7.6 The VPN on the Network
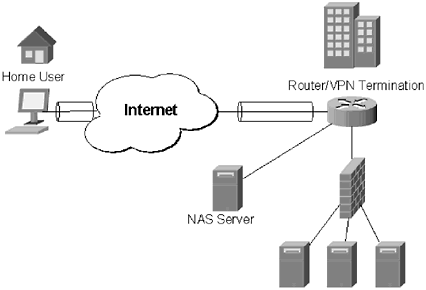
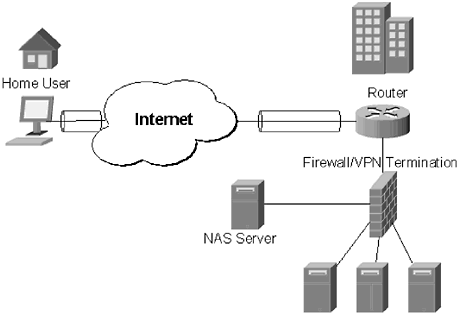
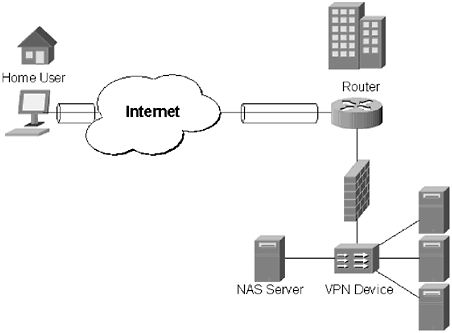
| There is some debate about the best place to terminate a VPN. Part of the debate originates from the fact that there are so many devices available for VPN termination. There are three common termination points for VPNs: router, firewall, and dedicated VPN device. Each one has advantages and disadvantages. The right method of VPN termination is largely dependent on available resources, network design, and comfort level. 7.6.1 Terminating the VPN on the RouterTerminating the VPN on the router is not very common for enterprise networks. As already demonstrated, routers have notoriously bad logging facilities, and rely on external logging sources to log information. Adding the burden of encrypting and decrypting VPN information may overwhelm some routers. For example, Cisco has introduced a VPN module for its 2600 series routers. The 2600 router, generally used for terminating T1s, with the VPN module requires a minimum of 128 megabytes (MB) of random access memory (RAM). A second problem is with the firewall rule set. Additional rules will need to be added to the firewall to allow VPN terminated traffic into the network. This may raise security concerns. Some vendors have resolved this problem by incorporating the VPN, firewall, and router into a single device. This type of access device may work well for small networks, but they are generally underpowered for large networks. In addition, having all three services in the same device removes two layers of security. If a hole into the network is found, there is not another layer of protection. As previously mentioned, VPN termination to a router requires that the router be equipped to handle VPN terminations. This involves encrypting and decrypting connections, and, depending on the number of VPN connections, can put a significant drain on CPU and memory resources. Shown in Figure 7.8, the VPN terminates at the edge router. The authentication request is forwarded to a NAS server, similar to the way TACACS+ or RADIUS works. The NAS server authenticates the user, and the user is granted access to the network. Figure 7.8. VPN termination at the edge router. A VPN connection is made to the router, which forwards the request onto the NAS. The NAS authenticates the user, who is now allowed access to the network. Figure 7.8 also illustrates the biggest problem with this approach: The user now has to get past the firewall. Unfortunately, there is not always an easy way to allow this, without creating rule sets that are so broad that they are essentially useless. Again, terminating the VPN at the router may be a good idea for a small network, or a home user ”who does not want to use a VPN client ”but for an enterprise network router, terminated VPNs are generally not a good idea. 7.6.2 Terminating the VPN on the FirewallFirewall termination of VPNs has become very popular recently. Cisco PIX, Check Point, and NetScreen all have products that allow their firewalls to become VPN terminating devices. The pairing of VPN and firewalls makes sense for several reasons. The firewall already performs extensive logging of network connections; adding the additional logging of VPN connections should not create an excessively large load. Firewalls are also the entry point to the network; having a VPN terminate at the firewall means that users can have network access without having to open additional holes in the firewall rule set. The termination of a VPN at the firewall level operates in much the same way as the termination of a VPN at the router level. A user makes a connection to the firewall. The firewall forwards the authentication to a NAS server. The NAS server authenticates the user, and the firewall grants the user access to the network. This process is outlined in Figure 7.9. Figure 7.9. The VPN from the user into the company network is terminated at the firewall. The firewall receives the authentication request and forwards it to the NAS server, which handles the actual authentication process. Firewall termination gives a network administrator much more control. Users terminated at the firewall can be restricted to only a certain part of the network, and firewall termination means that no holes have to be opened in the firewall for users already authenticated. One of the downsides that plagues this type of connection is the same problem that router terminated VPN connections have: The VPN encryption/ decryption process uses significant system resources. A firewall that is already burdened, especially one with an active DMZ, may be crushed under the weight of managing hundreds of simultaneous VPN tunnels. A firewall-terminated VPN solution is appropriate for an enterprise organization. However traffic patterns should be monitored closely to ensure the firewall is not being overloaded with VPN tunnels. 7.6.3 Terminating the VPN to a Dedicated DeviceSome companies prefer to use a dedicated VPN device, rather than a combination VPN and router, or a VPN and firewall device. Cisco, Nortel, AppGate, Lucent, and Check Point ”among others ”all make dedicated VPN devices or software that can run on a dedicated VPN device. Dedicated devices have several advantages, the primary one being that they take the load of managing the VPN off the router and the firewall. A purpose-built device is now handling the encryption and decryption process, so even if it does become overburdened by too many connections, it will not impact the rest of the network. A second advantage is that it creates another layer of security in the VPN process. Rather than risk having tunnels terminated at the router or firewall, they are terminated within the network, where administrators have more control (Figure 7.10). Termination inside the network gives network administrators the ability to restrict traffic to certain parts of the network, limiting the damage an attacker can do should the VPN be breached. Figure 7.10. VPN is terminated to a dedicated device. Depending on the placement of the device within the network, the user can be restricted to certain areas once authenticated. Figure 7.10 illustrates the process of terminating a VPN to a dedicated device. The user authenticates against the dedicated device. The VPN device can either handle the authentication process, or forward the request to a NAS. If the authentication of the user is successful, the user has access to the network. Again, the part of the network the user has access to can be controlled by the network administrators. While VPN devices provide a lot of benefits, there are minuses. The chief concern is that it is another network device that has to be managed, and monitored, for software upgrades and potential security holes. Security holes in a VPN device are of particular concern, because if they can be exploited they may give an attacker access to an entire network. In addition, there may be software management involved. Most of these dedicated devices include software that can be used to create the tunnels. This software has to be distributed and installed on machines of users who will connect to the VPN. Upgrades and patch installations of the software will also have to be maintained . This can often be avoided by taking advantage of the tunneling software bundled with an operating system. However, if there are connectivity problems between a user and a VPN device, the user may be forced to use the vendor-supplied tunneling software. Dedicated VPN devices also require creating additional holes in the corporate firewall. Ports have to be opened to allow either PPTP or L2TP tunnels through the firewall and into the network. While this does not pose much of a security concern, any time additional traffic has to be allowed through the firewall should be cause for concern. Finally, there is the cost factor associated with dedicated VPN devices. A VPN device that can maintain the number of connections required by an enterprise network can cost in excess of $10,000, double that number if redundancy is desired. That cost will increase as the popularity of the corporate VPN increases . A dedicated VPN solution does offer an excellent solution for organizations that desire a robust and scalable solution, which will not impact the rest of the network. As with any other decision, it is important to explore all options and assess potential traffic patterns thoroughly before making a decision. |
EAN: 2147483647
Pages: 131