Lesson 1: Identifying Common Firewall Strategies
A common way of providing security for the extranet is to deploy firewalls between the public network and the extranet. Being aware of common firewall features will help you design secure access to the resources in your extranet.
In addition to deploying a firewall between the public network and the extranet, many organizations deploy a firewall between the private network and the extranet. This configuration is commonly referred to as a Demilitarized Zone (DMZ), perimeter network, or screened subnet. This internal firewall ensures protection of the private network if the external firewall or resources in the extranet are compromised.
After this lesson, you will be able to
- Design a network infrastructure to secure your organization's extranet
- Identify the firewall features that you can use to protect the resources exposed in the extranet
Estimated lesson time: 45 minutes
Identifying Firewall Features to Protect the Extranet
In the simplest deployment, a firewall is placed between the private and public networks to secure the private network from the public network. This configuration is shown in Figure 14.1.
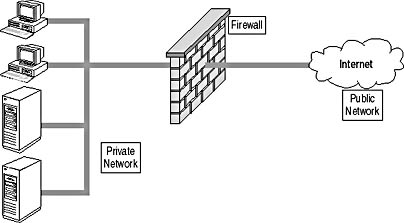
Figure 14.1 A firewall restricting public network access to the private network
A firewall acts as a barrier against attacks launched from the public network. A firewall can be a physical hardware device or a software application that executes on a computer.
To protect the private network, firewalls can offer a suite of services, including
- Network Address Translation (NAT). Translation of the source address of all outbound packets from a private network address to a public network address.
- Packet filtering. Configuration of rules at a firewall that define which protocols are allowed to pass through the firewall.
- Static address mapping. Configuration of how incoming packets are rerouted to servers using private network addressing.
- Stateful inspection of network traffic. Verification that protocols are following basic rules of communications. Stateful inspection ensures that sessions aren't hijacked by an attacker.
- Advanced features that detect common attacks against the private network. These include setting time-outs for incomplete session establishment and inspecting the content of incoming packets.
The following sections describe how these services function and the security threats they address.
Protecting Private Network Addressing with NAT
NAT prevents exposure of the IP addressing scheme used on your private network. An attacker with knowledge of the IP addressing scheme can attempt an IP spoofing attack by sending packets to the network with the falsified IP source address of a trusted private network address.
NAT protects against this form of attack by replacing the source IP address in all outgoing packets with a common IP address, as shown in Figure 14.2.
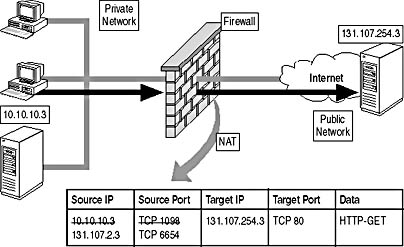
Figure 14.2 How NAT replaces the source IP address and source port fields for all outgoing packets
In addition to replacing the source IP address, NAT replaces the source port to prevent duplicate port requests by outgoing packets. The NAT device tracks all managed connections so that return packets are returned to the correct computer on the private network.
The private network commonly uses Request for Comment (RFC) 1918 addressing. RFC 1918 reserves three ranges of IP addresses for private network addressing:
- 10.0.0.0 – 10.255.255.255 (10.0.0.0/8)
- 172.16.0.0 – 172.31.255.255 (172.16.0.0/12)
- 192.168.0.0 – 192.168.255.255 (192.168.0.0/16)
These pools of IP addresses aren't used on the Internet and aren't included in Internet routing tables. The NAT process replaces the private network addresses with an IP address assigned to the organization by the Internet Corporation for Assigned Names and Numbers (ICANN).
NOTE
Windows 2000 provides a native NAT service in RRAS.
Packet Filters
Once you've deployed a firewall, you must establish firewall rules to define what data is allowed to enter and exit the private network. Firewall rules are made up of individual packet filters. A firewall uses a packet filter to profile a protocol so that data transmitted using the protocol is identified. Packet filters allow a firewall administrator to prevent unauthorized protocols from entering the private network. Alternatively, administrators can apply packet filters to outbound data to restrict which protocols are available to private network computers.
A packet filter is typically composed of fields that profile a protocol and identify what action to take if the protocol attempts to pass through the firewall. The fields used by packet filters include
- Source address. The individual IP address or network IP address from which the data originates.
- Source port. The port from which the data is transmitted. Every IP-based protocol originates from a port at the source host. The source port for a client computer connection is often a random port.
- Destination address. The individual IP address or network IP address to which the data is sent.
- Destination port. The port that the server uses to listen for connections. IP-based services and applications listen for connections on a predefined port.
TIP
To determine what ports are used by specific services and applications, view the Services text file in the systemroot\system32\drivers\etc folder, where systemroot denotes the folder where Windows 2000 is installed. To view a listing of all well-known port numbers, go to www.isi.edu/in-notes/iana/assignments/port-numbers.
- Protocol. Application and Services use a specific protocol ID or a transport layer protocol for transporting application data. If the application or service uses a transport layer protocol, it will be either Transport Control Protocol (TCP) or UDP.
- Action. Defines what action to take if the other fields are matched and the data transmission is identified. Options include Allow or Deny. In addition, many firewalls also allow logging to identify any attempts to use the protocol.
Many firewalls include an option to mirror all packet filters. Mirroring is necessary to allow response packets to return to the source client computer. Mirroring simply switches the source and destination information to allow the response packets to cross the firewall, as shown in Figure 14.3.
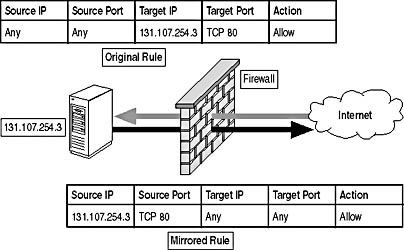
Figure 14.3 How mirroring switches the source and destination information within an IP packet
Typically, you will implement one of the following firewall strategies at your firewall:
- Specify allowed protocols and prohibit everything else
- Specify prohibited protocols and allow everything else
The strategy you choose will be based on your organization's risk level. Typically, higher security networks specify the allowed protocols and prohibit everything else. This ensures that only authorized protocols are allowed to pass through the firewall.
Static Address Mapping
Use static address mapping at a firewall to redirect incoming traffic to Internet-accessible resources hidden behind the firewall. The resources are advertised on the Internet with publicly accessible IP addresses. When the firewall receives the packets, the firewall translates the destination address to the true IP address of the resource behind the firewall and redirects the data to the resource, as shown in Figure 14.4.
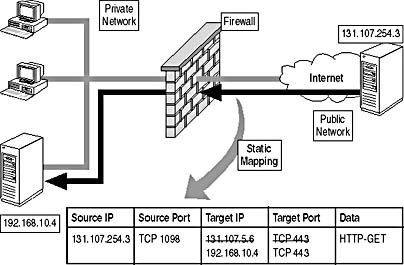
Figure 14.4 How static address mapping redirects requests to internet-accessible resources on the private network
In the figure the external DNS advertises the Web server as the IP address 131.107.5.6. Static address mapping translates the external IP address to 192.168.10.4 on the private network.
The advantage of using static address mapping is that it conceals the true IP address of Internet-accessible resources from potential attackers. Combined with packet filtering rules, static address mapping allows you to define authorized protocols and redirect the protocols to servers located in a DMZ.
Stateful Inspection
In higher-security networks, simple packet filters may not provide enough security. Packet filters define which ports are left open at the firewall to redirect network traffic to Internet-accessible resources. Many protocols utilize random ports above port 1024 at the client computer side. Opening up all ports above 1024 can leave both the firewall and the private network resources susceptible to attack. Stateful inspection allows the firewall to inspect which ports are used for an initial connection, open those ports, and then close the ports when the connection is terminated. If any suspect ports are requested, such as when a session hijack attempt takes place, the firewall can recognize the attack and drop the connection.
Stateful inspection allows firewall rules to be established so that UDP-based protocols such as Simple Network Management Protocol (SNMP) can pass through firewalls successfully. The firewall tracks client and server port information and allows only response packets to a valid host to pass through the firewall. The firewall does this by tracking the original ports used by a client application and ensuring that the server-side application only sends responses to the port used by the client application.
Advanced Techniques
In addition to these services, firewalls provide advanced security through the following features:
- Configuring time-out tolerance. Some attacks attempt to lock up the firewall by flooding it with incomplete TCP sessions. The time-out tolerance allows the firewall to disconnect these sessions before the synchronize (SYN) queue overflows.
NOTE
This attack is commonly known as a SYN flood attack. By flooding the firewall with SYN packets, the attacker can prevent further connections from being established. - Content scanning. Although packet filtering can restrict protocols, it can't inspect commands within a protocol. Content scanning allows the firewall to inspect the commands transmitted within a session. For example, you may want to disable the ability to upload data by using FTP. You can configure content scanning to allow FTP GET commands while preventing FTP PUT commands. Content scanning can also scan all incoming content for known virus signatures.
Making the Decision
When deciding which firewall features to implement, you should be aware of the benefits that each firewall feature provides. A knowledge of these benefits will assist you in utilizing the features to protect your network. Table 14.3 shows how you can use each firewall feature to protect your network.
Table 14.3 Designing Firewall Features to Protect Internet-Accessible Resources
| Use This Firewall Feature | To Do the Following |
|---|---|
| NAT | Prevent the private network addressing scheme from being revealed Hide the true IP address of private network resources when accessing Internet-based resources |
| Packet filters | Manage what protocols are allowed to cross between the private network and the public network Define what action to take if a protocol is identified when crossing the firewall Define a default action to take if a protocol doesn't meet any of the defined packet filters |
| Static address mapping | Advertise Internet-accessible resources that have private network addresses using public network addressing Hide the true IP address of Internet-accessible resources |
| Stateful inspection | Protect UDP-based protocols that must enter the private network Detect session hijacking attempts Detect application-level attacks that attempt to bypass the packet filters established for a protocol |
| Time-out tolerances | Prevent SYN flood attacks by closing sessions that have timed out Free up connections for new connection attempts if the connection is left idle |
| Content scanning | Prevent specific application commands from being issued within a protocol Detect viruses within incoming packets |
Applying the Decision
The new firewall purchased by Market Florist should provide the following features to meet its security needs:
- NAT. The private network client computers require access to the Internet. To provide the ability to hide the true IP network addressing scheme used on the private network, NAT will replace all outgoing IP addresses with the NAT common address. In the Market Florist network scenario, all private network IP addresses will be replaced with the client.marketflorist.tld IP address of 131.107.88.2.
- Packet filters. You must define packet filtering at the firewall to allow only the authorized protocols to connect to each network resource. The specific filters will be discussed in Lesson 3, but Table 14.4 outlines the authorized protocols for connecting to each computer in the extranet.
Table 14.4 Protocols Allowed to Enter the Market Florist Extranet
Server Protocols MFDNS DNS. Public network users require access to the DNS server to resolve host names in the marketflorist.tld domain to IP addresses. Terminal Services. All administrators require the ability to remotely manage the MFDNS server.
MFWEB Hypertext Transfer Protocol (HTTP). All Web pages require HTTP access. HTTPS. Customers requesting a customer number require encryption of credit card and personal information.
Flower Power application. The Flower Power application listens for connections on a dedicated port.
Terminal Services. All administrators require the ability to remotely manage the MFWEB server. Additionally, you should configure the firewall to allow Terminal Services connections to each of the component servers, or nodes, in the NLBS cluster.
The MFWEB server also requires access to the MFSQL server on the private network.
MFFTP FTP. The MFFTP server allows FTP clients to enter FTP commands to access FTP data. FTP-DATA. FTP client software opens an FTP-DATA session when transferring data from the FTP server.
Telnet. John and Pat require Telnet access to manipulate the files available on the FTP server.
Terminal Services. All administrators require the ability to remotely manage the MFFTP server.
MFMAIL POP3. Remote Sales users must connect to the mail server using POP3 to retrieve their mail. SMTP. Remote Sales users connect to the MFMAIL server to send e-mail and customers connect to the MFMAIL server to deliver mail to Market Florist e-mail users.
Terminal Services. All administrators require the ability to remotely manage the MFMAIL server.
MFTUNNEL PPTP. Employees require PPTP to connect to private network resources from the Internet. Layer 2 Tunneling Protocol over Internet Protocol Security (L2TP/IPSec) can't be supported because the MFTUNNEL server is located behind a firewall that performs NAT. Terminal Services. All administrators require the ability to remotely manage the MFTUNNEL server.
- Static address mapping. To make the extranet servers accessible to customers on the public network, configure static address mapping for each server. Table 14.5 lists the necessary static address mappings.
Table 14.5 Market Florist Static Address Mapping Table
Hostname External IP Address Private Network IP Address www.marketflorist.tld 131.107.88.254 192.168.77.2 ftp.marketflorist.tld 131.107.88.253 192.168.77.7 mail.marketflorist.tld 131.107.88.252 192.168.77.8 vpn.marketflorist.tld. 131.107.88.251 192.168.77.9 - Stateful inspection. The Flower Power application uses UDP as its transport protocol. UDP-based applications do not establish sessions. A firewall must support stateful inspection to ensure that Flower Power connections aren't hijacked. The stateful inspection feature ensures that all response packets are using the same IP addresses and UDP ports that were used by the initial request packets.
- Time-out tolerance. To protect the Web site and other extranet resources from a denial of service attack, the firewall should support time-outs for disconnected sessions. This feature prevents SYN flooding attacks against the network.
- Content scanning. To prevent uploads of data to the MFFTP server, the firewall should deploy content scanning and prevent all attempts to use the FTP PUT command. This strategy provides greater protection by scanning the FTP transmissions for disallowed commands.
Comparing DMZ Configurations
When an organization hosts Internet-accessible resources, it's generally unadvisable to place those resources within the private network. Instead, place all Internet-accessible resources in a network segment commonly known as a DMZ between the private network and the public network.
What Are Some Other Terms for DMZ?
DMZs have a variety of common names, including screened subnet and perimeter network. Screened subnet refers to the function of a DMZ in network security. All network traffic that attempts to enter or exit the DMZ is screened by packet filters to determine whether they're allowed. Perimeter network refers to the DMZ's location. Typically, a DMZ exists between the private and the public network on the perimeter of the private network.
All three terms refer to the same area of your network and are configured identically to provide network security to Internet-accessible resources.
Networks use one of the following DMZ designs: a three-pronged firewall DMZ, a mid-ground DMZ, or a hybrid (or multizone) DMZ.
Designing a Three-Pronged Firewall DMZ
A three-pronged firewall DMZ consists of a firewall with three network interfaces. One interface is connected to the private network, another is connected to the public network, and the final interface is connected to the DMZ, as shown in Figure 14.5.
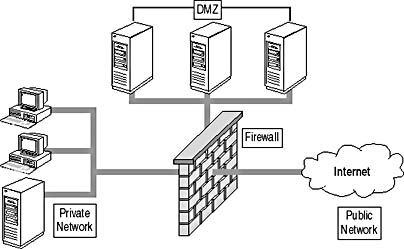
Figure 14.5 A three-pronged firewall DMZ
So Is the DMZ Part of the Private Network or the Public Network?
A DMZ is part of the private network and part of the public network. As you can see in Figure 14.5, the DMZ is separate from both the private and public networks.
In a sense, the DMZ is part of the public network, because resources that are accessible to the public network are placed in the DMZ. But the DMZ is also part of the private network because packet filters enforce which protocols can be used to connect to each server located in the DMZ.
An administrator establishes packet filters that are enforced by the firewall to restrict what traffic is allowed between each of the three zones. All Internet- accessible resources are placed in the DMZ to ensure that data connections originating from the public network can establish connections only to resources in the DMZ. They aren't allowed to establish connections to any resources on the private network.
When deploying a three-pronged firewall, ensure that your firewall solution supports three network interfaces. Each interface will be assigned to a zone and you must establish packet filters that define the interaction allowed between each zone.
When deciding whether the DMZ will use private or public network addressing, consider whether IPSec will be used from the public network to the DMZ. Since IPSec can't pass through a NAT service, you must use public network addressing in the DMZ whenever you require IPSec connections from the public network.
Mid-ground DMZ
You establish a mid-ground DMZ by using two firewalls. You place the first firewall between the public network and the DMZ and the second firewall between the DMZ and the private network, as shown in Figure 14.6.
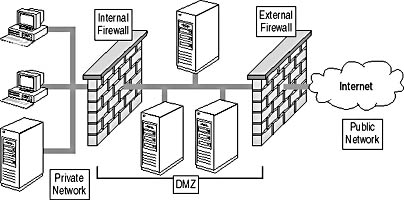
Figure 14.6 A mid-ground DMZ
While a three-pronged firewall DMZ can result in a single point of failure, the use of two firewalls provides additional protection to the private network because an attacker has to breach two firewalls before gaining access to the private network. By using two different firewall products, you can increase the protection offered to the private network because different methods may be required to breach the two firewalls.
As with a three-pronged firewall DMZ, the IP addressing used in the mid-ground DMZ can be either private or public network addressing. Generally you will use private network addressing in the DMZ unless there's a requirement to establish IPSec connections through the external firewall.
Hybrid DMZ
Sometimes a single DMZ may not meet your business requirements. In these cases, you can deploy a hybrid DMZ. A hybrid DMZ is a network where more than one zone exists between the private and the public networks.
Figure 14.7 depicts a hybrid DMZ configuration using a single firewall.
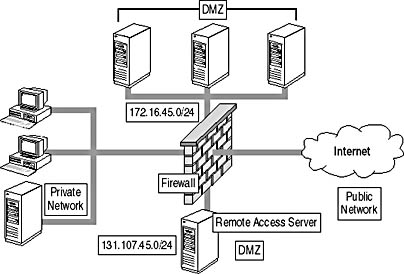
Figure 14.7 A hybrid DMZ with a single firewall
In this scenario you create two DMZs to support the need for IPSec connections and for protection of the private network addressing configuration for all other Internet-accessible resources. One DMZ, containing the remote access server that will accept IPSec connections, uses public network addressing. The second DMZ uses private network addressing and contains all other Internet-accessible resources. The firewall prevents static address mapping for all incoming traffic to the network segment. Likewise, NAT is performed on all outgoing traffic originating in the zone using private network addressing.
Alternatively, you can use multiple firewalls to establish two or more DMZs between the private network and the public network, as shown in Figure 14.8.
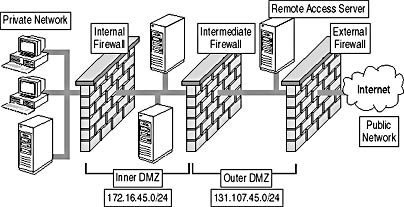
Figure 14.8 A hybrid DMZ with multiple firewalls
In this scenario the outermost DMZ uses public network addressing to allow IPSec connections to the remote access server. The innermost DMZ uses private network addressing to protect the remaining Internet-accessible resources. While more difficult to configure, the hybrid DMZ offers the most flexibility and allows a security administrator to group Internet-accessible resources based on the confidentiality of the data stored on the resource. Additionally, the administrator can configure each firewall with a set of packet filters to define exactly what traffic can enter and exit each DMZ.
Making the Decision
When network resources are exposed to the Internet, you should isolate the resources from the private network by deploying a DMZ. Table 14.6 discusses the design decisions for the three DMZ configurations that you must choose between.
Table 14.6 Choosing Between DMZ Configurations
| Use | To Meet These Business Objectives |
|---|---|
| Three-pronged firewall DMZ | To reduce the costs associated with deploying firewalls. Only a single firewall is required for this design. To maintain a single packet filter list. The packet filter rules determine which interface a packet filter is applied to. |
| Mid-ground DMZ | To provide physical separation of the private network from the public network with the DMZ being placed between the private and public networks. An attacker must breach two firewalls to access the private network. To reduce the chance that the breach of the external firewall will lead to access of the private network. If you use two different manufacturers for the internal and external firewalls, you gain security because different methods must be used to breach the second firewall. |
| Hybrid | To provide both private network and public network addressing to DMZ segments. To categorize Internet-accessible resources into different levels of access that can be protected by firewall strategies. |
Applying the Decision
Market Florist is limited by its budget and must develop a DMZ configuration that uses only a single firewall. Figure 14.9 shows a three-pronged firewall DMZ configuration that will meet Market Florist's security needs and support the proposed IP addressing scheme for all servers on the network.
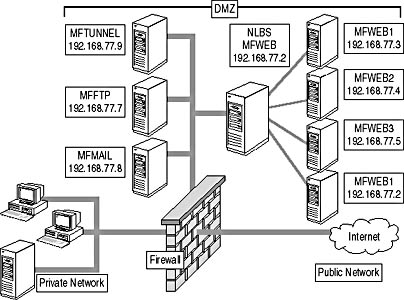
Figure 14.9 Proposed configuration for the Market Florist DMZ
Notice that each server in the NLBS cluster for the MFWEB server must be located in the DMZ. The NLBS listens on the IP address 192.168.77.2 but redirects the requests to one of the four servers in the cluster. The firewall is only required to redirect incoming HTTP or HTTPS packets to the NLBS cluster. The NLBS cluster service determines which node receives the incoming packets.
Lesson Summary
Knowing the features of firewalls and how they are commonly deployed will assist you in ensuring access to Internet-accessible resources is secure. Your design should take advantage of your firewall's configuration options to ensure that only authorized data transactions can take place.
EAN: 2147483647
Pages: 172