Lesson 2: Controlling Access to Active Directory Objects
Windows 2000 uses an object-based security model to implement access control for all Active Directory objects. This security model is similar to the one that Windows 2000 uses to implement Microsoft Windows NT file system (NTFS) security. Every Active Directory object has a security descriptor that defines who has the permissions to gain access to the object and what type of access is allowed. Windows 2000 uses these security descriptors to control access to objects. This lesson explains how to set permissions for Active Directory objects.
After this lesson, you will be able to
- Set permissions on Active Directory objects to control user access
Estimated lesson time: 20 minutes
Understanding Active Directory Permissions
Active Directory permissions provide security for resources by allowing you to control who can gain access to individual objects or object attributes and the type of access that you will allow.
Active Directory Security
Use Active Directory permissions to determine who has the permissions to gain access to the object and what type of access is allowed. An administrator or the object owner must assign permissions to the object before users can gain access to the object. Windows 2000 stores a list of user access permissions, called the access control list (ACL), for every Active Directory object. The ACL for an object lists who can access the object and the specific actions that each user can perform on the object.
You can use permissions to assign administrative privileges to a specific user or group for an OU, a hierarchy of OUs, or a single object, without assigning administrative permissions for controlling other Active Directory objects.
Object Permissions
The object type determines which permissions you can select. Permissions vary for different object types. For example, you can assign the Reset Password permission for a user object but not for a printer object.
A user can be a member of multiple groups, each with different permissions that provide different levels of access to objects. When you assign a permission to a user for access to an object and that user is a member of a group to which you assigned a different permission, the user's effective permissions are the combination of the user and group permissions. For example, if a user alone has Read permission for an object and is a member of a group with Write permission, the user's effective permission for the object is Read and Write.
You can allow or deny permissions. Denied permissions take precedence over any permissions that you otherwise allow for user accounts and groups. If you deny a user permission to gain access to an object, the user will not have that permission, even if you allow the permission for a group of which the user is a member. You should deny permissions only when it is absolutely necessary to deny permission to a specific user who is a member of a group with allowed permissions.
NOTE
Always ensure that all objects have at least one user with the Full Control permission. Failure to do so might result in some objects being inaccessible to the person using the Active Directory Users And Computers console, even an administrator, unless object ownership is changed.
Standard Permissions and Special Permissions
You can set standard permissions and special permissions on objects. Standard permissions are the most frequently assigned permissions and are composed of special permissions. Special permissions provide you with a finer degree of control for assigning access to objects.
For example, the standard Write permission is composed of the Write All Properties, Add/Remove Self As Member, and Read special permissions.
Table 19.3 lists standard object permissions that are available for most objects (most object types also have special permissions) and the type of access that each standard permission allows.
Table 19.3 Standard Object Permissions and Type of Access Allowed
| Object permission | Allows the user to |
|---|---|
| Full Control | Change permissions and take ownership and perform the tasks that are allowed by all other standard permissions |
| Read | View objects and object attributes, the object owner, and Active Directory permissions |
| Write | Change object attributes |
| Create All Child Objects | Add any type of child object to an OU |
| Delete All Child Objects | Remove any type of object from an OU |
Assigning Active Directory Permissions
You can use the Active Directory Users And Computers console to set standard permissions for objects and attributes of objects. You use the Security tab of the Properties dialog box for the object to assign permissions (see Figure 19.2). The Properties dialog box is different for each object type.
IMPORTANT
You must select Advanced Features on the View menu to access the Security tab and assign standard permissions for an object.
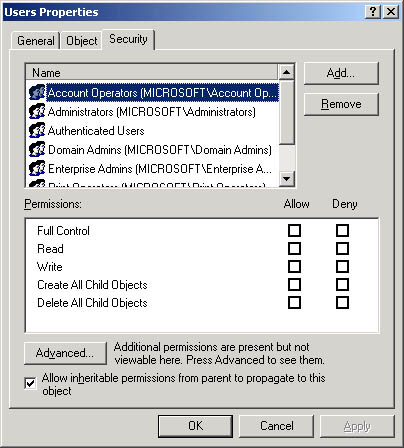
Figure 19.2 Setting Active Directory permissions
If the check boxes under Permissions are shaded, the object has inherited permissions from the parent object. To prevent an object from inheriting permissions from a parent folder, clear the Allow Inheritable Permissions From Parent To Propagate To This Object check box.
Follow these steps to assign standard permissions for an object:
- In Active Directory Users And Computers, on the View menu, ensure that Advanced Features is selected.
- Select an object, click Properties on the Action menu, and then click the Security tab in the Properties dialog box for the object.
- To assign standard permissions:
- To add a new permission, click Add, click the user account or group to which you want to assign permissions, click Add, and then click OK.
- To change an existing permission, click the user account or group.
- Under Permissions, select the Allow check box or the Deny check box for each permission you want to add or remove.
Standard permissions are sufficient for most administrative tasks. However, you might need to view the special permissions that constitute a standard permission. Occasionally the Security tab displays a user or a group where none of the standard permissions is allowed or denied; in such a case, the user or group has been given special permissions that are accessible through the Advanced button.
Follow these steps to view special permissions:
- In the Security tab in the Properties dialog box for the object, click Advanced.
- In the Access Control Settings For dialog box for the object (an example is shown in Figure 19.3), in the Permissions tab, click the entry that you want to view in the Permission Entries list, and then click View/Edit.
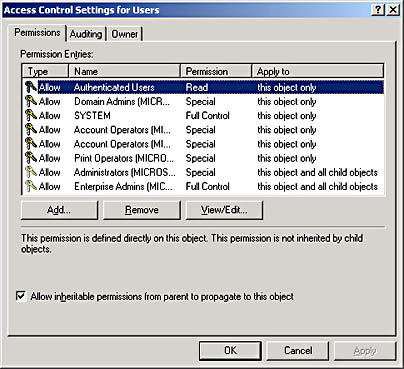
Figure 19.3 Access Control Settings For Users dialog box
- In the Permission Entry For dialog box (see Figure 19.4) for the object, view the special permissions on the appropriate tab.
Use the Object tab to view special object permissions assigned to the user or group, or use the Properties tab to view user or group read and write access to specific object properties.
NOTE
Avoid assigning permissions for specific properties of objects because this can complicate system administration. Errors can result, such as Active Directory objects not being visible, which prevents users from completing tasks.
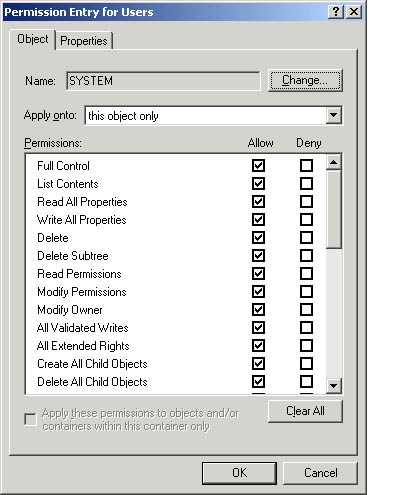
Figure 19.4 Permission Entry For Users dialog box
Using Permissions Inheritance
Permissions inheritance for Active Directory objects, which is similar to file and folder permissions inheritance, minimizes the number of times that you need to assign permissions for objects. When you assign permissions, you can apply the permissions to child objects, which propagates the permissions to all of the child objects for a parent object, as shown in Figure 19.5. To indicate that permissions are inherited, the check boxes for inherited permissions are shown as shaded.
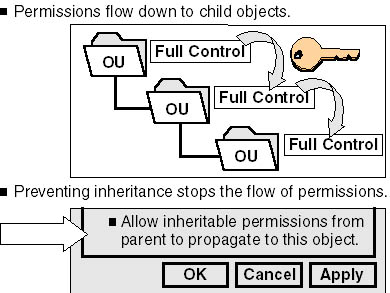
Figure 19.5 Inheriting permissions and blocking inheritance
For example, you can assign Full Control permission to a group for an OU that contains printers and then propagate this permission to all child objects. The result is that all group members can administer all printers in the OU.
You can specify that permissions for a given object are propagated to all child objects. You can also prevent permissions inheritance. When you copy previously inherited permissions, you start with exactly the same permissions that the object currently inherits from its parent object. However, any permissions for the parent object that you modify after blocking inheritance no longer apply. When you remove previously inherited permissions, Windows 2000 removes existing permissions and assigns no additional permissions to the object. You have to assign any permissions you want for the object.
Preventing Permissions Inheritance
You can prevent permissions inheritance so that a child object does not inherit permissions from its parent object by clearing the Allow Inheritable Permissions From Parent To Propagate To This Object check box. When you prevent inheritance, only the permissions that you explicitly assign to the object apply. You use the Security tab in the Properties dialog box to prevent permissions inheritance.
When you prevent permissions inheritance, Windows 2000 allows you to
- Copy previously inherited permissions to the object. The new explicit permissions for the object are a copy of the permissions that it previously inherited from its parent object. Then, according to your needs, you can make any necessary changes to the permissions.
- Remove previously inherited permissions from the object. Windows 2000 removes any previously inherited permissions. No permissions exist for the object. You can then assign any permissions for the object, according to your needs.

Practice: Controlling Access to Active Directory Objects
In this practice, you create an OU with two users and review the default security settings on Active Directory components.
CAUTION
In the following exercise, you should not change any security settings in Active Directory. Making changes could result in losing access to portions of Active Directory.
Exercise 1: Create an OU Containing Two User Accounts
In this exercise, you create a new organizational unit and add two user accounts to this OU.
- Log on to your domain as Administrator, and then open Active Directory Users and Computers.
- In the console tree, click on the name of your domain.
- On the Action menu, point to New, and then click Organizational Unit.
- In the New Object-Organizational Unit dialog box, in the Name box, type security1 and then click OK.
- In the Security1 OU, create a user account that has the First Name field and the User Logon Name field set to Assistant1. Type password as the password and accept the defaults for all other options.
- In the same OU, create another user account that has the First Name field and the User Logon Name set to Secretary1. Type password as the password and accept the defaults for all other options.
- Grant both users membership in the Print Operators group or another group with the right to log on locally to the domain controller.
Exercise 2: View Default Active Directory Permissions for an OU
Before you assign permissions, you should determine what, if any, permissions the users may have as a result of belonging to any groups. In this exercise you view and then record the default Active Directory permissions.
- On the View menu, enable Advanced Features.
Enabling the viewing of advanced features allows you to review and configure Active Directory permissions.
- In the console tree, right-click Security1, and then click Properties.
- Click the Security tab.
- In the following table, list the groups that have permissions for the Security1 OU. You will need to refer to these permissions in Lesson 5.
Groups that Have Permissions for the Security1 OU
| User account or group | Assigned permissions |
|---|---|
How can you tell if any of the default permissions are inherited from the domain, which is the parent object?
Answer
Exercise 3: View Special Permissions for an OU
Again, before assigning permissions, you should determine what permissions have already been assigned to the users. In this exercise, you will view any special permissions that have been assigned to the users or groups.
- In the Security1 Properties dialog box, in the Security tab, click Advanced.
The Access Control Settings For Security1 dialog box appears.
- To view special permissions for Account Operators, in the Permission Entries box, click each entry for Account Operators, and then click View/Edit.
The Permission Entry For Security1 dialog box appears.
What object permissions are assigned to Account Operators? What can Account Operators do in this OU? (Hint: Check each permission entry for Account Operators in the Permission Entries box in the Access Control Settings For Security1 dialog box.)
Do any objects within this OU inherit the permissions assigned to the Account Operators group? Why or why not?
Answer
- Close all open dialog boxes, but do not close Active Directory Users and Computers.
Exercise 4: View the Default Active Directory Permissions for a User Object
In this exercise, you will view and record any default Active Directory permissions assigned to a user object.
- In the Active Directory Users And Computers console tree, click Security1.
- In the details pane, right-click Secretary1, and then click Properties.
- Click the Security tab.
- In the following table, list the groups that have permissions for the Secretary1 user account. You will need to refer to these permissions in Lesson 5. If the dialog box indicates that special permissions are present for a group, do not list the special permissions to which you can gain access through the Advanced button.
Permissions for the Secretary1 User Account
| Group | Assigned permissions |
|---|---|
Are the standard permissions for a user object the same as those for an OU object? Why or why not?
Are any of the standard permissions inherited from Security1, the parent object? How can you tell?
What do the permissions of the Account Operators group allow its members to do with the user object?
Answer
- Close all programs and log off Windows 2000.
Lesson Summary
In this lesson, you learned that every Active Directory object has a security descriptor that defines who has permission to gain access to the object and what type of access is allowed. An administrator or the object owner must assign permissions to an object before users can gain access to it. Windows 2000 stores a list of user access permissions, called the ACL, for every Active Directory object.
You also learned how to set standard permissions and special permissions on objects. The standard permissions are Full Control, Write, Read, Create All Child Objects, and Delete All Child Objects. Special permissions provide you with a finer degree of control over assigning access to objects. Permissions inheritance in Active Directory minimizes the number of times that you need to assign permissions for objects. When you assign permissions, you can apply the permissions to child objects, which propagates the permissions inheritance for a given parent object. You also learned how to block permissions inheritance.
In the practice portion of this lesson, you created an OU with two users and reviewed the default security settings on Active Directory components.
EAN: N/A
Pages: 244
- Chapter I e-Search: A Conceptual Framework of Online Consumer Behavior
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XVII Internet Markets and E-Loyalty