Lesson 3: File Transfer
Lesson 3: File Transfer
There are many different protocols and utilities for transferring information over computer networks. In this lesson you learn about several file transfer and sharing methods and how to secure them. In some cases, the answer to securing these file sharing methods is to completely disable or remove them. In other cases, you'll learn specific actions to take to make file sharing more secure. In most of this lesson the focus is placed on securing file transfer programs for client operating systems. In Chapter 8, specific recommendations for securing file servers are covered.
After this lesson, you will be able to
-
Protect file transfers from packet sniffing
-
Protect your network from security issues related to file-sharing software
Estimated lesson time: 15 minutes
FTP Client Security Issues

There are two basic types of FTP servers: those that require authentication and those that allow anonymous FTP. FTP servers that use authentication require users to supply user names and passwords. Anonymous FTP servers do not require authentication and instead have users log on as "anonymous" and then enter their e-mail address as the password.
One of the major security issues with FTP client/server communications is that it is typically unencrypted. This means that a protocol analyzer, as shown in Figure 6-4, could easily capture passwords.
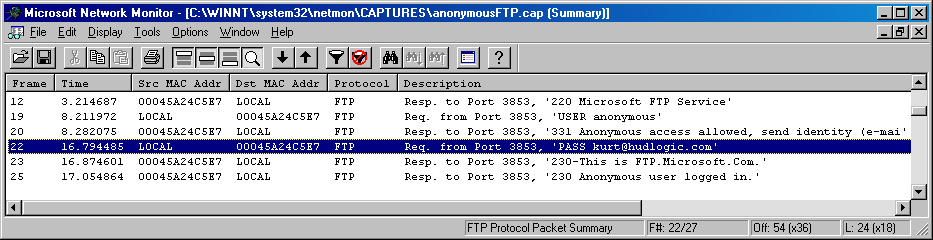
Figure 6-4. FTP packet captures
Figure 6-4 illustrates an anonymous FTP logon exchange. However, a simple packet capture utility can be used to compromise a standard FTP password transmission. However, FTP password transmissions typically transmit using multiple network packets, one character at a time. Further, the files transferred over FTP can also be decoded packet-by-packet and reassembled by attackers with protocol analyzers.
To protect your FTP client/server communications from password sniffing, consider using some type of encryption between them. One solution is to implement a VPN connection between the FTP client and server. Another option is to implement an FTP client and server that support encryption. The following sections cover Secure FTP and Kerberized FTP.
Secure FTP
Secure FTP (SFTP, S/FTP, or S-FTP) supports SSL/TLS encryption for FTP communications. SSL/TLS encryption protects the transfer of the password and all data between the client and server. Both the FTP client and FTP server must have SFTP software to enable encrypted authentication and file transfers. Further, because SSL is used, a CA is required to issue a certificate to the client and server.
SFTP software is available for all major operating systems. Many versions of SFTP are part of secure shell (SSH) software. In addition to SFTP, SSH provides encrypted versions of many remote administration utilities typically associated with administering UNIX systems. Many versions of the UNIX and Linux operating systems come with SSH and SFTP; other operating systems, such as those from Microsoft and Apple, might require additional client software.
More information and examples of SFTP software are available from Glub Tech at http://www.glub.com/products. For more information on SSH, see SSH Communications Security Corporation's Web site at http://www.ssh.com and the OpenSSH Web site at http://www.openssh.com.
Kerberized FTP
Kerberized FTP is based on the Kerberos protocol developed by the Massachusetts Institute of Technology (MIT). Kerberos is a secure asymmetric encryption method that is used to encrypt client/server authentication. Kerberized FTP provides secure authentication between the FTP client and server and it also encrypts file transfers. To use Kerberized FTP, both the FTP client and FTP server must be Kerberized.
To learn more about Kerberized FTP, visit the MIT Web site Help section on Kerberized FTP at http://web.mit.edu.
File Sharing
Many client operating systems are capable of sharing files on the network. The Server Message Block (SMB) and Network File System (NFS) are two of the most popular file-sharing protocols. These protocols often ship as part of popular operating systems such as Microsoft Windows, UNIX, and Linux. Unfortunately many client systems are compromised because users are often unaware that these protocols are enabled. In the following sections you'll learn how to disable SMB and NFS file sharing if it was inadvertently enabled on a client system.
For information on securing an NFS or SMB file server, see Chapter 8.
File sharing is not limited only to preinstalled protocols. Some users intentionally download and install file-sharing software that is often used to trade copyrighted software. Often, this file-sharing software can provide a method for users to download potentially harmful software. Such software is typically categorized as file-trading software. In the following section you'll learn more about the many different types of file-trading software that can pose security risks to your network.
SMB File Sharing
SMB is a file-sharing protocol often used for sharing resources in Microsoft networks. The revised version of SMB is called Common Internet File System (CIFS). Although SMB and CIFS are convenient ways for people to share files on a network, these shares are often exploitable targets for attackers. Network users might enable SMB file sharing and not realize the potential security consequences of doing so. There are many tools available for exploiting these file shares that are not properly secured.
In Microsoft operating systems, SMB/CIFS is enabled and disabled through a service called Microsoft File and Printer Sharing, as shown in Figure 6-5.
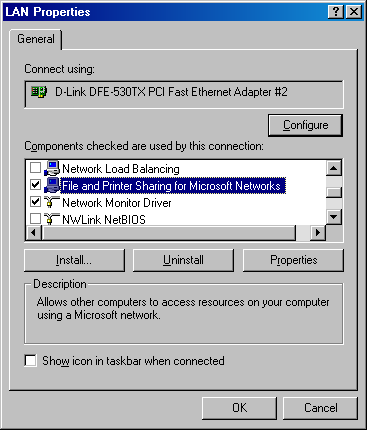
Figure 6-5. SMB file sharing in Microsoft Windows 2000
Other operating systems such as UNIX, NetWare, and Linux can also use SMB and CIFS for file sharing. These non-Microsoft operating systems typically require an additional SMB file-sharing program, such as Samba. Samba is free software that is often included in distributions of UNIX and Linux operating systems. To disable SMB file sharing on non-Microsoft clients, disable the Samba service. The directions for doing so vary greatly depending on the operating system you are using, so consult the operating system's documentation for specific details.
You can find out more about SMB/CIFS auditing and attack utilities at http://www.atstake.com and http://www.nai.com. Examples of these utilities are SMBCapture, SMBRelay, and SMB Grind.
NFS File Sharing
NFS is a file-sharing protocol developed by Sun Microsystems for UNIX-based operating systems. There are versions of NFS for non-UNIX operating systems, such as those from Novell and Microsoft. NFS allows network users to share files and access files shared on other NFS systems. Unfortunately, there are many possible security exploits that can be used to attack systems using NFS. Many users are unaware that they are sharing files over NFS.
To disable NFS file sharing on UNIX-based operating systems, look for the /Etc/Exports file, where NFS shared directories are listed. If you clear out all entries in that file, all sharing is disabled. Further, you can disable the NFS daemon. Steps to disable NFS file sharing in other operating systems vary, so check the software vendor's documentation for specific directions.
File-Trading Programs
There are many file-trading programs available, many of which are used to illegally trade copyrighted software, which is a concern of many organizations. The file-trading programs can also be used to spread Trojan horse software. For example, the file-trading user might think he or she is downloading a screen-saver program for Windows, but instead the software is a virus.
In most cases there is no legitimate use for file-trading programs on organizational networks. Often, such programs increase network utilization and decrease productivity. To protect your organization from exploits that might arise from file-trading programs (in addition to potential liabilities that might come from copyright violations) you should create a policy restricting or prohibiting the use of file-trading utilities. Further, you should remove all unnecessary file-trading programs from the computers in your organization and prevent them from being installed. Many centralized software management systems and individual operating systems allow you to prevent users from installing software.

The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson and then try the question again. Answers to the questions can be found in Appendix A, "Questions and Answers."
-
What are the main security concerns of client/server FTP communications?
-
How can you mitigate the security concerns regarding FTP?
-
What are some of the dangers of using file-trading utilities?
Lesson Summary
-
Standard FTP is not encrypted and consequently authentication and file transfers are not encrypted. This means that anyone with a protocol analyzer could potentially read user names, passwords, and the files transferred over this protocol.
-
To protect your FTP client/server communications from packet sniffing, you can implement Secure FTP or Kerberized FTP, which encrypt FTP communications.
-
File-trading utilities could pose a significant security risk to many organizations. They are often used to transfer copyrighted material from user to user. Further, these utilities can be used to circulate Trojan horse software.
-
The best protection against security issues related to file-trading utilities is to prohibit their use and remove them from all systems on the network.
EAN: 2147483647
Pages: 55
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- A View on Knowledge Management: Utilizing a Balanced Scorecard Methodology for Analyzing Knowledge Metrics
- Measuring ROI in E-Commerce Applications: Analysis to Action
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governance Structures for IT in the Health Care Industry