanding IPSec Policy Precedence" earlier in this chapter.
Testing Your Policies in a Pilot Project
Verifying successful IPSec operation is an important, and often neglected, step in deploying IPSec. Incorrectly configuring IPSec and related Windows networking components can cause network traffic to be unintentionally blocked or sent unprotected. The specifics of how to verify successful operation depend on the particulars of your deployment. You might need to engage the Help desk and conduct training in the technology, as well as create FAQs or self-help documents and procedures, so that you can quickly isolate problems.
Testing successful IPSec operations is uniquely different from testing other networking components. You can often test for successful operation of a system by performing tests to see if the applications behave as expected. However, applications in the overall system can perform properly while not protected by IPSec. Testing IPSec involves testing that the applications work, and that IPSec is in fact restricting access and performing protection.
It is also important to test IPSec policy management procedures and key IT operations processes, such as:
-
Importing and exporting IPSec policy
-
Remotely managing IPSec policy
-
Initially assigning IPSec policy to different types of computers
-
Changing IPSec policy on each computer
-
Backup and restore operations
-
Server and network monitoring
-
Deploying new domain controllers
-
Unassigning IPSec policy
-
Adding subnets to the network
-
Server scaling
-
Cross-platform IPSec policy compatibility
Finally, coordinate with your network operations team to determine how procedures for responding to internal network attacks might impact the use of IPSec in your network.
For more information about planning and rolling out a pilot project, see "Designing a Pilot Project" in Planning, Testing, and Piloting Deployment Projects in this kit.
Deploying IPSec Across Your Network
The general steps for assigning IPSec policy by using Group Policy are:
-
Create the IPSec policy in the directory. If you have a computer dedicated to using local IPSec policy, you can use the netsh ipsec static importpolicy command or the IP Security Policy Management snap-in.
-
Create a new GPO or identify an existing GPO to use to deliver the IPSec policy assignment. Remember that only members of the Domain Admins group can modify the GPO and assign IPSec policy.
-
Assign the GPO to the domain level or an appropriate OU level, and then resolve any IPSec policy precedence issues. Group Policy objects, which include IPSec policies, can be configured to not be updated over slow links. IPSec policy should always be implemented, regardless of whether the updates must use slow links. If you prevent IPSec policy updates over slow links, communication failures might occur.
-
Plan the rollout of the IPSec policy on both the client and server side. Determine whether to use Group Policy, the IP Security Policy Management snap-in, executable files, or some combination to deploy this technology. If you are going to secure a server, make sure to enable client-side IPSec policy first, allow time for all clients to retrieve the policy, then enable the server-side policy. When configuring the Negotiate security filter action, select the Allow unsecured communication with non-IPSec aware computers check box, so that IKE can fall back to unsecured communication if a remote computer has not yet retrieved IPSec policy.
-
Ensure that IPSec authentication methods are ready before rolling out IPSec policy. All certificate autoenrollment problems must be investigated and resolved before assigning IPSec policy. Any cross-certificate trusts must be established and deployed to all systems first. Likewise, if Kerberos is being used, ensure that all domain trusts between clients and servers are mutually trusted and that Kerberos traffic is permitted. After IPSec policy is applied, if IKE authentication fails, communication will be blocked. For more information about certificate autoenrollment, see "Designing a Public Key Infrastructure" in Designing and Deploying Directory and Security Services of this kit.
EAN: N/A
Pages: 146