Lesson 2: Securing Authentication in a Heterogeneous Network
When designing access to Windows 2000 networks by heterogeneous, or non-Microsoft clients, you must ensure the integrity of the authentication process. Authentication associates users with a security principal within Active Directory. The credentials provided by the user authenticate the user with the network. Once the user is authenticated, authorization can take place to limit access to specific authorized resources.
After this lesson, you will be able to
- Design secure authentication for Macintosh, Novell, and UNIX clients
Estimated lesson time: 30 minutes
Securing Authentication for Macintosh Clients
File Services for Macintosh supports users authenticating with Active Directory from Macintosh client computers. File Services for Macintosh requires that Macintosh clients authenticate using accounts stored in Active Directory.
When authenticating with the Windows 2000 network, Macintosh users can use any of the following authentication methods:
- No authentication. If guest access is enabled on the Windows 2000 Server, a Macintosh user can connect using the Guest account. Using the Guest account allows the user to connect without providing a password for authentication.
- Apple Clear Text. Passwords are passed in clear text from the Macintosh client to the Windows 2000 Server. Clear text authentication is available for Macintosh users who use the standard Apple Share client software or System 7 File Sharing.
- Apple Standard Encryption. Passwords up to eight characters are enabled. The encrypted password isn't transmitted on the network. Instead, a hash algorithm is executed against a random number using the user's password. At the server, the same password is used to perform the hash algorithm and the results are compared.
NOTE
This process requires the password to be stored in reversibly encrypted format at the server. - Microsoft User Authentication Module (MS-UAM). Allows encrypted passwords up to 14 characters in length. MS-UAM also requires reversibly encrypted format. MS-UAM requires the MS-UAM to be installed at each Macintosh client to support the stronger encryption of authentication credentials.
NOTE
If your Windows 2000 network has multiple domains, the user should provide his account in the format domain\username, where domain denotes the domain where the user's account is located, to ensure that the logon request is forwarded to the correct domain. Not providing the domain prefix can lead to different results if the same username exists in multiple domains.
To maintain a minimum security level in your network, configure the File Server for Macintosh properties to limit authentication to specific methods. For example, you could limit authentication to MS-UAM.
You can also configure Macintosh-accessible volumes with a volume password that forces Macintosh users to provide the associated password before accessing the volume.
Making the Decision
Use Table 16.2 when authenticating Macintosh clients in a Windows 2000 network.
Table 16.2 Securing Macintosh User Authentication
| To | Include the Following in Your Security Plan |
|---|---|
| Allow unauthenticated access to Macintosh users | Enable the Guest account at the server hosting File Services for Macintosh. Enable Guest access for the Macintosh-accessible volume. Have Macintosh users connect to the volume as a guest. |
| Allow all Macintosh clients to connect to the Windows 2000 server | Enable File Server for Macintosh to access Apple Clear Text authentication or enable Apple Clear Text or Microsoft authentication. |
| Require encrypted authentication | Configure all user accounts for Macintosh users to store passwords in reversible encrypted format. Configure File Server for Macintosh properties to require Apple Encrypted authentication or Microsoft authentication. |
| Restrict supported authentication methods | Configure File Server for Macintosh properties to accept only authentication requests using authorized methods. |
| Limit access to a volume | Create a volume password that must be provided in addition to user credentials to gain access to a volume. |
Applying the Decision
Blue Yonder Airlines requires that Macintosh user authentication not allow interception of user passwords. To enforce this, configure File Services for Macintosh to only allow Apple Standard Encryption or the MS-UAM, as shown in Figure 16.1.
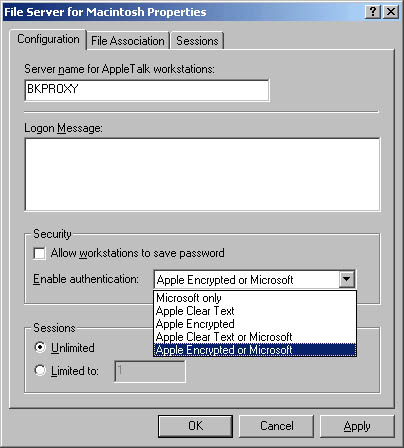
Figure 16.1 Configuring File Server for Macintosh to require encrypted authentication
The MS-UAM provides support for 14-character passwords but requires the installation of the MS-UAM at each Macintosh computer. Because all Macintosh computers are located in the same department, this shouldn't be difficult.
Securing Authentication for Novell Clients
A Windows 2000 Server running FPNW emulates a NetWare 3.x server and allows NetWare clients to authenticate with the Windows 2000 server. NetWare clients can access file and print services hosted by the Windows 2000 server using native NetWare commands and utilities.
NOTE
FPNW requires that the NetWare clients connect to the FPNW server using IPX/SPX protocols. Configure the FPNW server to use the same frame type and internal network number to ensure connectivity by NetWare clients. Failure to do so can result in the FPNW server being unavailable to NetWare clients.
To allow users to authenticate with Active Directory by using a NetWare client, configure user accounts as NetWare-enabled accounts in Active Directory Users And Computers. A NetWare-enabled account allows you to define NetWare-specific properties, such as the NetWare logon script for the user. You can limit which user accounts can authenticate using NetWare clients by enabling only the required accounts to Maintain NetWare Compatible Login in Active Directory Users And Computers. By configuring the Concurrent Connections option for a user account, you can also limit the number of sessions that a NetWare client can establish.
Making the Decision
Table 16.3 lists the design decisions you need to make when securing NetWare client authentication with a Windows 2000 network.
Table 16.3 Securing NetWare User Authentication
| To | Do the Following |
|---|---|
| Allow NetWare clients to authenticate with a Windows 2000 Server | Install FPNW on a Windows 2000 server. Enable each required user account to maintain NetWare compatible login Install the IPX/SPX Compatible transport on the Windows 2000 server running FPNW. |
| Limit the number of simultaneous connections by a single user account | Limit the number of concurrent connections in the NW Compatible tab of the Properties dialog box of a user account. |
| Allow authentication by Windows for Workgroups 3.11,Windows 95, Windows 98, or Windows NT client computers | Windows for Workgroups 3.11, Windows 95, Windows 98, and Windows NT clients allow the installation of multiple network clients. Rather than install FPNW, consider deploying the Microsoft and NetWare clients to all client computers. |
Applying the Decision
Blue Yonder Airlines must install FPNW on the BYDATA server to allow NetWare clients to connect to the file server using native NetWare clients. Before installing FPNW, Blue Yonder Airlines should determine what operating systems are in use for the client computers at the Consolidated Messenger office. If the client computers are running Windows 95 or later, consider installing both Microsoft and NetWare clients on the computers. This would allow file access and authentication to both the Windows 2000 and NetWare networks. You could remove the NetWare client software once the NetWare server data is migrated to Windows 2000.
Securing Authentication for UNIX Clients
UNIX clients can use several methods to authenticate with a Windows 2000 network. The choice will depend primarily on the application that's used to access data on the Windows 2000 server.
- Clear text. Several Windows Sockets (WinSock) applications use clear text authentication when authenticating with a Windows 2000 domain controller. Among the common applications, Telnet, Post Office Protocol version 3 (POP3), File Transfer Protocol (FTP), and Internet Mail Access Protocol version 4 (IMAP4) all use clear text authentication. The risk of using clear text authentication must be weighed against the needs for using these WinSock applications.
NOTE
These applications can use either Secure Socket Layers (SSL) or Internet Protocol Security (IPSec) to encrypt transmissions between the client and the server and protect clear text authentication. - Network Information Service (NIS). Used to authenticate UNIX clients with NFS servers. NIS allows user logon information and group information to be centrally acquired from the NIS database. Windows 2000 can host the NIS database in Active Directory when Services for UNIX 2.0 is installed on the Windows 2000 server. The NIS service maps the provided UID and Group Identifier (GID) to a corresponding user account in Active Directory.
- NT LAN Manager (NTLM). Samba, a NetBIOS server for UNIX workstations, allows file access using Server Message Blocks (SMBs). If the UNIX clients are running Samba version 2.0.6 and later, NTLM authentication can be used for authenticating the user accounts. Samba versions earlier than version 2.0.6 use clear text authentication.
WARNING
To allow access to UNIX Samba servers, you must configure Group Policy to enable the Send Unencrypted Password To Connect To Third-Party SMB Servers setting. You have to carefully consider implementing this setting because it results in passwords being passed on the network in clear text format. - Kerberos. Used to authenticate UNIX users by using accounts in Active Directory. To use Kerberos, you must either configure the UNIX clients to use Active Directory domain controllers as their Kerberos Key Distribution Center (KDC) or implement inter-realm trust relationships between the Kerberos realm and the Windows 2000 domain. Both methods require you to create an account in Active Directory and map the account to its related UID.
Making the Decision
When you design secure authentication for UNIX clients, you should include the following in your security plan:
- Identify the applications that UNIX clients will use for accessing resources on the Windows 2000 network. Each application will have a specific form of required authentication. By identifying the supported applications, you can define what forms of authentication to provide on the network.
- Design an authentication infrastructure to support the deployed applications. The infrastructure you design will vary based on the required authentication mechanisms.
- For Kerberos authentication, determine whether the UNIX clients will authenticate with a Windows 2000 domain controller or use inter-realm trusts to allow integration of the Kerberos realms with the Windows 2000 domain structure.
- For NIS access, determine whether a UNIX NIS server or Server for NIS will provide NIS authentication services.
- For Samba access, determine what version of Samba is used by UNIX clients. UNIX clients running versions 2.0.6 or higher can use NTLM for authentication, while older clients require Group Policy to be modified to allow unencrypted password authentication.
- For WinSock application access, determine whether the applications support SSL encryption for authentication. If they do, ensure that the server hosting the server-side application is configured to support SSL. For example, to use SSL to encrypt POP3 authentication, the mail server must acquire a server-side certificate. If SSL isn t supported, consider using IPSec to encrypt all data transmitted between the WinSock client application and the server-side WinSock application.
- Create accounts in Active Directory where necessary. Kerberos authentication and NIS authentication associate UNIX UIDs with Active Directory user accounts. When credentials are provided by a UNIX user, account mapping determines what Active Directory account to use when accessing resources stored on a Windows 2000–based server.
Applying the Decision
Blue Yonder Airlines must use NIS authentication to provide NFS access to UNIX users connecting to the BYDATA server. The NFS Server software requires you to configure Active Directory to act as an NIS server by using Server for NIS. You can import the existing NIS source files from the UNIX NIS servers by using the NIS To Active Directory Migration Wizard. Finally, configure User Name Mapping so that the UID provided by a UNIX client when accessing the resources on the BYDATA server is translated to a Windows 2000 security principal. Use Two-Way Password Synchronization to synchronize the passwords used for UNIX and Windows 2000 so that users won't have to reenter credentials.
Blue Yonder Airlines must establish a Kerberos inter-realm trust between the blueyonder.tld domain and the UNIX Kerberos realm to allow Active Directory users to authenticate with the UNIX database. Only an inter-realm trust allows the UNIX KDC to recognize user credentials from Active Directory.
Lesson Summary
Until a non-Microsoft user authenticates with the Windows 2000 network, there's no way to apply the Windows 2000 security model to the heterogeneous client sessions. You must ensure that your design doesn't weaken Windows 2000 security by allowing heterogeneous clients to authenticate using clear text. By using Windows 2000 add-on services, you can ensure that authentication is encrypted to protect the Windows 2000 user credentials.
EAN: 2147483647
Pages: 172