Components of IEEE 802.11 LANs
| An IEEE 802.11 LAN Basic Service Set (BSS) can operate in one of exactly two modes, specifically "independent" or "infrastructure." A BSS in infrastructure mode is also sometimes referred to as being part of an ESS (Extended Service Set; a collection of more than one BSS and the necessary wired LAN Distribution System (DS) that ties them together), which behaves logically like an extended BSS. To make a collection of BSS WLANs into an ESS, they must all identify themselves using the same Service Set Identifier (SSID, or ESSID, or BSSID, depending on the context, but in any case it's the same thing, a string of up to 32 characters that identifies each BSS.[11]
Each infrastructure-mode BSS has exactly one AP. Independent BSS LANs do not have an AP. The lack of an AP, a form of network infrastructure that the independent BSS lacks, is why the term ad hoc is sometimes used when referring to a WLAN in IBSS mode (IBSS is the abbreviation of Independent BSS). There is significant opportunity for confusion since the term IBSS could reasonably be taken to mean either "independent BSS" (correct) or "infrastructure BSS" (incorrect). Table 1-1 translates the terms in the standard into the words that are frequently used in conversation to describe the types of WLANs.
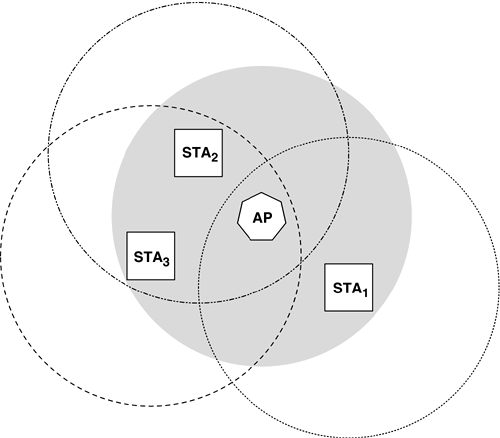
In this book, the author will tend to use the terms of the standard whenever possible, since they are more precise. Infrastructure ModeA WLAN in infrastructure (or BSS) mode consists of a control station (STA) known as an AP and a collection of client STAs.[12] Figure 1-2 illustrates a typical infrastructure-mode WLAN, consisting of a single BSS with an AP and several STAs.
Figure 1-2. A single wireless LAN BSS in infrastructure mode
The gray background centered on the AP indicates the AP's radio coverage (due to nonlinear propagation effects, the actual coverage domain is unlikely to be a circle). An STA is not able to be a part of the WLAN unless it is within range of the AP. The STA must also complete the procedures necessary to join the WLAN (a process comprising both authentication and association). All traffic in an infrastructure WLAN must pass through the AP. This restriction has a cost, which is that every frame must be sent across the wireless medium (WM) two times.[13] However, the benefit of this scheme is that all the stations need not be in range of each other; the BSS must only meet a much less restrictive constraint, namely that each STA must be able to hear the AP, and vice-versa. Every silver lining has a cloud, though, since by allowing STAs to be out of range of each other's radios, we have created a "hidden node" problem that increases the complexity of the access control procedures.
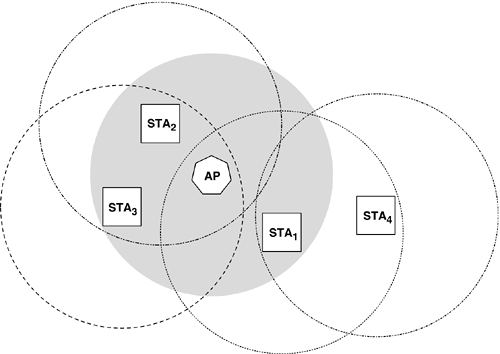
Realistically, however, the hidden node problem is only one aspect of the fundamental difference between the wireless medium and the wired medium with which we are all familiar, Ethernet. Ethernet detects collisions by simply listening for them while a transmission is in progress. A collision is an event that happens on the entire LAN segment simultaneously. The sender and all other members of the LAN can tell when it happens. However, in a WLAN, it is possible for a frame to be interfered with by some form of local interference at the receiver, without the interference being detectable by the sender. The way that the wireless LAN standards compensate for this is to require that most types of frames be acknowledged, which is not a reliability mechanism, but a remote collision detection mechanism. Therefore, there is no need for WLAN devices to incur the cost of duplex-capable radios (that can listen while they transmit; i.e., to try to detect collisions or other interference). The only requirement for WLANs is that the radio must be simplex; in other words, at any given time it is either a transmitter or a receiver, but it never needs to be both. Figure 1-3 shows a "hidden node" configuration in which STA2 and STA3 can both hear each other (as well as the AP), but STA1 can only hear the AP. Figure 1-3. Hidden nodes
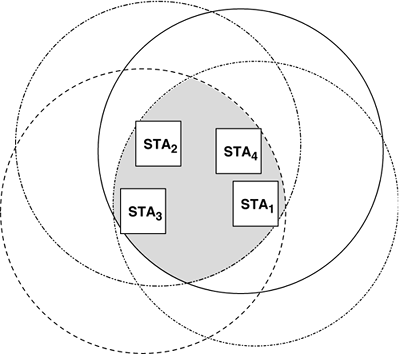
Moreover, STA4 is not part of the WLAN…at least not until it moves closer to the AP. The fact that STA1 can hear STA4 is irrelevant although the possibility exists that STA4 could interfere with STA1's ability to participate in the WLAN (i.e., if STA4 happens to transmit a frame while the AP is sending a frame to STA1). In the latter scenario, the AP would have no way to know that its transmission to STA1 was interfered with, because the AP is not within range of STA4. Even if two STAs happen to be within range of each other's radios (and the AP's, of course), the traffic flowing between the STAs still must pass through the AP. Note that even though STA2 and STA3 are both within range of each other's radios in Figure 1-3, their traffic still must pass through the AP. This may seem like a waste in the case of these two stations, but note that STA1 cannot directly reach STA2 or STA3…its only means of sending traffic to those two stations is via the AP. Therefore, even though using an AP has the effect of making the message cross the airwaves twice, this enables all stations in range of the AP to send traffic to each other, regardless of their actual proximity. If STA3 wants to send a frame to STA1, STA3 first sends the frame to the AP. The frame has now crossed the air once (the STA3-to-AP hop). The AP then forwards the frame on to its destination, namely STA1. The frame has now crossed the air a second time (the AP-to-STA1 hop). This has the effect of reducing the maximum capacity of the WLAN approximately in half. This may seem wasteful, but this "waste" is necessary, since in this example, STA1 and STA3 are not in range of each other's radios, so without the AP there would be no way for them to communicate. Each time the frame crossed the wireless medium, it is acknowledged (i.e., the ACK is hop-by-hop, not end-to-end). IBSS (Ad Hoc) ModeIn IBSS mode, a WLAN has no AP. Without the AP as a central control point, the STAs have to assume many of the duties of an AP. Because the AP function is not part of an IBSS-mode WLAN, a practical constraint on the layout of an ad hoc network is that all the STAs need to be reachable by all the other STAs. There can be no hidden nodes in an IBSS-mode WLAN. In Figure 1-4, we see four STAs in an IBSS-mode WLAN. The intersection of the coverage circles of the STAs represents the edges of the WLAN. Figure 1-4. Independent BSS (ad hoc) mode
For example, another function that an AP performs is to buffer traffic directed to a dozing STA (i.e., the state known as "dozing" occurs when the STA's radio is in power-save mode), the AP will buffer frames that are intended for that STA. In an IBSS, each STA must perform its own buffering in the event that another STA has temporarily dozed. Also, in an infrastructure BSS, the AP sends a periodic "Beacon" frame to coordinate the activities within the BSS, whereas in an IBSS, each STA takes turns sending the Beacon frame. IBSS WLANs also have a unique capability, in that they must support the merging of two IBSS-mode WLANs with the same SSID if they wander near enough each other. There are other differences, but these few samples should give the reader the correct impression that there are many fundamental differences between an IBSS-mode WLAN and an infrastructure-mode WLAN. Summary: Differences between Wired and Wireless LANsOne major difference between wired LANs such as Ethernet, and WLANs, is that in a WLAN, each STA has both limited transmitter power capacity and limited receiver sensitivity. On an Ethernet LAN, it is an assumption that all the stations can hear each other's transmissions, and can all speak loudly enough that all the other Ethernet stations can hear them. In addition, it is a presumption that the Ethernet transmitters can receive while they transmit, so that they can detect a collision as soon as it happens. In a WLAN, not all the STAs may be within range of a given STA's radio transmitter. Conversely, not all STAs may have sufficiently sensitive receivers to hear the transmissions of all the other STAs. Consequently, WLANs have a so-called "hidden-node" problem that wired LANs cannot have.[14]
Because of the hidden node problem, among other challenges specific to wireless media, the IEEE 802.11 MAC protocol supports an explicit ACK for unicast traffic. In a wired LAN, specifically Ethernet, there is an implicit requirement that a station will be able to tell on its own if its transmission was interfered with. In IEEE 802.11, however, the source may complete a transmission and never be able to hear the interference even if it had listened for it, the source of the interference may be close enough to the receiving STA to interfere with the frame it is receiving, but too far from the sending STA for its interference to be detected at the sender. In a WLAN, what matters is the noise environment at the destination, which is not necessarily the same as the noise environment at the source. The only way for the sender to be sure that its frame was received correctly is for the destination to acknowledge receipt of the frame. This ACK mechanism is not meant to make the IEEE 802.11 MAC protocol into a reliable data-link protocol; it is simply intended to compensate for the variation of RF noise and other interference across the WLAN. Another important fact to remember about WLANs is that the medium is inherently shared, so the MAC protocol is limited to what is effectively half-duplex operation (sometimes abbreviated as HDX), but the WLAN STAs are simplex devices, since at any given time they are either a transmitter or receiver, but never both. In plain English that means that only one station can be speaking at any given time. In HDX mode, the entire bandwidth of the channel is used completely by a single station for as long as the protocol allows, and the rest of the stations are idle while any given station is transmitting. In contrast, switching has brought full-duplex (FDX) operation to Ethernet's Medium Access Control (MAC) layer protocol, which was originally limited to HDX operation. In FDX mode, collisions are impossible and a station may be transmitting and receiving frames simultaneously. As will be seen in a subsequent chapter, the WLAN MAC sub-layer protocol is designed to function in the presence of hidden nodes, and other wireless-specific "challenges" with which wired LAN protocols do not need to be concerned. Before exploring the innards of the plethora of WLAN standards, it is useful to understand the organization that is producing these standards. |
EAN: 2147483647
Pages: 60