Lesson 2: Analyzing Security Settings with Security Configuration and Analysis
Before deploying security templates, you need to compare a target computer's current security settings to the desired settings configured in the security template for that class of computer.
After this lesson, you will be able to
- Compare the existing security configuration to the desired baseline configuration stored in a certificate template
Estimated lesson time: 30 minutes
Comparing Security Settings to the Security Template
Once you've created your security template, it's valuable to compare the current security settings of a Windows 2000–based computer to the security template to determine how the current configuration differs from the desired configuration.
This comparison ensures that the template meets all security requirements. If the Security Configuration And Analysis console indicates that the current security matches the tested baseline and there are still security issues, further work is required on the template design.
Comparing current security to desired security helps you identify
- Current security weaknesses on your network. If the security template hasn't been deployed yet, you can identify where the current configuration is weak when compared to the desired baseline security.
- Security template deficiencies. You must perform the testing at a computer separate from the computer where the security template was created. Doing this ensures that any manually configured settings at the computer where the security template was created are identified during the analysis.
- Modified security configuration at the testing station. Because the settings won't match those in the security template, any manually configured security settings are identified during the security analysis.
Performing the Analysis
You use the Security Configuration And Analysis console to analyze a computer's current security settings against a security template. The console indicates whether a Windows 2000–based computer's current security configuration matches the defined configuration in the security template. To perform the analysis, complete the following steps:
- Load the Security Configuration And Analysis console into an MMC console.
- Create a new database locally for storing the imported security template and the analysis data.
- Import the desired security template into the security database.
- Analyze the current security against the security configuration now stored in the security database, as shown in Figure 8.5.
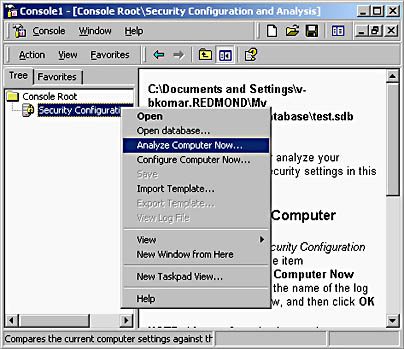
Figure 8.5 Performing an analysis of current security against a security template
- Review the analysis information. The Security Configuration And Analysis console displays whether individual security options match (indicated by a green check mark) or don't match (indicated by a red x) the configured settings in the security template, as shown in Figure 8.6.
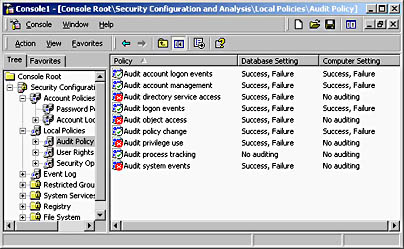
Figure 8.6 Reviewing the analysis of current security against a security template
- Choose either to rework the security template or to apply the security template to the local security configuration.
NOTE
The only time it's recommended to apply the security template at this point is when the computer being analyzed is in a workgroup or non–Windows 2000 network environment. In an Active Directory environment, it's better to import the security template into Group Policy to ensure the security template's continued application.
Automating the Continued Analysis of a Security Template
While the Security Configuration And Analysis console does allow one-time analysis of your computer's configuration compared to a security template, it doesn't allow for long-term analysis. You can perform long-term analysis by using the Secedit command line tool with the /ANALYZE option.
The syntax of the secedit command line is:
SECEDIT /ANALYZE [/DB filename ] [/CFG filename ] [/LOG logpath] [/VERBOSE]where
- /DB filename provides the path to the database file that contains the stored configuration from the desired security template indicated in the /CFG option.
- /CFG filename provides the path to the security template that's imported into the database for analysis. If this option isn't provided, it's assumed that a security template has already been imported in the indicated database.
- /LOG logpath provides the path that's used to log the reports of the analysis.
- /VERBOSE indicates that the log file contains more detailed progress information than regularly recorded.
By creating a batch file that contains your preconfigured Secedit command line, you can use the Scheduled Tasks program in the Control Panel to provide automated analysis of the security configuration of select computers, as shown in Figure 8.7.
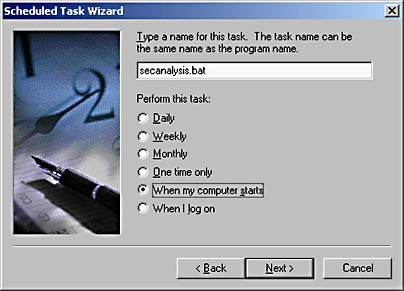
Figure 8.7 Adding the Secedit batch file to Scheduled Tasks
TIP
You can collect the Secedit log files by using Microsoft Systems Management Server (SMS) and then search for the phrase "Mismatch." Mismatch indicates that the current configuration of a computer doesn't match the security template.
Making the Decision
When determining whether a computer matches the security template, include the following in your security design:
- Analyze the security template before deployment. This ensures that the security template contains all required settings.
- Automate continued analysis of security baseline. By using the Secedit command and Schedule Tasks, you can ensure that a computer is regularly compared to the desired security baseline.
- Ensure that the continued analysis logs are collected and analyzed. By using a product such as SMS to collect the analysis logs, you can set regular intervals to search for the Mismatch phrase in the collected log files.
NOTE
A mismatch doesn't indicate weaker security configuration. It only indicates that the current configuration doesn't match the setting in the security template. It's up to you to determine whether the mismatch has strengthened or weakened security. For example, if the template requires a minimum password length of six characters and your DCs are configured to require eight, is this a weakness? No, it's simply a longer minimum password length.
Applying the Decision
Market Florist must ensure that any custom security templates meet security requirements. There are a few ways that Market Florist can accomplish this. The easiest would be to create a test OU structure within the marketflorist.tld domain and apply the security templates to OUs within this structure, as shown in Figure 8.8.
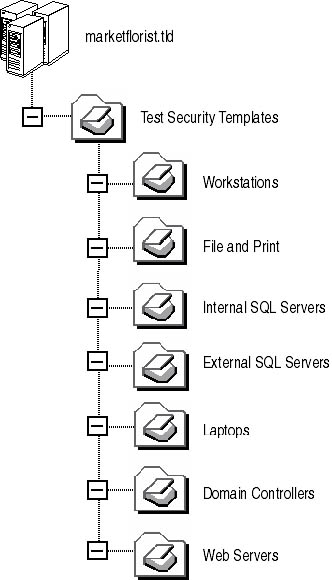
Figure 8.8 Developing an OU structure for testing security templates
To test the application of the Security Templates, you can define a Group Policy object (GPO) at each of the sub-OUs. You can import the security template associated with the sub-OU into the Group Policy object to apply the security template settings. Finally, you can move a computer to the OU to verify the security template settings.
For all of the Windows 2000–based computers, you can accomplish ongoing analysis of the security template application by running a batch file in the computer's startup script that runs Secedit with the /ANALYZE parameter. For example, the startup script for laptop computers could include the following line:
SECEDIT /ANALYZE [/DB Security.sdb ] [/CFG Laptop.inf ] [/LOG c:\Sectemp.log] [/VERBOSE]
Finally, you can use a product such as SMS to collect the c:\Sectemp.log files from each computer. You can examine these log files for the word Mismatch. If you find it, the effective security on the laptop computer doesn't match the security defined in the Laptop.inf security template.
Lesson Summary
Analyzing a Windows 2000–based computer current security configuration against the recommended settings in a security template allows you to determine how well security is configured on the Windows 2000–based computer. Scheduling regular analysis of security configuration will help prevent security weaknesses created by a user of the network modifying security configuration. Ongoing analysis will help in detecting the security configuration change before security weaknesses can be exploited.
EAN: 2147483647
Pages: 172