10.7 Making Technology Choices for the Network Design
10.7 Making Technology Choices for the Network Design
Now that we have developed some evaluation criteria for candidate technologies, we can begin the process of evaluating candidates for our design. In this section, we will develop some general guidelines for evaluating technologies, with the goal of producing a reasonable number of candidates for each area of the design. Typically, one or two candidates are reasonable. If one candidate is obviously above the rest, then the evaluation process was successful. When there are several candidates (more than two), the evaluation process needs improvement, the requirements and flows have not been sufficiently described, or the candidate technologies are very similar based on the evaluation criteria. When this occurs, you should reexamine the requirements and flows for the design.
In evaluating candidate technologies, we will use the evaluation criteria from the previous section. In addition, we will consider constraints imposed on the selection of technologies, based on cost or the precondition of existing networks. In making technology choices, we will first segment the network into workable sizes. Next we will apply a method that is termed here black box to isolate each area, and then we will apply the evaluation criteria and design guidelines to each area. The result will be one or more technology candidates for each area of the design.
10.7.1 Segmenting the Network
One of the problems we face in designing networks is that they are usually so large that it is difficult to absorb detailed information about the entire design. This is one of the most common complaints about designing a network: where to begin. What is needed is a way to segment the design into workable parts, termed here areas. The area concept that is developed here is similar to routing, addressing, and administrative areas that are used throughout the book. Segmenting the network is the first step toward making the design workable.
There are a few different ways to segment a network. We could segment a network based on geography, concentrations of users, or flow hierarchy. At times, all of these methods will produce similar results, so you should choose the method that makes the most sense and works best for you. Segmenting the network by geography is achieved by decomposing the network into areas whose sizes are based on physical or geographic regions. These regions may range from countries, states, or cities to areas within a city, campus, building, or parts of a building. If a network is being designed to interconnect offices in various cities, one way to segment the network is to divide it into individual city networks (LANs or metropolitan-area networks [MANs]), with a WAN to interconnect them, as in Figure 10.11.
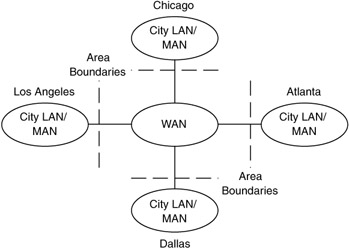
Figure 10.11: Sizing the network design at the (LAN/MAN)/WAN level.
At a campus level, we segment the network into buildings or parts of buildings, such as in Figure 10.12 of a campus network design.
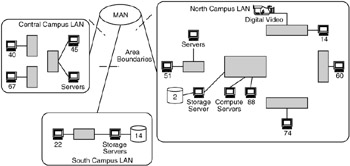
Figure 10.12: Sizing the network design at the campus level.
Similarly, we can divide the network design based on the numbers of users or on relative user concentrations. This may or may not equate to divisions based on geography. Instead of showing geographic information, we describe the numbers of users, perhaps including groups that they belong to within the organization. In Figure 10.13, boundaries are placed between groups of users.
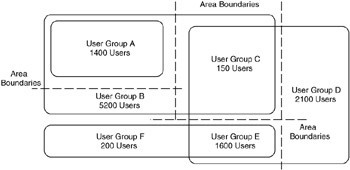
Figure 10.13: Sizing the network design based on user concentrations.
Separating users into groups may be based on where they are located or on some common characteristic. For example, users may be grouped by the organization for which they work.
This method is particularly useful when virtual groups of users are to be supported. Virtual user groups are either groups that are not tied to a particular location or groups that are dynamic in their locations, affiliations, or applications. At this point in the design process we have some flexibility in describing user groups and their user concentrations and in evaluating several methods for supporting virtual user groups, so it is now time to design for these groups. In doing so, we can optimize the design for them.
Arguably the most useful way to segment the network is by flow hierarchy. This method uses information in the flow specification to show where potential hierarchies may exist in the network. In addition, this method has the benefit of showing flows and their requirements, which will be important when evaluating and applying technologies to the design. Consider the flow hierarchies of a flow diagram such as those shown in Figure 10.14.
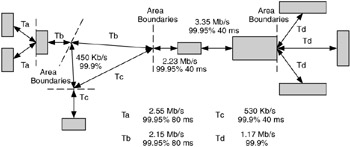
Figure 10.14: Sizing the network design based on flow hierarchies.
Here we can use the locations where individual and composite flows meet as boundaries for areas. In Figure 10.14, we placed boundaries at five locations, resulting in six network areas. Note that we also used performance templates (Ta, Tb, Tc, Td) to simplify showing performance requirements. When multiple flows have the same requirements, they are represented by the same performance template.
In a sense, segmenting by flow hierarchy incorporates geographic and user-group methods. Since flows are end-to-end between users, applications, and devices and their requirements have location information built into them, geography and usergroup information make up part of the flows.
The goal of segmenting a network is to decompose the network into areas whose sizes are small enough to limit the amount of information in choosing technologies, thus making technology selection easier. This means that the numbers of users, applications, devices, flows, and potential connections outside of the area are small enough that it is possible for a single technology to reasonably support that area. This requires an understanding of how various technologies size and scale. As you work through this chapter, you will find that segmenting the network overlaps with evaluating and applying network technologies.
Some related parameters for segmenting your network include the sizes of broadcast domains, types of services requested by users, and performance requirements of flows in the network. A broadcast domain is a group of network-addressable devices that can be reached by a single network address, the broadcast address. As a broadcast domain increases in size or as the number of broadcast protocols operating in a domain increases, the amount of broadcast traffic increases, affecting the overall performance of the network. It is desirable to keep the size of a broadcast domain reasonably small, especially if growth in the size of the network is expected.
An Alternative Method for Segmenting Networks
One method to segment networks that is often used in the field is to base the segmentation on functions and features required in that network. For example, WANs have some distinguishing characteristics that separate them from LANs (besides distance). A WAN may incorporate service providers and local and interexchange carriers that will affect its design. Likewise, there are locations in designs where many flows converge. These locations can have characteristics similar to Internet network access points (NAPs).
This method of segmenting leads to five types of areas in the design (Figure 10.15): WANs, which often use service providers and are focal points for flow consolidation; NAPs, which interconnect and integrate (or separate) the other areas; specialized areas, which have requirements and flows that dictate particular technologies; backbone or core areas, where flows are consolidated for transport; and general areas, which focus on more traditional requirements and where capacity planning, scalability, and cost-effectiveness are primary considerations. This method is offered as a simple, workable hybrid of the other methods. You should consider this method, as well as the other methods presented in this chapter, as a start toward developing your own method to segment networks.
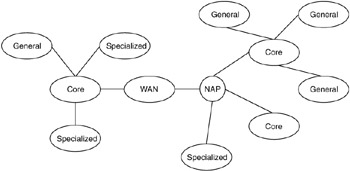
Figure 10.15: Sizing the network design based on functions and features of each area.
Segmentation can sometimes be used to solve security compartmentalization problems. Segments that need a higher degree of security can sometimes be isolated and a firewall can be used to provide the necessary protection. Segments isolated by security may be indicated during the development of the security architecture.
10.7.2 Isolating Areas—The Black-Box Method
With the network segmented into areas, we are ready to make technology selections for each area, after which the areas will be integrated into the design. As mentioned earlier in this chapter, one of the challenges in doing network design is being able to focus on a subset of the design. Some network designs are so large that it is easy to get lost within the design
The black-box method is a way to isolate each area of the network, making the technology selection process easier. This method hides areas of the design that we do not wish to focus on, isolating the area of choice. In this sense, it is similar to the traditional notion of a black box in engineering, where everything inside the black box is hidden from view.
This method can be applied in two ways: using a black box to cover the area under review and using it to cover everything else. In the first method, a black box is applied to the area where technology choices are to be made. When the black box is applied, only the inputs to and outputs from the black box are shown (Figure 10.16).
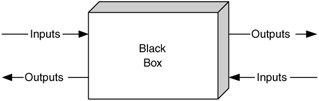
Figure 10.16: A black box isolates the inputs and outputs of each area.
In Figure 10.17, the inputs to and outputs from the black box equate to the flows and flow information for the area under review. With this method, the black box is applied to a particular area, technologies evaluated and chosen for that area, and the black box is moved to the next area. This process is repeated until technology choices are made for each area of the network design.
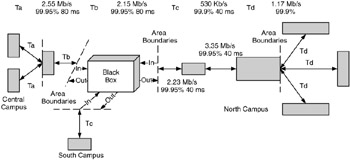
Figure 10.17: Black box applied to area under review.
The second method is to apply one or more black boxes to areas of the network design that are not under review. This allows visibility into the area under review while all else is blocked out (Figure 10.18).
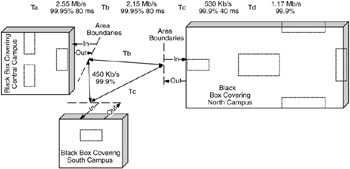
Figure 10.18: Black box applied to areas not under review.
As can be seen in Figure 10.18, this method blocks out the rest of the network design but leaves the area under review open to inspection. Although both methods have been used in the field, the first method (applying the black box to the area under review) is predominantly used.
We can use the black-box method at any level in the network design to hide the entire network (e.g., hiding existing networks), one or more areas or parts of areas, geographic or topological features (e.g., regions of a country, a campus, a building), even network devices in existing networks. At the extreme, a black box can hide everything except a single network device (e.g., router or switch), or it can be used only at the edges of the network design, leaving everything else within the network design exposed. Black boxes are applied to each area of the network design and are moved from area to area, until technology selections have been made for the entire design.
The black-box method, like other tools described in this book, is presented to help you in your design process. You may find it helpful, even necessary, to apply this method in large-scale network designs, although it may not be needed in smaller designs.
10.7.3 Applying Evaluation Criteria and Guidelines
As each area of the network design is isolated with the black-box method, we apply all of the information we have gathered, derived, and developed so far to make technology selections for the area. This information includes the variety of user, application, device, network, and other requirements; maps of location-specific information; flows and the flow specification; architecture and design goals; architecture information for each component architecture and the reference architecture; technology evaluation criteria; and guidelines.
How you apply all of this information depends primarily on what you have selected as your design goals, as well as how these design goals translate into evaluation criteria. The clearer your evaluation criteria are, the easier it will be to apply them to the design.
As you proceed through this process, making technology selections for each area of the design, you will find that different areas of the design may require different technologies. It is important to keep the design fairly homogenous in terms of network technologies. If too many technologies are chosen for the design, interoperability problems will arise. Therefore, as you move from area to area making technology selections, whenever you make selections that are different from previous areas, consider reevaluating previous areas to keep the number of selections low. At times, you may not be able to avoid having several technologies present in the design; however, limiting the number of technologies is suggested to keep the design simple and easy to implement.
EAN: 2147483647
Pages: 161