How Windows Executes Code
The Windows operating system uses two modes to maintain operating system efficiency and integrity: user mode and kernel mode. The architecture of 80386 and higher processors defines four privilege levels, called rings , to protect system code and data from being overwritten inadvertently or maliciously by less privileged code. This is called the Intel Protection model.
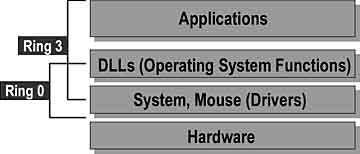
The 0 (zero) privilege level, also known as kernel mode , is the most privileged level. Privilege level 3, or user mode , is the least privileged. When code is running at a given privilege level, it is said to be running in that ring. For example, code running at privilege level 0 is said to run in ring 0. The Windows operating system only uses rings 0 and 3.
Kernel Mode
Kernel mode (ring 0) is the privileged mode of operation in which code has direct access to all hardware and all memory addresses. Software that runs in kernel mode has the following attributes:
- It can access hardware directly.
- It can access all of the memory on the computer.
- It cannot be moved to the virtual memory page file on the hard disk.
- It is processed at a higher priority than user mode processes.
Windows 95 and Windows NT core operating system code runs in kernel mode (ring 0). Because kernel mode components are protected by the processor architecture, the processor prevents one program from writing over another's components. Although ring 0 provides this kind of protection, not everything can run in ring 0 because components have access to the entire system. If a software component fails in ring 0, it can halt the entire system.
Because Windows 95 is designed to be as backwards compatible as possible, many older 16-bit device drivers and applications need direct access to hardware. Windows NT does not provide this level of access, and therefore not all legacy applications will run successfully under Windows NT Workstation and Windows NT Server.
User Mode
User mode (ring 3) is a less privileged processor mode than kernel mode and has no direct access to hardware. Code running in user mode can run only in its own address space. It uses the Windows APIs to request system services.
User mode processes:
- Have no direct access to hardware.
To protect against malfunctioning applications or unauthorized user access, user mode processes cannot directly access hardware. Hardware access requests must be granted by a kernel mode component.
- Are limited to an assigned address space.
Windows helps protect the operating system by limiting the areas of memory that a user mode process can access. This limitation is accomplished by assigning only certain addresses to the user mode process.
- Can be paged out of physical memory into virtual random access memory (RAM) on a hard disk.
Virtual memory, also known as virtual RAM, allows hard disk space to be used as if it were additional memory. The details of virtual memory are covered later in this chapter.
- Process at a lower priority than kernel mode components.
User mode processes are lower in priority; therefore, they have less access to the CPU than processes that run in kernel mode. This ensures that the operating system does not have to wait while an application finishes processing. In addition, any software component that fails in user mode cannot halt the entire system and may not affect any other software component running on the system at the same time.
EAN: N/A
Pages: 324
- The Second Wave ERP Market: An Australian Viewpoint
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Context Management of ERP Processes in Virtual Communities
- Distributed Data Warehouse for Geo-spatial Services
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement