Section 3.3. VACM
3.3. VACMVACM is used to control access to managed objects in a MIB or MIBs. This is where the Access Control Subsystem comes into play. 3.3.1. The BasicsThe msgFlags, msgSecurityModel, and scopedPDU fields are used by VACM for message access. Each parameter is used to determine access to managed objects. An error is returned to the sender if access is not allowed for the request type. VACM makes use of four tables for different aspects of access control. We will discuss these tables next. 3.3.2. Context TableThe vacmContextTable is a collection of managed objects that have access constraints which are associated with a context name. The vacmContextTable stores all available contexts. The table is indexed by a contextName, and each row in this table contains:
3.3.3. Security to Group TableThe vacmSecurityToGroupTable is used to store group information. A group is made up of zero or more securityModel and securityName combinations. This combination defines what managed objects can be accessed. The table itself is indexed by a securityModel and securityName. The table contains rows made up of the following columns:
3.3.4. Access TableThe vacmAccessTable is used to store the access rights defined for groups. This table is indexed by a groupName, contextPrefix, securityModel, and securityLevel. Each row in this table contains:
3.3.5. View Tree Family TableThe vacmViewTreeFamilyTable is used to store MIB views. A MIB view is defined as a family of view subtrees that pair an OID subtree value with a mask value. The mask indicates which subidentifiers of the associated subtree OID are significant to the MIB view's definition. All the MIB views are stored in the vacmViewTreeFamilyTable. It is indexed by a viewName and an OID of a MIB subtree. The VACM MIB defines the vacmViewSpinLock advisory lock that is used to allow several SNMP engines to coordinate modifications to this table. Each row in the vacmViewTreeFamilyTable contains:
Figure 3-3[*] shows the logic flow for VACM.
Figure 3-3. VACM logic flow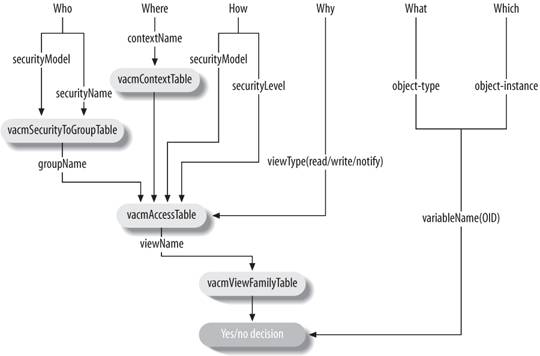 |
EAN: 2147483647
Pages: 165