Lesson 1: Planning Administrative Group Membership
When designing security for your network, you must consider the membership requirements for Windows 2000 administrative groups. Administrators are able to perform tasks that could change your network's security design. You must carefully consider the criteria for membership in these groups (and their component groups) to ensure that security can't be weakened on the network.
After this lesson, you will be able to
- Plan membership within Windows 2000 administrative groups and identify when to create custom administrative groups
Estimated lesson time: 30 minutes
Designing Default Administrative Group Membership
Windows 2000 contains several predefined administrative groups. When designing security for your Windows 2000 network, you must determine appropriate membership in each group. By understanding the capabilities of each group and assigning the correct memberships, you can ensure that users aren't assigned excess privileges on the Windows 2000 network.
The Default Windows 2000 Administrative Groups
Several default groups exist within Active Directory and are assigned rights on the network. Understanding the rights each group is assigned can assist you in determining the appropriate administrative group memberships within your Active Directory.
Table 4.2 identifies the default administrative groups that exist in a Windows 2000 network.
Table 4.2 The Default Windows 2000 Administrative Groups
| Group Name | Group Type | Purpose |
|---|---|---|
| Enterprise Admins | Universal | Exists only within the forest root domain. Has forest-wide administrative scope. Members of this group are allowed to modify Enterprise-wide configuration. Membership must be monitored at all times. |
| Schema Admins | Universal | Exists only within the forest root domain. Members can make changes to the forest schema, including the modification of existing attributes and classes or the addition of new attributes or classes. |
| Domain Admins | Global | A member of the Administrators group within each domain of the forest. When a member server or workstation joins the domain, the Domain Admins group is added as a member of the local Administrators group. Members can administer the domain in which they are defined. Additionally, members of the Domain Admins group in the forest root domain are permitted to modify membership of the Enterprise Admins or Schema Admins groups as they exist in the forest root domain. |
| Group Policy Creator Owners | Global | Members are allowed to create new Group Policy objects in Active Directory. |
| Administrators | Domain Local | Members are allowed to fully manage the domain in which the group exists, including management of services and accounts within Active Directory. |
| Power Users | Local Group | Exists only on nondomain controllers. Members are allowed to manage users and groups in the local SAM database, modify or delete accounts that they created, and manage membership in the Users, Guests, and Power Users groups. Power Users also can install most applications; create, manage, and delete local printers; and create and delete file shares. |
| Account Operators | Domain Local | Members of this group can create, modify, or delete accounts for users, groups, and computers in any container within the domain where the Account Operators group exists. The only exceptions are the Builtin container and the Domain Controllers OU. The only groups that Account Operators are prohibited from managing are the Administrators and Domain Admins groups. In the forest root domain, members can't modify the properties of the Enterprise Admins or Schema Admins groups. |
| Server Operators | Domain Local | Members are allowed to log on locally at a server, manage network shares, stop and start services, back up and restore data, format hard disk drives, and shut down the computer. |
| Print Operators | Domain Local | Members can manage printers and printer queues, including managing print jobs that weren't submitted by the member. |
| Backup Operators | Local | Members are allowed to back up and restore all files on the computer. Members aren't subject to permissions on files when performing the backup. Members also can log on locally and shut down the computer. |
| Replicators | Domain Local | In Windows NT domains, it's a built-in group used by the File Replication service on DCs. |
| DHCP Administrators | Domain Local | Members can administer DHCP services within the domain where the group exists. This group is created automatically when the DHCP service is installed. |
| DNS Admins | Domain Local | Members can administer DNS services in the domain where the group is defined. This group has members in any domain where the DNS service is installed. |
| WINS Admins | Domain Local | Members can administer the Windows Internet Naming Service (WINS) service within the domain where the group is defined. This group is not created automatically when the WINS service is installed in a domain. |
| DNSUpdate Proxy | Global | Members can create DNS resource records without taking ownership of the DNS resource records. Generally, DHCP servers are made members of this group to ensure that a client workstation using Windows 95, Windows 98, or Windows NT can take ownership of the resource record after the computers are upgraded to Windows 2000. |
| Pre–Windows 2000 Compatible Access | Domain Local | Members can query Active Directory using a NULL session. During the DCPROMO process, which installs and configures Active Directory to promote a server to a DC, if the option to enable pre–Windows 2000 compatible access for remote access is enabled, the Everyone group is added as a member to this group. |
NOTE
Unless otherwise noted, Windows NT refers to versions 3.51 and 4.0.
Assessing Administrative Group Membership Design
Poor administrative group design can hurt your network security. If you don't control administrative group membership, your network security can be severely compromised.
In a Windows 2000 network you can use two common strategies to control the membership of Windows 2000 administrative groups. The two methods are
- Periodically audit the membership of administrative group membership
- Implement restricted groups in Group Policy to control membership in administrative groups
Auditing Group Membership
You can use Windows 2000 auditing and periodic manual audits to ensure that group membership is as it should be in your Windows 2000 network. Your network must determine which groups must be periodically audited.
The audit must ensure that both users directly configured as members of the administrative group and the membership of any composite groups are verified against documented membership. You can do this either by performing regularly scheduled manual inspection of the administrative groups or by using third-party products that report group memberships to precustomized reports.
Using Third-Party Tools to Determine Group Membership
You can use several alternatives to report on group memberships in a Windows 2000 network. Common methods used in the industry include the following:
- SomarSoft's Dumpevt. The Dumpevt utility (formerly known as DumpACL) is commonly used to report on the configured discretionary access control lists (DACLs) that are defined for file and share resources. In addition, this software reports on group memberships for all groups within Active Directory. You can download this utility for free at http://www.somarsoft.com/.
- Windows Scripting Host. You can use the Windows Scripting Host (WSH) to generate scripts that report on group membership. Many example scripts are available at cwashington.netreach.net/.
Whatever method you choose, ensuring that the reports are run at regular intervals and are examined to verify that no anomalies exist in the administrative group memberships will prevent excess rights from being applied to unauthorized user accounts.
You must determine which group meets your needs. Consider that the Account Operators and Server Operators are assigned only a subset of the privileges of the Administrators group. If a user is only required to perform user and group management, then assign her membership only in Account Operators.
Using Restricted Groups to Maintain Group Memberships
If you want to limit membership within a specific group, you can use the Restricted Groups option within Group Policy to predefine membership within the groups. This Group Policy ensures that membership matches the defined membership. If members are added or deleted, the Group Policy will ensure that the desired membership is reestablished.
You can apply Restricted Groups policy at the site, domain, or OU level. When applied, the Restricted Groups policy setting provides two forms of protection for a defined group, as shown in Figure 4.2.
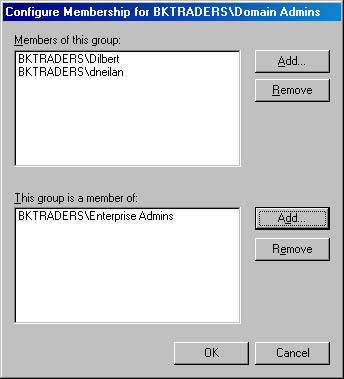
Figure 4.2 Defining both the membership within the group and the groups that the group can be a member of for a restricted group
- It protects membership in the group. Within restricted groups, you can define which accounts can be members of the group. If the membership is changed, the next time that Group Policy is applied it will modify the membership to match the membership defined in the policy.
NOTE
Group Policy will be automatically applied to DCs every 5 minutes. Windows 2000 Professional workstations and Windows 2000 member servers that are members of the domain will apply the computer policies every 90 minutes by default. You can force the application of the security policy by running the following command from the command prompt at the target workstation: SECEDIT/REFRESHPOLICY MACHINE_POLICY/ENFORCE. - It limits groups that the restricted group can be a member of. In addition to protecting the membership within the restricted group, you can also configure what groups the restricted group can be a member of. This prevents security from being modified by adding the restricted group to an administrative group that isn't desired.
Making the Decision
When making your decision on administrative group design, you must do the following:
- Determine exactly who must be a member of each administrative group. By predetermining group membership and documenting the proposed membership, you can use this documentation to periodically audit the group membership. By having the membership documented, you can ensure that membership hasn't been modified.
- Don't grant membership to a group that provides excess privileges. When making your administrative group membership decisions, always determine exactly what rights the member will require. Don't make the user account a member of a group that provides excess privileges. For example, if you wish the user account to be able to modify the properties of all nonadministrative groups, either use delegation of administration to OUs where the user accounts exist or make the user a member of the Account Operators group. Don't make the user a member of the Administrators or Domain Admins security groups. Membership in these groups would allow the user to perform the desired tasks but would also grant the user rights on the network that are beyond the desired rights.
- Use restricted groups to ensure that only approved membership is maintained. Restricted groups ensure that membership is maintained to match your desired memberships. Be sure to document all desired memberships and to require that the restricted group membership definition be modified if the desired membership changes.
- Ensure that membership is audited for these groups. You should periodically audit all administrative group membership, either manually or with automated reporting utilities. Whatever method you select, the audit should occur at regularly scheduled intervals.
- Watch membership in the forest root domain's Domain Admins group. Within a forest, the Domain Admins group in the forest root domain is able to modify the membership of the Enterprise Admins and Schema Admins groups. Due to the forest-wide implications, you must carefully monitor membership in these groups to ensure that only authorized memberships exist.
Applying the Decision
The decisions that Hanson Brothers faces include determining membership in the administrative groups for the Central IT team and ensuring that membership is guarded and audited for enterprise-level administrative groups.
Based on the role definitions provided in the chapter scenario, you must define the administrative group membership for Hanson Brothers, shown in Table 4.3.
Table 4.3 Administrative Group Memberships for Hanson Brothers
| Group | Membership |
|---|---|
| Enterprise Admins | Only the default administration account. The account must be restricted further to be used at only specific locations on the network. |
| DNSAdmins | Derek Graham |
| DHCP Administrators | Derek Graham |
| Account Operators | Steve Masters |
| Schema Admins | Yvonne Schleger |
| Server Operators | Eric Miller |
| Group Policy Creator Owners | Stephanie Conroy |
Note that in the table no members are assigned to the Backup Operators group. This is because Hanson Brothers requires that the Backup and Restore privileges be divided between Stephanie Conroy and Kim Hightower. Membership in the Backup Operators group would be an excess assignment of user rights.
The other requirement you must manage is the membership of the Domain Admins, Enterprise Admins, Schema Admins, and Administrators groups. You can manage these groups by
- Defining restricted groups in Group Policy
- Auditing success and failure events for account management
- Auditing membership in these groups at regular intervals
For restricted groups, you can set the properties for Hanson Brothers as shown in Table 4.4 to ensure that group membership isn't changed from the desired membership. To ensure that the group memberships are maintained on the domain, the Restricted Groups policy must be deployed at the Domain Controllers OU for Hanson Brothers.
Table 4.4 Restricted Group Definitions for Hanson Brothers
| Group | Members | Member of |
|---|---|---|
| Domain Admins | Administrator | Administrators Enterprise Admins |
| Enterprise Admins | Administrator | None |
| Schema Admins | Administrator Yvonne Schleger | None |
| Administrators | Domain Admins Enterprise Admins Administrators | None |
Designing Custom Administrative Groups
Sometimes you will require a group to have only a subset of the rights that an administrative group is assigned. For example, your security policy may require that the backup and restore privileges are separated. In Windows 2000 the Backup Operators group provides both privileges.
By creating two custom groups and assigning one group the right to back up files and the other group to restore files, as illustrated in Figure 4.3, you can reduce the risk associated with a single user account having the rights to back up and restore files from the network.
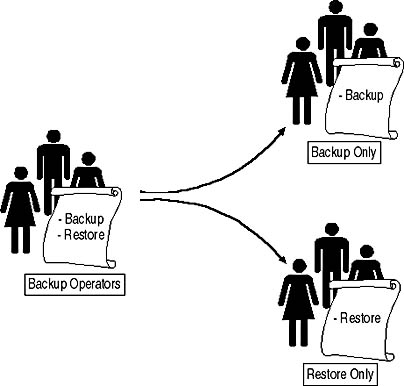
Figure 4.3 Splitting backup rights between a custom Backup and custom Restore group
NOTE
The main concern that network administrators have with the mixing of the rights to back up and restore files is that an account with the right to back up files can back up all files on the network. This includes files that the account may not have access to on the network.
Determining When to Create Custom Groups
The key to creating custom administrative groups is to determine exactly which rights a specific account requires. One group that has a large number of rights on a network is the Enterprise Admins universal group in the forest root domain. An organization will often create custom groups to delegate only specific rights to an account, rather than make the account a member of the Enterprise Admins group and provide the account with excess privileges.
To carry this example further, membership in the Enterprise Admins group is required to perform the following security tasks in a Windows 2000 forest:
- Create new domains and new DCs in the forest. Whenever a new domain or DC is added to an existing forest, a member of the Enterprise Admins group (or at least their credentials) must normally be provided to execute the Dcpromo process. By using Ntdsutil to create the necessary cross-reference and server objects in Active Directory in advance, a member of the Enterprise Admins group can allow users who aren't members to perform the actual Dcpromo process.
NOTE
The Enterprise Admins must create the domains and servers in advance by using the domain management set of commands in Ntdsutil. Within this menu, they can create the domain cross-reference object by using the following command: PRECREATE %1 %2, where %1 is the name of the domain to create and %2 is the name of the DC that will be added to the domain. - Authorize Remote Installation Services (RIS) and DHCP servers in Active Directory. To authorize a RIS server in Active Directory, you must log on with an account that's a member of the Enterprise Admins group in the forest where you want the RIS server to be authorized. By default, members of the Enterprise Admins group are the only users who can authorize DHCP/RIS servers. Before a RIS server can accept requests, you must authorize it to run. To authorize a RIS server in Active Directory, you must log on with an account that's a member of the Enterprise Admins group in the forest where you want the RIS server to be authorized. By default, members of the Enterprise Admins group are the only users who can authorize DHCP/RIS servers by default. This right can be delegated in Active Directory.
- Install Enterprise Certification Authorities. Only members of the Enterprise Administrators group are allowed to create Enterprise Certification Authorities. This is because the creation of an Enterprise CA requires that the account performing the installation be able to create objects in the CN=Public Key Services, CN=Service, CN=Configuration subtree. This right can't be delegated to other users or groups in Active Directory.
- Manage sites and subnets. By default, only Enterprise Administrators are allowed to create new site or subnet objects to design replication for your Windows 2000 network. This right can be delegated by delegating the right to create new objects in the CN=Sites, CN=Configuration subtree.
Making the Decision
You should base your decision on whether to create custom security groups for the purpose of administration in your Active Directory on the following guidelines:
- Determine that an existing administrative security group doesn't meet your security requirements. This can be one of two scenarios. Either the existing security groups don't offer sufficient rights for the tasks that are required or the existing groups offer excess rights. The assignment of excess rights is considered a weakness in security.
- Determine which rights are required by the custom administrative groups. By testing and iteration, you must determine what areas of Active Directory, the NT file system (NTFS), and possibly the registry keys that the custom administrative group will require elevated privileges to access. By determining these rights, you ensure that excess privileges aren't assigned.
- Determine if the necessary administrative rights can be delegated. If administrative delegation is supported, you can develop your OU design to facilitate delegation of administration either to all objects, only specific objects, or only for specific attributes.
- Determine which objects are accessed by the permissions. This will help you to set the DACL on these objects to permit the newly created group to access the object with the necessary permissions.
- Create a domain local group that will be assigned the determined permissions and rights. By creating a group that will be assigned the desired rights and permissions, you can test the designed permissions and rights by creating a user account that's a member only of the newly created domain local group. This way, other group memberships don't affect the testing of rights and permission assignments.
Applying the Decision
Hanson Brothers must create custom administration groups to meet the following requirements outlined in this chapter's case scenario:
- Help desk personnel. You must create a custom domain local group that contains all the staff that work at the help desk. This custom group can then be given the ability to reset passwords and clear the account lockout attribute for all user accounts. You do this by performing the delegation at the hansonbrothers.tld domain.
- Human Resources. You must also create a custom domain local group for members of the Human Resources department. At the hansonbrothers.tld domain, this group must be given the ability to modify all Human Resources-related attributes, such as address and home phone number.
- BoiseAdmins and CalgaryAdmins. You must create a custom domain local group for administrators at each office, and then give these custom groups the ability to manage both user and computer objects, as shown in Figure 4.4.
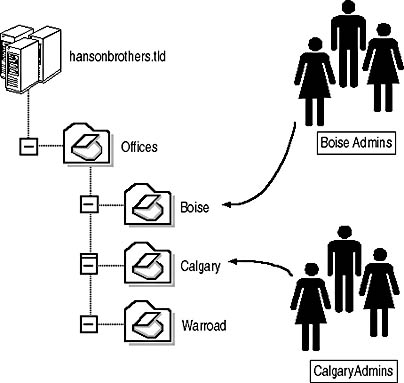
Figure 4.4 OU structure necessary to delegate administration to the remote offices
- BackupsAdmins. This domain local group would be assigned the user right to Backup Files And Directories, as illustrated in Figure 4.5. If Stephanie Conroy is required to back up only Domain Controllers, then this user right must be applied at the Domain Controllers OU. If the requirement is to back up all Windows 2000–based computers, then this user right must be assigned at both the Domain Controllers OU in the Default Domain Controller Group Policy object and at the Domain in the Default Domain Group Policy object.
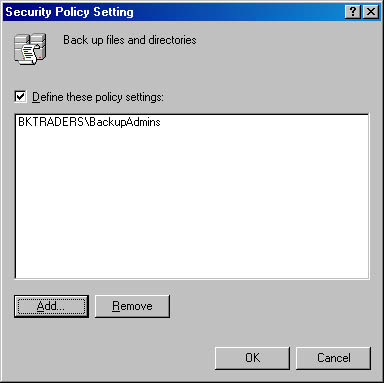
Figure 4.5 Assigning a Custom Local group the Backup Files And Directories right
- RestoreAdmins.This domain local group would be assigned the user right to Restore Files And Directories. Assuming that Kim Hightower would have to restore backup data to any Windows 2000–based computer in the network, this user right must be assigned at both the Domain and the Domain Controllers OU.
Lesson Summary
When designing the administrative group structure for your forest, you must make sure that membership is designed not to grant excess rights on the network. You do this by only assigning security principals to an administrative group that provides the required rights on the network. Don't just add the security principal to the Administrator or Domain Admins group because it "works."
By using the restricted groups in Group Policy and performing regular audits of administrative groups, you can verify that only authorized users are members of administrative groups.
EAN: 2147483647
Pages: 172