Lesson 1: NTFS Permissions
After this lesson, you will be able to
- Define the standard NTFS folder and file permissions
- Describe the results of combining user account and group permissions
- Describe the results of assigning permissions for folders that are different from those of the files in the folder
- Assign NTFS folder and file permissions to user accounts and groups
Estimated lesson time: 15 minutes
File Systems
After you create the installation partition, Setup prompts you to select the file system with which to format the partition. Windows 2000 supports three file systems: Windows 2000 file system (NTFS), file allocation table (FAT), and FAT32.
The Table 3.1 lists the features of the various file systems.
Table 3.1 File System Features
| File system | Feature |
|---|---|
| NTFS | File and Folder level security |
| Disk Compression | |
| Disk Quota management | |
| Encryption | |
| Remote Storage | |
| Dynamic Volume | |
| Mounting of Volumes to Folders | |
| Permission settings | |
| FAT and FAT32 | Dual Booting No File-level security |
Unless you require dual booting, NTFS is the file system to use.
File and Folder Permissions
NTFS also allows you to specify which users and groups can gain access to files and folders and what they can do with the contents of the file or folder. NTFS permissions are available only on NTFS volumes. NTFS permissions are not available on volumes that are formatted with FAT or FAT32 file systems. NTFS security is effective whether a user gains access to the file or folder locally or from the network. The permissions you assign for folders are different from the permissions you assign for files.
NTFS Folder Permissions
You assign folder permissions to control the access that users have to folders and to the files and subfolders contained within the folder.
Table 3.2 lists the standard NTFS folder permissions that you can assign and the type of access that each provides to users.
Table 3.2 NTFS Folder Permissions
| NTFS folder permission | Allows the user to |
|---|---|
| Read | See files and subfolders in the folder and view folder ownership, permissions, and attributes (such as Read-Only, Hidden, Archive, and System) |
| Write | Create new files and subfolders within the folder; change folder attributes; view details of folder ownership and permissions |
| List Folder Contents | See the names of files and subfolders in the folder |
| Read & Execute | Move through folders to reach other files and folders, even if the users don't have permission for those folders; perform actions permitted by the Read permission and the List Folder Contents permission |
| Modify | Delete the folder; perform actions permitted by the Write permission and the Read & Execute permission |
| Full Control | Change permissions, take ownership, and delete subfolders and files; perform actions permitted by all other NTFS folder permissions |
As an administrator, you can deny permission to any user account or group. To deny all access to a user account or group for a folder, deny the Full Control permission.
NTFS File Permissions
You assign file permissions to control the access that users have to files. Table 3.3 lists the standard NTFS file permissions that you can assign and the type of access that each permission provides.
Table 3.3 NTFS File Permissions
| NTFS file permission | Allows the user to |
|---|---|
| Read | Read the file view file attributes, ownership, and permissions |
| Write | Overwrite the file; change file attributes; view file ownership and permissions |
| Read & Execute | Run applications; perform the actions permitted by the Read permission |
| Modify | Modify and delete the file; perform the actions permitted by the Write permission and the Read & Execute permission |
| Full Control | Change permissions and take ownership; perform the actions permitted by all other NTFS file permissions |
Applying NTFS Permissions
Administrators, the owners of files or folders, and users with Full Control permission can assign NTFS permissions to users and groups to control access to files and folders.
Access Control List
NTFS stores an access control list (ACL) with every file and folder on an NTFS volume. The ACL contains a list of all user accounts and groups that have been granted access for the file or folder, as well as the type of access that they have been granted. If a user attempts to gain access to a resource, the ACL must contain an entry called an access control entry (ACE) for the user account or a group to which the user belongs. The entry must allow the type of access that is requested (for example, Read access) for the user to gain access. If no ACE exists in the ACL, the user can't gain access to the resource.
Multiple NTFS Permissions
You can assign multiple permissions to a user account and to each group in which the user is a member. To assign permissions, you must understand the rules and priorities regarding how NTFS assigns and combines multiple permissions and NTFS permission inheritance.
Cumulative Permissions
A user's effective permissions for a resource are the sum of the NTFS permissions that you assign to the individual user account and to all of the groups to which the user belongs. If a user has Read permission for a folder and is a member of a group with Write permission for the same folder, the user has both Read and Write permission for that folder.
Overriding Folder Permissions with File Permissions
NTFS file permissions take priority over NTFS folder permissions. A user with access to a file will be able to gain access to the file even if he or she doesn't have access to the folder containing the file. A user can gain access to the files for which he or she has permissions by using the full universal naming convention (UNC) or local path to open the file from its respective application, even though the folder in which it resides will be invisible if the user has no corresponding folder permission. In other words, if you don't have permission to access the folder containing the file you want to access, you will have to know the full path to the file to access it. Without permission to access the folder, you can't see the folder, so you can't browse for the file you want to access.
Overriding Other Permissions with Deny
You can deny permission to a user account or group for a specific file, although this is not the recommended way to control access to resources. Denying a permission overrides all instances where that permission is allowed. Even if a user has permission to gain access to the file or folder as a member of a group, denying permission to the user blocks that and any other permission the user might have (see Figure 3.1).
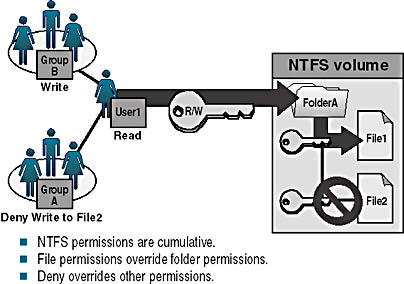
Figure 3.1 Multiple NTFS permissions
In Figure 3.1, User1 has Read permission for FolderA and is a member of Group A and Group B. Group B has Write permission for FolderA. Group A has been denied Write permission for File2.
Because of the read and write permissions User1 has to FolderA, User1 can read and write to File1. The user can also read File2 because of the folder permissions, but she cannot write to File2 because she is a member of Group A, which has been denied Write permission for File2.
NTFS Permissions Inheritance
By default, permissions that you assign to the parent folder are inherited by and propagated to the subfolders and files that are contained in the parent folder. However, you can prevent permissions inheritance, as shown in Figure 3.2.
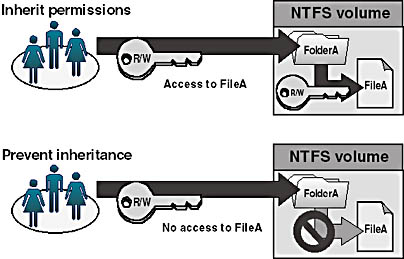
Figure 3.2 Inheritance
You can prevent permissions assigned to a parent folder from being inherited by subfolders and files that are contained within the folder. That is, the subfolders and files will not inherit permissions that have been assigned to the parent folder containing them.
The folder for which you prevent permissions inheritance becomes the new parent folder, and permissions that are assigned to this folder will be inherited by the subfolders and files that are contained within it.
Planning NTFS Permissions
You should follow certain guidelines for assigning NTFS permissions. Assign permissions according to group and user needs, which includes allowing or preventing permissions inheritance from parent folders to subfolders and files that are contained in the parent folder.
If you take the time to plan your NTFS permissions and follow a few guidelines, you will find that NTFS permissions are easy to manage. Use the following guidelines when you assign NTFS permissions:
- To simplify administration, group files into application, data, and home folders. Centralize home and public folders on a volume that is separate from applications and the operating system. Doing so has the following benefits:
- You assign permissions only to folders, not to individual files.
- Backup is less complex because you don't need to back up application files, and all home and public folders are in one location.
- Allow users only the level of access that they require. If a user only needs to read a file, assign the Read permission to his or her user account for the file. This reduces the possibility of users accidentally modifying or deleting important documents and application files.
- Create groups according to the access that the group members require for resources, and then assign the appropriate permissions to the group. Assign permissions to individual user accounts only when necessary.
- When you assign permissions for working with data or application folders, assign the Read & Execute permission to the Users group and the Administrators group. This prevents application files from being accidentally deleted or damaged by users or viruses.
- When you assign permissions for public data folders, assign the Read & Execute permission and the Write permission to the Users group and the Full Control permission to the CREATOR OWNER user. By default, the user who creates a file is also the owner of the file. After you create a file, you can grant another user permission to take ownership of the file. The person who takes ownership then becomes the owner of the file. If you assign the Read & Execute permission and the Write permission to the Users group and the Full Control permission to the CREATOR OWNER user, users can read and modify documents that other users create and they are able to read, modify, and delete the files and folders that they create.
- Deny permissions only when it is essential to deny specific access to a specific user account or group.
- Encourage users to assign permissions to the files and folders they create and educate users about how to do so.
Setting NTFS Permissions
By default, when you format a volume with NTFS, the Full Control permission is assigned to the Everyone group. You should change this default permission and assign other appropriate NTFS permissions to control the access that users have to resources.
Assigning or Modifying Permissions
Administrators, users with the Full Control permission, and the owners of files and folders (CREATOR OWNER) can assign permissions to user accounts and groups.
To assign or modify NTFS permissions for a file or a folder, on the Security tab of the Properties dialog box for the file or folder, configure the options that are shown in Figure 3.3 and described in Table 3.4.
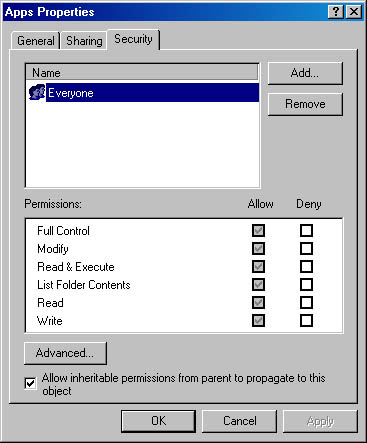
Figure 3.3 The Security tab of the Apps Properties dialog box for a folder
Table 3.4 Security Tab Options
| Option | Description |
|---|---|
| Name | Allows you to select the user account or group for which you want to change permissions or that you want to remove from the list |
| Permissions | Allows you to select the Allow check box to allow a permission Allows you to select the Deny check box to deny a permission |
| Add | Allows you to open the Select Users, Computers, Or Groups dialog box, which you use to select user accounts and groups to add to the Name list |
| Remove | Allows you to remove the selected user account or group and the associated permissions for the file or folder |
| Advanced | Allows you to open the Access Control Settings for the selected folder so that you can grant or deny additional permissions |
Preventing Permissions Inheritance
By default, subfolders and files inherit permissions that you assign to their parent folder. This is indicated on the Security tab in the Properties dialog box by a check mark in the Allow Inheritable Permissions From Parent To Propagate To This Object check box. To prevent a subfolder or file from inheriting permissions from a parent folder, clear the Allow Inheritable Permissions From Parent To Propagate To This Object check box. If you clear this check box, you are prompted to select one of the options described in Table 3.5.
Table 3.5 Preventing Permissions Inheritance Options
| Option | Description |
|---|---|
| Copy | Allows you to copy the permissions from the parent folder to the current folder and then deny subsequent permissions inheritance from the parent folder |
| Remove | Allows you to remove the permissions that are inherited from the parent folder and retain only the permissions that you explicitly assign to the file or folder |
| Cancel | Allows you to cancel the dialog box and restore the check mark in the Allow Inheritable Permissions From Parent To Propagate To This Object check box |
Lesson Summary
In this lesson, you learned that, by default, when you format a volume with NTFS, the Full Control permission is assigned to the Everyone group. You should change this default permission and assign other appropriate NTFS permissions to control the access that users have to resources. To assign or modify NTFS permissions for a file or a folder, you use the Security tab of the Properties dialog box for the file or folder.
You also learned that, by default, subfolders and files inherit permissions that you assign to their parent folder. You can disable this feature so that subfolders and files don't inherit the permissions assigned to their parents.
EAN: N/A
Pages: 244