Hardware Components
| In the following sections, we describe the three common hardware components present in all RFID systems, tag, reader, and, antennae. TagThe tag, also known as the transponder (derived from the terms transmitter and responder), holds the data that is transmitted to the reader when the tag is interrogated by the reader. The most common tags today consist of an Integrated Circuit (IC) with memory, essentially a microprocessor chip (see Figure 3.3). Other tags are chipless and have no onboard IC. Chipless tags are most effective in applications where simpler range of functions is all that is required; although they can help achieve more accuracy and better detection range, at potentially lower cost than their IC-based counterparts. From here on out, we will use the term tag to mean IC-based tag. We will refer to chipless tags explicitly, when needed. Figure 3.3. A Typical Passive Tag (Left) and a Photo of a Partial Tag Microchip Design (Right)[1] (Photos Courtesy of Texas Instruments Incorporated (Left) and Celis Semiconductor Corporation (Right))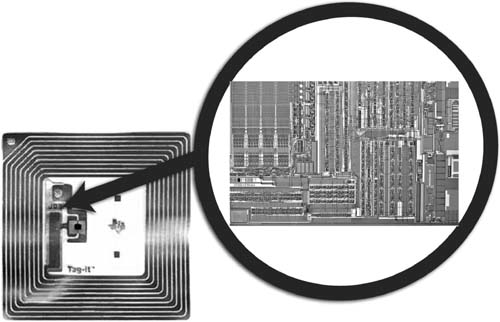
When a tag is interrogated, the data from its memory is retrieved and transmitted. A tag can perform basic tasks (read/write from/to memory) or manipulate the data in its memory in other ways. A tag's memory attribute can be read-only (RO), write once-read many (WORM), or read-write (RW). Memory write capability generally increases the cost of a tag, along with its capability to perform higher-level functions. At the same time, read-only tags eliminate the risk of accidental or malicious over-writing of tag data. Tag TypesThe most popular tags today are passive tags. These tags have favorable form factors and can be produced at very low cost, partly because they require no battery power. They get their power by harnessing the electromagnetic energy emitted from the reader. Many solutions are currently in place that employ passive tag technology, such as animal tracking, asset management, industrial automation, electronic article surveillance, and access control applications. Unlike passive tags, active tags have a battery on board that powers the tag and allows for longer read ranges, better accuracy, more complex information exchange, and richer processing capabilities. Because active tags have their own power source, they can transmit data without requiring a reader to power (energize) them. Due to the battery, active tags have a finite lifetime. One of the more common uses for active tags is for tracking high-value objects over long ranges such as tagging and tracking of military supplies shipped around the world. However, active tags are also used in many other commercial applications where environmental conditions and application requirements demand more robust tag and reader communication. The case studies titled, "Operation Enduring Freedom/Operation Iraqi Freedom (OEF/OIF)" and "Woolworths, Plc." in Appendix A demonstrate how the same active tag technology, by Savi Technology, is being used in a military and (separately) in a commercial application to operate in very challenging environmental conditions. There is also a class of tags called semi-active or semi-passive (the naming convention varies, depending on the tag manufacturer). This type of tag draws power from the onboard battery to "energize" and operate the tag's IC and perform simple tasks. However, it still utilizes the reader's electromagnetic field to "wake up" and draw power for transmitting the data stored in the tag back to the reader. A very common example of this tag type is electronic toll collection, in use since the 80s. Batteries used in these types of tags typically last several years because power is only consumed when the tag is activated and is in the reader's field. Tag PackagingTag packaging plays an important role in the "art" of creating RFID applications. Because a tag might require embedding in or attachment to an object that varies in size, contour, and surface material, the package that delivers a tag defines, to a large degree, its usefulness. Tag package dimensions are often defined by the size and shape of the tag's antenna. Current technology has enabled the production of flexible tags, also referred to as smart labels. A smart label functions like a typical adhesive label and often carries traditional printed barcode information in addition to an embedded RFID tag. Smart labels are affixed to objects in applications such as baggage handling or asset tracking. There are even flexible tags that have an onboard battery. These tags are called smart active labels (SAL). We discuss SAL technology in more detail in Chapter 11, "Emerging Trends in RFID." Tags can be embedded into a variety of other objects, including the following:
Tag Memory SizeTag memory is a very important element of IC-based RFID systems. Proper planning and use of tag memory can greatly enhance the functionality of an application. In certain supply chain applications, such as livestock tracking, the tag memory can be used initially to store a unique identifier. Then, at any stage in the supply chain, critical information can be updated, stored, and read. In this application, information might include health history, number of calves produced, date and location of ownership transfer, weight at the time of a sale, and so on. Tag memory configurations can vary greatly based on cost and physical requirements. In the case of EAS (electronic article surveillance), tags have essentially 1 bit of memory and are relatively inexpensive when compared to tags with more memory. These tags have no unique identifiers and are used only to signal their presence when they are in the field of a reader. Beyond the 1-bit tags, typical memory footprints can range from 16 bits to several hundred kbits for certain active tags. The amount of memory present on a tag is then defined by application requirements and/or any relevant standards or regulations. For example, due to the expected global acceptance of the EPCglobal standards, the memory size for the newer generation of passive tags will be 2 kbits or more. Table 3.1 shows a summary of selected tag attributes and compares their common characteristics.
Chipless TagsChipless identification technology, an emerging form of RFID, has the potential to help proliferate the use of RFID technology into an even greater number of applications. Essentially passive, chipless tags lack some of the memory capabilities of their IC-based (that is, microchip) counterparts. However, they can enhance the performance of applications in other ways. In simple terms, most of the chipless technologies employ the idea of "encoding" unique patterns on the surface of various reflective materials. These patterns then become the data that will be reflected back to custom designed readers via radio waves. Chipless tags require power only to transmit radio waves. They have no chip that would require additional power as is needed for IC-based tags. Although the underlying technology in chipless tags is well beyond the scope of this book, it is important to note the following significant advantages they can offer:
Note that these features are not the attributes of all chipless technologies, but they represent the range of features that exists amongst various types of chipless technologies. Chipless tags have been introduced into product labels, documents, and packaging. Developers of chipless tags market their technologies to medical, pharmaceutical, and consumer-packaging companies, as well as to agencies and entities concerned with intellectual property, classified information, securities, and banknotes. Sensory TagsSensory tags offer the capability to monitor, measure, and record various environmental conditions. The concept is quite simple. A sensing device is packaged together with a tag to interact and record whatever condition the sensor is designed to monitor. The technology involved can get challenging if an application calls for passive sensory tags. This means first that the sensor has no power while the tag is not in a reader's range and second that the power is very limited even when there is a reader in range. Some of the more interesting sensory tags that exist today, or are under development, include tags that can detect, record, and transmit changes in air pressure, temperature, volume of liquid, or the presence of chemical or bacterial agents. There are also tamper detection tags that can be applied to products at manufacture time. ReaderThe reader, also referred to as the interrogator, is a device that captures and processes tag data (see Figure 3.4). Although some readers can also write data onto a tag, the device is still referred to as a reader or interrogator. The reader is also responsible for interfacing with a host computer. We discuss typical functions of RFID readers in the following sections. Figure 3.4. Two Typical Passive RFID Readers (Photos Courtesy of Alien Technology Corporation [left] and Texas Instruments Incorporated [right]) Energize the TagIn the case of passive and semi-active tags, the reader provides the energy required to activate or energize the tag in the reader's electromagnetic field. The reach of this field is generally determined by the size of the antenna on both sides and the power of the reader. The size of the antenna is generally defined by application requirements. However, the power of the reader (through the antenna), which defines the intensity and reach of the electromagnetic field produced, is generally limited by regulations. Each country has its own set of standards and regulations relating to the amount of power generated at various frequencies. For this reason, incompatibilities do exist between RFID systems in various countries. In Chapter 4, "Standards Related to RFID," we discuss standards and their impact on the implementation of RFID-based applications, in detail. Define Operating FrequencyOne of the more important aspects of a tag and reader connection (coupling) is the frequency at which it operates. Frequency of operation can vary based on the application, standards, and regulations. The most common RFID frequency ranges are Low Frequency (LF) at 135kHz or less, High Frequency (HF) at 13.56MHz, Ultra High Frequency (UHF) starting at 433MHz, and Microwave Frequency at 2.45GHz and 5.8GHz. In general, the frequency defines the data transfer rate (speed) between the tag and the reader. The lower the frequency, the slower the transfer rate. However, speed is not the only consideration in designing an RFID solution. Environmental conditions can play a significant role in determining the optimal operating frequency for a particular application. For example, the substrate that tags are attached to (such as cans of soda) and the presence of other radio wave producing devices (such as microwave ovens or cordless telephones) can create interference in the UHF and microwave bands respectively. Higher frequency usually means smaller antennae, smaller tag size, and greater rangeand typically, more regulatory use restrictions and often, higher cost. Table 3.2 summarizes the most popular frequency bands, and their typical uses and characteristics.
Read Data from the TagThe most common task a reader will perform is, unsurprisingly, to read data stored on the tag. This process requires a sophisticated software algorithm to ensure reliability, security, and speed. We discuss the software required to achieve these objectives later in this chapter. Write Data onto the TagFor write-capable RFID systems, a reader can perform a dual function by also writing data onto a tag. This can be very useful because of the following:
Communicate with the Host ComputerThe reader is also responsible for the flow of data between the tags and the host computer. Typically the reader communicates with a host computer through a Serial or Ethernet connection. A reader may also be equipped to communicate with the host computer through a wireless connection, particularly if the reader is a portable or handheld device. We discuss the details of the software interface between the reader and the host computer later in this chapter.
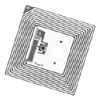
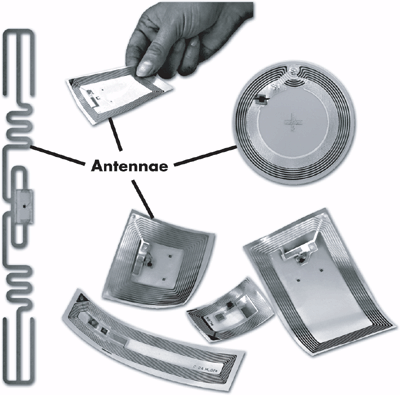
AntennaThe antennae are the conduits for data communication between the tag and the reader. Antenna design and placement plays a significant factor in determining the coverage zone, range and accuracy of communication. For example, a so-called linear reader antenna offers a higher range than a circular reader antenna. At the same time a linear antenna will yield less accurate read results in applications where the orientation of a tag's antenna, with respect to the reader's antenna, can vary randomly. This makes the linear antenna more suitable for applications where a tagged item's orientation is always the same, such as on an automated assembly line. The tag antenna is usually mounted on the same surface as the IC and packaged as a single unit. Figure 3.5 shows several common passive tag and antenna configurations. Although the tag IC can be tiny (the size of a grain of rice or smaller), the size and shape of the antenna typically determines the limits of the dimensions of the entire tag packaging. Figure 3.5. Some Typical Passive RFID Tags with Antenna Highlighted (Photos Courtesy of Texas Instruments Incorporated and Alien Technology Corporationfar left tag) The packaging characteristics for the antenna on a reader also vary greatly depending on application requirements. In certain cases such as handheld readers, the antenna is mounted directly on the reader. In other cases, several antennae can be mounted away from a reader unit and positioned strategically to enhance the quality and range of the radio signals. For example, in a pallet tracking application, the reader may be connected through a network of antennae forming a well-defined detection zone such as a portal or a gate for accurate and reliable performance at the loading dock (see Figure 3.6). Figure 3.6. RFID Reader and Antennae Portal (Photo Courtesy of Symbol Technologies, Inc.) Limitations of Tag and Reader CommunicationsBecause the science of radio frequency is analog, not digital, it is susceptible to degradation caused by interference from spurious RF noise sources and environmental conditions. Interference can be caused by proximity to the following:
The degree to which these conditions affect a given RFID system's performance depends on the operating frequency. The capability to address interference issues plays a significant role in the success of an RFID deployment. For this reason, extensive trials and pilots to enable optimal placement and installation of the individual RFID components are critically important. RF engineers are making great progress in designing systems that continue to push the RF physics to overcome some of these limitations. At the same time, many of the inaccuracies and inconsistencies also can be addressed with sophisticated software solutions that implement error correction, fault tolerance, and redundancy. Host ComputerThe hardware characteristics of a host computer are generally dependent on the type of software applications running on the computer. We therefore describe the function of the host computer in terms of the host application. The host application, described in the next section, is the collection of existing and new software programs that leverage the data generated by an RFID system. Going forward, we will use the terms host computer and host application interchangeably. |
EAN: 2147483647
Pages: 112
- An Emerging Strategy for E-Business IT Governance
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- A View on Knowledge Management: Utilizing a Balanced Scorecard Methodology for Analyzing Knowledge Metrics
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governing Information Technology Through COBIT