Lesson 3: Identifying the Components of a Public Key Infrastructure
Lesson 3: Identifying the Components of a Public Key Infrastructure
Using asymmetric key pairs is simple enough to implement, but when scaled beyond a small community using a few applications, it becomes difficult to distribute the public keys and hard to track and manage private keys. When a private key is compromised, it is difficult to locate and remove that key.
The security infrastructure created to solve these problems is known as a public key infrastructure (PKI). PKI uses asymmetric key pairs and combines software, encryption technologies, and services to provide a means of protecting the security of communications and business transactions. RFC 2459 defines the X.509 PKI, which is the PKI defined for use on the Internet. It is comprised of certificates, certification authorities (CAs), certificate management tools, and certificate-enabled applications.

After this lesson, you will be able to
-
Understand what a PKI is
-
Understand what certificates are
-
Understand what a certification authority is
-
Understand how certificates are used
Estimated lesson time: 20 minutes
Components of a PKI
A PKI uses public key encryption technologies to bind public keys to their owners and to help with reliable distribution of keys across multiple heterogeneous networks. Figure 3-3 shows the major components of a PKI.
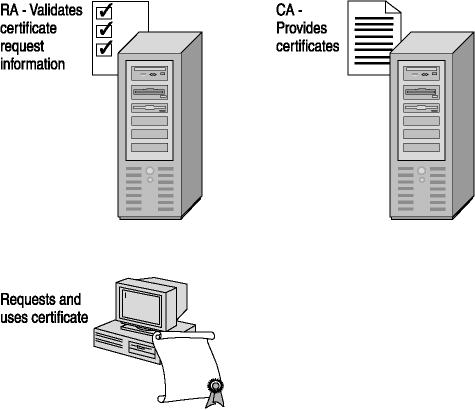
Figure 3-3. Major components of a PKI
The PKI provides a framework of services, technologies, protocols, and standards that enable you to deploy and manage a strong and scalable information security system. With the PKI in place, companies can conduct business electronically and be assured of the following:
-
The person or process sending a transaction is the actual originator.
-
The person or process receiving a transaction is the actual receiver.
-
The integrity of the data has not been compromised.
The basic components that make up a PKI are as follows:
- Digital certificates.
An electronic credential used to authenticate users.
- Certification Authority (CA).
A computer that issues digital certificates, maintains a list of invalid certificates, and maintains a list of invalid CAs.
- Registration authority (RA).
An entity that is designed to verify certificate contents for a CA.
- Key and certification management tools.
Tools for auditing and administering digital certificates.
- Certificate publication point.
A location where certificates are stored and published.
- Public key-enabled applications and services.
Applications and services that support using certificates.
What Are Certificates?
Certificates are a digital representation of information that identifies you and are issued by CAs, which are often a TTP. A TTP is an entity trusted by other entities with respect to security-related services and activities. The certificate (Figure 3-4) includes the TTP, subscriber, subscriber's public key, its operational period, and the digital signature of the TTP issuing it. The TTP is vouching that the person or process with the certificate can be trusted.
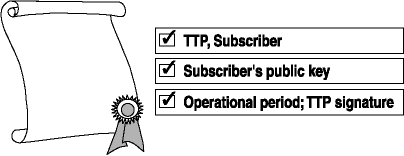
Figure 3-4. Certificate contents
A TTP creates and issues a certificate that is valid for a specific amount of time, much like a credit card, which is issued by a credit card company and is valid for a specific amount of time. Just as a credit card can be canceled at any time, so can a certificate.
Certificates can be used with a variety of applications and security services to provide authentication, data integrity, and security. Uses for certificates include the following:
- Secure mail.
Configure the Secure Multipurpose Internet Mail Extensions (S/MIME) protocol to ensure the integrity, origin, and confidentiality of e mail messages.
- Secure Web communications.
Use certificates with Secure Sockets Layer (SSL) or TLS protocols for authenticating and encrypting communications between servers and clients.
- Secure Web sites.
Use certificates to authenticate access to secure Web sites.
- Custom security solutions.
Use certificates to provide confidentiality, integrity, authentication, and nonrepudiation for custom applications.
- Smart card logon process.
Use certificates to authenticate users with smart card devices attached to their computers.
What Are CAs?
A CA is a computer that is recognized as an authority trusted by one or more users or processes to issue and manage X.509 public key certificates, a revocation list of CAs that are no longer valid, and a revocation list of certificates that have been revoked.
Each CA creates and maintains a list of the certificates that it has issued, as well as a list of certificates that have been revoked. A CA can revoke a certificate for many reasons, for example:
-
When the certificate owner's private key is lost
-
When the owner leaves the company he or she works for
-
When the owner changes names
A CA must also maintain a list of CAs that are no longer valid. A certificate revocation list (CRL) is a signed, time-stamped list of server serial numbers of CA public key certificates that have been revoked. The CRL is necessary to allow CAs to accept and reject certificates that were issued by a different CA.
There are two types of CAs that can be used by a company, a commercial CA, and a private CA:
-
A commercial CA is operated by a certificate-issuing company and provides certificates to the general public, or for use when communicating with other entities.
-
A private CA is used to issue certificates for your company's private use, such as when an employee attempts to gain access to an internal server or gain access remotely.
How It Works
A PKI can be compared to performing credit card transactions remotely. Refer to Figure 3-5 and compare a generic PKI and credit card transaction.
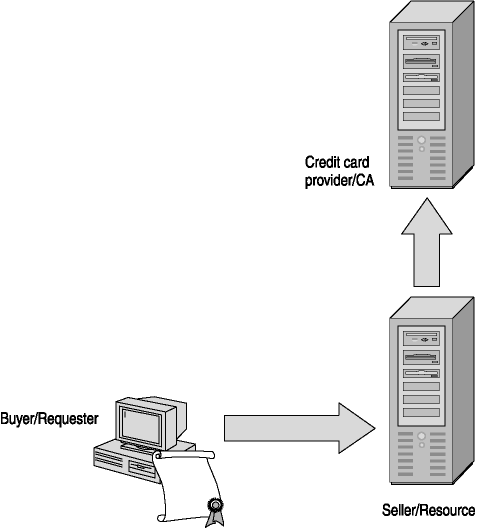
Figure 3-5. Comparing a credit card transaction with a PKI transaction
For comparison, if you order a product over the telephone using a credit card:
-
You provide your credit card information along with information that can prove that you are the actual holder of the card.
-
The seller of the product cannot view your signature and cannot view any additional identification. They trust that because you had the credit card information and proper billing information you are the holder of the card.
-
They send you the product you are purchasing.
If you do not receive the product, you can cancel the transaction. If your credit card information is not correct, the seller does not have to send you the product. Both parties rely on the credit card company as the TTP.
Now, when you make a purchase and use a certificate and PKI for validation:
-
You provide your certificate.
-
The seller of the product still cannot view your signature and cannot view any additional identification. They trust that because you have a valid certificate, you are the owner of the certificate.
-
They send you the product you are purchasing.
This is a simplified version of how PKI is implemented, what the major components do, and the function it provides.

The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson and then try the question again. Answers to the questions can be found in Appendix A, "Questions and Answers."
-
Which best describes a PKI?
-
A digital representation of information that identifies you as a relevant entity by a TTP
-
An entity that is recognized as an authority trusted by one or more users or processes to issue and manage a certificate
-
Uses asymmetric key pairs and combines software, encryption technologies, and services to provide a means of protecting the security of communications and business transactions
-
A list of certificates issued by a CA that are no longer valid
-
-
Which best describes a certificate?
-
A digital representation of information that identifies you as a relevant entity by a TTP
-
An entity that is recognized as an authority trusted by one or more users or processes to issue and manage a certificate
-
Uses asymmetric key pairs and combines software, encryption technologies, and services to provide a means of protecting the security of communications and business transactions
-
A list of certificates issued by a CA that are no longer valid
-
-
Which best describes a CA?
-
A digital representation of information that identifies you as a relevant entity by a TTP
-
An entity that is recognized as an authority trusted by one or more users or processes to issue and manage a certificate
-
Uses asymmetric key pairs and combines software, encryption technologies, and services to provide a means of protecting the security of communications and business transactions
-
A list of certificates issued by a CA that are no longer valid
-
-
What are some reasons a certificate might be placed on a CRL? Select all correct answers.
-
The certificate owner lost the private key.
-
The certificate owner is going on a business trip and wants the certificate expiration refreshed so it does not expire.
-
The certificate owner left the company.
-
The certificate owner changed names.
-
The certificate owner lost the public key.
-
Lesson Summary
-
Using asymmetric keys without a supporting infrastructure is not scalable to a large environment. A public key infrastructure (PKI) uses asymmetric key pairs and combines software, encryption technologies, and services to provide a means of protecting the security of communications and business transactions.
-
A certificate is a digital representation of information that identifies you as a relevant entity by a trusted third party (TTP).
-
A certification authority (CA) is an entity that is recognized as an authority trusted by one or more users or processes to issue and manage certificates.
-
A certificate revocation list (CRL) is a list of certificates issued by a CA that are no longer valid.
EAN: 2147483647
Pages: 55