End-to-End Enterprise Application Security Integration (EASI)
As e-commerce environments have evolved to distributed component models, security technologies have been trying to keep up. Most of the pieces of the security puzzle exist as off-the-shelf products, but it still takes considerable effort to put all these pieces together to build an integrated solution.
Twenty-two years ago, life was reasonably simple for the security professional. Sensitive data resided on monolithic backend data stores. There were only a few physical access paths to the data, which were protected by well-understood operating system access control mechanisms. Policies, procedures, and tools have been in place for many years to solve this class of problems.
Several years ago, Web-based applications burst onto the scene. With the advent of e-commerce in this environment, secure access to the Web servers was extremely important. Today, there are many mature perimeter security technologies, such as SSL, firewalls, and Web authentication/authorization servers that enforce security between browser clients and corporate Web servers.
Huge numbers of companies are now building complex e-commerce logic into application servers in the mid-tier. The business motivation for this development is compelling. Mid-tier business logic allows accessibility to backend legacy data in ways never imagined. The opportunities for increased interaction among all kinds of buyers and suppliers seems endless.
Security gets much more interesting through the introduction of components in the middle tier. Although there are many mid-tier technologies that hook up Web servers to backend legacy systems, the security of these approaches is often nonexistent. In fact, several recent publicized attacks have been caused by weaknesses in mid-tier security that have exposed sensitive backend data (customer credit card numbers and purchase data) to the outside world. Companies are usually at a loss for what to do with middle tier security.
To solve the thorny issue of securely connecting Web servers to the back office, let’s now discuss the concept of end-to-end EASI. As previously discussed, EASI is a special case of EAI.
In addition, EAI is a technique for unifying many different applications by using a common middleware infrastructure. EAI provides an application “bus” that allows every application to communicate to others via a common generic interface. Without EAI, an application would need a separate interface for each other application, thus causing an explosion of pairwise stovepipes between applications. EAI allows application development to scale to a large number of interchangeable components.
Integration of end-to-end security requires EAI techniques. Many different security technologies are used in the perimeter, middle, and legacy tiers, as shown in Figure 17.3[1]. Typically, these security technologies do not easily interoperate. As a result, you will face exactly the same problem that application integrators face: a separate ad hoc interface to connect one security technology to another causes an explosion of pairwise stovepipes between security technologies.
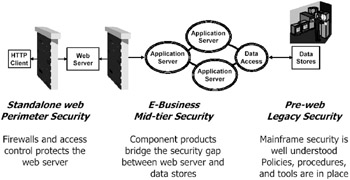
Figure 17.3: E-commerce requires Enterprise Application Integration (EAI) across multiple security technologies.
EASI, on the other hand, provides a common security framework to integrate many different security solutions. By using EASI, new security technologies in each tier can be added without affecting the business applications. EASI will be further explored next.
EAN: 2147483647
Pages: 260