Justifying Your Purchase
Let us suppose that you have chosen an IDS that satisfies all your requirements. After making your choice, you need to purchase the chosen system. At this step, you might encounter some misunderstandings with top management (the board of directors), who often underestimate the need for investing into intrusion detection system. In 1999, two companies - ICSA and SAIC - polled 745 respondents with a single question: "What is the greatest obstacle that prevents you from ensuring information security?" The most common answers and their frequency are outlined in Table 8.2.
| Obstacle | Number of organizations (%) |
|---|---|
| | |
| Budget limitations | 29 |
| Lack of managerial support | 14 |
| Lack of qualified security specialists, low qualification of end users | 10 |
| Low qualification of security personnel | 9 |
| Lack of correspondence to the internal security policy | 8 |
| Lack of authority | 8 |
| Technical complexity | 6 |
| Incomprehensible liabilities | 4 |
| Lack of reliable security tools | 3 |
| Other | 9 |
The results of a similar poll conducted in 1999 by Information Week among 2700 respondents in 49 countries produced the results shown in Table 8.3.
| Obstacle | Number of organizations (%) |
|---|---|
| | |
| Lack of time | 17 |
| Technological difficulties | 16 |
| Rate of technological evolution | 11 |
| Lack of support by top management | 11 |
| Poorly designed security policy | 10 |
| Financial expenses | 8 |
| Lack of cooperation between departments | 8 |
| Lack of knowledgeable end users | 8 |
| Low qualification of security personnel | 6 |
| Time expense and lack of human resources | 5 |
From the results of these two polls, it is evident that lack of support by top management is one of the reasons that prevent organizations from deploying intrusion detection systems. Consequently, the better you can justify the necessity of investments into the intrusion detection infrastructure, the higher is the probability of the project's success. Thus, if you can compose a well-grounded budget for IDS deployment and implementation, and find proper arguments in support of your project when facing top management, you'll have a good chance of building a really efficient and reliable security system. Remember that upper-level managers of the company, such as the General Manager, the Chief Financial Officer, the Chairman of the Board of Directors, etc., are not usually technical experts, and can not quite understand all the technical details of intrusion detection technologies. The fact that some of them might seem to support your ideas of ensuring information security does not necessarily mean that they will continue supporting the idea of IDS deployment when it comes to their attention how much it will cost. Besides this, some of those in top management may have heard about the existence of freeware intrusion detection products. If this is the case, be prepared to answer the question, which is a quite logical and reasonable one from any financier's point of view: "Why should we invest money if we can use free solutions?" Thus, it is very important to carefully plan the budget for organizing the security infrastructure and provide a well-grounded basis for each item in the budget. If you speak IT language only, your managers will not understand you, and will not be able to understand your ideas without prejudice (of course, this only applies if they are not technical persons that come from the same technical environment as you). Try to explain the situation using financial language rather than technical, and they will understand you much better. Furthermore, if you succeed in preparing a good budget and carefully finding good reasons for the need to invest into the intrusion detection infrastructure, you will notice that the directors will value you, and provide your project with the required financial resources without discussing the technical details. Certainly, this is only possible if you manage to clearly explain all advantages that the company will get from IDS deployment and implementation, methods of controlling the investments, and evaluating its efficiency.
What is the goal of any company? Clearly, it is not purchasing and installing the most advanced and most expensive intrusion detection system. For most commercial companies and other organizations, the main goal is obtaining revenue, and naturally, all efforts are concentrated on achieving this aim. Information technologies (IDS infrastructure being one of its components) also aim at increasing the company's profit (which, roughly speaking, is the difference between the company's income and expenses). Thus, the company achieves its goal either by increasing its income or by decreasing expenses. An ideal situation is one where you can combine both approaches. However, this is not always possible. As a rule, expenses grow with the increase of income. Thus, the company will suffer financial losses from bringing a technology into operation only if the income from that technology does not exceed the expenses for deployment, operation, and maintenance of that specific system. You will thus have to calculate and evaluate the potential advantages and incomes expected from the deployment of the intrusion detection infrastructure, and compare them to the expenses required for these operations. The first task can be solved using the ROI (Return on Investment) mechanism, while the second one can be done using the TCO (Total Cost of Ownership) mechanism. However, you should note that even if calculating the TCO is not such a difficult task, it is rather problematic (if even possible) to calculate the efficiency of bringing IT technologies into operation, since intrusion detection systems do not directly participate in generating income. Furthermore, the task of comparing system states before and after deployment of the intrusion detection infrastructure is also rather difficult.
Total Cost of Ownership
The Total Cost of Ownership determines the planned and unforeseen costs related to ownership and usage of a specific system for its whole life cycle. Obviously, besides the direct expenses for an intrusion detection system, there are indirect expenses that appear during its operation. For example, according to the data of the Gartner Group, direct expenses make up only 15 to 21% of the total expenses of purchasing and operating an information system.
Total Cost of Ownership can be divided into direct and indirect expenses. Direct expenses include the following:
-
Capital outlays for IDS hardware and software.
-
Cost of additional software (DBMS, Internet browser, hardware setup and configuration tools, backup solutions, etc.) and required equipment (network cables, T-connectors, cable, etc.). This topic will be covered in more detail in Chapter 11.
-
Cost of maintenance and training of personnel (if these expenses are not included into the cost of software and equipment). In addition, maintenance and training costs also include travelling expenses for visiting remote offices and setting up remote components of the intrusion detection system. According to Gartner Group data, this item can make up from 17 to 27% of the total cost.
-
Expenses for IDS management, which include the salaries of the security administrator and other technical personnel that support and maintain the intrusion detection system. Besides which, this item of expenses can include the costs of outsourcing services and responses to attacks. As a rule, this item of expenses takes up about 9 to 13% of the TCO.
-
Expenses required to bring the system into operation (including preliminary investigation and composing the network map). This item usually takes up about 20% of the TCO.
Indirect expenses might include the following:
-
Losses incurred by inefficient work, when users start working with the system without proper knowledge and understanding of its working principles. This might result in possible malfunctions, loss of time, etc.
-
Losses caused by the downtime of the intrusion detection system.
Thus, a choice in favor of a freeware intrusion detection system, which at first glance might seem logical and advantageous, is not necessarily the best solution. If you choose this approach, expenses for bringing such a system into operation, along with the maintenance and support expenses, can significantly exceed similar expenses for a commercial product (which at first might seem rather expensive).
The most important aspects that must be taken into consideration when calculating the Total Cost of Ownership of the intrusion detection system are listed below:
-
The cost of the computer selected for installing the management console and control server (in three-tier architecture).
-
The cost of the computer selected for installing the IDS sensor (if the sensor is not supplied as a separate security appliance or is not integrated with network equipment).
-
Network equipment required for controlling network traffic (splitter, hub, and workload balancer). More detailed information on this topic will be provided in Chapter 10.
-
Costs of add-on software and hardware, which will be covered in detail in Chapter 11.
-
Purchasing additional hard disks for storing large amounts of data from system sensors.
-
The decrease in the performance of controlled hosts and networks, and consequently, reduced incomes obtained as a result of the operation of the controlled hosts.
-
The salary of the IDS operators, including expenses for supporting a 7x24 mode of operation.
-
The salary of the personnel responsible for administering the intrusion detection system, incident response, and investigation.
-
Expenses for development and implementation of the incident response plan.
-
Expenses for recovery of the intrusion detection system in case it becomes an attack target.
-
The cost of downtime caused by malfunctions of the IDS's components.
When composing a yearly budget, do not forget about depreciation, which, in the IT area, includes the obsolescence of computers and network equipment, as well as that of the software used. Now, practically everyone understands that since information technologies seem to evolve exponentially, both hardware and software become obsolete very soon. Remember that it was not so long ago when 20 MB hard disks were an unattainable dream of many users (and compare this situation to the current one, when it is hard to find a hard disk of a size less than 20 GB). The situation is similar with intrusion detection systems. Hardware appliances become obsolete and can not handle an increased amount of data within half a year after its implementation! Let's consider this situation using a practical example. Suppose that your network sensor started to experience performance problems, and in order to improve the situation, you need to increase the RAM installed on the sensor. Once again, you will need to justify the necessity of these additional expenses to someone who does not understand technical problems. In this case, it is the most likely that you will get a standard answer: "According to the norms and standards, the life cycle of the RAM module is 3 years. Your sensor was purchased only 6 months ago. Come back in two-and-a-half years." You will probably have quite a tough time advocating your point of view. And even if you do actually accomplish the impossible and prove to a person far removed from information technology that the addition is necessary, he or she still might not be able to help you, since the money for updating the sensor was not foreseen in the budget. On the other hand, if you correctly formulated the budget and included a special item of expenses for hardware or software upgrades, the situation might seem a little brighter.
Furthermore, the analysis and calculation of the TCO often helps you understand whether or not you will be able to operate an IDS efficiently relying just on your internal resources. If it seems that you will be able to, you should consider purchasing an outsourcing service. In other words, calculating the TCO allows you to justify the necessity of purchasing technical support or outsourcing services.
Return on Investment
Currently, it is common practice to measure the success of a specific project in terms of Return on Investment (ROI). ROI is the ratio of money earned to the sum invested into a specific area of activity, expressed as a percentage. This concept is easily understandable. However, behind this simplicity, there is quite a complicated procedure for calculating the ROI, which can not always be formalized. The calculation formula includes a large number of parameters, including ones directly related to the intrusion detection infrastructure, as well as the general financial parameters of your company. Thus, it is very important to know the total value of the corporate resources and revenues yielded by specific sectors of the company's business activity. When you lack this information, calculating the ROI gets much more complicated, or even becomes impossible. It is not always possible to calculate the ROI even if you do know all these parameters. An example of a situation in which you will have difficulty evaluating the ROI is when one specific technology or system yields indirect advantages that are hard to evaluate numerically. For example, if you migrate from the Snort intrusion detection system (which does not provide a graphical user interface and is hard to manage and maintain in a large distributed network) to another product, such as RealSecure or Cisco IDS, the advantages are obvious, but difficult to express in numbers. How can you calculate the cost of ease of use and administrator convenience? However, even in such a case, you must understand the advantages that the company will see after migrating to the new technology, starting from ease of use, convenience, and reduction of the response time, all the way up to a decrease in system maintenance and personnel training costs.
We can provide the following simplified model for evaluating the damage related to not using an IDS. The formula provided below calculates the total sum of the financial loss for a single host (for example, a web server). However, this formula can easily be rewritten for calculating the financial losses incurred by an attack on the whole corporate network. When calculating the total losses incurred by an attack on the whole network, all parameters will become global and will relate to all corporate resources.
The initial data will be provided below.
-
Downtime caused by the attack, tD (in hours)
-
Time required to repair a system damaged by the attack, tR (in hours)
-
Time required to re-enter lost information, tRI (in hours)
-
The salary of the technical maintenance personnel (administrators, technicians, etc.), SM
-
The salary of employees maintaining the attacked host or segment, SE
-
Number of maintenance personnel administrators, technicians, etc., NM
-
Number of employees maintaining the attacked host or segment, NE
-
Sales made by the attacked host or segment, SALES ($ per year)
-
Cost of replacing equipment or spare parts, CSP
-
Number of attacked hosts or segments, I
-
Number of attacks per year, n
The total sum of losses caused by the lost productivity of the employees of the attacked host is equal to:
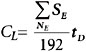
The cost of restoring the attacked host or network segment comprises several components:
![]()
where CRI is the cost of re-entering the lost information, and CRH is the cost of restoring the host (OS installation and configuration, etc.).
These are calculated using the following formulas:
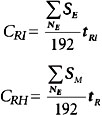
The profit loss caused by downtime of the attacked host or segment is:
![]()
where
![]()
Thus, the total damage caused by an attack on the host or segment of the corporate network is equal to:
![]()
Let's give an example that illustrates the procedure of assessing the damage caused by an attack on a protected object based on the following initial data.
-
Downtime caused by the attack tD (in hours) = 2 hours
-
Time required to repair the damaged system after an attack, tR (in hours) = 8 hours
-
Time required to re-enter the lost data, tRI (hours) = 8 hours
-
The salary of the technical maintenance personnel (administrators, technicians, etc.), SM ($ per month) = $5,000 [SANS2-00]
-
The salary of the employees of the attacked host or segment, SE ($ per month) = = $6,000
-
Number of maintenance personnel (administrators, technicians, etc.), NM = 1
-
Number of employees of the attacked host or segment, NE = 4
-
Sales made by the attacked host or segment, SALES ($ per year) = $1,000,000
-
Cost of replacing the equipment or spare parts CSP = $0
-
Number of attacked hosts or segments, i = 1
-
Number of attacks per year, n = 5
The salary of an employee per hour will be 6,000 / 192 = 31.25, while the salary of the support personnel per hour will be 5,000/192 = 26.042. The cost of the lost productivity of the employees of the attacked host or segment will be CL = 4 × 31.25 × 2 = = $250, while the cost of re-entering the lost information and restoring the damaged host will be CRH = 0 and CRI = 1 × 26.042 × 8 = $208.34, respectively. Since the equipment was not replaced (CSP = 0), the cost of restoring a host damaged by the attack will be CR = $208.34. V= 1,000,000/2080 × (2 + 8 + 0) = $4,807.70 and the total lost profit will be equal to U = 250 + 208.336 + 4807/7 = $5,266. As a result, the total damage caused by 5 attacks on a segment per year totals L = 5,226 × 5 = $26,330, which justifies the purchase of an intrusion detection system for this amount.
As you can see, this formula does not take into account some probability parameters that increase or decrease the risk of losses, including the following:
-
Labor turnover, which results in a lack of qualified personnel and an increase in expenses for training new employees.
-
Internet access, which results in an increased number of possible attacks. Notice that the use of other security tools in combination with an intrusion detection system decreases this number.
-
The availability of dedicated employees responsible for intrusion detection and response.
Sales made by the attacked host is not a single parameter that can be used in this formula. We can also take into account, for example, the amount of lost profit resulting from downtime and malfunctions, or what the company will have to pay because of the failure to carry out its responsibilities resulting from the failure of the attacked resource.
Such parameters as expenses for criminal prosecution due to a leakage of confidential information, lost productivity, loss of customer confidence (or what is worse, customer migration to the company's competitors), damage to the company's reputation, etc., are very hard to calculate. However, they also must be taken into account in this formula. Taking these parameters into account increases the total of the potential financial losses caused by lack of an intrusion detection infrastructure.
Finally, there are several other aspects that result from the deployment of an intrusion detection system, and their assessment will also help you to assure the management as to the necessity of investments.
First, IDS deployment and implementation (or migration to a newer IDS version) releases security administrators from having to perform a large amount of manual operations (beginning with the manual analysis of log files and network traffic, and ending with the updating of the signature database and remote host scanning according to schedule). As a result, administrators will work more efficiently, which can be expressed in the following financial formula:
![]()
where P is the productivity of n administrators, tM and tA is the time required to perform intrusion detection operations in manual and automatic modes, respectively, and S is the salary of the security administrators.
Second, the automation of intrusion detection operations results in a decrease in the number of specialists who must participate in this process. Furthermore, tasks that earlier could only be delegated to qualified experts can now be performed by operators.
![]()
where EA is the efficiency of n administrators, Nbefore and Nafter are the number of administrators before and after deployment of the IDS, and SA is the salary of security administrators.
By adding up the parameters listed above and subtracting the TCO from the results, you will get the effect of deploying the IDS, which must be more than 1. If the result is less than 1, using an intrusion detection system will not solve your problems, will not produce any effect, and will only complicate the current situation with corporate network security.
EAN: 2147483647
Pages: 152